Network Arrangements and Technologies
Network Arrangements and Technologies
Wireless technology has been around since the days before radios became popular. The astronauts in a space shuttle communicate to mission control without wires, just as a cordless phone allows people anywhere on the globe to communicate without the burden of wires tying them to a fixed location. Wireless technologies as defined in this text, however, are newer and more sophisticated, operating at higher speeds and conforming to different standards. In this text we introduce three types of wireless technologies:
802.11b
The Wireless Application Protocol (WAP)
Bluetooth
Some wireless technologies are standards-based wireless transport protocols, some are application protocols, and some are both, but all are technologies. They represent a broad range of technologies, and continually evolving ones at that. It is essential to realize that the only appropriate way to secure a system is to investigate it thoroughly. This book does so with the technologies presented, but its goal is to teach the method for doing so, not to provide answers that will be pervasive in their details throughout the next thirty years. The methods taught here for analyzing a system are invaluable and are tailored specifically to wireless systems. They should be further customized as standards, protocols, and technologies change in the future. Each technology is discussed in much greater detail in Chapter 3, "Technologies."
To place the technologies in appropriate contexts, we will simultaneously examine different network arrangements typically used in wireless systems:
Personal area networks (PANs)
Local area networks (LANs)
Wide area networks (WANs)
The technologies discussed here cross all three network arrangements, but some are more closely associated with one. The discussion of wireless LANs comprises the bulk of this section because it is the most commonly seen implementation of a wireless network for most home and office environments. In the discussion of PANs, it is best to focus on Bluetooth technology. In the discussions of WANs and LANs, it is best to discuss a combination of 802.11b and WAP. These technologies cover different layers of the architecture of each type of network.
802.11b
The most comprehensive technology examined here, 802.11b is a standard developed by the Institute for Electronics and Electrical Engineers (IEEE). 802.11b is the IEEE standard for wireless communications in its revised form, which includes higher communication rates. At the time of the writing of this book, industry analysts indicate that it may be the technology that outlasts the rest and prospers long into the future. (Our opinion is that this may well be true, but parts of the other technologies examined may likely be incorporated into whichever one surfaces as the front-runner for the long term. Furthermore, 802.11b will need to be accompanied by a strict security design paradigm to constitute a viable "total" solution.)
802.11b is backwards compatible with its predecessor, 802.11, and lays out a standard for wireless communication that offers technical specifications about architecture and services, as well as design implementation guidelines. The specifications define components and network configurations and describe the relevant layers of the International Standard Organization's (ISO) Open System Interconnect (OSI) reference model, as well as security implications. Although it may be touted as the most versatile and robust wireless standard that is emerging, 802.11 has been found to have significant problems.
Two reports released in the early part of 2001 unveiled some holes in 802.11 networks. The reports, from the University of California, Berkeley, and the University of Maryland, examined the components of the 802.11 system that attempt to mirror a wired system in terms of security. The examinations led to discoveries of distinct problems and, intentionally or unintentionally, were followed by a steady stream of articles pointing to other insecure measures in the system. Two hundred dollars worth of equipment from Radio Shack was all it took two wily individuals to compromise countless wireless networks in the San Francisco Bay area. These discoveries do not necessarily point to the demise of the technology but rather the need for application security on top of easily implemented networks to bolster weak security measures that come out of the package with these systems.
The Wireless Application Protocol (WAP)
WAP operates at a higher level than transmission protocols such as 802.11b. It provides a protocol used to implement communications in an architecture that requires a gateway to provide the translations between wireless and wired communication. WAP has faced much criticism since its emergence but is currently the leader in cell phone wireless configurations in the United States. WAP browsers, WAP-enabled phones, and WAP development are en vogue, especially in Europe.
WAP includes specifications for application environments, transmission, and session handling, as well as security functionality. In its transport layer, WAP includes a wireless version of Secure Socket Layer (SSL) called Wireless Transport Layer Security (WTLS). WTLS helps secure communication from wireless devices through bearers to WAP gateways (see Figure 1.4). The problem starts at this point. The gateway is a place where the secure communication is vulnerable because the gateway has to translate to communication configured to the standards of the wired Internet. WAP receives its biggest criticism from this. It does not provide end-to-end security and opens holes. WAP specifications use a special language for development of Web pages readable by small devices that communicate on high-latency, low-speed networks.
Figure 1.4. WAP architecture
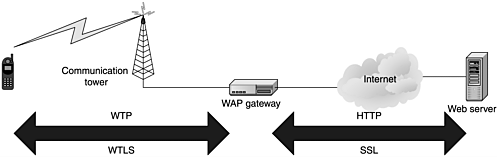
Wireless Wide Area Networks
Both 802.11b and WAP are used in varying network arrangements. (For the purposes of this text, when referring to a network as wide area network, we mean wireless wide area network. When referring to a WAN connected via wires, we call it a wired WAN. The exception to this is that we employ the acronym WLAN for wireless LANs because this size network is discussed more frequently throughout the book and we want to be clear.) WANs are typically used in the cases of service providers, not corporate or home networks. Loosely, WANs enable devices to connect via wireless technologies and protocols to the Internet, an intranet, or an e-mail system. Depending on the connecting entity, WANs are administered by Internet service providers (ISPs), application providers, or corporations.
WANs are expanding to provide wireless coverage for more areas of the world. Most major cities enjoy WAN service, but rural and less developed areas have not yet seen the benefits of WAN. Remote or underdeveloped areas without wired WANs can benefit from the resources that Internet access brings to an area: infrastructure, communication, necessary supplies, and aid. Also, these great improvements can be realized without the need for costly infrastructure (that is, fiber optic cable) being laid over great distances. Certainly, some cost is involved in implementing a WAN solution to areas with limited resources, but the cost is less than that of wired WAN solutions.
Local Area Networks
A wireless local area network (WLAN) is an electronic data communications system providing an extension, or alternative, to a wired LAN. WLANs use a variety of communication mechanisms to replace the traditional cables and wires of a LAN. In a traditional LAN, data is transmitted as electronic pulses or signals along a physical wire or carrier. Some systems have a continuous signal or carrier running on the wire, such as a tone on the phone line, and the data is superimposed or modulated onto the carrier signal. In a simplified example of the phone, the transmitter makes slight variations to the tone frequency, and the receiver is then set to detect these variations and retrieve the transmitted data. Similarly, in a WLAN, there are transmitters, receivers, and a carrier on which data is modulated.
Currently, two general mechanisms are being employed as the data carrier in WLANs: radio frequency (RF) and infrared (IR). Both mechanisms allow for the trans-mittal and reception of electronic data through the air, minimizing the need for cable and wire connectivity between devices. Several RF technologies are being utilized, and two IR technologies for WLANs. The technologies are Narrowband Technology, Spread Spectrum Technology, Frequency-Hopping Spread Spectrum Technology, Direct-Sequence Spread Spectrum Technology, Direct Infrared Technology, and Diffuse Infrared Technology.
Personal Area Networks and Bluetooth
PANs are networks that focus around an individual. Loosely, a PAN could comprise a cell phone in someone's shirt pocket, his PDA, and his wireless-enabled laptop (see Figure 1.5). The three devices would communicate among one another, forming an ad hoc PAN. The cell phone could dial in to his ISP, offering Internet connectivity to both the PDA and the laptop. The laptop could then send a *.pdf document to the PDA, and the cell phone could disconnect. Each component of the PAN serves a unique purpose, requiring that the three function together to form an intelligent network, but by distributing tasks and functionality, not requiring one heavy cumbersome device.
Figure 1.5. A personal area network (PAN)
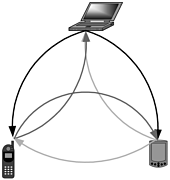
The technology that might make this possible is Bluetooth. Bluetooth is a once highly acclaimed technology that has suffered great setbacks. The intention of its major contributors was to develop a standard so that wireless devices could interoperate easily and cheaply in a short-range distance. Adding Bluetooth to a device was supposed to add about five dollars to its cost. Estimates have been off, though, and it is actually costing manufacturers closer to thirty dollars to build the technology into their devices. Perhaps bad luck, perhaps a fortuitous omen, at a conference in April 2001, Bluetooth supporters intended to set a record and have the largest number of Bluetooth users connected at the same time. Not only did they fail to reach their record numbers, but also, because of a system failure, none were able to connect.
Despite setbacks and more than a 30-month delay in mass deployment, Bluetooth slowly gains ground, and developers have yet to abandon it. Bluetooth differs from 802.11b in several ways:
It can only connect devices within 10 meters of each other.
It operates similarly to InfraRed Data Assocation (IrDA).
Its goal is for devices to form networks among each other quickly and easily.
The security ramifications of this are phenomenal. Security is not built in to devices as far as connection capability is concerned. It is left to application developers and, perhaps even scarier, users.
Wireless LAN Appeal
Now that we have introduced a few technologies and network arrangements, there is a question begging to be answered: Why use a wireless LAN? Four main factors describe the appeal of a wireless LAN: mobility, flexibility, cost, and scalability.
Mobility
WLANs can provide users with access to public and private network resources from anywhere within the coverage area. The coverage area may vary quite a bit, depending on the system being used. Some large commercial wireless access providers provide Internet access to large coverage areas. The BellSouth Network and Mobitex cover entire metropolitan areas in most of the United States. We concentrate here on corporate and on home or private wireless networks.
Flexibility
WLANs allow connectivity where running additional cables or wires may be unfeasible or cost-prohibitive. WLANs also allow the configuration or location of the terminals to be tied no longer to the network access; users can rearrange office areas at will and remain connected to the network. Home owners or renters benefit from this flexibility by not having to run network lines throughout a house or an apartment. Yet, they still have access to centralized printers or high-speed Internet access points such as Inte-grated Service Digital Network (ISDN) or a cable modem. These devices can remain wherever they have been installed, and the user's computer can be moved anywhere in the house and still retain access.
Cost
Although the initial cost of WLAN equipment is currently higher than conventional LAN equipment, the cost in installations that are fluid, or temporary and frequently changing, is soon recuperated in rewiring and time.
Scalability
WLAN technologies can be configured in varying topologies to meet the needs of the specific application or installation. These topology configurations are easily changed; new devices or users can be added without affecting existing users or devices. This is truer for some technologies than others, but in general, WLAN technologies are more readily scalable than their LAN counterparts.
EAN: 2147483647
Pages: 73