Cryptography: Theory and Practice:Secret Sharing Schemes
 | Cryptography: Theory and Practice by Douglas Stinson CRC Press, CRC Press LLC ISBN: 0849385210 Pub Date: 03/17/95 |
| Previous | Table of Contents | Next |
Suppose Γ is an access structure having basis Γ0, and 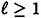 is an integer. Let
is an integer. Let 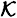 be a specified key set, and for 1
be a specified key set, and for 1 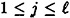 , suppose that
, suppose that 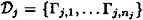 is an ideal decomposition of Γ0. Let
is an ideal decomposition of Γ0. Let 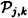 denote the participant set for the access structure Γj,k. For every participant Pi, define
denote the participant set for the access structure Γj,k. For every participant Pi, define
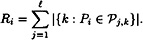
Then there exists a perfect secret sharing scheme realizaing Γ, having information rate 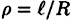 where
where
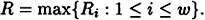
PROOF For 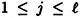 and 1 ≤ k ≤ n, we have an ideal scheme realizing the access structure with basis Γj,k, with key set
and 1 ≤ k ≤ n, we have an ideal scheme realizing the access structure with basis Γj,k, with key set 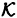 , having
, having  as its set of distribution rules. We construct a scheme realizing Γ, with key set
as its set of distribution rules. We construct a scheme realizing Γ, with key set 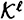 . The set of distribution rules
. The set of distribution rules 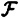 is constructed according to the following recipe. Suppose D wants to share a key
is constructed according to the following recipe. Suppose D wants to share a key 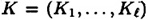 . Then for
. Then for 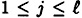 and 1 ≤ k ≤ n, he chooses a random distribution rule
and 1 ≤ k ≤ n, he chooses a random distribution rule 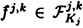 and distributes the resulting shares to the participants in
and distributes the resulting shares to the participants in 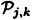
The information rate can be computed in a manner similar to that of Theorem 11.12.
Let's look at a couple of examples.
Example 11.10
Consider access structure # 5. The basis is a graph that is not a complete multi-partite graph. Therefore we know from Theorem 11.11 that ρ* ≤ 2/3.
Let p be prime, and consider the following two ideal 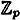 -decompositions:
-decompositions:
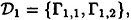
where
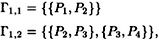
and
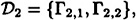
where
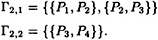
Each decomposition consists of a K2 and a K1,2, so they are indeed ideal  -decompositions. Either of them yields a scheme with ρ = 1/2. However, if we “combine” them by applying Theorem 11.13 with
-decompositions. Either of them yields a scheme with ρ = 1/2. However, if we “combine” them by applying Theorem 11.13 with  , then we get a scheme with ρ = 2/3, which is optimal.
, then we get a scheme with ρ = 2/3, which is optimal.
One implementation of the scheme, using Theorem 11.5, is as follows. D will choose four random elements (independently) from  , say b11, b12, b21, and b22. Given a key
, say b11, b12, b21, and b22. Given a key 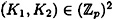 , D distributes shares as follows:
, D distributes shares as follows:
- 1. P1 receives b11, b21.
- 2. P2 receives b11 + K1, b12, b21 + K2.
- 3. P3 receives b12 + K1, b21, b22.
- 4. P4 receives b12, b22 + K2.
- 2. P2 receives b11 + K1, b12, b21 + K2.
(All arithmetic is performed in 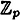 .)
.)
Example 11.11
Consider access structure # 8. Again, ρ* ≤ 2/3 by Theorem 11.11, and two suitable ideal compositions will yield an (optimal) scheme with ρ = 2/3.
Take 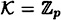 for any prime p ≥ 3, and define two ideal
for any prime p ≥ 3, and define two ideal 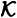 -decompositions to be:
-decompositions to be:
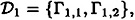
where
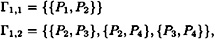
and
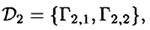
where
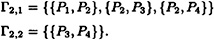
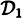 consists of a K2 and a K3, and
consists of a K2 and a K3, and 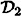 consists of a K2 and a K1,3, so both are ideal
consists of a K2 and a K1,3, so both are ideal  -decompositions. Applying Theorem 11.13 with
-decompositions. Applying Theorem 11.13 with  , we get a scheme with ρ = 2/3.
, we get a scheme with ρ = 2/3.
One implementation, using Theorem 11.5, is as follows. D will choose four random elements (independently) from 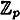 , say b11, b12, b21, and b22. Given a key
, say b11, b12, b21, and b22. Given a key 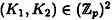 , D distributes shares as follows:
, D distributes shares as follows:
- 1. P1 receives b11 + K1, b21 + K2.
- 2. P2 receives b11, b12, b21.
- 3. P3 receives b12 + K1, b21 + K2, b22.
- 4. P4 receives b12 + 2K1, b21 + K2, b22 + K2.
- 2. P2 receives b11, b12, b21.
(All arithmetic is performed in 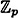
To this point, we have explained all the information in Table 11.1 except for the values of ρ* for access structures # 12 and # 13. These values arise from a more general version of the decomposition construction which we do not describe here; see the notes below.
11.9 Notes and References
Threshold schemes were invented independently by Blakley [BL79] and Shamir [SH79]. Secret sharing for general access structures was first studied in Ito, Saito, and Nishizeki [ISN87]; we based Section 11.2 on the approach of Benaloh and Leichter [BL90]. The vector space construction is due to Brickell [BR89A]. The entropy bound of Section 11.7 is proved in Capocelli et al. [CDGV93], and some of the other material from this section is found in Blundo et al. [BDSV93].
In this chapter, we have emphasized a linear-algebraic and combinatorial approach to secret sharing. Some interesting connections with matroid theory can be found in Brickell and Davenport [BD91]. Secret sharing schemes can also be constructed using geometric techniques. Simmons has done considerable research in this direction; we refer to [SI92A] for an overview of geometric techniques in secret sharing. Further discussion of these topics, as well as constructions for schemes having information rate 2/3 for access structures # 12 and # 13, can be found in the expository paper by Stinson [ST92A].
| Previous | Table of Contents | Next |
Copyright © CRC Press LLC
EAN: 2147483647
Pages: 133
- Challenging the Unpredictable: Changeable Order Management Systems
- Enterprise Application Integration: New Solutions for a Solved Problem or a Challenging Research Field?
- Distributed Data Warehouse for Geo-spatial Services
- Intrinsic and Contextual Data Quality: The Effect of Media and Personal Involvement
- Development of Interactive Web Sites to Enhance Police/Community Relations
- Chapter II Information Search on the Internet: A Causal Model
- Chapter IV How Consumers Think About Interactive Aspects of Web Advertising
- Chapter VII Objective and Perceived Complexity and Their Impacts on Internet Communication
- Chapter XIII Shopping Agent Web Sites: A Comparative Shopping Environment
- Chapter XIV Product Catalog and Shopping Cart Effective Design