Module Objectives
This module deals with Virus. The scope of discussions here is to look at some of those viruses that widely infected computer systems across the globe. This is taken up in order to have an insight into the workings of various viruses. After the completion of this module you will be familiar with the following topics:
-
Chernobyl
-
ExploreZip
-
I Love You
-
Melissa
-
Pretty Park
-
Code Red Worm
-
W32/Klez
-
BugBear
-
W32/Opaserv Worm
-
MS Blaster
-
Anti-Virus Software
| |
-
Chernobyl is a deadly virus. Unlike the other viruses that have surfaced recently, this one is much more than a nuisance.
-
If infected, Chernobyl will erase data on your hard drive, and may even keep your machine from booting up at all.
-
There are several variants in the wild. each variant activates on a different date. Version 1.2 on April 26th, 1.3 on June 26th, and 1.4 on the 26th of every month.
| |
We begin our discussion on viruses with the Chernobyl virus, as it became infamously known as its payload was first triggered April 26, 1999 - which was the 13th anniversary of the disaster at the Chernobyl nuclear reactor. Speculations abound regarding if Chernobyl was the activation date or whether it was activated a year since it was released in the wild.
| Threat | The payload was a devastating one that destroyed all computer data by erasing the FAT file when the infected file was executed. The virus has another distinction as being the first virus known to damage computer hardware, as the active strain flashes the system BIOS as well. The virus infects several files as they are run during the course of normal operations, making it easily transmittable across the network. |
The virus was detected in the wild almost a year before it caused a catastrophe. Although U.S. and European computer users were affected, most of Chernobyl's damage was produced in Asia and the Middle East. The virus is a variant of a virus known as CIH (named after its author Chen Inghua) and is also known as a space filler virus due to its ability to stealthily take up file space on computers and prevent anti-virus software from running.
This is a Windows95/98 specific parasitic virus infecting Windows PE files (Portable Executable), and about 1Kbyte of length. The virus targets users of Windows 95 and Windows 98 as it is under these operating systems that the virus replicates and becomes active. Users of Windows NT, Windows 2000 or Macintosh are not considered to be at risk. The variants of the virus differ in the activation dates or pattern.
How the virus works
The virus installs itself into the Windows memory and hooks file access calls which infect EXE files that are opened at that time. Depending on the system date the virus runs its trigger routine. The virus has bugs and in some cases halts the computer when an infected application is run.
The virus' trigger routine operates with Flash BIOS ports and tries to overwrite Flash memory with "garbage". This is possible only if the motherboard and chipset are write-enabled, allowing the virus to write to flash memory. Usually writing to flash memory can be disabled by a DIP switch; however this depends on the motherboard design. Unfortunately, there are modern motherboards that cannot be protected by a DIP switch. Some other motherboard designs provide write protection that can be disabled / overridden by software.
The trigger routine then overwrites data on all installed hard drives . The virus uses direct disk write calls to achieve this and bypasses standard BIOS virus protection while overwriting the MBR and boot sectors.
There are three "original" virus versions known, which are very closely related and only differ in few parts of their code. They have different lengths, texts inside the virus code and trigger date.
Other known virus versions
The original virus author released to the wild not only virus code in affected EXE files, but virus source (assembler) code as well. These source code were patched, recompiled, and new virus version were found because of that. Most of these versions are buggy and not able to replicate, but others do that. All of them are very close to original viruses, but there are few differences. The main difference is that the "bomb" date was changed, and new variants of the virus either erase data and Flash BIOS on other days, or this routine is never called.
There are also "original" versions of the virus patched so that they have other "bomb" days. The basic of this fact is very silly: the virus checks the trigger date by comparing current day and month number with two constants (two bytes). By patching these constants it is possible to select any day the virus will destroy the computers.
| |
-
ExploreZip is a Win32-based e-mail worm. It searches for Microsoft Office documents on your hard drive and network drives.
-
When it finds any Word, Excel, or PowerPoint documents using the following extensions: .doc, .xls and .ppt, it erases the contents of those files. It also emails itself to any one who send you an e-mail.
-
ExploreZip arrives as an email attachment. The message will most likely come from someone you know, and the body of the message will read:
"I received your email and I shall send you a reply ASAP. Till then, take a look at the attached Zipped docs." The attachment will be named " Zipped files.exe" and have a WinZip icon. Double clicking the program infects your computer.
| |
This is a 32bit Worm that travels by sending email messages to users. It drops the file explore.exe and modifies either the WIN.INI (Windows 9x/ME) or modifies the registry (Windows NT/2K/XP).
This worm attempts to invoke the MAPI aware email applications as in MS Outlook, MS Outlook Express and MS Exchange. This worm replies to messages received by sending an email message with the following body:
"I received your email and I shall send you a reply ASAP.
Till then, take a look at the attached zipped docs."
The subject line is not constant as the message is a reply to a message sent to the infected user . The worm (named "zipped_files.exe" as the attachment, with a file size of 210,432 bytes. The file has a WinZip icon which is designed to fool unsuspecting users to run it as a self-extracting file. Users who run this attachment will be presented with a fake error message that says:
"Cannot open file: it does not appear to be a valid archive. If this file is part of a ZIP format backup set, insert the last disk of the backup set and try again. Please press F1 for help."
| Threat | Payload Notice This worm has a payload. Immediately after execution it will search all local and network drives for the following files types .c, .cpp, .h, .asm, .doc, .xls, or .ppt. When found, their content is erased. Approximately 30 minutes after infection this process is repeated. Files that have been affected by this payload will need to be restored from backup. Repair is not possible. |
This worm will locate system drives which are NOT mapped drives using functions from MPR.DLL and Network Neighborhood. On these systems, the WIN.INI is modified with a run statement to load a file called _SETUP.EXE from the Windows path , and the file _SETUP.EXE is copied to the Windows path. These systems will become infected when restarted. This worm will only try to infect such systems once, whereas systems which are mapped drives are constantly attempted to be re-infected. Secondly, a machine infected via another share will switch between _setup and explore per reboot.
Existence of any of the 3 file names mentioned above [note EXPLORER.EXE is a valid name - do not confuse this name ]. Process running as mentioned above, files being corrupted / deleted as mentioned above.
Running the file will directly infect the local system by installing itself and running memory resident, then it will use browsing of the network to locate available shares. The program searches local and networked drives (drive letters C through Z) for specific file types and attempts to erase the contents of the files, leaving a zero byte file. The targets may include Microsoft Office files, such as .doc, .xls, and .ppt, and various source code files, such as .c, .cpp, .h, and .asm.
The program propagates by replying to any new email that is received by an infected computer. A copy of zipped_files.exe is attached to the reply message. The program creates an entry in the Windows 95/98 WIN.INI file:
run=C:\WINDOWS\SYSTEM\Explore.exe
On Windows NT systems, an entry is made in the system registry:
[HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows] run = "c:\winnt\system32\explore.exe"
The program creates a file called explore.exe in the following locations:
Windows 95/98 - c:\windows\system\explore.exe Windows NT - c:\winnt\system32\explore.exe
This file is a copy of the zipped_files.exe Trojan horse, and the file size is 210432 bytes.
MD5 (Explore.exe) = 0e10993050e5ed199e90f7372259e44b
| |
-
LoveLetter is a Win32-based e-mail worm. It overwrites certain files on your hard drive(s) and sends itself out to everyone in your Microsoft Outlook address book.
-
LoveLetter arrives as an email attachment named: LOVE-LETTER-FOR-YOU.TXT.VBS though new variants have different names including VeryFunny.vbs, virus_warning.jpg.vbs and protect.vbs

| |
LoveLetter was found globally in the wild on May 4th, 2000. At the beginning of the code, the virus contains the following text:
rem barok -loveletter(vbe) <i hate go to school> rem by: spyder / ispyder@mail.com / @GRAMMERSoft Group / Manila,Philippines
VBS/LoveLetter is a VBScript worm. It spreads over email as a chain letter. The worm uses the Outlook e-mail application to propagate. Additionally, LoveLetter is also an overwriting VBS virus, and spreads itself using mIRC client. When executed, it copies itself to the Windows system directory as: MSKernel32.vbs / - LOVE-LETTER-FOR-YOU.TXT.vbs and to Windows directory as Win32DLL.vbs. Afterwards, it adds itself to the registry, so that it is executed when the system is rebooted. The worm also replaces the Internet Explorer home page with a link that points to an executable program "WIN-BUGSFIX.exe". If the file is downloaded, the worm adds this to registry, causing the program to be executed when the system is restarted.
| Threat | The executable part that the LoveLetter worm downloads from the web is a password stealing Trojan. On startup the Trojan tries to find a hidden window named 'BAROK...' If present, the Trojan exits immediately, otherwise , the main routine takes over. The Trojan checks for the WinFAT32 subkey in the following Registry key: HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run |
If the WinFAT32 subkey key is not found, the Trojan creates it, copies itself to the Windows system directory as WINFAT32.EXE and then executes the file from there. The above registry key modification activates the Trojan every time Windows starts. The Trojan sets Internet Explorer startup page to 'about: blank'. Later, the Trojan tries to find and delete the following keys:
Software\Microsoft\Windows\CurrentVersion\Policies\Network\HideSharePwds Software\Microsoft\Windows\CurrentVersion\Policies\Network\DisablePwdCaching .DEFAULT\Software\Microsoft\Windows\CurrentVersion\Policies\Network\HideSharePwds .DEFAULT\Software\Microsoft\Windows\CurrentVersion\Policies\Network\DisablePwdCachin g
The Trojan proceeds to register a new window class and creates a hidden window titled 'BAROK...' and remains resident in the Windows memory as a hidden application. After startup when the timer counters reaches certain value, the Trojan loads MPR.DLL library, calls WNetEnumCashedPasswords function and sends stolen RAS passwords and all cached Windows passwords to 'mailme@super.net.ph' e-mail address. The Trojan uses the 'smpt.super.net.ph' mail server to send e- mails . The e-mail's subject is 'Barok... email.passwords.sender.trojan'.
There is the author's copyright message inside the trojan's body:
barok ...i hate go to school suck ->by:spyder @Copyright (c) 2000 GRAMMERSoft Group >Manila,Phils.
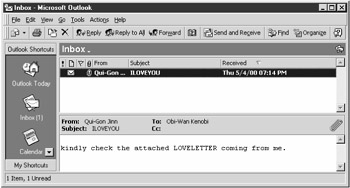
There is also some encrypted text messages in the Trojan's body used for its internal purposes. After that, the worm creates a HTML file, "LOVE-LETTER-FOR-YOU.HTM", to the Windows System directory. This file contains the worm, and it will be sent using mIRC whenever the user joins an IRC channel. The worm will then use Outlook to mass mail itself to everyone in each address book. The message that it sends will be as follows :
Subject: ILOVEYOU Body: kindly check the attached LOVELETTER coming from me. Attachment: LOVE-LETTER-FOR-YOU.TXT.vbs
LoveLetter sends the mail once to each recipient. After a mail has been sent, it adds a marker to the registry and does not mass mail itself any more.
The virus then searches for certain filetypes on all folders on all local and remote drives and overwrites them with its own code. The files that are overwritten have either "vbs" or "vbe" extension. For the files with the following extensions: ".js", ".jse", ".css", ".wsh", ".sct" and ".hta", the virus will create a new file with the same name, but using the extension ".vbs". The original file will be deleted.
Next the the virus locates files with ".jpg" and ".jpeg" extension, adds a new file next to it and deletes the original file. Then the virus locates ".mp3" and ".mp2" files, creates a new file and hides the original file. For above two cases, the new files created will have the original name added with the extension ".vbs". For example, a picture named "pic.jpg" will cause a new file called "pic.jpg.vbs" to be created.
| |
-
User Controlled Data is placed into an SQL query without being validated for correct format or embedded escape strings.
-
Affects majority of applications which use a database backend and don't force variable types.
-
At least 50% of the large e-commerce sites and about 75% of the medium to small sites are vulnerable.
-
Improper validation in CFML, ASP, JSP and PHP are the most frequent causes.
| |
The Slammer worm targets versions of Microsoft SQL Server 2000 products, as well as MSDE 2000 and related packages. The outbreak began on 25 January 2003 (GMT). According to early reports , the worm had a very significant presence around the world in less than one hour , and the peak time of the worm lasted for about three hours. During the worm's initial outbreak, Internet users experienced large percentage packet drops that developed into a large-scale DoS attack.
| Threat | The worm exploits a stack-based overflow that occurs in a DLL implementing the SQL Server Resolution Service. This DLL (ssnetlib.dll) is used by the SQL Server service process called SQLSERVR.EXE. The vulnerability had been reported to Microsoft by David Litchfield (NGSSoftware), along with a few others. Furthermore, exploit code was made available at a BlackHat conference in 2002 and it is clear that this code was used as a base from which to develop the worm. |
Exploit Setup
The SQL Server process listens on TCP as well as UDP ports. The worm targets U DP port 1434, sending a special request (0x04) specified as the first character of the payload. In the datagram this is followed by a specially crafted 'string' that contains the worm code. The worm code is 376 bytes, which is the shortest binary worm known today. (376 bytes is the length of the UDP datagram without the protocol headers.)
Since the worm can use a UDP packet for the attack, it is probable that the source IP address of the original attacker was spoofed. The worm spreads to randomly generated IP addresses and, as a result, it is very difficult to determine from which country the attack originated.
The vulnerable function in ssnetlib.dll (as implemented in SQL Server 2000) is nested two levels deep inside a thread associated with the incoming request. The function is supposed to build a string for a Registry access by concatenating three strings into a 128-byte buffer. This string will be built on the stack and there are no input validations for the size of the middle string parameter. Strings 1 and 3 are constant and located in the ssnetlib.dll.
(String 1) 'SOFTWARE\Microsoft\Microsoft SQL Server\' (String 2) String passed in the datagram (starts after the 0x04 type field) (String 3) '\MSSQLServer\CurrentVersion'
As a result, whenever a string that is too long is passed to the function, the stack is corrupted (smashed). String 2 is an SQL Server instance name. According to the Microsoft Knowledge Base this string should be 16 characters long at most. However, this is neither enforced in the server , nor even in some of the common clients .
The worm has been crafted carefully . Its code is not only compact but it contains no zeros. This is because the buffer is used as a string parameter to a sprintf () library function call. As a result of the overflow a concatenated string will build on the stack where string 2 is the worm body itself.
Getting Control
Since the worm cannot contain zeros the author uses a lot of 01 filler bytes. Furthermore, attempts are made to use addresses that do not contain any zeros and, in some cases, the code uses XOR to mask zero bytes, which is a known shell code technique.
The worm starts with a header posing as local variables of the buggy function. A new return address (0x42B0C9DC) follows these filler bytes. This address is a pointer to a JMP ESP instruction inside SQLSORT.DLL, another module of the SQL Server process.
To make sure the vulnerable function will give control to the worm body, the header section of the worm also uses dummy ('crash test dummies') values (0x42AE 7001) to replace function arguments on the stack. It is necessary to do this because these arguments are used after the call to sprintf () triggering the overflow. Failure to replace these arguments would cause an exception and thus the function would not return normally. When the function returns, control flows to the JMP ESP instruction which jumps on the stack to the location immediately after the hijacked return address. The first instruction will be a short jump around fake function arguments to the main worm code.
Initialization
The local variables within the worm header section could change during the time between the actual faulty sprintf () and the function return to the worm body, which means that the worm's header could become corrupted. Thus the worm will rebuild this area first to make sure that its header section remains constant for the next attack. Since the query type field (0x04) is missing from the top of the worm on the stack it is also rebuilt by pushing a 0x04000000 DWORD whose high byte is referenced by the replication code later.
Now the worm needs only a few functions to call. Following the original exploit code the worm's author uses the import address directory of SQLSORT.DLL to make calls to LoadLibraryA () and GetProcAddress () function calls. This routine is compatible with different Service Pack releases and patches of SQL Server. Therefore GetProcAddress ()'s code is checked first to be sure that it is the proper function entry point.
Then the worm gets access to the handles (base addresses) of WS2_32.DLL and KERNEL32.DLL. Next it gets the addresses of socket (), sendto () and GetTickCount () APIs, which is all it needs to replicate.
Replication
The replication method is extremely simple. The worm sends 376 bytes to UDP port 1434 to randomly generated IP addresses in an endless loop. This will cause the server CPU usage to increase and thousands of packets will be sent, effectively causing a DoS attack and at the same time compromising a large number of new systems around the world. The random number used to generate IP addresses is a variant of the Microsoft Basic random number generator. It uses the same multiplier . This results in sufficient randomness in the distribution of targeted systems.
| |
-
Melissa is a Microsoft Word macro virus.
-
Through macros, the virus alters the Microsoft Outlook email program so that the virus gets sent to the first 50 people in your address book
-
It does not corrupt any data on your hard drive or make your computer crash. It just changes some Word settings and sends itself to the people you don't want to infect.
-
Melissa Virus Infection
-
Melissa arrives as an email attachment.
-
The subject of the message containing the virus will read: "Important message from "followed by the name of the person whose email account it was sent from.
-
The body of the message reads: Here's the document you asked for...don't show anyone else ;-) Double clicking the attached Word document (typically named LIST.DOC) will infect your machine.
-
| |
Melissa is a standard Word 97 Class-style infector. The first time an infected document is opened on a given machine, the virus receives control via the standard Document_Open () macro.
To begin, it attempts to deactivate macro security. It checks for the value Level in the registry key: HKEY_CURRENT_USER\Software\Microsoft\Office\9.0\ Word\Security. If this value is found, Melissa assumes that it is running inside Word 2000. Subsequently, it disables the Security option on the Macro menu (this causes that option to appear greyed out on the menu), and then resets the Level value mentioned above to 1.
If the Level value is not found, Melissa assumes that it is running under Word 97. It greys out the Macro option on the Tools menu, disables format conversion warnings, Word's own virus protection, and prompts to save the global template. Instead of setting these options to False or 0, it sets them to (1 - 1) in an attempt to fool macro heuristics. Following this initial work, Melissa moves on to trigger the payload.
Infection
The virus copies itself from the source document to the destination one using the InsertLines method on a CodeModule object. It takes care to change the first line of the macro accordingly . This is dependent upon whether it is copying itself into the global template from a document, or into a document from the global template. This is necessary because the macro has two different names - in a document, it is called Document_Open(), and in the global template, it is called Document_Close().
Melissa also has a little noticed side effect - it will overwrite the first item in the collection of documents and global templates which it infects. For most documents, this will not be an issue, of course - however, for global templates; it can be a problem.
| Threat | Payloads Melissa has two payloads. Whether or not the virus has had to copy its body from one place to another, at the end of its execution it checks the time. If the minutes of the hour are the same as the day of the month (for example, 11.15 on 15 December, or 10.04 on 4 July), it will insert the following text into the active document, wherever the cursor happens to be:
|
At this point in the virus, the following text appears in comments:
WORD/Melissa written by Kwyjibo Works in both Word 2000 and Word 97 Worm? Macro Virus? Word 97 Virus? Word 2000 Virus? You Decide! Word -> Email Word 97 <-> Word 2000 ... it's a new age!
Kwyjibo and the text that the virus inserts into the current document derive from an episode of The Simpsons called 'Bart the Genius'. The family is playing Scrabble, and Bart says: 'K-W-Y-JI-B-0... Kwyjibo. 22 points... plus 50 points for using all my letters! Game's over, I'm outta here...'. When asked, he defines Kwyjibo as 'a big, dumb, balding, North American ape with no chin...'.
That Other Payload
Immediately after the virus attempts to disable Word's security features, it uses the CreateObject () function to initialize an instance of Microsoft Outlook. The virus installs 'On Error Resume Next' handler, so that if and when all the commands that follow fail, it will blunder on regardless, without telling the user that anything is wrong.
Once Melissa has obtained a running instance of Outlook , it asks it for a MAPI (Messaging API) namespace. Following this, it checks for the existence of a value 'Melissa?' in the registry key: HKEY_CURRENT_USER\Software\ Microsoft\Office.
If this value is set to '... by Kwyjibo', then it skips the next set of instructions - after the payload has been executed, the virus will set that value to that string, preventing the payload from being executed more than once. Even a system with a write-protected registry would allow the payload to execute each and every time an infected document is opened. In this case, security works against the prepared.
Then Melissa logs on to Outlook as the default user on that machine. In many environments, Outlook attempts to connect to the server using the current network username and password, which would obviously work well in Exchange -based environments.
Melissa now iterates across all the ' members ' of the MAPI session's AddressLists 'collection' - MAPI (and Outlook ) allowing the user to have multiple address books in which to store names and email addresses of both individuals and groups of individuals for easy access. Once again, in Exchange -based environments, one or more of these address books can be held on the server - these address books are shared between multiple users.
For each list in the collection, Melissa constructs a message to the first fifty entries, with the subject line 'Important Message From <username>', where <username> is set to the name used to register the currently-running copy of Word. The body text is set to 'Here is that document you asked for ... don't show anyone else ;-)', and Melissa attaches the current infected document to the message, and sends it.
Melissa's Initial Spread
Melissa was distributed on Friday 26 March via a posting to the Usenet group ALT.SEX, in an infected document containing what was claimed to be a list of passwords for porn sites (LIST.DOC, contained within LIST.ZIP).
The initial impact of Melissa was considerable - news stories quoted Microsoft officials as saying that they had been forced to shut down their outbound and inbound email servers. During the weekend of 27/28 March, only two of Microsoft's five inbound mail servers were in operation. One large organization reports that between four hundred thousand and half a million email messages were generated by the virus in under three hours - after which time they also shut down their servers.
| |
-
Pretty Park is a privacy invading worm. Every 30 seconds, it tries to e-mail itself to the e-mail addresses in your Microsoft Outlook address book.
-
It has also been reported to connect your machine to a custom IRC channel for the purpose of retrieving passwords from your system.
-
Pretty park arrives as an email attachment. Double clicking the PrettyPark.exe or Files32.exe program infects your computer.
-
You may see the Pipes screen after running the executable.
| |
| Threat | Pretty Park comes in the form of an email attachment with the name prettypark.exe, files32.exe, or prettyorg.exe. Windows users are susceptible to the worm. Once the worm program is executed, it tries to email itself automatically every 30 minutes (or 30 minutes after it is loaded) to email addresses registered in the address book. |
It also tries to connect to an IRC server and join a specific IRC channel. The worm sends information to IRC every 30 seconds to keep itself connected, and to retrieve any commands from the IRC channel. Through the IRC connection, the author of the worm can obtain system information, including the computer name, product name, product identifier, product key, registered owner, registered organization, system root path, version, version number, ICQ identification numbers , ICQ nicknames, victim's email address, and Dial up Networking username and passwords. In addition, being connected to IRC opens a security hole in which the client can potentially be used to receive and execute files.
It creates a file called files32.vxd in the C: \Windows\System directory and modifies the following registry key located at
HKEY_LOCAL_MACHINE\Software\Classes\exefile\shell\open\command From "%1" %* to files32.vxd "%1" %*
A variant of the Pretty Park Worm also creates a similar change to the following registry key.
HKEY_CLASSES_ROOT\exefile\shell\open\command
Some may see the Microsoft Pipes screen saver after running the executable.
| |
-
This worm propagates via shared network folders and via email.
-
It also terminates antivirus programs, act as a backdoor server application, and sends out system passwords - all of which compromise security on infected machines.
-
BugBear Infection
-
This worm fakes the FROM field and obtains the recipients for its email from email messages, address books and mailboxes on the infected system. It generates the filename for the attached copy of itself from the following:
-
A combination of text strings: setup, card, docs, news, Image, images, pics, resume, photo, video, music or song data; with any of the extensions: SCR, PIF, or EXE. An existing system file appended with any of the following extensions: SCR, PIF or EXE.
-
On systems with un patched Internet Explorer 5.0 and 5.5, the worm attachment is executed automatically when messages are either opened or previewed using Microsoft Outlook or Outlook Express.
-
| |
W32/Bugbear-A is a network-aware worm. W32/Bugbear-A spreads by sending emails containing attachments and by locating shared resources on your network to which it can copy itself.
Note that W32/Bugbear-A tries to copy itself to all types of shared network resource, including printers. Printers cannot become infected, but they will attempt to print out the raw binary data of W32/Bugbear-A's executable code. This usually results in many wasted pages.
| Threat | The worm attempts to exploit a MIME and an IFRAME vulnerability in some versions of Microsoft Outlook, Microsoft Outlook Express, and Internet Explorer. These vulnerabilities allow an executable attachment to run automatically, even if you do not double-click on the attachment. |
If the worm activates, several new files will appear on the infected computer. Their names consist of letters of the alphabet randomly chosen by the worm.
-
xxx.EXE (usually 50688 bytes) in the Startup folder
-
yyyy.EXE (usually 50688 bytes) in the System folder
-
zzzzzzz.DLL (usually 5632 bytes) in the System folder
The two EXE files are executable copies of the worm. The DLL is a keystroke logging tool which is used by the worm when it is activated. The worm not only adds itself to the Startup folder, but also adds an entry to the following registry key:
HKLM\Software\Microsoft\Windows\CurrentVersion \RunOnce
This means that the worm will be reactivated when the infected computer is rebooted.
The worm spreads itself via email. The emails can look like normal emails or they could have no body text and one of the following subject lines:
| Hello! Update Payment notices Just a reminder Correction of errors history screen Announcement various Introductions Interesting... I need help about script!!! Please Help... Get 8 FREE issues - no risk! Greets! | Report Membership Confirmation Get a FREE gift! Today Only New Contests Lost & Found bad news fantastic click on this! Market Update Report empty account My eBay ads 25 merchants and rising Your News Alert | CALL FOR INFORMATION! New reading Sponsors needed SCAM alert!!! Warning! Its easy free shipping! Daily Email Reminder Tools For Your Online Business New bonus in your cash account Your Gift $150 FREE Bonus! |
Attachments can have the same filename as another file on the victim's computer but they may contain the following strings:
Readme, Setup, Card, Docs, News, Image, Images, Pics, Resume, Photo, Video, Music, Song, Data.
The attachments have double extensions with the final extension being EXE, SCR or PIF. The worm can spoof the from and Reply To fields in the emails it sends.
W32/Bugbear-A has a thread running in the background which attempts to terminate anti-virus and security programs with one of the following filenames:
ZONEALARM.EXE, WFINDV32.EXE, WEBSCANX.EXE, VSSTAT.EXE, VSHWIN32.EXE, VSECOMR.EXE, VSCAN40.EXE, VETTRAY.EXE, VET95.EXE, TDS2-NT.EXE, TDS2-98.EXE, TCA.EXE, TBSCAN.EXE, SWEEP95.EXE, SPHINX.EXE, SMC.EXE, SERV95.EXE, SCRSCAN.EXE, SCANPM.EXE, SCAN95.EXE, SCAN32.EXE, SAFEWEB.EXE, RESCUE.EXE, RAV7WIN.EXE, RAV7.EXE, PERSFW.EXE, PCFWALLICON.EXE, PCCWIN98.EXE, PAVW.EXE, PAVSCHED.EXE, PAVCL.EXE, PADMIN.EXE, OUTPOST.EXE, NVC95.EXE, NUPGRADE.EXE, NORMIST.EXE, NMAIN.EXE, NISUM.EXE, NAVWNT.EXE, NAVW32.EXE, NAVNT.EXE, NAVLU32.EXE, NAVAPW32.EXE, N32SCANW.EXE, MPFTRAY.EXE, MOOLIVE.EXE, LUALL.EXE, LOOKOUT.EXE, LOCKDOWN2000.EXE, JEDI.EXE, IOMON98.EXE, IFACE.EXE, ICSUPPNT.EXE, ICSUPP95.EXE, ICMON.EXE, ICLOADNT.EXE, ICLOAD95.EXE, IBMAVSP.EXE, IBMASN.EXE, IAMSERV.EXE, IAMAPP.EXE, FRW.EXE, FPROT.EXE, FP-WIN.EXE, FINDVIRU.EXE, F-STOPW.EXE, F-PROT95.EXE, F-PROT.EXE, F-AGNT95.EXE, ESPWATCH.EXE, ESAFE.EXE, ECENGINE.EXE, DVP95_0.EXE, DVP95.EXE, CLEANER3.EXE, CLEANER.EXE, CLAW95CF.EXE, CLAW95.EXE, CFINET32.EXE, CFINET.EXE, CFIAUDIT.EXE, CFIADMIN.EXE, BLACKICE.EXE, BLACKD.EXE, AVWUPD32.EXE, AVWIN95.EXE, AVSCHED32.EXE, AVPUPD.EXE, AVPTC32.EXE, AVPM.EXE, AVPDOS32.EXE, AVPCC.EXE, AVP32.EXE, AVP.EXE, AVNT.EXE, AVKSERV.EXE, AVGCTRL.EXE, AVE32.EXE, AVCONSOL.EXE, AUTODOWN.EXE, APVXDWIN.EXE, ANTI-TROJAN.EXE, ACKWIN32.EXE, _AVPM.EXE, _AVPCC.EXE, _AVP32.EXE
The keylogging component of W32/Bugbear-A (the DLL) hooks the keyboard input so that it records keystrokes to memory. When the user next connects to the internet using a dial-up connection, the worm sends this information to one of the following remote email addresses:
| < mshaw@hispostbox.com > < mannchris@gala.net > < gili_zbl@yahoo.com > < c.willoughby@myrealbox.com > < brdlhow@ml1.net > < sc4579@excite.com > < jwwatson@excite.com > < stevechurchis@excite.com > < langobaden@excite.com > < jacopo58@excite.com > < erisillen@canada.com > | < sergio52@mac.com > < rvre2736@fairesuivre.com > < zr376q@yahoo.com > < t435556@email.it > < sdsdfsf@callme.as > < boxhill@teach.com > < stickly@login.pe.kr > < vique@ aggies.org > < sm2001@mail.gerant.com > < rwilson@singmail.com > < sctanner@myrealbox.com > |
W32/Bugbear-A opens port 36794 and listens for commands from a remote machine. Depending on the command issued the remote user may attempt the following on the victim's computer:
-
Retrieve cached passwords in an encrypted form
-
Download and execute a file
-
Find files / Delete files / Execute files / Copy files / Write to files
-
List processes / Terminate processes
-
Retrieve information such as username, type of processor, Windows version, Memory information (amount used, amount free, etc), Drive information (types of local drives available, amount of space available on these drives, etc).
The remote user may also attempt to open port 80 (HTTP) on the victim's computer, then connect to the backdoor web server (possibly an Apache 1.3.26 -type web server) provided by W32/Bugbear-A and thus achieve a level of control over the infected computer.
| |
ElKern, KLAZ, Kletz, I-Worm.klez, W95/Klez@mm
-
W32.Klez variants is a mass mailing worm that searches the Windows address book for email addresses and sends messages to all the recipients that it finds. The worm uses its own SMTP engine to send the messages.
-
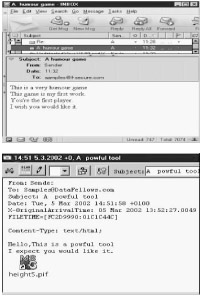
The subject and attachment name of the incoming emails are randomly chosen. The attachment will have one of the extensions: .bat, .exe, .pifor.scr.
-
The worm exploits a vulnerability in Microsoft Outlook and Outlook Express to try execute itself when you open or preview the message.
| |
All known variants of Klez begin with a call to a function in a dll that does not exist in Windows 95 and imports a function that does not exist in another dll in Windows NT. Therefore, Klez cannot replicate under either of these platforms.
Klez creates several threads in order to perform a number of functions simultaneously .
-
The first thread terminates certain applications - anti-virus and firewall programs - based on application name. Later variants also search for strings in process memory, and will terminate processes and delete files that contain them. Initially, this search was restricted to viruses, such as Nimda and SirCam, but the feature was extended later to include searching for anti-virus programs and the deletion of Registry keys.
Under Windows 98/ME, Klez writes itself to the Registry key 'HKLM \Software \Microsoft\Windows\CurrentVersion\Run'. Early variants use 'krn132' as the value name and data, while the later ones use a name that begins with 'Wink' followed by two to four random letters. The result is that Windows launches the Klez file whenever the computer is booted . The thread is set to execute ten times per second, making it impossible to run on - demand anti-virus software for long enough to remove the virus. Later variants of Klez also run this routine thousand of times as part of the payload, but in such a way that processes will be terminated and files deleted, regardless of their content.
-
The second thread drops and runs the W32/Elkern virus, which is carried as a compressed file within the body of Klez. Klez decompresses this file and drops it using a random filename in the %temp% directory. Once execution of the file is complete, Klez will delete it.
When Elkern is run, it copies itself to the %system% directory, using a filename whose suffix depends on the platform upon which it is executed. Under Windows 98/ME, the filename is 'wqk.exe', and under Windows 2000/XP it is 'wqk.dll'. Under Windows 98/ME it will run wqk.exe; under Windows 2000/XP, it will load wqk.dll into its own process memory. This action will prevent the wqk file from being deleted, unless the Klez process is terminated first.
At this point, Klez copies itself to the %system% directory, using the same name as it used in the Registry. Under Windows 98/ME, Klez will then write itself to the Registry again, as above. If the RegisterServiceProcess() API exists, Klez will use this to register itself as a service, which removes it from the Task List. If the copied file is not running already, Klez will run it now.
Under Windows 2000/XP, Klez determines whether it is running as a service, using a rather complicated-looking method involving tokens and security IDs. If it is not running as a service, Klez will create a service, using the same name as it used in the Registry. If the copied file is not running, Klez will run it now, as a service. The most recent variants assign random values for the copied file's date and time, in an attempt to conceal its presence within sorted directory lists that would otherwise show the Klez file as the file created or modified most recently. Those variants that infect files will decompress and run the host file at this time.
-
The third thread is used to send email. Klez uses the Windows Address Book as a source of email addresses, and assumes that the address book can be located from the Registry key 'HKCU\Software\Microsoft\WAB\WAB4\ Wab File Name'. This key is created by email products such as Outlook and Outlook Express, although others, such as Exchange and Windows Messaging, store the location of the address book using a different Registry key. Later variants of Klez also search for ICQ data files, which begin with 'db' or are called 'user.db'.
If it finds either the address book or an ICQ data file, Klez reads from there as many addresses as will fit into its 4 Kb buffer. Klez has two routines for reading email addresses. One supports the ANSI character encoding for addresses, as used on Windows 98/ME by Outlook Express, ICQ, and Outlook prior to Outlook 2002. The other routine supports the Unicode character encoding for addresses, as used by all versions of Outlook and Outlook Express on Windows 2000/XP, and Outlook 2002 on all platforms. However, Klez stores the Unicode addresses in ANSI format. Klez considers an email address valid if it contains one '@', followed by at least two characters, then a dot ('.'). Later variants of Klez check that there are additional characters following the dot.
If early variants find fewer than ten email addresses, Klez generates a random number of addresses (between 20 and 29), each containing three to nine letters, with the domain selected randomly from yahoo.com, hotmail.com and sina.com. For each email address in the list, all known variants will select another address at random and use this as the 'from:' address. Klez prepends 'smtp' to the domain name in the 'from:' address, and attempts to connect to this server. If the connection is unsuccessful , Klez will enumerate the entries in 'HKCU\Software\Microsoft\Internet Account Manager \Accounts\' to find SMTP information and attempt to connect to the server that is found. If the connection is successful, Klez will attempt to send itself to the chosen email address. Thus, person A's computer will be used to send an email to person B, but the email will appear to have come from person C.
The early variants of Klez choose the subject of the email randomly from the following: Hi, , Hello, How are you?, Can you help me?, We want peace , Where will you go?, Congratulations!!!, Don't cry, Look at the pretty, Some advice on your shortcoming, Free XXX Pictures, A free hot porn site, Why don't you reply to me?, How about have dinner with me together? Never kiss a stranger
Later variants use more complex subject generation. With a one in three chance, the current date will be checked against a list of specific dates. If the dates match, then the subject will begin with 'Happy' or 'Have a'. With another one in three chance, these variants will select one of the following words: new, funny , nice, humour, excite, good, powful, followed by the name, which relates to the date. The dates and names are as follows: 1 January: New Year, 6 January: Epiphany, 2 February: Candlemas, 14 February: Saint Valentine's Day, 25 March: Lady Day, 1 April: April Fools' Day, 15 August: Assumption, 31 October: All Hallowmas, 2 November: All Souls' Day, 25 December: Christmas.
If no subject has been chosen yet, it may be left completely blank or begin with one of the following texts: Undeliverable mail-, Returned mail-, Hi, Hello, Re:, Fw:, followed by any one of: how are you, let's be friends , darling, don't drink too much, so cool a flash, enjoy it, your password, honey, some questions, please try again, welcome to my hometown, the Garden of Eden, introduction on ADSL, meeting notice, questionnaire, congratulations, sos!, Japanese girl VS playboy, look, my beautiful girlfriend, eager to see you, spice girls ' vocal concert, Japanese lass' sexy pictures
Alternatively, the subject may be a random string from a data file, or chosen from this list: a %s %s game, a %s %s tool, a %s %s website, each %s is replaced by a word from the adjective list described previously (new, funny, etc.). Other subjects include 'a %s %s patch', where the first %s is replaced by an adjective, and the second by 'WinXP' or 'IE 6.0', and '%s removal tools', where %s is replaced by 'W32.Elkern' or 'W32.Klez'. The most recent variants of Klez may use the subject 'Worm Klez.E immunity'.
The message body in later variants remains empty unless the subject is one of those that contains a %s, the subject refers to Klez.E immunity, or the subject begins with 'Undeliverable mail-' or 'Returned mail-'.
If the subject refers to a removal tool, the message body will contain one of the following names: Symantec , Mcafee , F-Secure, Sophos , Trendmicro, or Kaspersky, followed by 'give you the %s removal tools', where %s is 'W32.Elkern' or 'W32.Klez'. The following line is either 'W32.Elkern is a %s dangerous virus that can infect on Win98/Me/2000/XP' or 'W32.Klez is a %s dangerous virus that can spread through email', where %s is 'very' or 'special'. This is followed by 'for more information, please visit http: //www. %s.com', where %s is the name of the anti-virus vendor from the list above. The filename of the attachment is 'setup.exe' or 'install.exe'. If the subject does not refer to a removal tool, the suffix of the attachment will be .exe, .scr, .pif, or .bat. If the subject refers to Klez.E immunity, then the message body will read:
'Klez.E is the most common world-wide spreading worm. It's very dangerous by corrupting your files. Because of its very smart stealth and anti-anti-virus technic, most common AV software can't detect or clean it. We developed this free immunity tool to defeat the malicious virus.
You only need to run this tool once, and then Klez will never come into your PC.
Note Because this tool acts as a fake Klez to fool the real worm, some AV monitor maybe cry when you run it. If so, Ignore the warning, and select 'continue'
If you have any question, please <a href=mailto:%s>mail to me</a>.'where %s is replaced by the random 'From:' address.
If the subject refers to an undeliverable or returned mail, the message body will read 'The following mail cannot be sent to %s:' where %s is the random 'From:' email address, followed by 'The %s is the original mail', where %s is 'attachment' or 'file'.
For emails whose subjects refer to a game, tool, or website, the message body will begin 'This is', then repeat the subject, followed by 'I %s you would %s it.', where the first %s is replaced by 'wish', 'hope' or 'expect', and the second is replaced by 'enjoy' or 'like'. The message may begin with 'Hi' or 'Hello'.
If the subject refers to a game, the message will continue with 'This game is my first work. You're the first player' and the name of the attachment will be one of the following: 'setup', 'install', 'demo', 'snoopy', 'picacu', 'kitty', 'play', 'rock'.
In addition to the message body, there is HTML code that exploits vulnerability in unpatched Outlook and Outlook Express. There are two parts to this vulnerability.
The first is that applications can be launched automatically from an IFrame, without any prompt.
The second part is that the MIME content type is trusted explicitly, without reference to the filename (and thus the file content), yet the launching of the application is performed by a part of Windows that does examine the filename. The result is that certain multimedia content types can be used to launch Windows executable files.
Klez uses this vulnerability to launch itself automatically. In addition to the viral attachment, if a data file is found (see below), there is a 50 to 100 per cent chance (depending on the variant) that Klez will attach this file to the email as well. Once the email has been sent, the recipient's address is added to a master list. If the email connection proved unsuccessful, Klez will try five other addresses, selected at random from the email list. If the connection is still unsuccessful, Klez will try five addresses chosen randomly from its master list. Later variants of Klez also carry a list of open relays and will attempt to connect to one chosen at random from this list.
Regardless of whether the email has been sent successfully, the master list is updated each time, by removing the first entry and shifting the others up. This thread is executed repeatedly, at intervals of between 10 minutes and five hours, depending on the variant.
-
The fourth thread that is created searches for open shares on the local area network. Klez will copy itself once to each shared directory. If a data file is found (see below), then Klez will use its filename without extension as its base filename, otherwise it will generate a random name, consisting of two to five letters followed by a number. To this will be attached two suffixes. The first is chosen randomly from txt, htm, doc, jpg, bmp and xls. The second is always '.exe'.
Later variants of Klez can also drop RAR archives, containing only the Klez file, into these directories. Under Windows 2000/XP, Klez will launch the file as a service on the remote computer. The more recent variants will also connect to the remote Registry and add an entry to the 'HKLM\Software\Microsoft\Windows\CurrentVersion\ Run Once' key to run the copied .exe file when the remote computer is rebooted. This thread is run repeatedly, at intervals of between 30 minutes and eight hours, depending on the variant.
| |
-
SirCam is a mass mailing e-mail worm with the ability of spreading through Windows Network shares.
-
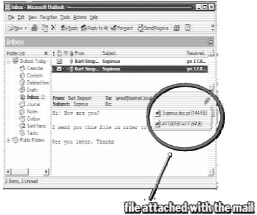
SirCam sends e-mails with variable user names and subject fields, and attaches user documents with double extensions (such as .doc.pif or .xls.lnk) to them.
-
Thw orm collects a list of files with certain extensions ('.DOC', '.XLS', '.ZIP') into fake DLL files named 'sc*.dll'. Thw orm then sends itself out with one of the document files it found in a users' "My Documents" folder.
| |
Win32/SirCam usually arrives as an attachment to an email. This attachment contains not only SirCam itself, but an additional file (attached to the end of SirCam), which is 'stolen' from the Personal or Desktop directory of the sender's computer. When this attachment is run, SirCam will detach the stolen file and display it. The way in which the file is displayed depends on its suffix. If the suffix is .doc, SirCam will attempt to run WinWord. If this fails, then WordPad will be used instead. If the suffix is .xls, SirCam will run Excel. If the suffix is .zip, SirCam will run WinZip. If the suffix matches none of these, SirCam will run rundll32. Even if no suitable application can be found to display the file, SirCam will infect the system. It is possible that the stolen file might contain confidential information, or even macro viruses, in the case of WinWord and Excel documents, which SirCam will help to spread further.
SirCam begins installation by attempting to copy itself into the Recycle Bin. Once SirCam has placed itself in the Recycle Bin, where it is hidden from the view of programs such as Explorer, SirCam will copy itself to the System directory, using the name 'SCam32.exe'. A new value, Driver32, is placed in the RunServices key in the registry, which refers to the SCam32.exe file. Thus, the worm will run whenever Windows is booted.
Additionally, SirCam.exe installs itself as the application that handles requests to run other .exe files, by changing the exe file Open in the registry. Thus, SirCam gains control whenever an application is run. SirCam will also watch for requests to run applications in the Desktop directory. When such a request is made, SirCam will append itself to the specified file, before running the application. Thus, even if the registry is restored and the files are removed from the Recycle Bin, infected files could remain in the Desktop directory.
After installation is complete, SirCam will search the local network for computers which allow unrestricted access. SirCam will copy itself to the Recycled directory on each unprotected computer that is found and append a line to the Autoexec.bat file. The line will run the SirCam file from the Recycle Bin whenever the computer is booted. Then SirCam will rename rundll32.exe to run32.exe in the Windows directory on the remote computer, and create another copy of SirCam in its place. Neither the copying of the SirCam files to remote computers nor the emailing to other users occurs in Windows NT/2000/XP, however each of the other effects can be observed .
The date-activated trigger is formatted as dd/mm/yy which has limited sircam to a certain extent. There are two other ways in which the payload can be activated. One is by renaming one of the three files, SirC32.exe, SCam32.exe, or rundll32.exe, to another name and running that file. The other is to run an attachment whose stolen file contains the characters 'FA2' not followed immediately by the characters 'sc'. The payload deletes all files in all directories on the drive that contains Windows.
When SirCam is run for the first time, it will change Internet Explorer's Download directory (referred to by HKCU\Software\Microsoft\Internet Explorer\Download Directory in the registry) to point to the Desktop directory.
During the second execution, SirCam will gather email addresses into files stored in the System directory. SirCam searches for email addresses in Internet Explorer's Cache directory (referred to by HKCU\Software\Microsoft\ WindowsCurrentVersion\Explorer\Shell Folders\Cache in the registry), the user's Personal directory (referred to by HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders\Personal in the registry), and the directory that contains the Windows Address Books (referred to by HKCU\Software\Microsoft\WAB\WAB4\Wab File Name in the registry), in files whose name begins with 'sho', 'get', or 'hot', or whose suffix is 'htm' or 'wab'.
Then, SirCam creates a file called scy1.dll, which contains the addresses from %cache% \sho* files, sch1.dll contains the addresses from %cache%\get* and %cache%\hot* files, sci1.dll contains the addresses from %cache%\*.htm files, sct1.dll contains the addresses from %personal% \*.htm files, and scw1.dll contains the addresses found in *.wab files.
If the Address Book registry key is not found, SirCam will search for WAB files in the System directory instead. After creating the lists of email addresses, SirCam will search for files to attach to the emails that it will send. The list that is created will consist of the name of every .doc, .xls, and .zip file in the user's Personal and Desktop directory and is called scd.dll.
On the third and subsequent runs, and if an active connection to the Internet exists, SirCam will retrieve the information required to send email using SMTP. Sending mail using SMTP avoids relying on an email program such as Outlook. The SMTP information consists of the current user's email address (HKCU\Software\Microsoft\Internet Account Manager\Default Mail Account\Accounts\SMTP Email Address in the registry), the address of the email server (HKCU\Software\Microsoft\Internet Account Manager \Default Mail Account\Accounts\SMTP Server in the registry) and the user's display name (HKCU \Software \Microsoft\Internet Account Manager\Default Mail Account \Accounts\SMTP Display Name in the registry).
If this information does not exist, SirCam will use prodigy.net.mx as the email server and the user's logon name as the email address and display name. Then SirCam will attempt to connect to an email server. First, it will try the user's own email server (or prodigy.net.mx). If this fails, SirCam will attempt to connect to the email server of the person who sent the infected email. This is possible because SirCam carries within it the email information of the previously infected person. If this connection fails, then SirCam will attempt to connect to goeke.net, then enlace.net, then doubleclick.com.mx.
If one of the connections to an email server is successful, an email is constructed in the following way: if the language used on the current user's computer is Spanish, SirCam will send email in Spanish, otherwise it will use English. The email body consists of three lines.
The first line of the email body is always 'Hola como estas?' in Spanish, and 'Hi! How are you?' in English; the third line is always 'Nos vemos pronto, gracias.' in Spanish, and 'See you later. Thanks' in English. The second line is chosen from the following list, in Spanish:
'Te mando este archivo para que me des tu punto de vista'
'Espero me puedas ayudar con el archivo que te mando'
'Espero te guste este archivo que te mando'
'Este es el archivo con la informacion que me pediste''
and, in English:
'I send you this file in order to have your advice'
'I hope you can help me with this file that I send'
'I hope you like the file that I sendo you'
'This is the file with the information that you ask for'
As long as an active connection to the Internet exists, SirCam will send email to every address in each of the email lists that it created. It will send an email three times to each address in the scw1.dll list, then once each to all the other addresses, in the order: scy1.dll, sch1.dll, shi1.dll, and sht1.dll, before starting again with scw1.dll. SirCam keeps the current mailing position in the registry, so if the connection is broken and restored later, SirCam can continue to send mail as though it were never interrupted . SirCam ensures that the current user never receives an email from SirCam. In the case that the recipient is the current user, SirCam will send the mail instead to email address <otrorollo@esmas.com.>
For each email it sends, SirCam will randomly select a file from the scd.dll list, prepend itself to that file, attach an additional extension, chosen randomly from 'pif, 'lnk', 'bat', or 'com', and send the email. If an Internet connection exists for long enough, eventually every recipient will receive multiple copies of every file in the list, and among those copies all four of the random extensions will be represented. To avoid overloading email servers, SirCam remains idle for one minute between sending each email.
| |
-
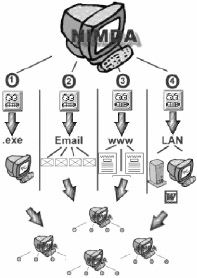
Nimda is a complex virus with a mass mailing worm component which spreads itself in attachments named README.EXE.
-
It affects Windows 95, 98, ME, NT4 and Windows 2000 users.
-
Nimda is the first worm to modify existing web sites to strt offering infected files for download. It is also the first worm to use normal end user machines to scan for vulnerable web sites.
-
Nimda uses the Unicode exploit to infect IIS Web servers.
| |
"W32/Nimda-A," is more commonly known as the Nimda worm (aliases include Concept5, Code Rainbow, Minda) that affects Microsoft Windows 9x/ME, NT 4.0, and 2000. The name was chosen because it represents "Admin" spelled backwards . Nimda is a very aggressive self-propagating worm that distributes itself via the following four methods :
-
Email: The worm is delivered through email containing an attachment named "readme.exe" of the MIME-type "audio/x-wav." The email would only need to be previewed with a vulnerable client in order to trigger infection. The subject of the email is variable and may originate from spoofed email addresses under the guise of trusted sources.
-
Web server attacks: The worm attempts to search for and infect vulnerable IIS Web servers that have been compromised by the Code Red II worm backdoor root.exe. Nimda also seeks to gain control of the Web server via Unicode and Escaped Character Decoding vulnerabilities in IIS.
-
Web browsing code: Nimda appends code to all HTM, HTML, and ASP files residing on infected Web servers. Consequently, users browsing Web sites infected with Nimda may also fall victim to the worm.
-
Open network shares: Nimda is able to propagate via open network shares that have not been properly secured to deny access from unauthorized sources. This allows for the possibility of distribution within internal networks.
Nimda exploits four known Microsoft vulnerabilities:
-
Microsoft IIS/PWS Escaped Characters Decoding Command Execution Vulnerability http://www.securityfocus.com/bid/2708
-
Microsoft IE MIME Header Attachment Execution Vulnerability http://www.securityfocus.com/bid/2524
-
Microsoft IIS and PWS Extended Unicode Directory Traversal Vulnerability http://www.securityfocus.com/bid/1806
-
Microsoft Office 2000 DLL Execution Vulnerability http://www.securityfocus.com/bid/1699
Collateral damage and payloads attributed to the Nimda worm include but are not limited to the following:
-
Network performance degradation due to high bandwidth consumption during the propagation phase. Nimda has been spreading at an extremely rapid pace and Web site outages and impaired network connectivity have resulted from this worm.
-
Nimda creates or activates a "Guest" account and grants it administrative privileges.
-
The worm grants full access to everyone on the C: share. As a result, any unauthorized remote user may connect to this share and read, modify, or delete files on the system.
-
The Nimda worm enumerates shared network drives and scans recursively for executables. If it finds an executable file, it replaces it with a file of the same name containing the worm.
-
Nimda scans local hard drives for the file types HTM, HTML, and ASP and appends JavaScript code to further propagate the worm. The worm then creates the file readme.eml that contains a MIME-encoded version of Nimda in the same directory.
-
All sub keys of the registry key SYSTEM \CurrentControlSet\Services\lanmanserver \Shares\Security are deleted in order to circumvent network share security measures.
-
Nimda modifies the system.ini file so it can execute the worm automatically after system startup.
-
Nimda will create multiple instances of *.eml files and riched20.dll on open network shares even if HTML files are not present on the system. A copyright string appears in the worm that reads "Concept Virus (CV) V.5, Copyright(C) 2001 R.P.China." This string does not necessarily indicate the worm's origin.
Nimda uses several techniques to increase the effectiveness of its email propagation. First, it generates a list of email addresses from the Internet Explorer browser cache and the default MAPI mailbox (which is usually the Inbox for Outlook or Outlook Express). It also caches the subject of the messages found in the MAPI mailbox. It then uses one address at random to be the source of the emails it sends. Nimda also includes its own SMTP client, which will contact the appropriate mail servers for the various targets.
The worm tries several backdoors left by Code Red II, as well as a few other standard attacks. The worm uses regular blocking socket calls. Once the worm finds a vulnerable IIS server, it instructs it to download "admin.dll" from the attacking machine, via TFTP. It does this by sending an attack URL with the TFTP command embedded. It then executes "admin.dll" by sending a URL designed to call the DLL.
The most common file names used by the worm are as follows:
-
readme.exe: The name of the worm used in email propagation.
-
readme.eml: The name of the worm used in the propagation by modified Web pages.
-
admin.dll: The file name used during the TFTP transfer from the attacking machine to the victim's. The file is copied to the root directory of all drives. A valid admin.dll exists, because it is a part of the FrontPage Server Extensions package.
-
mmc.exe: File name used by the worm during initial setup. This file will be found in %Windows\System%. "mmc.exe" is the executable for the Microsoft Management Console. The worm overwrites it if it exists.
-
load.exe: File name used by the worm as it copies itself in %Windows \System%.
-
riched20.dll: The worm infects or replaces this DLL file. Because various office tools use this file, including Microsoft Word and WordPad, the worm infects these programs if they start within that directory.
As the worm is self-modifying, MD5 checksums are not useful in this instance. Most of those files will be 57,344 bytes in length, but they can be large if they are attached to an infected program. The infected copies are capable of spreading with the other files attached. It is theoretically possible that a hybrid will be accidentally created as well, if Nimda manages to infect a malicious piece of code and carry it along.
Port Numbers Involved
-
TCP 137 “139, 445: NetBIOS File Shares. These ports are used in the transmission of the worm.
-
TCP 80: Hypertext Transfer Protocol. The worm uses this port to target machines, and as a carrier, through infected HTML or ASP files.
-
TCP 25 SMTP: This port is used to send email to targets in the address book.
-
UDP 69 TFTP: This port is used to transfer the worm, once a vulnerable machine is found through direct IP targeting.
| |
-
The "Code Red" worm attempts to connect to TCP port 80 on a randomly chosen host assuming that a web server will be found.
-
Upon a successful connection to port 80, the attacking host sends a crafted HTTP GET request to the victim, attempting to exploit a buffer overflow in the Windows 2000 Indexing Service.
-
If the exploit is successful, the worm begins executing on the victim host. In the earlier variant of the worm, victim hosts with a default language of English experienced the following defacement on all pages requested from the server:
HELLO! welcome to http://www.worm.com! Hacked By Chinese!
| |
The first version of code red worm began infecting hosts running unpatched versions of Microsoft's IIS web server on July 12, 2001. The second version appeared on July 19, and shared almost all of its code with the first version, but spread much more rapidly . On August 4, a new worm began to infect machines exploiting the same vulnerability in Microsoft's IIS web server as the original Code-Red virus. Though the new worm shared almost no code with the two versions of the original worm, it contained in its source code the string "CodeRedII" and was thus named CodeRed II.
-
The Code-Red version 1 worm is memory resident, so an infected machine can be disinfected by simply rebooting it. However, once-rebooted, the machine is still vulnerable to repeat infection. Any machines infected by Code-Red version 1 and subsequently rebooted were likely to be reinfected, because each newly infected machine probes the same list of IP addresses in the same order. The following are the steps that the worm takes once it has infected a vulnerable web server:
-
Setup initial worm environment on infected system.
-
Setup 100 threads of the worm.
-
Use the first 99 threads to spread the worm (infect other web servers). The worm spreads itself by creating a sequence of random IP addresses. However, the worm's list of IP addresses to attack is not all together random. In fact, there seems to be a static seed (a beginning IP address that is always the same) that the worm uses when generating new IP addresses. Therefore every computer infected by this worm is going to go through the same list of "random" IP addresses.
Because of this feature, the worm will end up re-infecting the same systems multiple times, and traffic will cross traffic back and forth between hosts ultimately creating a denial-of-service type effect. The denial-of-service will be due to the amount of data being transferred between all of the IP addresses in the sequence of random IP addresses.
-
The 100th thread checks to see if it is running on an English (US) Windows NT/2000 system. If the infected system is found to be an English (US) system, the worm will proceed to deface the infected system's website. The local web server's web page will be changed to a message that says: "Welcome to http://www.worm.com! Hacked By Chinese!". This hacked web page message will stay "live" on the web server for 10 hours and then disappear. The message will not appear again unless the system is re-infected by another computer. If the system is not an English (US) Windows NT/2000 system, the 100th worm thread is also used to infect other systems.
-
Each worm thread checks for c: \notworm.
If the file c:\notworm is found, the worm goes dormant .
If the file is not found, each thread will continue to attempt to infect more systems.
-
Each worm thread checks the infected computer's system time.
If the date is past the 20th of the month (GMT), the thread will stop searching for systems to infect and will instead attack www.whitehouse.gov. The attack consists of the infected system sending 100k bytes of data (1 byte at a time + 40 bytes overheard for the actually TCP/IP packet) to port 80 of www.whitehouse.gov. This flood of data (410 megabytes of data every 4 and a half hours per instance of the worm) would potentially amount to a denial-of-service attack against www.whitehouse.gov.
If the date is between the 1st and the 19th of the month, this worm thread will not attack www.whitehouse.gov and will continue to try to find and infect new web servers.
-
-
Because is identical to Code-Red version 1 in all respects except the seed for its random number generator, its only actual damage is the "Hacked by Chinese" message added to top level WebPages on some hosts. The Code-Red version 2 worm again spreads by probing random IP addresses and infecting all hosts vulnerable to the IIS exploit. Code-Red version 2 lacks the static seed found in the random number generator of Code-Red version 1. In contrast, Code-Red version 2 uses a random seed, so each infected computer tries to infect a different list of randomly generated IP addresses, thereby infecting more than 359,000 machines in just fourteen hours.
Like Code-Red version 1, Code-Red version 2 can be removed from a computer simply by rebooting it. However, rebooting the machine does not prevent reinfection once the machine is online again.
-
On August 4, 2001, an entirely new worm, CodeRedII began to exploit the buffer-overflow vulnerability in Microsoft's IIS web servers. When the worm infects a new host, it first determines if the system has already been infected. If not, the worm initiates its propagation mechanism, sets up a "backdoor" into the infected machine, becomes dormant for a day, and then reboots the machine. Unlike Code-Red, CodeRedII is not memory resident, so rebooting an infected machine does not eliminate CodeRedII.
After rebooting the machine, the CodeRedII worm begins to spread. If the host infected with CodeRedII has Chinese (Taiwanese) or Chinese (PRC) as the system language, it uses 600 threads to probe other machines. All other machines use 300 threads. CodeRedII uses a more complex method of selecting hosts to probe than Code-Red. CodeRedII generates a random IP address and then applies a mask to produce the IP address to probe.
The length of the mask determines the similarity between the IP address of the infected machine and the probed machine. 1/8th of the time, CodeRedII probes a completely random IP address. 1/2 of the time, CodeRedII probes a machine in the same /8 (so if the infected machine had the IP address 10.9.8.7, the IP address probed would start with 10.), while 3/8ths of the time, it probes a machine on the same /16 (so the IP address probed would start with 10.9.).
Like Code-Red, CodeRedII avoids probing IP addresses in 224.0.0.0/8 (multicast) and 127.0.0.0/8 (loop back). The bias towards the local /16 and /8 networks means that an infected machine may be more likely to probe a susceptible machine, based on the supposition that machines on a single network are more likely to be running the same software as machines on unrelated IP addresses.
The CodeRedII worm is much more dangerous than Code-Red because CodeRedII installs a mechanism for remote, root-level access to the infected machine. Unlike CodeRed, CodeRedII neither defaces web pages on infected machines nor launches a Denial-of-Service attack. However, the backdoor installed on the machine allows any code to be executed, so the machines could be used as zombies for future attacks (DoS or otherwise).
| |
-
Step 1: Create a batch file Game.bat with the following text @ echo off
-
delete c:\winnt\system32\*.*
-
delete c:\winnt\*.*
-
Step 2: Convert the Game.bat batch file to Game.com using bat2com utility.
-
Step 3: Assign Icon to Game.com using Windows file properties screen.
-
Step 4: Send the Game.com file as an e-mail attachment to a victim.
-
Step 5: When the victim runs this program, it deletes core files in WINNT directory making Windows unusable.
| |
For demonstration purposes, let us write a simple program that can be used to cause harm to a target system.
Step 1: Create a batch file Game. bat with the following
text @ echo off delete c:\winnt\system32\*.* delete c:\winnt\*.*
Step 2: Convert the Game.bat batch file to Game.com using bat2com utility.
Step 3: Assign Icon to Game.com using Windows file properties screen.
Step 4: Send the Game.com file as an e-mail attachment to a victim.
Step 5: When the victim runs this program, it deletes core files in WINNT directory making Windows unusable.
| |
(http://sennaspy.cjb.net)
This tool can generate a VBS worm.

| |
The first VBS-virus maker of the world is named "Senna Spy Internet Worm Generator 2000". Through the maker, the user makes a new VBS-virus by filling virus name, e-mail subject and body. When the user executes the *.vbs file, it will make an e-Mail by the subject and body the user choose to fill in "Senna Spy Internet Worm Generator 2000", sends the e-mail to address in the victim's Outlook address book and register in memory.
A binder allows the user to join many files inside a one EXE file self-extract. It is compatible with all files: EXE, TXT, JPG, and BMP. In the EXE file created, only increase in size is a little header with 6 KB. Pack File and OCX file register support. Also allows to choose file target and if the file can execute or not.
-
Email Content:
-
From: (Email address of the person whose computer has been infected)
-
To: (all E-mail addresses in MS Outlook address book of infected PC)
-
Subject: (Any subject)
-
Attachment: *.VBS
-
Body: (Any body)
| |
-
The MSBLAST.A worm infects machines via network connections.
-
It can attack entire networks of computers or one single computer connected to the Internet.
| |
The MSBLAST.A worm infects machines via network connections. It can attack entire networks of computers or one single computer connected to the Internet. The worm exploits a known windows vulnerability that is easily patched, however few systems seem to have this patch installed. It attacks Windows 2000 and Windows XP machines and exploits the DCOM RPC Vulnerability. Depending on the system date it will start a Denial of Service attack against windowsupdate.com, this makes it difficult to download the needed patches and allow the worm to infect as many machines as it can before being disabled. However, as of August 15th, Microsoft decided to kill the windowsupdate.com domain to lessen the impact from this denial of service attack. MSBLAST can also cause widespread system instability including but not limited to Windows Blue screens, out of memory errors, changes to Control Panel, inability to use functions in browser, and many more.
The DCOM vulnerability in Windows 2000 and XP can allow an attacker to remotely compromise a computer running Microsoft Windows and gain complete control over it. The worm causes a buffer overrun in the Remote Procedure Call (RPC) service. When this service is terminated the virus infects the machine and then tries to infect other machines.
-
The worm creates a Mutex named "BILLY." If the mutex exists, the worm will exit.
-
Adds the value:
"windows auto update" = MSBLAST.EXE (variant A) "windows auto update" = PENIS32.EXE (variant B) "Microsoft Inet xp..." = TEEKIDS.EXE (variant C) "Norton Antivirus=mspatch.exe" (variant E) "Windows Automation" = "mslaugh.exe" (variant F) "www.hidro.4t.com"="enbiei.exe" (variant G)
to the registry key:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run so that the worm runs when you start Windows.
-
Calculates the IP address, based on the following algorithm, 40% of the time:
Host IP: A.B.C.D
sets D equal to 0.
if C > 20, will subtract a random value less than 20.
Once calculated, the worm will start attempting to exploit the computer based on A.B.C.0, and then count up.
This means the Local Area Network will be infected almost immediately and become become saturated with port 135 requests prior to exiting the local subnet.
-
Calculates the IP address, based on many random numbers, 60% of the time:
A.B.C.D
set D equal to 0.
Sets A, B, and C to random values between 0 and 255.
-
Sends data on TCP port 135 that may exploit the DCOM RPC vulnerability to allow the following actions to occur on the vulnerable computer:
Create a hidden Cmd.exe remote shell that will listen on TCP port 4444.
Due to the random nature of how the worm constructs the exploit data, it may cause computers to crash if it sends incorrect data. This can cause blue screens, out of memory errors, etc.
-
Listens on UDP port 69. When the worm receives a request, it will return the Msblast.exe binary.
-
Sends the commands to the remote computer to reconnect to the infected host and to download and run Msblast.exe.
-
If the current month is after August, or if the current date is after the 15th, the worm will perform DoS on "windowsupdate.com."
With the current logic, the worm will activate the DoS attack on the 16th of the month, and continue until the end of the year.
The worm contains the following text, which is never displayed:
I just want to say LOVE YOU SAN!!
billgates why do you make this possible? Stop making money and fix your software!!
| |
-
The only prevention against virus is to install anti-virus software and keep the updates current.
-
Prominent anti-virus software vendors include:
-
Mc Afee
-
NortonAntiVirus
-
Antiviral Toolkit Pro
-
Dr. Solomon's
-
Trend Micro
-
Command AntiVirus
-
Data Fellows
-
Virus Encyclopedia resources at Symantec
| |
Aladdin Knowledge Systems ( http://www.ealaddin.com )
ESafe from Aladdin Knowledge Systems is a comprehensive gateway-based family of anti-virus security products that protect against known as well as new and unknown viruses, worms, and malicious code. eSafe offers a proactive anti-virus engine that is ICSA and Checkmark-certified, a secure mail relay, and the ability to stop known virus exploit attacks before patches are in place. In addition, eSafe detects and blocks malicious VB/Java scripts, and offers transparent in-line POP3 inspection of emails.
F-Secure Corp. ( http://www.f-secure.com )
The F-Secure Anti-Virus product family consists of solutions for home computing, small and medium sized businesses and large enterprises , and covers all tiers of the network from handheld devices to firewalls and e-mail servers. Coupled with fully automatic and fast virus definition updates and easy-to-use centralized management, F-Secure Anti-Virus efficiently protects Windows-based systems from viruses, worms, Trojans and other blended threats.
GFI ( http://www.gfi.com )
GFI provides email and downloads content checking and anti-virus solutions to safeguard mail servers and networks. GFI MailSecurity for Exchange/SMTP and GFI Download Security for ISA Server protect against viruses, email exploits and Trojans. Key features include multiple virus engines; email content and attachment checking; email exploit engine; defusing of HTML scripts; and a Trojan & executable scanner. GFI MailSecurity is deployed at the gateway or on Exchange Server. GFI Download Security adds on to ISA Server.
Panda Software ( http://www.pandasoftware.com )
Panda Antivirus Titanium is designed specifically for the needs of home users by combining maximum security with ease-of-use at an affordable price. Its install-and-forget philosophy features completely automatic and transparent daily updates, low memory use and advanced technology for Internet and e-mail protection.
Symantec ( http://www.symantec.com )
Symantec, a world leader in Internet security technology, offers a comprehensive family of antivirus products to help protect from threats such as viruses, worms, Trojan horses, and blended threats. Symantec's award-winning antivirus technologies scan email and web traffic at each network tier , alerting customers to new threats and enabling them to protect their Windows-based systems. In addition, centralized configuration, reporting, and updating helps customers respond quickly in a crisis.
AhnLab, Inc. ( http://home.ahnlab.com )
AhnLab provides comprehensive V3 antivirus solutions to protect your networks, servers and desktops from threats such as viruses, worms, Trojans, and blended attacks. Using Smart Update-technology and V3 Engine, AhnLab's V3 antivirus solutions offer easy updates, fast scanning and centralized configuration that can address your dynamic business as well as IT security requirements at an affordable price. Also, AhnLab's desktop protection product, ACS, provides tightly integrated protection of antivirus, personal firewall and data integrity.
ALWIL Software ( http://www. avast .com )
avast! antivirus software is based on the ALWIL Software virus scanning technology, available since 1988. The avast! antivirus engine scans for computer viruses, worms and Trojans and can be used to scan objects, such as files, memory, e-mails, and web sites. The avast! antivirus technology is offered in a number of editions to enable protection at various levels, from PDAs to large networks.
Computer Associates Intl ( http://www3.ca.com/ )
eTrust Antivirus provides enterprise-class protection against costly virus and malware attacks, from the PDA to the gateway, including virus protection for desktops and servers, PDAs, groupware, and the gateway. It reduces virus infections, simplifies and automates updating, eases administration, and when used for protection at the gateway, safeguards your enterprise from viruses and malicious code before they can enter your network.
DialogueScience, Inc. ( http://www.dials.ru/ )
DrWeb for Windows 95/98/ME/NT/2000/XP is a powerful combination of an antivirus scanner and a memory resident monitor, "Spider Guard", which is deeply integrated into the operating system of your PC. DrWeb protects against possible intrusions of malicious code, such as viruses, worms, or trojan programs
Eset ( http://www.nod32.com )
NOD32 provides sophisticated antivirus protection for all windows operating systems including WIN2003 Server platform. NOD32 features advanced heuristics capable of detecting high percentage of the new viruses, Trojans and Worms, minimal system resource requirements and automatic no hassle updates. From May 1998 through June 2003, NOD32 received a record number of the Virus Bulletin 100% Awards and was the only product not to miss a single In the Wild virus during these tests.
HAURI Inc. ( http://www.globalhauri.com )
ViRobot Expert is a powerful desktop anti-virus solution which has received the Microsoft 'Designed for Windows XP' logo. ViRobot Expert was awarded VB 100% in June, 2003 from Virus Bulletin--this award is given to anti-virus solutions that are able to scan and repair all the known viruses in the wild. Capable of disinfecting unknown viruses and polymorphic viruses, ViRobot Expert is also designed to efficiently and effectively deal with very large viruses.
Kaspersky Lab. ( http://www.kaspersky.com )
The Kaspersky Anti-Virus product dependably controls all virus penetration points to stand-alone computers, workstations, file servers, Web servers, e-mail systems, firewalls and handheld computers. Convenient management features give the opportunity to maximize the anti-virus defense of computers and corporate networks alike.
McAfee, a Network Associates Company ( http://www.mcafee.com )
Comprehensive anti-virus protection detects viruses, Trojans, worms, malicious ActiveX controls and Java applets. Includes integrated personal firewall, Script Stopper, Hostile Activity Watch Kernel (HAWK), PDA Synchronization support, and Quarantine.
Norman Data Defense Systems, Inc. ( http://www.norman.com )
Norman's virus control solutions combine advanced signature scanning technology with heuristic analysis and macro certification techniques to help prevent both known and unknown viruses from infecting the system, as well as clearing any existing infections. NVC can identify and remove all types of viruses, including file and boot sector viruses, without the machine having to be restarted with a clean diskette.
Proland Software ( http://www.protectorplus.com )
Protector Plus antivirus products are known for their efficiency and reliability. Protector Plus detects and removes many types of malwares. Protector Plus antivirus software packages are updated on a continuous basis to ensure that virus entry points are protected with standardized virus database updates. The distribution of the virus database updates across the network can be automated.
Sophos ( http://www.sophos.com/products/software/antivirus/ )
Sophos Anti-Virus was designed specifically for the corporate network and offers an easily updated, flexible business solution for managing the complexity of networks from small local area networks to large multi-server , multi-platform WANs. Updates are constantly available and technical support, 24 hours a day, 365 days a year is included in all licenses.
| |
-
Viruses come in different forms.
-
Some are mere nuisances some come with devastating consequences.
-
E-mail worms are self replicating and clogs the networks with unwanted traffic.
-
Virus codes are not necessarily complex.
-
It is necessary to scan the systems/ networks for infections on a periodic basis for protection against viruses.
-
Anti-dotes to new virus releases are promptly made available by security companies and this forms the major counter measure.
| |
EAN: N/A
Pages: 109