Exam 70-124: Objective 4.1.4: Configuring Kerberos Trusts
|
|
When the first Windows 2000 Server computer in a network is promoted to domain controller, it creates the root domain for the organization. Since this domain is the first one created in the forest, it becomes the root for the forest and the root for its tree. It will have a DNS name, such as mycompany.com. When additional domains are created in the company's network (by promoting other Windows 2000 servers to domain controllers and designating them as domain controllers for the new domains), there are three options:
-
They can be created as children of the forest root domain
-
They can be created as root domains for new trees in the existing forest
-
They can be created as root domains for a new forest
What are the components that make up the enterprise? Active Directory is made up of the following main components:
-
Forest A logical grouping of trees; defines an organization
-
Tree A logical grouping of domains
-
Domain A security boundary and unit of replication for Active Directory
-
Organizational Units (OUs) (and Containers) Hold objects and provide logical separation for the domain
-
Leaf Objects Examples are users, machines, printers, and groups
OUs and leaf objects have nothing to do with trust relationships, therefore they will not be discussed any further. This section focuses on forests, domains, and trees and how they fit together.
Domains are the main boundary for Active Directory. Account policies are applied at the domain level. Users log into a domain; they do not log in to a tree or a forest. Every domain has its own set of objects (users, groups, machines, and so on). Every domain also has its own administrators. Domains are installed into trees.
A tree is a grouping of domains that share a contiguous namespace. What does this mean? There is something in common about all the domain names in a tree. Each child domain shares the naming context of its parent. The first domain created in a tree is called the tree root. Trees are created inside the forest.
A forest is a collection of trees (and domains). All domains within a forest share a common schema and global catalog. If there are two different schemas, there must be two separate forests. The first domain created in the forest is called the forest root. The entire forest is named after the forest root. Forestwide settings are set at the forest root domain only.
Let's apply these concepts to organization illustrated in Figure 8.16. There are two trees: mycompany.com and yourcompany.com. Mycompany.com was created before yourcompany.com, which makes mycompany.com the forest root. Both trees have subdomains. There are four subdomains in all:
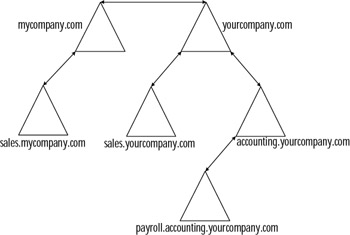
Figure 8.16: The Relationships of Domains within a Tree and Trees within a Forest
-
Sales.mycompany.com
-
Sales.yourcompany.com
-
Accounting.yourcompany.com
-
Payroll.accounting.yourcompany.com
Notice how each of the subdomains has the name of its parent. The payroll domain is a subdomain of a subdomain. It shares both its parents' names. All these domains and trees are said to be in the mycompany.com forest.
The Great Link: Kerberos Trusts between Domains
In Windows NT networks, every domain was an island. In order for users in one domain to access resources in another, administrators of the two domains had to set up an explicit trust relationship, as discussed earlier in this chapter. Moreover, these trusts were one way. If the administrators wanted a reciprocal relationship, two separate trusts had to be created because these trusts were based on the NTLM security protocol, which does not provide for mutual authentication. Figure 8.17 gives an example of using Windows NT 4.0 trusts to configure complete trusts (all domains trust each other) between six domains. If the administrators want to configure all six domains to trust each other, they must manually create 16 one-way trusts.
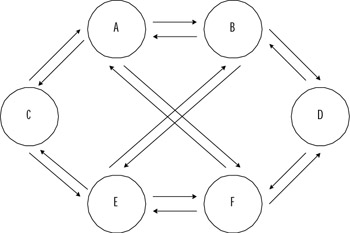
Figure 8.17: Trust Relationships in Windows NT 4.0
With the Kerberos protocol, all trust relationships are two-way, and implicit, automatic trusts exist between every parent and child domain. It is not necessary for administrators to create these trusts. Finally, these trusts are transitive, which means that if the first domain trusts the second domain, and the second domain trusts the third domain, the first domain will trust the third domain, and so on. This transitive state comes about by using the Kerberos referral; every domain in a tree implicitly trusts every other domain in that tree.
One final benefit Is that the root domains in a forest of domain trees also have an implicit two-way transitive trust relationship with each other. By traversing the trees, every domain in the forest trusts every other domain. As long as a user's account has the appropriate permissions, the user has access to resources anywhere on the network, without worrying about the domain in which those resources reside.
For practical purposes, a user in the payroll.accounting.yourcompany.com domain who needs to access a file or printer in the sales.mycompany.com domain can do so (provided that the user's account has the appropriate permissions). The user's domain, payroll.accounting.yourcompany.com, trusts its parent, accounting.yourcompany.com, which in turn trusts its own parent, yourcompany.com. Since yourcompany.com is an internal root domain in the same forest as mycompany.com, those two domains have an implicit two-way transitive trust; thus mycompany.com trusts sales.mycompany.com. This referral process is described as walking the tree. In Windows 2000, only five implicit trusts are needed to accomplish the same thing that Windows NT 4.0 needed 16 explicit trusts for . The best part is that all of the trusts are set up automatically in Windows 2000.
The Kerberos trusts apply only to Windows 2000 domains. If the network includes Windows NT 4.0 domains, they must still use the old NTLM one-way explicit trusts to share resources to or from the Windows 2000 domains.
Taking a Shortcut
Walking the tree requires many referrals, which is why shortcut trusts are useful. Shortcut trusts are two-way transitive trusts that allow administrators to shorten the path in a complex forest. These trusts must be explicitly designed by administrators to create a direct trust relationship between Windows 2000 domains in the same forest. A shortcut trust is used to optimize performance and shorten the trust path that Windows 2000 security must take for authentication purposes. The most effective use of shortcut trusts is between two domain trees in a forest.
Shortcut trusts are one of the two types of explicit domain trusts that can be established in Windows 2000; the other is the external trust used to establish a trust relationship with domains that are not part of the forest. The external trust is one-way and non-transitive, as in Windows NT 4.0 domain models. However, as with Windows NT, two one-way trusts can be established if a two-way relationship is desired. Figure 8.18 demonstrates both shortcut trusts and external trusts.
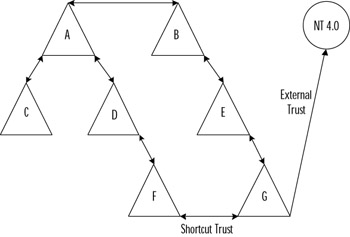
Figure 8.18: Connecting to an External Domain
To keep things simple, the domains in Figure 8.14 are named A, B, C, D, E, F, G, and NT 4.0. Users within the forest (domains A through G) can access resources (if permissions allow it) at any of the domains within the forest. Users in domains F and G can share resources directly with each other without having to be referred up and down the tree. Lastly, users in the NT 4.0 domain can access resources in the G domain, but not vice versa.
Active Directory automatically creates the parent/child and tree root trusts for you. You must manually create all shortcut (domain F and domain G) and external trusts (domain G and domain NT 4.0). Trusts can be created from the command prompt using Netdom or from the graphical user interface (GUI) using Active Directory domains and trusts.
The Netdom command has the following syntax when working with Active Directory trusts (Netdom actually has a much more advanced syntax and can be used for a variety of Active Directory tasks):
netdom trust trusting_domain_name /Domain:trusted_domain_name [/UserD:user] [/PasswordD:[password | *]] [/UserO:user] [/PasswordO:[password | *]] [/Verify] [/Reset] [/PasswordT:new_realm_trust_password] [/Add] [/Remove] [/Realm] [/Twoway] [/Kerberos] [/Transitive[:{yes | no}]] [/OneSide:{trusted | trusting}] [/Force] Table 8.1 explains the syntax for using Netdom to create trusts.
| Switch | Description |
|---|---|
| /Domain | Specifies the name of the trusted domain. |
| /UserD | Account used to make the connection to the trusted domain. |
| /PasswordD | Password of the user account specified by /UserD. |
| /UserO | User account for making the connection to the trusting domain. |
| /PasswordO | Password of the user account specified by /UserO. |
| /Verify | Verifies the trust. |
| / Reset | Resets the trust passwords. |
| /PasswordT | New trust password. |
| /Add | Specifies the trust to add. |
| /Remove | Specifies the trust to remove. |
| /Realm | Specifies a Kerberos realm if creating a Windows 2000 to Kerberos realm trust. |
| /Twoway | Specifies a bidirectional trust. |
| /Transitive | Creates a transitive trust. |
| /OneSide | Indicates that the trust should be created on only one domain. |
| /Force | Forces the requested operation. |
| Test Day Tip | You may find it helpful to memorize the functions of the Netdom prior to the exam and then write them down on scrap paper once you get into the testing center. |
Exercise 8.05 goes through using Active Directory domains and trusts to create a new two-way trust. Exercise 8.06 goes through using Netdom to create a new two-way transitive trust.
Exercise 8.05: Configuring Trusts with Active Directory Domains and Trusts
-
Click Start | Programs | Administrative Tools | Active Directory Domains and Trusts.
-
Within Active Directory Domains and Trusts (shown in Figure 8.19), right-click your domain name and choose Properties. You will see the window shown in Figure 8.20.
Figure 8.19: Active Directory Domains and Trusts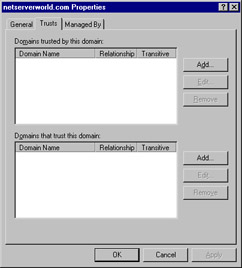
Figure 8.20: The Trusts Tab of the Domain Properties Window -
There are two sections in the Trusts tab of your domain's properties. You add the trusted domains to the top section and the trusting domains to the bottom section. Click the Add button in the "Domains trusted by this domain" section. You will see the window shown in Figure 8.21.
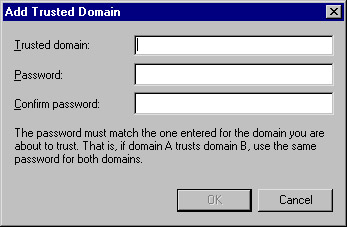
Figure 8.21: The Add Trusted Domain Window -
Type the name of the trusted domain and the trust password twice. When you are finished, click OK to return to the Trusts tab.
-
Click the Add button in the "Domains that trust this domain" section. You will see the window shown in Figure 8.22.
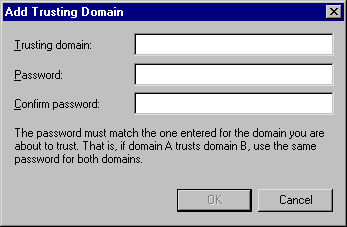
Figure 8.22: The Add Trusting Domain Window -
Type the name of the trusting domain and the trust password twice. When you are finished, click OK to return to the Trusts tab.
-
Click OK on the Trusts tab to save your changes, and close the Trusts window.
Exercise 8.06 will present you with the procedure to configure a new two-way transitive trust from the command line.
Exercise 8.06: Configuring Trusts with NetDOM
-
Open a command prompt.
-
Enter the following command to create a two-way transitive trust. If the domain is Windows 2000, use the full DNS name; if it is Windows NT 4.0, use the domain name.
netdom trust trusting_domain /domain:trusted_domain /userD:trusted_domain_admin_account /passwordD:trusted_domain_admin_password /userO:trusting_domain_admin_account /passwordO:trusting_domain_admin_password /ADD /Twoway /Trans:yes
|
|
EAN: 2147483647
Pages: 162