OutlookOutlook Express
| | ||
| | ||
| | ||
Outlook/Outlook Express
Microsoft's free email client Outlook Express and its big brother Outlook go beyond basic messaging. Both include contact management features and a newsgroup reader and Outlook adds calendar, note, task management, and journal capabilities. Both products can work with standard SMTP (for outgoing) and POP3/IMAP (for incoming) mail services or with a Microsoft Exchange Server.
Outlook Express
Outlook Express stores all message information in a proprietary DBX format. A separate DBX file is used for each folder a user has created, with Inbox, Outbox, Sent Items, and Deleted Items files created by default.
| Note | Outlook Express version 4 uses two files per folder: an MDX file, which contains the message contents, and an IDX file, which contains message indexing information. |
Acquisition
Outlook Express DBX messages can be viewed directly on the analysis machine by copying the DBX files to the local machine's Outlook Express instance or by viewing with a dedicated viewer. To view the DBX files using Outlook Express, follow these steps:
-
Install a clean version of Outlook Express on the analysis machine.
-
Locate the Outlook Express DBX files ( generally under Documents and Settings\profilename\Local Settings\Application Data\Identities\ identity name \Microsoft\Outlook Express) on the suspect image.
-
Copy all DBX files from the suspect machine's directory to the analysis machine's Outlook Express directory.
-
Disconnect the analysis computer from the network to prevent accessing any mailboxes inadvertently.
-
Open Outlook Express on the analysis machine.
| Note | The actual identity and profile names will be different on the analysis machine. Copy the DBX files to whatever profile name is present on the analysis machine. |
The files and folder present on the suspect's machine will now be visible and searchable on the analysis box. The Outlook Express example in Figure 13-1 shows the standard folders imported and an additional folder titled "Spam."
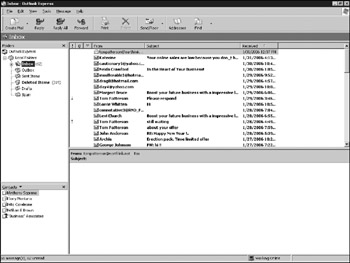
Figure 13-1: Outlook Express Inbox
A second way of viewing DBX files is through a dedicate viewer such as OE Viewer. OE Viewer provides a more forensically sound way of viewing the files. Since it is read only, the messages cannot be inadvertently altered . Using OE Viewer is simple. Just select File Open and choose the individual DBX folders present. The messages will be viewable in a similar fashion to the way they are in Outlook Express itself. Figure 13-2 shows a sample of messages displayed in OE Viewer. OE Viewer provides an additional tool which is useful in investigations. Selecting File Gather Email Addresses quickly shows all corresponding email accounts from all messages in a folder, providing a quick-and-easy way to identify associates of a suspect.
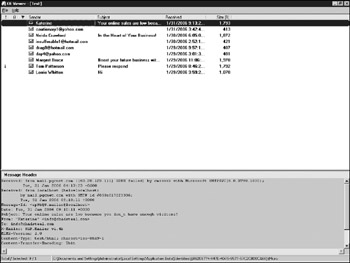
Figure 13-2: OE Viewer contents of a folder called Test
Analysis
The default folders in which mail is stored are as follows :
-
Inbox. Contains incoming mail until it is moved to another folder.
-
Drafts. Contains emails that have been drafted but not sent yet.
-
Outbox. Stores mail messages for sending when a connection to the server is established.
-
Sent Items. Contains any files sent (and a copy saved automatically).
-
Deleted Items. Stores messages that have been deleted from other folders. The Deleted Items folder acts like a minirecycling bin. Deleted messages are kept until it is emptied either automatically or manually.
Any numbers next to a folder (for example, 272 next to Deleted Items) indicate unread messages. These same messages will be bolded by default to indicate status. In an email investigation, both folder name and unread status are important.
Unread messages indicate it is likely but not certain that the recipient did not read a particular message. First, the recipient may have viewed the message in the preview pane (where the word Test is shown in Figure 13-1), which does not change the unread status. Second, the recipient may have changed the status back to Unread after reading the message. This is done be right-clicking and choosing Mark As Unread. Better proof that a suspect reviewed a message is contextual. References to the message content in replies or other documents are a better indication of having read the contents. Similarly, placing the message in a folder based on the contents is a likely indicator of having read the message.
Folder names and structure can be important in determining intent as well. In an inappropriate use investigation, the same message in a folder titled Spam may not be viewed as negatively as one in a folder titled Hot Pics or even Personal Mail. With large mail files, folders can direct an investigation as well. In the preceding inappropriate usage example, Hot Pics is more likely to turn up evidence than a Weekly Project Report folder. An embezzlement investigation, on the other hand, may have more interest in the latter folder name.
Because the views exclude header information by default (and header information may be critical in tracking the source of spam or phishing messages), this information frequently needs to be made available. Header information can be viewed in Outlook Express by right-clicking a message and selecting Properties Details, and then clicking Message Source (in OE Viewer, it's shown by default in the Preview Pane). The header info and raw message as received by the SMTP server will be shown. Figure 13-3 shows an example of header information which displays both the headers and the encoded attachment. This text can be selected and copied into an evidence file from this screen as well.
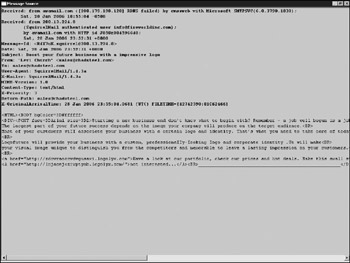
Figure 13-3: Actual message source
Searching messages is possible through the Find option in Outlook Express. Find works similarly to the Search function built into Windows XP and traverses a folder or folders (starting with the folder selected when Find was clicked) looking for messages that meet specified characteristics. Messages can be searched for by sender, receiver, date, or message itself (with wildcards accepted). Another useful option provided is to search for messages with attachments, which can dramatically narrow the number of messages that need to be reviewed in certain cases. The Find panel is shown in Figure 13-4.
Figure 13-4: Find Message searching in Outlook Express
| Warning | The Find function in Outlook Express will turn up any message text that matches the string but will not search the contents of attachments, attachment names, or header information, including the Subject line. |
Microsoft Outlook Express also includes a Contact Manager. Personal information on individuals is stored in the Addresses section of the program. These can be imported from messages (with vCards) or input directly, and may include names, addresses, email addresses, phone numbers, and personal details about the contact. Contacts can also be grouped into folders, allowing for differentiation between business and personal associates.
The Outlook Express address book information is stored in the Windows Address Book (WAB) format. By default, the address book resides in Documents and Settings\profile\Application Data\Microsoft\Address Book and is named after the individual's profile. The address book can be viewed in Outlook Express by selecting File Import Address book and choosing the WAB file. Figure 13-5 shows the WAB file as viewed by Outlook Express.
Figure 13-5: Windows Address Book in Outlook Express
A read-only Address Book viewer, called Address Book Recovery, is as well. This software, shown in Figure 13-6, provides a read-only view of a WAB file, repairs corrupted WAB files, and even recovers deleted contacts that have not been overwritten from these files.
Figure 13-6: Recovered Windows Address Book
Outlook
Microsoft Outlook is an enterprise-class email client. It is generally used in conjunction with Microsoft Exchange for corporate email systems but supports standard SMTP/POP3/IMAP messages also. Outlook adds to the functionality of Outlook Express by providing Calendar, Note, Task Management, and Journaling functions. The basic mail and contact functions are enhanced as well, and the storage formats differ significantly.
| Tip | A sister format to PST, Exchange also uses an OST Offline Storage format. This can be easily converted to the PST format using tools like Passware ExchangeRecovery, available at http://www.officerecovery.com/exchange/index.htm. |
Outlook data is stored in a consolidated proprietary record format, which within PST files. The PST files for a specific user are located under the user's profile within the Documents and Settings\profile name\Local Settings\ Application Data\Microsoft\Outlook folder by default, and named Personal Folders.pst. Additional PST files can be present for multiple mailboxes or other personal folders such as archive folders. PST files can be password protected and encrypted, making direct viewing of them difficult if these controls are enabled. The files present on the server are in a different, Exchange-specific format in files with EDB extensions. These need to be viewed with specialized software when copied locally.
Because Outlook is a client-server program, the contents stored locally may differ from those on the Exchange server. Depending on the user's setup, some content may reside on only the server (to allow access from the Web Connectorbased client or other computers with Outlook), only the client (when server-based mail quotas are enabled), or in both locations. Investigations should look at both the client-and server-based mail locations to ensure complete coverage.
| Note | Looking at both the client and server applies to any mail investigation. IMAP-based mail servers can keep messages on the server, and even POP3 mailboxes may have new mail that hasn't been downloaded stored remotely. |
Acquisition
Acquisition of local Outlook mailboxes is a matter of copying the PST file using standard forensic duplication techniques and viewing with Outlook itself or a third-party viewer. To use Outlook to view a PST file:
-
Install a clean version of Outlook on the analysis machine.
-
Locate the Outlook PST files on the suspect image.
-
Copy all PST files from the suspect machine's directory to the analysis machine's evidence directory.
-
Disconnect the analysis computer from the network to prevent accessing any mailboxes inadvertently.
-
Open Outlook on the analysis machine.
-
Select File Open Outlook Data File and select the PST file (or files) copied.
Viewing an Exchange database file in the EDB format is more difficult. To view an EDB file, the Exchange server should first be shut down. Next, the relevant EDB file should be copied in a forensically sound manner to the analysis machine and archived appropriately. Finally, a forensic EDB viewer such as PowerControls from Ontrack should be used to view the contents.
Access Control
The Microsoft Outlook PST file format is proprietary and encrypted, and can be further password protected to prevent unauthorized users from browsing it. Because of a weakness in the proprietary encryption algorithm, Outlook passwords can be instantly recovered using Passware's Outlook Key. The tool is run on a PST mail file and actually decrypts the password directly as opposed to using a dictionary or brute-force attack.
Analysis
Outlook stores its mail messages in user-created folders, with several folders created at installation. The standard folders created for mail are as follows:
-
Inbox. Contains incoming mail until it is moved to another folder.
-
Drafts. Stores emails that have been drafted but not yet sent.
-
Outbox. Stores mail messages for sending when reconnection to the server is made.
-
Sent Items. Contains any files sent (and a copy saved automatically).
-
Deleted Items. Stores messages that have been deleted from other folders. Deleted Items acts like a minirecycling bin. Deleted messages are kept until it is emptied either automatically or manually.
Outlook also has user-specific and public folder features. User-specific folders are located on the local system, and each folder may or may not be in a separate PST file. A popular one is an archive folder for older emails, generally in a separate PST file. Shared folders act more like a file share for collaboration. They are set up on the Exchange server itself and are accessible by others across the network.
The Contacts functionality of Outlook provides integrated address book capabilities. Individuals and distribution lists (groups of email addresses) are kept under Contacts, which has similar fields to Windows Address Book and can import Windows Address Book files.
Calendar is an online time management system. Meetings, appointments, and events are all tracked for a user, and in an Exchange-enabled system for groups of users. Knowledge of who was invited to a particular meeting, where an individual likely was at a given time, and known associates (those who have met with the individual) can be garnered from the Calendar view.
Tasks keep track of tasks assigned to or entered by the user. Tasks may be linked to Microsoft Project plans for business activities, and can be a clue as to a suspect's whereabouts at any particular time. Daily, weekly, or longer tasks may indicate a work pattern for a suspect.
The Journal feature provides the most interesting forensic- related feature over Outlook Express by keeping a record of all user activities. If turned on (it is off by default), the Journal feature tracks emails sent and received, Microsoft Office document activity, and Task completion details. If it is present, the Journal provides a daily forensic log of many user activities of interest. A sample Journal is shown in Figure 13-7.
Figure 13-7: Outlook Journal features
The Journal feature does the timeline work for the forensic examiner , showing what was done and when it was done. Everything from document updates to messages sent (even if the message is later deleted) may be present if fully enabled. In general, the Journal feature is used by consulting organizations and others that have client billing obligations (for example, accounting firms and law firms).
Searching a PST file can be done natively in Outlook or using a third-party program, but most third-party packages are limited due to the proprietary and encrypted nature of PST files. Since most third-party programs use the Outlook search capability, or export the data from PST files to another format, first, their forensic value is limited over using Outlook itself for analysis.
Searching a mail file in Outlook is a matter of opening the file on a non-net-worked analysis machine and selecting Tools Advanced Find. The search is not indexed and occurs quickly and searches all mail files but not attachments or attachment names. Figure 13-8 shows an advanced search for any messages sent by the suspect to smith@foo.com. Remember to look for cc: and bcc: recipients as well.
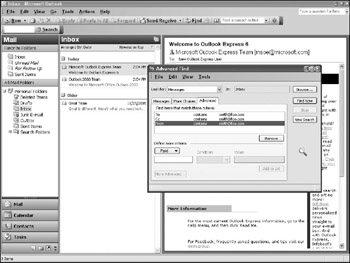
Figure 13-8: Outlook search for messages to smith@foo.com
By default, the mail headers are not displayed in the Outlook view menu, although add-ins that show them can be purchased. To display the headers for a particular message, right-click the message and select Options. The header info will be displayed in the Message Options dialog box.
| |
Network News Transfer Protocol (NNTP), the newsgroup-focused sister protocol to SMTP, emerged as the predominant way to exchange Usenet news articles in the mid 1980s. Usenet, developed several years prior, was a collection of communities in specific areas of interest organized into a newsgroup hierarchy. With top-level organizations like alt (for alternative), sci (for scientific), and rec (for recreation), like-minded individuals could connect to their local news server, send and receive messages (articles) organized by group , and have their messages relayed across the Internet. Until it was surpassed by HTTP in the mid 1990s, NNTP-based Usenet traffic represented the highest percentage of traffic on the Internet.
Because NNTP operates in a similar fashion to SMTP, many email clients , including Outlook Express, Outlook, and Notes, include it in their suite of functions. The ability to subscribe to groups of interest, read, and reply to messages in a basic fashion is present in all three products. Specialized newsreaders are available as well.
Newsgroups are historically relevant to forensics because of a few specific hierarchies. These include the alt.binaries hierarchy, whose subsidiary groups contain binaries posted in a translated ASCII format, and the alt.sex hierarchy, whose constituent groups discuss the varied aspects of human reproduction in frequently explicit ways. Although other hierarchies of forensic interest exist, and all alt.binaries and alt.sex groups are not obscene or dangerous, these are the two groups most often frequented by suspects .
Prior to peer-to-peer networking, the easiest way to share inappropriate and sometimes illegal content was through newsgroups. By spoofing an NNTP message (the same way an SMTP message can be spoofed) or using an anonymizing news server, individuals could share pirated software, copyrighted music and movies, and pornography, even child pornography. The contents would be shared globally to anyone subscribing to a particular hierarchy and became a distribution channel for all forms of interesting content. Groups like the alt.binaries.warez have been used to distribute software, alt.binaries .pictures.erotica for pornographic images, and alt.sex.stories for general, inappropriate-for-the-workplace content.
Although losing popularity, Usenet still exists and may still be encountered in an investigation. Any email clients with news readers should be analyzed to determine:
-
What newsgroups the suspect subscribed to.
-
What newsgroups the suspect read.
-
Any attachments that were downloaded by the suspect.
-
Any postings by the suspect.
Because binaries are encoded, there may still be messages present which are not found by text searches or hash analyses. Newsreaders should be used to extract and convert any existing encoded messages to their binary form and then analyzed. Any unusual-looking text messages should likewise be reviewed manually. Frequently encodings like ROT-13 are used on Usenet to bypass standard text-based filtering. Finally, the news server used should be noted, even if there are no current subscriptions present. The news server may have a log of past activities for the suspect.
| |
| | ||
| | ||
| | ||
EAN: 2147483647
Pages: 71