3.2 Key types
|
3.2 Key types
So how does all this wonderful history impact our businesses and us? We need to get to present-day technology. Let us take one more look at the keys and how they are used in encryption.
There are basically two types of key-based algorithms: symmetric (secret-key) and asymmetric (public-key). The difference between these is that the symmetric keys use the same algorithms for encryption and decryption. The asymmetric algorithm uses a different key for encoding, another for creating the ciphertext, and another for decoding, or translating, the ciphertext into readable text. You may have heard of the term "public- private key." This is the technique that current encryption systems use within today's Internet environment.
Figure 3.1 shows how a public-private encryption system works. The system will generate a key pair for an assigned user. One public key and one private key are generated. These keys are mathematically related so that the private key can decrypt any messages that are encrypted by the public key. Here is an example of encrypting a message.
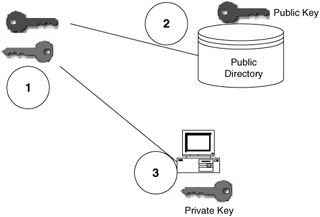
Figure 3.1
-
The public-private key pair is created.
-
The public key is placed into a public directory. A directory is a storage facility that can house user names and information about the users (e.g., e-mail address, phone numbers, and the public key).
-
The private key is stored in an area that only the designated user can access, such as his or her local PC or laptop. Note: This example does not address roaming users and the management of keys.
-
You can now send an encrypted message. From the directory you select the intended recipient's user name (this is managed via a software program).
-
The message is encrypted using the targeted user's public key (see Figure 3.2).
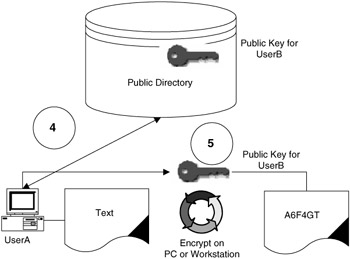
Figure 3.2 -
The data is now transferred between systems, applications, or e-mail as ciphertext. You now have an encrypted message that is difficult for a third party to read (see Figure 3.3). But how can we read the message? This is where the private key is used.
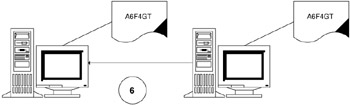
Figure 3.3 -
The user then retrieves the message and decrypts it with his or her private key. The private key may be locked with a password that only the user knows. The message is now readable by the targeted user (see Figure 3.4).
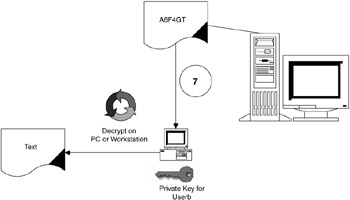
Figure 3.4
|