Lesson 4:Troubleshooting Authorization Problems
|
| < Day Day Up > |
|
The more effort you make to tighten access control, the more likely your users are to experience authorization problems. Authorization problems occur when a legitimate user should have access to perform a particular action on an object according to your organization's management team, but overly restrictive access control prevents the user from performing that action.
The first thing to check when troubleshooting an authorization problem is the target object's ACL. The problem may be as simple as an ACE that explicitly denies access to that user. More often, the problem is caused by the user not having any permissions assigned to the object. If examining the object's ACL does not identify the problem, check the object's effective permissions.
If you cannot identify which objects the user needs access to, you can use auditing to identify which objects the user is attempting to access and how the user is accessing the file. It is common for applications to access resources that an administrator would not be able to anticipate. For example, the application might require access to Dynamic Link Libraries (DLLs) located in the system directory, or the application might attempt to write temporary files to an unusual location. Troubleshooting authorization using auditing is complex, but it can identify insufficient privileges that would otherwise be nearly impossible to find.
| Tip | You can quickly identify whether a particular problem is caused by authorization by performing the action while logged on as an administrator. If it works as an administrator, but not as a standard user, then authorization is almost certainly the cause of the problem. |
After this lesson, you will be able to
-
Identify a user's effective permissions for an object.
-
Determine the source of incorrectly assigned permissions.
-
Identify which objects a user or an application is attempting to access.
-
Resolve problems relating to users who cannot access required resources.
Estimated lesson time: 45 minutes
Troubleshooting Simple Authorization Problems
If you are troubleshooting a simple authorization problem in which you know which objects the user cannot access, start by examining the object's access control list. The user interface varies slightly depending on what type of object you are examining, but the concepts are the same. In most circumstances, you will follow these steps to analyze effective permissions and resolve the problem:
-
View the object's permissions.
-
Click the Advanced button.
-
In the Advanced Security Settings dialog box, click Effective Permissions.
-
Click Select. In the Select User, Computer, Or Group dialog box, type the name of the user and click OK.
-
Examine the Effective Permissions list, as shown in Figure 2.8, to identify permissions that the user requires but currently lacks. Click OK to return to the object's permissions dialog box.
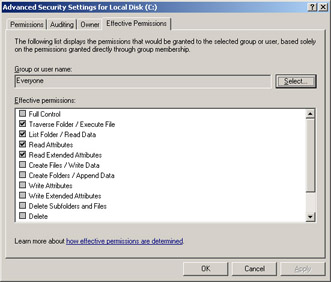
Figure 2.8: Windows Server 2003 allows you to view the effective permissions for most object types -
Grant the user, or a group to which the user belongs, the privileges necessary to perform the action.
When correcting authorization problems, follow the same guidelines you used for initially designing the authorization strategy. Whenever possible, assign permissions to a group rather than a user. If the user should have access to all the objects in a container, assign permissions to the container itself and allow those permissions to be inherited by the child objects.
| Warning | Check your organization's security policy before elevating any user's permissions to an object. |
Troubleshooting Complex Authorization Problems
Part of the challenge of troubleshooting authorization problems is identifying which objects the user is attempting to access. If the user is attempting to edit a file and is denied access, identifying the file is straightforward. However, if a custom application is returning an ambiguous error message because it cannot access a required object, identifying the specific object the application is attempting to access is much more complex. In fact, it may not be clear whether the application is attempting to access a file, printer, registry value, Active Directory object, or service.
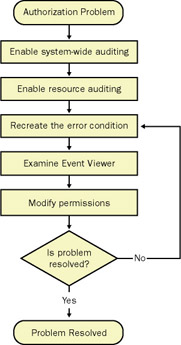
Fortunately, you can use auditing to identify objects that a user or application is attempting to access. The flowchart in Figure 2.9 illustrates the authorization troubleshooting process that occurs when you use auditing.
| Off the Record | Most people think of auditing as solely an intrusion detection mechanism. In reality, its usefulness for intrusion detection is limited because auditing tends to generate far too many events to successfully parse. However, it is immensely useful when troubleshooting authorization problems. |
While most of the troubleshooting process is self-explanatory, enabling system auditing, enabling resource auditing, and analyzing events by using Event Viewer deserve further explanation.
Enabling system auditing
The first step in identifying resources with insufficient privileges is to enable auditing on a system-wide basis:
-
As an administrator, log on to the system with the resources you are troubleshooting. If you are troubleshooting access to Active Directory objects, log on to a domain controller.
-
Click Start, and then click Administrative Tools. If this is a domain members or a standalone computer, click Local Security Policy. If this is a domain controller, click Domain Controller Security Policy.
-
Expand Local Policies, and then click Audit Policy.
-
If you are troubleshooting access to Active Directory objects, double-click Audit Directory Service Access. If you are troubleshooting access to any other type of object, double-click Audit Object Access.
-
Make note of the current setting. You will return this setting to its original state after you have completed the troubleshooting process.
-
Select Define These Policy Settings, and then select Failure, as shown in Figure 2.10. Click OK.
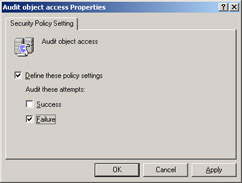
Figure 2.10: Auditing must be enabled for the system before it can be enabled for individual resources
Enabling resource auditing
After enabling failure auditing for the Audit Object Access or Audit Directory Services Access policies, you must enable auditing for the individual resources that are being accessed. The exact process varies depending on the type of object you want to audit. The following process applies to enabling auditing for folders or files, the most common source of authorization problems. The process for auditing other types of objects is very similar, although you will use a different tool for each object. For information on the specific tools to use for each object type, refer to the 'Standard and Special Permissions' section in this chapter.
-
Click Start, point to All Programs, point to Accessories, and then click Windows Explorer.
-
Navigate to the file or folder you want to audit. If you are not sure which object is being accessed, you can enable auditing for entire disks.
-
Right-click the file or folder, and then click Properties.
Tip If you were auditing the registry, you would right-click the registry key and select Permissions.
-
On the Security tab, click the Advanced button.
-
In the Advanced Security Settings dialog box, click the Auditing tab. Make note of the current settings, and then click Add.
-
In the Select User Or Group dialog box, type the name of the user whose problem you are troubleshooting, and then click OK. The Auditing Entry dialog box appears.
-
Click the Failed check box for the Full Control entry, as shown in Figure 2.11. All Failed check boxes will be automatically selected.
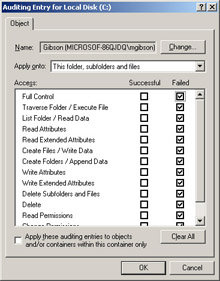
Figure 2.11: Failure auditing causes events to be added to the event log when a user is denied access to a resource -
Click OK twice. Windows Server 2003 will apply the auditing setting to the folder, subfolder, and files automatically. If you are applying access to a large number of files, such as the entire C drive, this may take a moment.
-
Click OK to close the properties dialog box and return to Windows Explorer.
Now that failure auditing is enabled for those resources, every time the specified user is denied access to the resource, Windows Server 2003 will add an event to the Security event log.
Analyzing events in Event Viewer
After you have enabled auditing and re-created the problem condition, Windows Server 2003 will add events to the Security event log describing which resource could not be accessed and the type of operation that was attempted. To view failure audit events by using Event Viewer:
-
As an administrator, log on to the system with the resources you are troubleshooting. If you are troubleshooting access to Active Directory objects, log on to a domain controller.
-
Click Start, click Administrative Tools, and then click Event Viewer.
-
In the left pane, click Security. The Security event log will be displayed.
-
On the View menu, click Filter. The Security Properties dialog box appears.
-
Clear the Information, Warning, Error, and Success Audit check boxes. Only the Failure Audit check box should remain selected. Click OK.
-
Event Viewer will now display only failure audits in the right pane. Double-click the most recent failure audit to examine the contents of the event. The Event Properties dialog box appears, as shown in Figure 2.12.
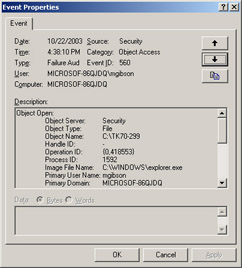
Figure 2.12: Event Viewer reveals the object that the user lacked sufficient permissions to access -
Examine the Description field. This field shows the type of object, the object name, the process ID and image file name of the application used to access the object, and the type of operation that was performed on the object. For example, the following are the contents of the Description field for a user, mgibson, that was denied access to the C:\TK70-299 folder when she attempted to access the folder using Windows Explorer.
Object Open: Object Server: Security Object Type: File Object Name: C:\TK70-299 Handle ID: - Operation ID: {0,419122} Process ID: 1592 Image File Name: C:\WINDOWS\explorer.exe Primary User Name: mgibson Primary Domain: MICROSOF-86QJDQ Primary Logon ID: (0x0,0x60641) Client User Name: - Client Domain: - Client Logon ID: - Accesses: SYNCHRONIZE ReadData (or ListDirectory) Privileges: - Restricted Sid Count: 0 Access Mask: 0x100001Notice that the Accesses line lists Synchronize and ReadData. This indicates that the user was attempting to gain read access to the C:\TK70-299 directory. To resolve this problem, you would grant the user (or a group to which the user belongs) read access to that folder.
-
Browse through other failure audit events to determine other resources to which the user might require access.
After identifying the resources the user requires access to and assigning new permissions, repeat the troubleshooting process by re-creating the problem. If the problem is resolved, follow the procedure described in 'Enabling resource auditing' and 'Enabling system auditing' in this chapter to return the auditing configuration to its original state. If the problem isn't resolved, review the Security event log again to identify other permissions that are lacking, and repeat this process.
Lesson Review
The following questions are intended to reinforce key information presented in this lesson. If you are unable to answer a question, review the lesson materials and try the question again. You can find answers to the questions in the 'Questions and Answers' section at the end of this chapter.
-
John is a member of both the IT and Finance groups. When John attempts to edit a file, he is denied access. Which of the following scenarios are potential causes of this problem? (Choose all that apply.)
-
The IT group has the Deny Read & Execute file permission assigned, and the Finance Group has the Grant Modify permission assigned.
-
The IT group has the Grant Modify permission assigned, and the Finance group has no permissions assigned.
-
Neither the IT group, the Finance group, nor John's user account have permissions to the object explicitly assigned.
-
The IT group has the Grant Modify permission assigned, and the Finance group has the Deny Change Permission special permissions assigned.
-
-
The Effective Permissions tool can be used to discover which of the following pieces of information? (Choose all that apply.)
-
That the user John is a member of the Interactive special group
-
That the user John is a member of the Finance security group
-
That the Finance security group has been denied access to a folder
-
That the user John will be denied access to a file because access is denied to a group of which John is a member
-
Lesson Summary
-
Identify whether a particular problem is related to authorization by attempting to perform the action using an administrator account.
-
If you follow the principle of least privilege carefully, you are likely to inadvertently restrict users from accessing resources they should legitimately be able to access.
-
To troubleshoot authorization problems, start by identifying the objects that are required by the user. Auditing can be used to identify which objects the user is being denied access to. After auditing is enabled, Windows Server 2003 will add events to the event log describing the resource with insufficient privileges.
-
If you enable auditing for the purpose of troubleshooting, return it to its original state after the problem has been resolved.
-
Use the Effective Permissions tool to identify the permissions a user or group has to an object.
|
| < Day Day Up > |
|
EAN: 2147483647
Pages: 217