Cryptography: Theory and Practice:The Data Encryption Standard
 | Cryptography: Theory and Practice by Douglas Stinson CRC Press, CRC Press LLC ISBN: 0849385210 Pub Date: 03/17/95 |
| Previous | Table of Contents | Next |
Chapter 3
The Data Encryption Standard
3.1 Introduction
On May 15, 1973, the National Bureau of Standards published a solicitation for cryptosystems in the Federal Register. This lead ultimately to the development of the Data Encryption Standard, or DES, which has become the most widely used cryptosystem in the world. DES was developed at IBM, as a modification of an earlier system known as LUCIFER. DES was first published in the Federal Register of March 17, 1975. After a considerable amount of public discussion, DES was adopted as a standard for “unclassified” applications on January 15, 1977. DES has been reviewed by the National Bureau of Standards (approximately) every five years since its adoption. Its most recent renewal was in January 1994, when it was renewed until 1998. It is anticipated that it will not remain a standard past 1998.
3.2 Description of DES
A complete description of DES is given in the Federal Information Processing Standards Publication 46, dated January 15, 1977. DES encrypts a plaintext bitstring x of length 64 using a key K which is a bitstring of length 56, obtaining a ciphertext bitstring which is again a bitstring of length 64. We first give a “high-level” description of the system.
The algorithm proceeds in three stages:
- 1. Given a plaintext x, a bitstring x0 is constructed by permuting the bits of x according to a (fixed) initial permutation IP. We write x0 = IP (x) = L0R0, where L0 comprises the first 32 bits of x0 and R0 the last 32 bits.
- 2. 16 iterations of a certain function are then computed. We compute LiRi,
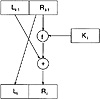
Figure 3.1 One round of DES encryption1 ≤ i ≤ 16, according to the following rule:
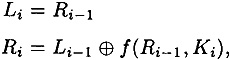
where ⊕ denotes the exclusive-or of two bitstrings. f is a function that we will describe later, and K1, K2, . . . , K16 are each bitstrings of length 48 computed as a function of the key K. (Actually, each Ki is a permuted selection of bits from K.) K1, K2, . . . , K16 comprises the key schedule. One round of encryption is depicted in Figure 3.1
- 3. Apply the inverse permutation IP-1 to the bitstring R16L16, obtaining the ciphertext y. That is, y = IP-1(R16L16). Note the inverted order of L16 and R16.
- 2. 16 iterations of a certain function are then computed. We compute LiRi,
The function f takes as input a first argument A, which is a bitstring of length 32, and a second argument J that is a bitstring of length 48, and produces as output a bitstring of length 32. The following steps are executed.
- 1. The first argument A is “expanded” to a bitstring of length 48 according to a fixed expansion function E. E(A) consists of the 32 bits from A, permuted in a certain way, with 16 of the bits appearing twice.
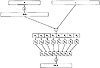
Figure 3.2 The DES f function- 2. Compute E(A) ⊕ J and write the result as the concatenation of eight 6-bit strings B = B1B2B3B4B5B6B7B8.
- 3. The next step uses eight S-boxes S1, . . . , S8. Each Si is a fixed 4 × 16 array whose entries come from the integers 0 - 15. Given a bitstring of length six, say Bj = b1b2b3b4b5b6, we compute Sj(Bj) as follows. The two bits b1b6 determine the binary representation of a row r of Sj (0 ≤ r ≤ 3), and the four bits b2b3b4b5 determine the binary representation of a column c of Sj (0 ≤ c ≤ 15). Then Sj(Bj) is defined to be the entry Sj(r, c), written in binary as a bitstring of length four. (Hence, each Sj can be thought of as a function that accepts as input a bitstring of length two and one of length four, and produces as output a bitstring of length four.) In this fashion, we compute Cj = Sj(Bj), 1 ≤ j ≤ 8.
- 4. The bitstring C = C1C2C3C4C5C6C7C8 of length 32 is permuted according to a fixed permutation P. The resulting bitstring P(C) is defined to be f(A, J).
- 2. Compute E(A) ⊕ J and write the result as the concatenation of eight 6-bit strings B = B1B2B3B4B5B6B7B8.
The f function is depicted in Figure 3.2. Basically, it consists of a substitution (using an S-box) followed by the (fixed) permutation P. The 16 iterations of f comprise a product cryptosystem, as described in Section 2.5.
| Previous | Table of Contents | Next |
Copyright © CRC Press LLC
EAN: 2147483647
Pages: 133