Lesson 1: Working with Computer Certificates
Lesson 1: Working with Computer Certificates
Windows 2000 uses computer certificates to bind the identity of a computer to a public/private key pair. This key pair can subsequently be used for a myriad of security purposes, such as creating an Internet Protocol Security connection to another computer or proving the computer's identity.
After this lesson, you will be able to
-
Understand the purpose and function of computer certificates
-
Deploy computer certificates
Estimated lesson time: 30 minutes
Understanding the Purpose of Computer Certificates
Computer certificates are used for five primary purposes in Windows 2000:
-
Internet Protocol Security (IPSec) encrypts data flowing between two computers in the same domain.
Computer certificates are required to establish IPSec communication between Windows 2000 computers. Read more about IPSec in Chapter 8, "IP Security."
-
Layer 2 Tunneling Protocol (L2TP) encrypts data flowing between computers based on user authentication and allows users to log on securely from remote locations. L2TP is the subject of Chapter 9, "Remote Access and VPN."
-
Secure Sockets Layer (SSL) encrypts data flowing between computers that have not otherwise agreed to trust one another. SSL does not provide identity of the user or machine, but does encrypt the connection between them. SSL is covered in Chapter 12, "Web Service Security."
-
Smart card log on validates the identity of users, and stores the secret keys used to encrypt their data.
-
Secure/Multipurpose Internet Mail Extensions (S/MIME) encrypts e-mail messages when they are created, and provides a mechanism to exchange encryption keys between e-mail users.
Identifying How a Certificate Is Used
Windows 2000 CAs create X.509v3 certificates. X.509v3 is a format that specifies how information in a certificate is organized, and it provides enough detail so that software from different vendors can create, manage, and use certificates from any source if they contain the correct type of information for the application.
Multiple types of certificates exist because each type of application requires specific information within a certificate. When a certificate contains information that pertains to more than one application, the certificate can be used for each of those applications. The following are some examples of applications and their specific requirements for certificates:
-
Some applications, such as a code signature verifier, might require only that a certificate contain identity information and be digitally signed by a CA that the applications are configured to trust.
A code signature is a digital signature appended to a program that guarantees that the program has not been modified when in transit between the vendor and the end user.
-
Other applications, such as a smart card logon suite, might require access to a public or private key embedded within the certificate. Smart cards are the subject of Lesson 3 in this chapter.
-
Some applications might require specific information in the identity portion of the certificate that other applications do not need. For example, an e-mail client might require that the user's e-mail address appear in the certificate, while a file encryption package would have no use for that information.
Using Certificate Templates
Windows 2000 CAs create certificates specifically for applications, depending on the requirements of the application. These applications select a standard certificate template to ensure that the information they require will be embedded within the certificate. A certificate template is a file that specifies exactly what information is required by the application that is requesting the certificate. Figure 6.1 shows the general information for a specific certificate.
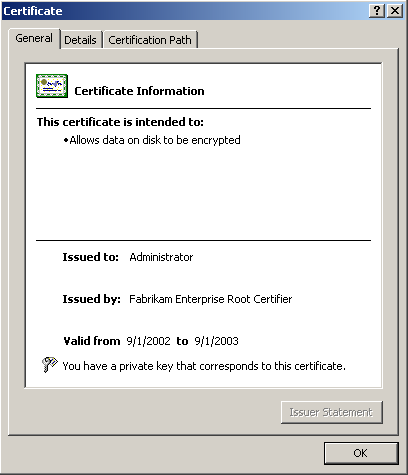
Figure 6-1. A certificate's information
For example, the Encrypting File System (EFS), which encrypts files in Windows 2000, requests certificates by specifying the file encryption certificate template. This guarantees that the proper information has been provided by the client (or the request will be rejected) in order for the CA to create a certificate that will be compatible with the EFS encryption service.
Most often, you will request certificates using the certificate templates listed in Table 6.1, which are built into Windows 2000. Other templates exist that are used automatically by various services; you will not need to administer those templates.
| Template name | Purpose |
| Computer | IPSec, L2TP, SSL |
| User | Authentication, e-mail security, file encryption |
| EFS | File encryption |
| S/MIME | E-mail security |
| Smart card logon | Log on through smart cards |
| Smart card user | Authentication, e-mail security, and file encryption through smart card |
| Enrollment agent | Authorization of administrators to sign smart card certificates |
| Subordinate CA | Authorization of a CA to issue certificates within a trust hierarchy |
Deploying Computer Certificates
There are two ways to deploy computer certificates:
-
Manually on an individual computer
-
Automatically on a domain or organizational unit (OU)
Manual Deployment
Deploy computer certificates manually when you need to deploy only a few certificates for a specific purpose, such as establishing an IPSec link between two computers, and you don't want to incur the planning or network overhead of automatic deployment.
To perform a manual deployment, you create a Certificates management console (Figure 6.2) on the computer for which you want to create the certificate, and specify that the console be used to manage computer certificates. The exercises in this lesson show you exactly how to do this. You then request the computer certificate. The CA issues the certificate, and your Certificates management console installs it.
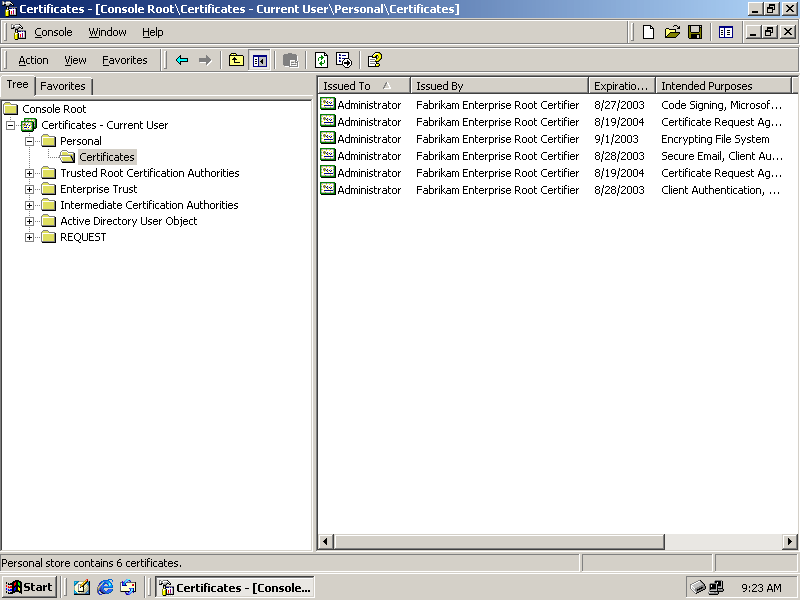
Figure 6-2. The Certificates management console
Automated Deployment
Deploy computer certificates automatically when you want to deploy certificates to large groups of computers. Automatic computer certificate deployment works very well so well, in fact, that you need to plan for the additional network and computer load that will occur when computers throughout your domain or OU simultaneously request certificates.
To deploy certificates automatically, establish a Group Policy setting in a Group Policy Object (GPO) that is linked to the container holding the computers to which you want to deploy certificates. At the Group Policy refresh interval, the automatic certificate request policy is applied to the computers, and the computers will request certificates from the enterprise CA configured in the policy.
In general, you should have a CA for every 100 to 1000 computers that will be requesting certificates, depending on how much noticeable load you are willing to let your users see. If you postpone your deployment to a non-work time such as a weekend, you might be able to deploy 10,000 to 100,000 certificates from a single CA. Apply the policy changes at the end of the workday on Friday, and let the CA issue certificates throughout the weekend.
While deployment is usually performed at a domain level, you can load-schedule the deployment by creating an OU designed solely for certificate deployment. Create the OU as a subordinate to the domain, and then move computers into the OU in batches. Once they've gone through a Group Policy refresh interval, they will request and install the certificates automatically. You can then move the computer objects back to their original OUs and move a new batch in.
Be certain that you aren't obviating any important GPO settings by moving computers you should always make your certificate deployment OU a subordinate to the OU that contains computers to ensure that you aren't accidentally removing settings.

In this practice, you use two different methods to deploy computer certificates: manually on a per-computer basis, and automatically through Group Policy to all computers within the Active Directory container.
Exercise 1: Deploying Computer Certificates Manually
In this exercise, you create a Certificates management console and manually request a computer certificate for a specific computer. Perform this exercise on a Windows 2000 Professional workstation joined to the domain.
To create a Certificates management console
-
Log on as a domain administrator.
-
Click Start, and then click Run. The Run dialog box appears.
-
Type mmc, and click OK. An empty management console window will appear.
-
From the Console menu, choose Add/Remove Snap-In. The Add/Remove Snap-in dialog box appears.
-
Click Add. The Add Standalone Snap-in dialog box appears with a list of snap-ins.
-
Double-click certificates. The Certificates Snap-in Wizard appears with a list of the types of certificates that the snap-in can manage.
-
Select Computer Account, and click Next. The Select Computer Wizard page now asks which computer you would like to manage.
-
Select Local Computer, and click Finish.
-
Click Close to close the Add Standalone Snap-in dialog box. The Certificates snap-in is now in the Add/Remove Snap-ins list box.
-
Click OK to close the Add/Remove Snap-in dialog box.
-
From the Console menu, choose Save. The Save As dialog box appears.
-
Type Certificates in the File Name box, and click Save.
A Certificates management console now appears in the Administrative Tools folder of the Start menu.
To request a certificate
-
From the Certificates management console that you created in the first procedure, expand the Certificates Snap-in.
-
Right-click the Personal folder, click All Tasks, and select Request New Certificate. The Certificate Request Wizard appears.
-
Click Next. The Certificate Template dialog box appears. Computer is the only option.
-
Click Next to view the dialog box for the certificate-friendly name and description, as shown in Figure 6.3.
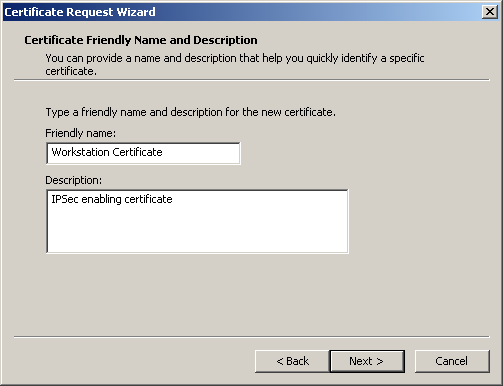
Figure 6-3. The Certificate Request Wizard
-
Type Workstation Certificate as the Friendly Name for the certificate.
-
Type IPSec enabling certificate as the Description for the certificate.
-
Click Next, and then click Finish. A message box appears indicating that the certificate request was successful.
-
Click OK to acknowledge that the certificate request was successful.
-
Click the Certificates folder under the Personal folder. The certificates contained within this folder appear in the leftmost panel of the screen.
-
Double-click the CLIENT01.domain.Fabrikam.com certificate to view the certificate information. The window that appears will be similar to the window shown in Figure 6.1.
Exercise 2: Deploying Computer Certificates Through Group Policy
In this exercise, you configure Group Policy to automatically deploy computer certificates to computers when they are booted or at the next Group Policy update interval.
To configure domain security policy for automatic computer certificate deployment
-
Click Start, point to Programs, point to Administrative Tools, and click Active Directory Users And Computers. The Active Directory Users And Computers management console appears.
-
Right-click domain.fabrikam.com in the domain tree, and click Properties. The domain.fabrikam.com Properties dialog box appears.
-
Click Group Policy.
-
Double-click Domain Security Policy. The Group Policy editor appears with the Domain Security Policy open.
-
Expand Domain Security Policy, Computer Configuration, Windows Settings, Security Settings, and Public Key Policies.
-
Right-click Automatic Certificates Request Settings, point to New, and click Automatic Certificate Request, as shown in Figure 6.4. The Automatic Certificate Request Setup Wizard appears.
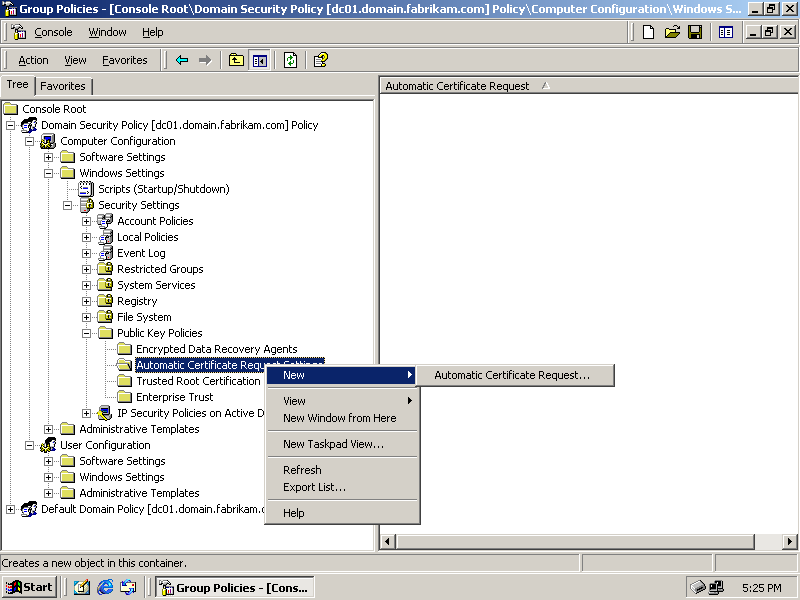
Figure 6-4. The Group Policy editor showing the Public Key Policies container
-
Click Next. The Certificate Template page appears, as shown in Figure 6.5.
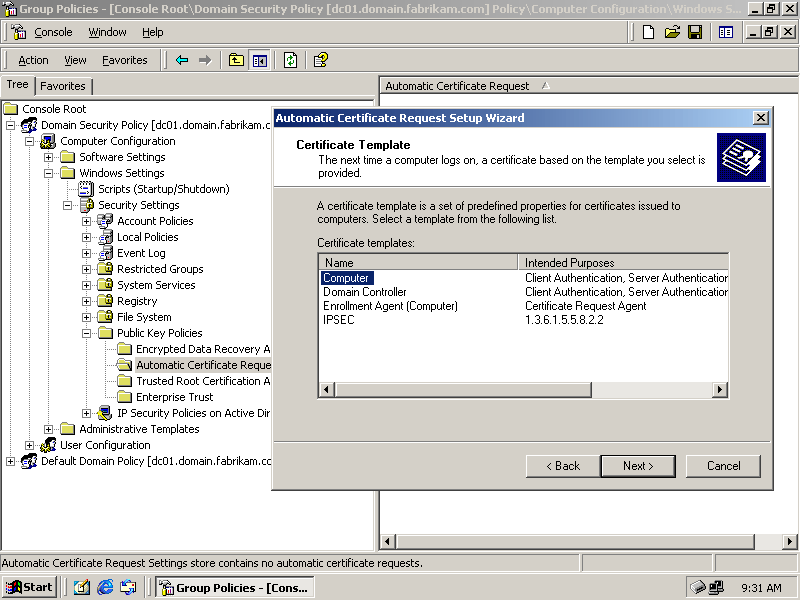
Figure 6-5. The Automatic Certificate Request Setup Wizard
-
Select the Computer template, and click Next. The Certification Authority page appears, with Fabrikam Enterprise Root Certifier selected.
-
Click Next, and then click Finish.
-
Close the Group Policy editor window.
-
Click OK to close the domain.fabrikam.com Properties dialog box.
-
Close the Active Directory Users And Computers management console.
To verify certificate deployment
Perform this procedure on a Windows 2000 Professional workstation joined to the domain.
-
Restart the client computer.
-
Log on and open the Certificates management console.
-
Verify that the new certificate is listed under the Personal Certificates folder.
To verify certificate deployment at the CA
-
On the domain controller, open the Certification Authority management console.
-
Expand Fabrikam Enterprise Root Certifier, and select Issued Certificates. A list of all certificates issued by the CA appears in the management console, as shown in Figure 6.6.
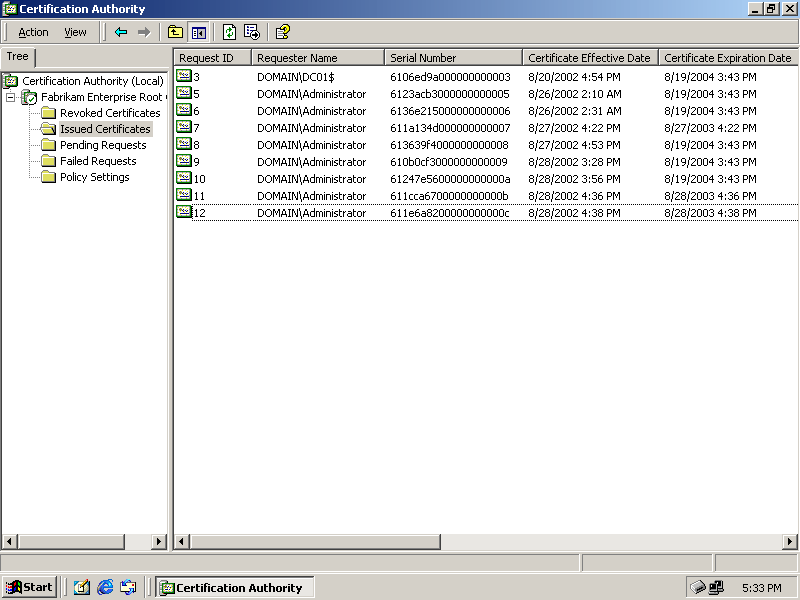
Figure 6-6. The list of certificates issued by a CA
-
Double-click the most recently issued certificate to view the certificate information, as shown in Figure 6.7. This is the certificate automatically issued to the client computer.
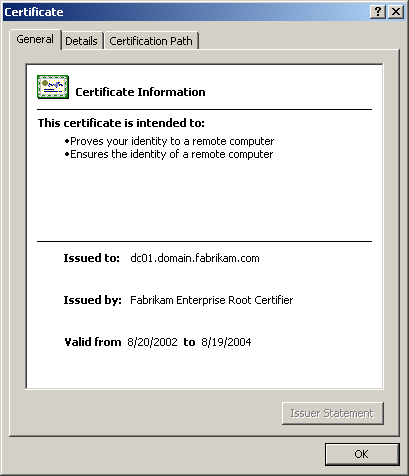
Figure 6-7. Verifying the deployment of a certificate

The following questions are intended to reinforce key information in this lesson. If you are unable to answer a question, review the lesson and try the question again. Answers to the questions can be found in the appendix.
-
What is the primary purpose for computer certificates in Windows 2000?
-
When would you choose to use manual computer certificate deployment?
-
When would you choose to use automatic computer certificate deployment?
-
What tool do you use to perform manual deployment?
-
What tool do you use to perform automatic deployment?
Lesson Summary
-
Computer certificates are used to perform network link encryption between computers. Depending on the circumstance, computer certificates can be used to perform IPSec, L2TP, and SSL encryption.
-
Computer certificates can be manually deployed by using the Certificates management console on the computer that requires the certificate.
-
Computer certificates can be automatically deployed using Group Policy to computers within a Group Policy container such as a domain or an OU.
You must take special precautions to avoid overloading the certificate authority when you deploy computer certificates automatically, because all computers in the container will request certificates more or less simultaneously. Either perform the deployment when the CA has plenty of time to respond to requests or use subordinate OUs to isolate computers into smaller groups so that certificates can be deployed in batches.
EAN: 2147483647
Pages: 82
- An Emerging Strategy for E-Business IT Governance
- Measuring and Managing E-Business Initiatives Through the Balanced Scorecard
- Technical Issues Related to IT Governance Tactics: Product Metrics, Measurements and Process Control
- Governance in IT Outsourcing Partnerships
- The Evolution of IT Governance at NB Power