Managing and Troubleshooting Connectivity Across Firewalls
| < Day Day Up > |
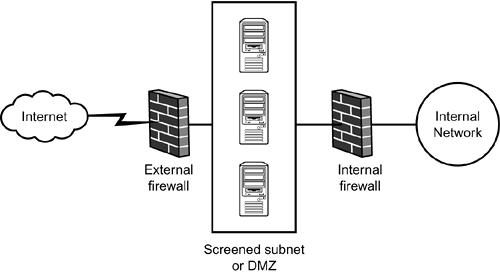
| Almost all organizations protect their network with at least one, quite often two, firewalls, as shown in Figure 9.1. At its most basic, a firewall is a system that is used to control which traffic does and does not pass from the public Internet to the organization's private network. Some networks are configured with a screened subnet or demilitarized zone (DMZ). A DMZ is a network that is located between an external firewall and an internal firewall. Both firewalls are configured so that all traffic must pass through the screened subnet and can never pass directly, even though it is filtered, from the Internet to the internal network. Figure 9.1. A basic screened subnet or DMZ bounded by an external firewall connected to the Internet and an internal firewall connected to the internal network.
The DMZ is where you are likely to locate a Simple Mail Transfer Protocol (SMTP) server, proxy servers, and, in some cases, Exchange front-end or Outlook Web Access (OWA) servers. An important part of the 70-284 exam is being able to correctly describe how to configure a firewall to allow the types of communication necessary for Exchange to work, without letting unnecessary traffic through that might compromise the security of the network. This description often takes the form of identifying which ports should be opened on a particular firewall. Differentiating Traffic on the Basis of PortTCP/IP traffic is differentiated by the port it uses. Different network application protocols use different ports. Hypertext Transfer Protocol (HTTP) traffic, for example, which is used to carry Web traffic, uses port 80. SMTP traffic uses port 25, and Post Office Protocol version 3 (POP3) traffic uses port 110. Thousands of ports have been configured to support different application protocols. At their most basic levels, firewalls allow and deny traffic based on the port that the traffic uses and the source and destination addresses.
The important ports that are used by Exchange Server 2003 are listed in Table 9.1.
Only Allowing Access to Front-end Servers via Secure Sockets Layer (SSL)One of the first steps you need to take in securing a server that communicates with hosts on the Internet is ensuring that the protocols used to communicate with that server are as secure as possible. Rather than allowing insecure and secure versions of the same protocol to pass via the external firewall, administrators should only allow access to SSL-protected protocols to an Exchange Server 2003 front-end server located on the DMZ. The downside to using this method is that the front-end server will experience increased processor load in handling and decrypting the SSL traffic. Although it is possible to purchase SSL accelerator cards, this is an additional infrastructure expense. One port that Exchange communicates via should not be blocked, even though transmissions occur via this port in an insecure fashion. Port 25, used by SMTP, transmits and receives messages from other email servers located on the Internet. To retain interoperability with SMTP servers outside the organization (as they do not share the same SSL certificates), this external communication should not be encrypted in this manner. To use SSL, you require an SSL certificate. Obtaining a certificate for securing internal SMTP traffic via SSL is relatively simple if you have an enterprise root CA. If you do not have an enterprise root CA, you need to use the Certificate Request Wizard and submit the generated file to your CA. After you have the required SSL certificate installed, you can enable secure communication by editing the properties of the SMTP virtual server. Smart HostsSmart hosts present an alternative to placing an Exchange Server 2003 computer on the DMZ. You would use a smart host rather than an Exchange Server 2003 front-end server when you do not need to provide mail services to users located on the Internet side of the external firewall. A smart host is a Windows 2000 Server or Windows Server 2003 server that is configured as an SMTP relay. An SMTP relay simply relays messages to and from the Internet to the internal network. A smart relay has no knowledge of AD and does not require Exchange Server to be installed. When a smart relay is installed, the only port that needs to be opened is port 25 on the external firewall and port 25 on the internal firewall. Connecting MAPI Clients to Exchange Server 2003 Through a FirewallThe situation will arise in which you have Messaging Application Programming Interface (MAPI) clients located on the Internet, with the firewall between them and the Exchange Server 2003 server, who need to access data on that server. As an administrator, you must find a balance between allowing access and keeping the internal network secure. You have several options available for giving remote users access to Exchange. These include
External Firewall ConfigurationIf you want to allow remote clients on the Internet to access the Exchange servers via POP3 or IMAP, you need to install an Exchange front-end server on the DMZ and make the following configuration settings:
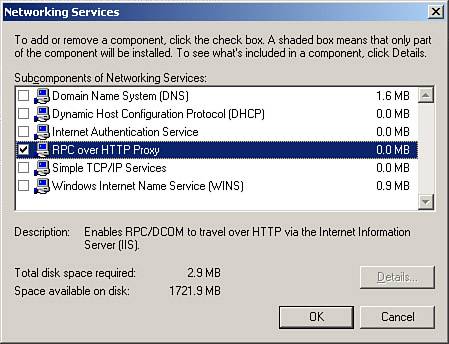
Secure traffic comes through the firewall to the Exchange front-end server. Front-end servers do not host mailboxes or public information stores and are located on the DMZ. The internal firewall is configured so that the front-end server is able to communicate normally with back-end servers located on the internal network. We discuss front-end and back-end server configuration further in Chapter 6, "Managing, Monitoring, and Troubleshooting the Exchange Organization." RPC over HTTPRPC over HTTP is Microsoft's new preferred technology for allowing external MAPI clients to access the internal Exchange infrastructure. RPC over HTTP is a technology that allows an Outlook 2003 MAPI client to communicate with an Exchange Server 2003 system hosted on a Windows Server 2003 computer via port 80. An Exchange Server 2003 front-end server that does not host any mailboxes or public information stores is located on the DMZ. You can then specify which ports are used to communicate with the domain controller (DC), global catalog (GC), and Exchange servers that the RPC client will access. Alternatively, if ISA Server is installed, it can route RPC over HTTP, in which case the RPC proxy server can use all of the ports it requires. To prepare an Exchange Server 2003 computer to support RPC over HTTP:
The advantage of RPC over HTTP is that only port 80 needs to be opened on the firewall. The disadvantage is that it is limited to Outlook 2003. If older Outlook clients must be supported, this technology cannot be implemented. Integrating ISA Server 2000 with Exchange Server 2003Exchange Server 2003, unlike Exchange 2000 Server, is designed to work closely with ISA Server 2000, the Microsoft firewall and proxy product. ISA Server 2000 can be configured so that Exchange front-end servers are no longer required on the screened subnet. To perform this function, ISA Server 2000 must be patched with Service Pack 1. The ISA Server 2000 Feature Pack 1 must also be installed. An ISA server located on the screened subnet can process the following kinds of traffic from the Internet to the internal network:
ISA Server also checks the data for any malicious traffic before forwarding it to the appropriate Exchange server on the internal network. To perform these functions, ISA Server 2000 does not need to be hosted on a computer that is a member of the domain. This provides greater security because if the ISA Server 2000 computer is compromised, the attacker does not have domain access.
|
| < Day Day Up > |
EAN: 2147483647
Pages: 171