Design Model
| Recall from Chapter 1, "Network Design," that when designing a network, the following tasks should be considered:
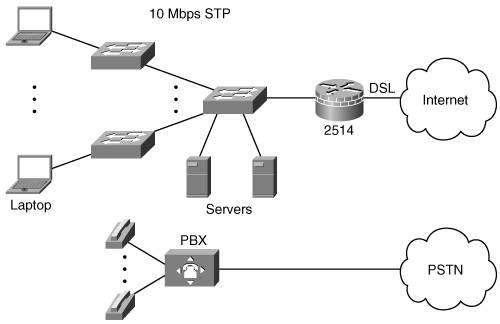
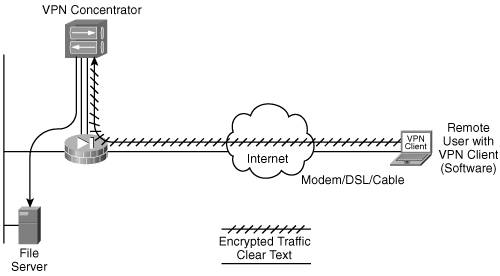
Chapter 11 provides the background for the case study, including the details of the existing network and the requirements for the new and updated network. In this chapter, we produce the design. For the purposes of this case study, we assume that the relevant personnel at Venti Systems are being consulted along the way and that they are approving the design as we go. We do not go into the deployment or monitoring steps for this case study, but we provide all the details that would be necessary to produce the design documentation. We use the Enterprise Composite Network Model, including hierarchical layers as appropriate (as detailed in Chapter 1), for this case study design. The three functional areas of the model are Enterprise Campus, Enterprise Edge, and Service Provider Edge. Each of these functional areas can be further divided into various modules, as illustrated in Figure 12-1. Each of the modules can include the hierarchical core, distribution, and access layer functionality. Figure 12-1. Modules of the Enterprise Composite Network Model[1]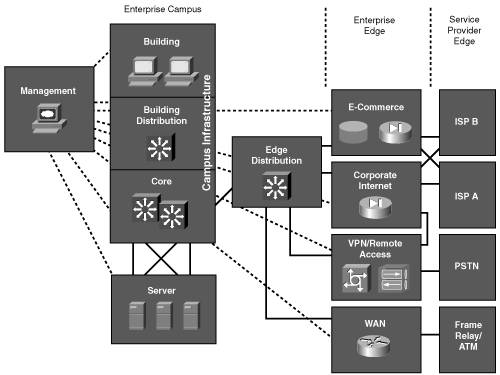 Venti Systems has no e-commerce, and communication between offices and remote users will be through virtual private networks (VPNs) over the Internet. We therefore do not include the e-commerce, WAN, or Frame Relay/Asynchronous Transfer Mode (ATM) modules. The following sections provide the design models for the head office (in Toronto), branch office (in Seattle), and remote users (including the international sales personnel). Following those sections is a description of the users' devices and the servers. Head OfficeThe new Toronto office will initially have one building, with an option to acquire a second building. Up to 185 people will be at this location within 18 months, and IP telephony is to be used for all internal calls. Redundancy is required, both at the infrastructure level and for some servers. VPN connectivity to the Seattle office and for remote users is to be used and wireless connectivity within the building is to be implemented. Enterprise CampusThe Campus Infrastructure and Server modules of the Enterprise Campus for the head office are illustrated in Figure 12-2. Figure 12-2. Part of the Venti Systems Head-Office Enterprise Campus Note IP phones and wireless access points are shown in Figure 12-2; the details of how these technologies are integrated within the network are described in the "QoS and Voice" and "Wireless" sections, respectively, later in this chapter. The Management module is described in the "Network Management" section, later in this chapter. The Campus Infrastructure module includes Layer 2 access switches for connectivity between the end-users' laptops and IP phones and the rest of the network. These switches provide inline power for the IP phones as well as user authentication and quality of service (QoS) marking. Redundancy for the laptops is provided through their wireless connections. The collapsed backbone combines the Building Distribution and Core functionality in Layer 3 switches. Routing, route filtering, route summarization, and filtering are performed here. Redundancy to the Building access switches, to the Server access switches, to the Edge Distribution module, and to the Management module is provided to ensure a highly available and reliable backbone. The centralized Server module contains the internal servers, including e-mail and file servers, and Cisco CallManager (CCM) servers for IP telephony. Redundancy is implemented to the collapsed backbone so that users always have access to the servers they need. Layer 2 access switches are used in this module to connect to the collapsed backbone. The Edge Distribution module, shown as part of Figure 12-3, is the interface between the Enterprise Campus (through the Core) and the Enterprise Edge functional areas. This module uses Layer 3 switching to provide high-performance routing; redundancy is also implemented to ensure that campus users always have access to the Enterprise Edge. Figure 12-3. Venti Systems' Enterprise Collapsed Edge: Corporate Internet, VPN Access, and PSTN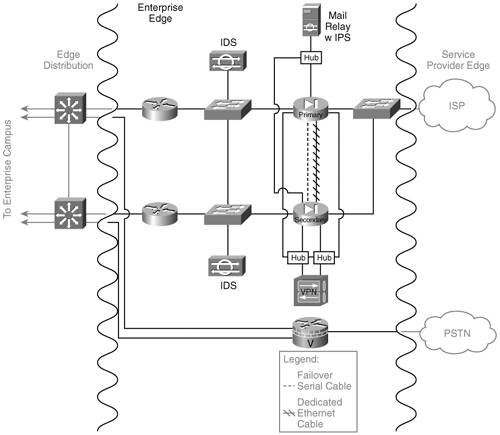 Note Figure 12-3 shows the physical network topology, including redundant devices and connections. Subsequent figures might show the logical topology, without the redundancy, for ease of understanding concepts. Enterprise Edge and Service Provider EdgeThe modules of the Enterprise Edge and Service Provider Edge for Venti Systems' head office are also shown as part of Figure 12-3. The Enterprise Edge's VPN/Remote Access module is collapsed into the Corporate Internet module because all external traffic will be converging from the Internet to the head office. The Corporate Internet module provides Internet access for the users (and usually passes VPN traffic from remote users to the VPN/Remote Access module). This module includes an e-mail relay server (as detailed in the "E-Mail" section, later in this chapter). Security systems include firewalls and intrusion detection systems (IDSs) to ensure that only legitimate Internet traffic is allowed into the enterprise. (Security is described further in the "Security" section, later in the chapter.) The Domain Name Service (DNS) of the Internet service provider (ISP) will be used. A VPN/Remote Access module usually terminates VPN traffic from external users. Devices in this module include VPN concentrators to terminate the remote user connections, and firewalls and IDS appliances to provide security. In our Venti Systems design, this functionality is collapsed with the Corporate Internet module. A VPN concentrator is attached behind the redundant firewalls to initiate and terminate VPN tunnels to and from the branch office and remote users. The ISP module represents the connection to the Internet. Venti Systems connects to the ISP through a digital subscriber line (DSL) connection. A backup Internet connection is not initially required, because no mission-critical applications are running over the Internet, and the additional cost and complexity are not deemed necessary at this time. Venti Systems will negotiate with its ISP a comprehensive service-level agreement (SLA), including availability above 99.997 percent. The public switched telephone network (PSTN) module is shown in Figure 12-3 because all external calls will be through the PSTN, not through IP telephony. Recall, though, that remote users will not dial in; rather, they will connect through a VPN, so PSTN access is not required for dial-in functionality. As is common for enterprises, PSTN redundancy is not required. Venti Systems will negotiate with its PSTN provider a comprehensive SLA, including a 99.999 percent availability. Branch OfficeAs indicated in Chapter 11, few changes are required to the network in the Seattle office because the work done there is not information-intensive. The Seattle office originally outsourced its Internet connectivity, telephone, and e-mail services. E-mail will be accessed using the server at the Toronto office, through the VPN connection. Internet connectivity will be through DSL. The Seattle office will remain Layer 2 switched only because of the small number of people and the simplicity of the network. The office will connect to the Internet through the Cisco 2514 router that was decommissioned from Toronto and on which the Internet Operating System (IOS) will be upgraded to the latest IOS firewall feature set (at least to Release 12.2[29]). This router will be then able to route traffic and to terminate VPN tunnels. Figure 12-4 illustrates the network at the Seattle office. Figure 12-4. Seattle Office Network: A Router with Integrated Firewall Will Provide VPN Access to the Head Office As also shown in Figure 12-4, the Seattle office will get a new private branch exchange (PBX) (from the old Grandics Corporation office); IP telephony will not be implemented at this time. Remote UsersAll remote users will access the network through a VPN connection to the Toronto office. All employees, in all offices, who need a computer will be given a wireless-enabled laptop; all of these laptops will be from the same vendor, running the same operating system, with a standard suite of programs installed. (Existing desktop PCs and any laptops that are not compatible with the new standard will be replaced.) The laptops will be configured with VPN client software that provides connectivity to the head office. A significant advantage of running a software VPN client is that the encrypted tunnel originates from the laptop so that the data traveling on the home-area network (HAN) toward the head office is encrypted, making the transmission safer. A typical connection from a remote user is illustrated in Figure 12-5. Figure 12-5. Typical Remote User Connection The users' laptops are as described in the following section. User DevicesAll users' laptops will have the following features:
ServersAll servers will include management software so that they can be remotely managed. The servers will also be equipped with intrusion prevention system (IPS) software. The internal e-mail, finance, and computer-aided design/computer-aided manufacturing (CAD/CAM) file servers will be installed as clusters. As its name implies, a cluster is a group of identical servers interconnected and accessible as a common storage pool. Clustering prevents the failure of a single file server from denying access to data. Should Venti Systems grow, an additional benefit of clustering is that it adds computing power to the network for large numbers of users. The financial and other business applications used in the three offices will be standardized to use Venti Systems' applications. The data from the systems in the other offices needs to be converted and incorporated into the new system; a task force will be created for each application to be responsible for migrating the data and integrating the systems. |
EAN: 2147483647
Pages: 156