Questions and Answers
|
| < Day Day Up > |
|
Lesson 1 Review
Page
9-16
| 1. | Which of the following options ensures that certificates are accepted from only valid computer accounts in the same forest?
| |
| 2. | Which of the following operating systems could you configure by using the IPSecPol command-line tool?
| |
Answers
| 1. | a. The Enable Certificate To Account Mapping option causes IPSec to look up a valid computer account in the current forest before authenticating a connection from an IPSec peer using a certificate. |
| 2. | c. IPSecPol is a Resource Kit Tool available only for Windows 2000. For Windows XP, you should use IPSecCmd. For Windows Server 2003, use the Netsh tool. |
Lesson 2 Review
Page
9-38
| 1. | Which of the following parameters can be found in IP Security Monitor’s Main Mode Statistics? (Choose all that apply.)
| |
| 2. | Which of the following tools can be used to verify that network traffic to a specific host is being encrypted on a computer running Windows Server 2003? (Choose all that apply.)
| |
| 3. | Which of the following tools can display the total cumulative number of successful Main Mode negotiations on a computer running Windows Server 2003? (Choose all that apply.)
| |
Answers
| 1. | a, d, e, and f. These statistics relate to the IKE negotiations, and, as such, are found under Main Mode Statistics. The other answers are found in Quick Mode Statistics because they relate to the IPSec sessions. |
| 2. | a, c, and e. IP Security Monitor lists active SAs in addition to the methods used for encryption and integrity for any specific connection. Netsh can provide the same information at a command line. Network Monitor captures the entire packets as they are communicated between IPSec-protected computers. If the packets are encrypted, Network Monitor will not be able to interpret the contents of the packets contained within the ESP headers. |
| 3. | a, c, and g. IP Security Monitor displays the IKE Main Mode parameter within the Main Mode Statistics node. Netsh can provide the same information at a command line. The Performance console can display the value for the Total Main Mode SAs counter within the IPSec v4 IKE performance object. |
Lesson 3 Review
Page
9-46
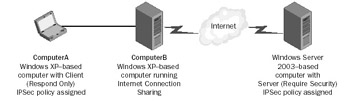
| 1. | IPSec peers ComputerA and ComputerB, as shown in Figure 9.15, are unable to establish a connection. What is the cause of the problem? | |
Answers
| 1. | Internet Connection Sharing in Windows XP does not support NAT-T, even though Windows XP supports NAT-T as an IPSec client. |
Design Activity: Case Scenario Exercise
Page
9-48
| 1. | How can you prevent internal employees from capturing other employees’ passwords in the future? | |
| 2. | Which of the built-in IPSec policies would you assign to the mail server? | |
| 3. | Will you use Kerberos, certificates, or a preshared key to authenticate the IPSec connections? | |
| 4. | Besides IPSec, what measures can you take to reduce the risk of an attacker capturing network communications and misusing that information? | |
Answers
| 1. | There are a couple of ways to do this. The simplest way is to configure your e-mail server to use only encrypted protocols. But the choices available for encrypting e-mail transmissions depend on the mail server and client software used. If your environment used Exchange Server and Outlook exclusively, you could choose to encrypt all mail communications and almost entirely eliminate the risk of an attacker gathering passwords by using a sniffer. However, if the organization uses various mail servers or a variety of mail clients, there might not be an encrypted protocol that all the clients can use. Given the limitations of using encrypted mail protocols, IPSec is the most attractive choice for encrypting the communications. IPSec provides a way to encrypt network traffic regardless of the server and client applications used. |
| 2. | For the time being, you have no choice but to assign the Request Security IPSec policy. You cannot use the Require Security policy because you have clients that probably don’t support IPSec, such as two-way pagers. Even if all clients do support IPSec, it is going to take weeks or months to test and deploy IPSec for all the computers in your organization. |
| 3. | You should use both Kerberos and certificates. Kerberos is the fastest way to allow IPSec authentication for computers that are members of your domain. You can issue certificates to client computers that are not members of the domain. |
| 4. | First, you should implement non-technical countermeasures. Create a computer usage agreement that explains what users can and cannot do with the organization’s computers, and have all employees sign that agreement. Make it clear that employees can and will be caught if they break the agreement. Employees must understand that when they are caught, they will be punished. Second, implement physical security wherever possible. Use network hardware that does not send network communications to all ports. In other words, use Layer 2 switches rather than hubs. Restrict access to your network equipment to prevent a potential attacker from tapping directly into a hub or switch and capturing network traffic. Third, use software restrictions to limit the tools users, and even administrators, can run. There are legitimate reasons for running Network Monitor on a server, but the potential for abuse is high. It is difficult to restrict administrators from running applications while allowing them to do their jobs, but it might be worth the effort to reduce the risk of an employee violating another employee’s privacy. |
Design Activity: Troubleshooting Lab
Page
9-50
| 1. | Which of the following tools can you use to check which IPSec policy is assigned to Computer1? (Choose all that apply.)
| |
| 2. | Open Microsoft Internet Explorer on Computer2, type the URL http://computer1 in the address bar, and then click Go. Is traffic from Computer2 reaching Computer1? How can you tell? | |
| 3. | Is the traffic encrypted? How can you tell? | |
| 4. | Are Main Mode negotiations succeeding? How can you tell? | |
| 5. | Based on the information you have gathered, what is the likely cause of the problem, and how will you resolve the problem? | |
| 6. | How will you verify that IPSec negotiations are now successful? | |
Answers
| 1. | a and c. IP Security Monitor and Netsh both report the active IPSec policy. |
| 2. | Yes. You can run Network Monitor on Computer1 to verify this. |
| 3. | No. Network Monitor reveals that standard, unencrypted HTTP communications were captured. If the traffic were encrypted, Network Monitor would not have been able to identify the communications as being HTTP. |
| 4. | No. There are several ways you can determine this. First, Network Monitor has revealed that traffic is not encrypted, which is a sign that either Main Mode or Quick Mode negotiations have failed. Second, the Main Mode Statistics counters in the IP Security Monitor snap-in are not incrementing in the way they would if Main Mode negotiations were succeeding. You could also review the Oakley.log, which would reveal that Computer1 applied the Server (Request Security) policy to the incoming traffic, but that negotiations with Computer2 failed. |
| 5. | Either Computer1 does not have IPSec enabled or Computer1 and Computer2 do not have a compatible set of protocols enabled. You should check the configuration on both computers and assign a policy to Computer2 that would enable IPSec communications with Computer1. The Client (Respond Only) policy would be perfect. |
| 6. | You can use Network Monitor to verify that traffic is encrypted and that it is being transferred with ESP. Alternatively, you can use the IP Security Monitor snap-in, the Performance console, or Netsh to verify that the total number of IPSec connections counter has incremented. |
|
| < Day Day Up > |
|
EAN: 2147483647
Pages: 217
- Chapter V Consumer Complaint Behavior in the Online Environment
- Chapter VII Objective and Perceived Complexity and Their Impacts on Internet Communication
- Chapter VIII Personalization Systems and Their Deployment as Web Site Interface Design Decisions
- Chapter X Converting Browsers to Buyers: Key Considerations in Designing Business-to-Consumer Web Sites
- Chapter XIII Shopping Agent Web Sites: A Comparative Shopping Environment