Internet Access
| Another important service that is required with MPLS VPNs is Internet access to VPN customers. There are several ways of providing Internet access, one of the simplest ways of which is to provide access to the gateway holding Internet routes to the VPN customers. This can be done by configuring a default route for all nonVPN prefixes and forcing the traffic to be routed via a firewall between the Internet and VPN. Each time a new VPN needs access to the Internet, a new dedicated gateway or a virtual gateway is required. There are several other ways of offering Internet service to MPLS VPN customers. Some of them include a shared centralized gateway; others move the ownership of Internet connectivity to the VPN customers themselves. Let us briefly discuss the following four ways of offering Internet services (refer to Figures 5-4 and 5-5). Figure 5-4. Fnternet Access (Options 1 and 2)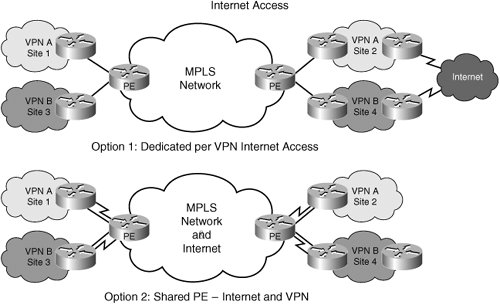 Figure 5-5. Internet Access (Options 3 and 4)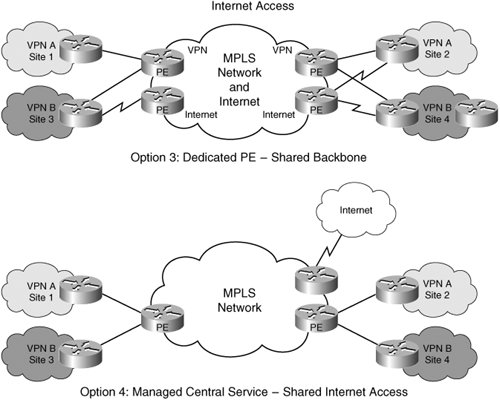
Let us discuss each one in detail. Dedicated Per-VPN Internet AccessAs shown in Figure 5-4, the Internet access is via the VPN. No direct connection to the Internet exists from the VPN provider network. The Internet connectivity is through one or more VPN sites. Traffic to the Internet from the VPN goes through a firewall or gateway. The Internet connectivity is independent of the VPN connectivity, so the VPN subscriber has the opportunity to buy Internet service from any provider. The VPN subscriber must pay for another dedicated connection. Although, this model of connectivity is simple, the VPN provider has no play in the Internet connection. This can be advantageous because the VPN provider can claim this is a pure private IP network. Shared PEInternet and VPNThis model of connectivity is simple: The PE is shared between Internet and VPN. In addition to carrying VPN routes in a VRF, the PE usually carries Internet routes in the global table. To connect to the Internet from a VPN, the VPN subscriber must buy another circuit, such as a data-link connection identifier (DLCI) or a DS1/DS3 channel from the VPN site(s) to the nearest PE. The CE then routes traffic on two interfaces based on whether the traffic is destined to the Internet or to another VPN site. As the number of Internet connections increases, an operator can reflect these additions from the CE within a VPN by provisioning a DLCI, VC, or dedicated DS1/DS3 channel to the PE. The result of such an implementation is an efficient traffic flow that forces the Internet traffic to the nearest PE rather than always being routed via a single VPN site (HQ or Internet gateway site). If all CEs have connectivity to both an Internet and a corporate VPN, the Internet traffic is offloaded at the first hop and will not traverse the VPN path to reach a gateway. This method of connectivity is relatively simple, and all isolation and firewall techniques can be applied to the Internet connectivity. However, this implementation might not be the most secure due to the perceived threat from the Internet to the PE routers. Additionally, PE routers carry the burden of Internet routes and instabilities with the VPN routes, and these affect scalability and convergence. It is not our intention to deal with security and convergence issues in this chapter. They will be dealt with in Chapter 13. Dedicated PEShared BackboneTo separate the VPN routes from the Internet routes, dedicated PEs can be deployed that carry Internet routes and VPN routes only. The PE carrying VPN routes does not peer or have connectivity with the PE carrying Internet routes. However, they share the same backbone or core network. This can be viewed as two planes of connectivity riding on the same network core where paths (LSP) from one plane do not intersect with LSPs from the other plane. Plane 1 carries VPN information, and LSPs for VPN traffic are established by the VPN PEs. LSPs for the Internet traffic are established by Internet PEs. The core network can be BGP free with neither Internet nor VPN routes but simply IGP connectivity. The CEs responsible for routing Internet traffic connect to both PEs. This method of connectivity provides a good separation of VPN and Internet traffic. Security issues are minimized when compared to the shared PE model. However, the cost of this method of connectivity is high because of the requirement of a dedicated PE for each function. From a VPN subscriber point of view, the cost is the same as the shared PE model due to the requirement to buy multiple connectionsone for the Internet and another for VPN. Managed Central ServiceShared Internet AccessThe fourth model leverages VRF-aware IP services to provide Internet access. It makes use of IP services such as Dynamic Host Configuration Protocol (DHCP), network address translation (NAT), firewalls, and on-demand address pools (ODAP) being VRF-aware. This means that these IP services (NAT, ODAP, and firewall) understand VRF context and maintain separation between the traffic of one VRF and another. Let us assume that several VPNs are using private address space. This means that when performing NAT from any VPN to the public address space (Internet), the gateway/PE must be able to maintain the VPN contexts. By using VRF-aware NAT, a PE can distinguish between 10.1/16 of VPN A and 10.1/16 of VPN B. Therefore, a single PE can now become the gateway to the Internet for all the VPNs, as shown in the diagram. The Internet gateway PE contains the VRFs (VPN information) and routes traffic for multiple VPNs to the Internet. This gateway PE can be located at a central location, providing easy Internet connectivity to all the sites. As the name suggests, this model of connectivity is used for centrally building the Internet access and sharing it across all VPNs. It can be used to build bundled services providing value add for the VPN provider. The important advantages include both cost reduction through the use of fewer gateways and reduced management requirements caused by the capability to enforce a single security policy centrally in the network. Several variations can be created with these four basic models of Internet access for VPN customers. These are discussed in detail in several books and whitepapers from Cisco including the following:
|
EAN: 2147483647
Pages: 162