Work
|
| < Day Day Up > |
|
Each spammer has a unique method of sending spam and the success of each method varies greatly. As a spammer progresses and sends more spam their techniques and abilities grow. This forms a progressing trend; by reading spam I can quickly see how smart the spammer is, how long they have been in the game, and how much profit they make.
Following are some examples of random pieces of spam from my inbox. The quality varies from inexperienced to professional, but allows you to see how spam is composed.
Example 1: Mort gageQuotes
Let’s start with an example of spam that is trying to sell mortgage quotes, as seen in Figure 11.1
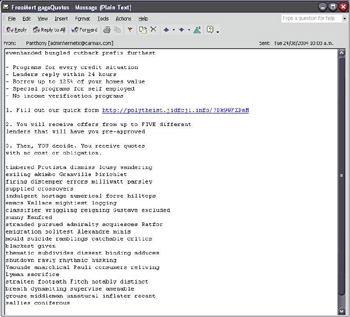
Figure 11.1: The Message
By studying this e-mail, we can figure out a fair amount of information about the spammer who sent this message. First, they tried to evade filters by adding large amounts of random data into the body. The words: “lenders,” “pre-approved,” “Borrow up to” and “credit situation” all increase the chances of spam filters filtering this. However, the 19 lines of random data decrease the suspect nature of the message by attempting to look legitimate. Notice the spelling of some of the words; it looks like the spammer is using words from highly specific scientific documents (i.e., not random words from the dictionary). “Dirichlet” and “Protista” are good examples of this; Dirichlet is the name of a mathematical number series and Protista is a type of organism, which is probably only found in a biology text. There are also many words that look like they may be part of someone’s name such as “Gustave,” “Pauli,” and “Alexandre.”
The domain of the Web site listed, http://polytheist.jidfcjl.info, is registered to Karin Zakerman who apparently lives in Russia. This looks like a fake identity that is probably registered with a stolen credit card because if you look at http://spamvertised.abusebutler.com/whois.php?dom=jidfcjl.info you see the following:
inetnum: 200.205.xx.xxx/xx aut-num: AS10429 abuse-c: EUA11 owner: Rafael XXXXX XXXXX XXXXXX ownerid: 290.626.xxx-xx
abusebutler.com has a copy of the whois record for this domain from August 1. In this we see that the domain was first registered to a Rafael X from Brazil on 08/11/2004. However, on the 22nd of that month the domain was either closed or transferred to Karin Zakerman in Russia. Notice the countries that are used as the domain holders—Russia and Brazil are not known for their anti-spam policies, and by housing the Domain Name Server (DNS) in a secure country the spammer is given a large amount of privacy. American DNS servers would house this name for a week at the most before closing it down, while Russian and Brazilian DNS servers are more lax.
Jidfcjl.info currently resolves to 200.205.xx.xxx. The whois information for this Internet Protocol (IP) shows that this host IP belongs to a Brazilian company called Telefonica Empresas (telefonicaempresas.net.br) and the IP is again registered under “Rafael.” A Google search shows that this is a known spam domain and that many other domains are run from jidfcjl.info. The entire domain is banned in many filters and is well known to be associated with sending spam. There are many complaints against TelefonicaEmpresas posted to various newsgroups and message boards. One such complaint (www.kayakforum.com/cgi-bin/Technique/index.cgi/noframes/read/15665 ) directly names the person in charge of the company and states that:
“telefonicaempresas.net.br , another Brazilian spam factory. The responsible person is Manual X, who I’m investing some money into a lawsuit against him and his company.”
Interestingly, it seems that many other people have received his spam; he seems to be selling many products including herbal pills, not just home loans.
Now let’s look at the header information and see if we can find out anything interesting about how the e-mail was sent:
Return-Path: <adminhermetic@carmax.com> Delivered-To: spammerx@spammerx.com Received: (qmail 25674 invoked by uid 509); 23 Aug 2004 14:26:58 -0000 Received: from adminhermetic@carmax.com by SpamBox by uid 89 with qmail-scanner-1.22 (clamdscan: 0.70. spamassassin: 2.63. Clear:RC:0(61.211.xxx.xx):SA:0(?/?):. Processed in 3.686726 secs); 23 Aug 2004 14:26:58 -0000 X-Spam-Status: No, hits=? required=? Received: from unknown (HELO spammerx) (61.211.xxx.xx) by 0 with SMTP; 23 Aug 2004 14:26:54 -0000 Message-ID: <abbleniiun.6650580993seqvuspzwk@Panthonyjsnnbrvjv.com> From: "Panthony" <adminhermetic@carmax.com> Date: Mon, 23 Aug 2004 21:59:59 +0000 To: spammerx@spammerx.com Subject: FreeMort gageQuotes Content-Transfer-Encoding: 8bit Content-Type: text/plain; charset=iso-8859-1 X-Qmail-Scanner-1.22: added fake MIME-Version header MIME-Version: 1.0
If you start at the top, you see various suspicious headers that don’t make much sense, and that clearly identify it as spam. Let’s start with:
Return-Path: adminhermetic@carmax.com
This is enough to cause suspicion because carmax.com is a legitimate online car site; this e-mail didn’t come from them. If we look at the HELO command we see:
Received: from unknown (HELO spammerx) (61.211.xxx.xx)
Interestingly, the HELO that server 61.211.xxx.xx sent was “HELO spammerx.” I find this of great interest because a host should not HELO my username; it should identify whom the server is that is trying to deliver the e-mail, not who the e-mail is being sent to.
This trick ensures that the HELO command is always unique; it will stop any watchful filtering that is looking for fake hotmail.com or yahoo.com addresses. Host 61.211.xxx.xx that sent the e-mail belongs to a131051.usr.starcat.ne.jp, a high-speed Japanese-based home user. This means that either the spammer has control of this IP by way of a virus or Trojan, or the server is running an insecure proxy server. Further evidence of this can be found in the following Message ID string:
Message-ID: abbleniiun.6650580993seqvuspzwk@Panthonyjsnnbrvjv.com
The Message ID looks legitimate, but you can tell it is fake from the domain Panthonyjsnnbrvjv.com. This domain is part of a random variable that the mailing program added into the message to increase its validity. Panthony seems to be a common word because the e-mail is from someone called Panthony. Maybe this is another method of trying to make the message look legitimate, or maybe it is a random word used twice in the same e-mail.
Having no legitimate Message ID in the headers points to the sending it directly and not running its own mail server. If the host was running an insecure mail server there would be another Message ID in the headers, something legitimate that comes from the mail server like qmail or sendmail. Instead we only see the fake header:
Subject: FreeMort gageQuotes
This is tricky but not very readable. Using obfuscation and misspelling is a poor way to present a topic. The recipient would have difficulty understanding the subject; therefore, I do not consider it an attractive ploy.
Let’s recap everything we now know about the spammer:
-
The e-mail is sent using a spam program that attempts to use large amounts of randomly placed data to fool filters.
-
The spam originates from what looks like open proxy servers or previously compromised hosts.
-
The number of hosts needed to send this amount of spam requires the spammer to have control of or access to a Botnet.
-
The spammer is either Manual X or someone that is connected to this person.
-
We know that the spammer is working closely with Telefonica Empresas in Brazil, because they host the spammer’s Web sites. The spammer is also probably located in or near Brazil.
-
The spammer recently moved their DNS server to a Russian host, probably because of all the complaints people made to his old Brazilian DNS provider (nic.br).
-
The spammer is well set up, has many servers, and a fair amount of money; however, their spam method still needs work.
Example 2: Give Your Partner More Pleasure
In the following e-mail is another classic genre of spam: sexual performance enhancers:
<HTML> "My girlfriend loves the results, but she doesn't know what I do. Shethinks it's natural" -Thomas, CA<br> <br> "I've been using your product for 4 months now. I've increased my length from 2" to nearly 6" . Your product has saved my sex life." -Matt, FL<br> <br> <br> Pleasure your partner every time with a bigger, longer, stronger Unit<br> Realistic gains quickly<br> <br><a href="http://www.attractivebodysite.com/5/">to be a stud press here</a> <br> <br> <br> <br>Good-by! he cried <br><a href="http://www.attractivebodysite.com/5/">this does not interest me</a> <br>I ought to be a fairy, grumbled Jim, as he slowly drew the buggy home;for to be just an ordinary horse in a fairy country is to be of no account whatever When mortal eyes next behold me they will be those of one fit to command my services! As for you, your days will be passed in obscurity and your name be unknown to fame Good-by,--forever! The room filled with a flash of white light so like a sheet of lightning that the boy went reeling backwards, half stunned and blinded by its dazzling intensity </FONT></HTML>
And then the headers:
Return-Path: <elizstaniford@offisland.com> Delivered-To: spammerx@spammerx.com Received: (qmail 6327 invoked by uid 509); 27 Aug 2004 12:54:42 –0000 Received: from elizstaniford@offisland.com by Spambox by uid 89 with qmail-scanner-1.22 (clamdscan: 0.70. spamassassin: 2.63. Clear:RC:0(222.64.xxx.xxx):SA:0(?/?):. Processed in 6.871604 secs); 27 Aug 2004 12:54:42 –0000 X-Spam-Status: No, hits=? required=? Received: from unknown (HELO offisland.com) (222.64.xxx.xxx) by 0 with SMTP; 27 Aug 2004 12:54:35 –0000 Message-ID: <1EF04391.A13AA51@offisland.com> Date: Fri, 27 Aug 2004 11:41:28 –0300 Reply-To: "kirby shaw" elizstaniford@offisland.com From: "kirby shaw" <elizstaniford@offisland.com> User-Agent: Foxmail 4.2 [cn] X-Accept-Language: en-us MIME-Version: 1.0 To: "Cleopatra Ford" roughus@spammerx.com Cc: "Anika Lawrence" <jackson@spammerx.com>, "Sage Williams" spammerx@spammerx.com Subject: Give your partner more pleasure Content-Type: text/html; charset="us-ascii" Content-Transfer-Encoding: 7bit
This is my favorite type of spam because it preys on men’s insecurity (as mentioned in Chapter 5). The spammer does not have to be a brilliant salesperson, they just have to make the recipient doubt their own abilities.
A large portion of the daily spam I receive is for sex-related products. The first thing I notice about this e-mail is that it is addressed to three different (legitimate) usernames at my domain (spammerx.com). This means that the spammer harvested these three accounts and sorted the e-mail to group the accounts at my domain together. Sending the e-mail to three accounts at the same domain is highly efficient. The process sends one e-mail and has a higher chance of looking legitimate since it is addressed to three valid recipients. Reasonable thought went into this spam-sending process; it’s apparent this spammer knows what they’re doing.
If you look at the message content, you see that the spammer sent the message in Hypertext Markup Language (HTML) format, and has used HTML links within the message to link to the site where you can purchase the product (www.attractivebodysite.com). The User-Agent string in the header suggests that the message was sent from the Chinese version of FoxMail 4.2, a popular e-mail client in non-English speaking countries. This is highly unlikely because the message’s HTML formatting style is not in correct HTML syntax according to the W3C (the consortium that created the HTML standard). Any legitimate HTML’s body will be located between body tags, and any HTML page will contain a HEAD tag where you can set things such as the title. E-mail clients usually stick within these guidelines, especially when spam filters actively look for spam that is missing body tags. No one will write an e-mail client by default that will be blocked by spam filters. This is a mark of misinformation; this e-mail did not come from FoxMail and shows you that you should never trust the information in e-mail headers.
The message itself is very interesting; I can see that this spammer is a little smarter than the previous spammer in the first example reviewed. This spammer has utilized some interesting language techniques, again focusing on filters that are looking for known spam words such as Bayesian and rule-based filters.
Pleasure your partner every time with a bigger, longer, stronger Unit<br> Realistic gains quickly<br>
Pay careful attention to this sentence, because grammatically it makes much more sense.
Pleasure your partner every time with a bigger, longer, stronger Penis<br> Realistic gains quickly<br>
This spammer knows that Penis is a known spam word so he has replaced the word with other random words that are similar enough that the reader will still be able to understand the subject of the spam. If you look carefully at the text, you will see that there is also an extra space before “Unit” and that Unit is the only word in the line that is capitalized. The same can be seen in “Realistic gains quickly;” Realistic looks like another word that should not be there because it doesn’t flow in the sentence structure correctly.
The spammer has tried to bypass Bayesian and rule-based filters by not using known spam words, and using words that make sense to the reader. More evidence of this can be found in the link to the jump site; instead of saying “Click Here” the spam says “to be a stud press here.” To human readers this makes perfect sense and sounds better than “Click Here,” which is impersonal and cold. However, spam filters do not tend to read and fully understand text printed in e-mails, so they don’t know what the text is suggesting.
The random data used in the base of the message is not actually random. If you pay close attention to the body you can see some common elements scattered throughout the text. This section is from childhood favorite The Wizard of OZ, written by Frank L. Baum.
I ought to be a fairy, grumbled Jim, as he slowly drew the buggy home; for to be just an ordinary horse in a fairy country is to be of no account
This line is from The Master Key, again written by Frank L. Baum. In fact, the entire body of random data consists of various lines from these two stories. Because the text contains exact punctuation marks, it is easy to find Web sites that have these exact strings of text.
When mortal eyes next behold me they will be those of one fit to command my services!
These apparent random lines of text are all hosted on the same domain: http://fairy-tales.classic-literature.co.uk. It seems that this spammer downloaded each e-book from http://fairy-tales.classic-literature.co.uk and then inserted random lines from each story into the foot of each spam. This keeps the spam unique while also keeping the body grammatically correct. Any filters parsing these sections for non-English text or obviously fake language structure would not find any.
Using passages from existing text is an easy way to bypass Bayesian filters or any natural language parsers that attempt to find obviously random strings. The effort is minimal; the only thing the spammer must do is download the text files and tell the mailing program to insert a random line from each file into the spam. Spammers don’t need to worry about language frequency statistics or parsing engines looking for suspicious text. The author of the passages used has already made sure that it is legitimate looking.
www.attractivebodysite.com is linked as a Jump page in this spam and is registered to Ric X from Eugene, Oregon. I can tell this is a fake identity because a Google search for common words used on this Web site reveals many duplicate Web sites, all on different domains but with the exact same content.
-
www.naturalitemssale.com
-
www.incrediblecoolinformers.com
All of the DNS entries are registered in Eugene, Oregon and list P.O. Box 30123 as their address; however, each show a different name as the accountholder. This spammer is obviously well set up with multiple storefronts, because each domain they use is quickly blacklisted by spam filters, therefore forcing the spammer to move to a new domain every few months.
Although each accountholder name is random, the location is always P.O. Box 30123 in Eugene, Oregon, which seems suspect to me. If you change the name of the registration holder, why not also change the country or state? Although the DNS’ may be registered in the U.S., the IP address that each domain resolves to is hosted by ChinaNet (in China), so the site is definitely not located in Eugene.
The body of this spam also features an opt-out link that is hosted on the same domain as the site the spammer is advertising. This is an obvious attempt to find out what users read this spam. This spammer’s creativity also extends into how the opt-out link was phrased. Instead of simply saying, “To opt-out click here,” which is a commonly filtered phrase, the spammer chose the phrase, “Good-by! he cried. This does not interest me,” with a hyperlink to the opt-out page. The opt-out link is probably there to make the reader think they can actually opt-out, or it is there to make the spam compliant with the Controlling the Assault of Non-Solicited Pornography and Marketing Act of 2003 (CAN-SPAM) since all spam requires having an opt-out link.
The reality is that this opt-out link will only ensure that you receive more spam, since the spammer knows that your account is active and that you read spam messages. This Web site even sports a “report spam” link that makes you think that you have reported your spam to someone; the only catch is that you reported your spam to the spammer. This is a nice trick that probably stops people from complaining to U.S. legal authorities because they believe they have already complained to the product vendor. More importantly, this gives the recipient a method of venting their frustration. Again, this as a smart technique, which I’m sure has helped the spammer stay in business.
If we look at the headers in the message to determine how this spam was sent, we find some very interesting data:
Received: from unknown (HELO offisland.com) (222.64.xxx.xxx) by 0 with SMTP; 27 Aug 2004 12:54:35 –0000 Message-ID: <1EF04391.A13AA51@offisland.com>
The IP address lists 222.64.xxx.xxx as where the e-mail originated from, although the HELO came from a server called offisland.com, which is not the originating host. Instead, 222.64.xxx.xxx belongs to an Asia Pacific Network Information Centre (APNIC) IP block (APNIC holds the IP blocks for Asia and the Pacific region, China, Japan, Korea, Fiji, Australia, and New Zealand). Although this host has no reverse DNS, there is a trace route leading us to a Chinese router, as seen in the following:
16 202.101.xx.xxx (202.101.xx.xxx) 374.181 ms 402.964 ms 385.657 ms 17 218.1.x.xxx (218.1.x.xxx) 323.106 ms 296.954 ms 298.779 ms 18 218.1.x.xx (218.1.x.xx) 315.369 ms 308.289 ms 308.069 ms 19 218.1.x.xx (218.1.x.xx) 404.470 ms 406.781 ms 411.668 ms 20 218.1.xx.xx (218.1.xx.xx) 302.946 ms 301.558 ms 302.309 ms
The last hop, 218.1.xx.xx, is registered to ChinaNet in Shanghai, so it is safe to assume that this host is buying connectivity from ChinaNet or is located in ChinaNet’s network, as seen in the whois record for 218.1.xx.xx in the following:
inetnum: 218.1.0.0 - 218.1.xxx.xxx netname: CHINANET-SH descr: CHINANET Shanghai province network descr: Data Communication Division
This does fit the User-Agent header string, which suggests that the message was sent with Foxmail 4.2 [cn] (cn stands for Chinese).
I don’t believe that the spammer is Chinese, because the English used on the Web site and in the e-mail is western English and contains no traits of eastern language; it is too fluid and comprehensible. My guess is that the host that sent this spam (222.64.xxx.xxx) is part of a bulletproof spam-sending company located in China. Further evidence also suggests this because the Web site promoted in the spam is also housed in China and is located in ChinaNet’s network.
By port scanning the spam-sending host I see no evidence of open proxies (as seen in the following), and the host is not running any listening services. Any host that is sending e-mail and has no running services is highly suspicious.
[spammerx@spambox spam]# nmap -P0 222.64.xxx.xxx Starting nmap 3.51-TEST2 ( http://www.insecure.org/nmap/ ) at 2004-08-20 11:33 All 1660 scanned ports on 222.64.182.124 are: filtered
If you were an American spammer and you wanted people to think you were located elsewhere, where would you say you lived? Why, as far away from the U.S. as possible, of course. The same could be said for being Chinese. You would not use your Internet Service Provider (ISP) at ChinaNet to send spam; that’s far too obvious. You would use a host in Russia or the Czech Republic. This spammer is trying to use misdirection to make you think that he is located in China; but I believe he’s in the U.S.
Apart from the IP not belonging to offisland.com, the headers are otherwise correct. The Message ID looks legitimate and is located at the domain the HELO came from. The only questionable data is the time offset given. This is suspect because it is saying it is located in the same time zone as my e-mail server.
This is a good example of what spam headers should look like. They are smooth and have no obvious traits that can be used to track the spammer. This particular spammer is probably making a considerable amount of money and can buy a provider in China to host his Web site and can rent time with a commercial spam-sending company. I know this is not cheap.
Money buys high quality spam services, and usually a spammer is better off if they spend the cash up front. There is a significant return on investment (ROI) in spam, but you need money up front to cover the set-up costs. This is often why spammers choose free options such as open proxy servers and Botnets. My guess is that this spammer is spending $300.00 to $400.00 USD per week to send and host this spam, but it has paid off and the spam is smooth and successful in my eyes.
Example 3: Re: OXR, Where the Windows
What does “Re: OXR, where the windows” mean? Nothing. It is a collection of random words, probably unique to each spam, which is the basis of our next case study:
<HTML><HEAD> <BODY> <p>Fr</durward>ee Ca</bray>ble%RND_SYB TV</p> <a href="http://www.8002hosting.com/cable/"> <img border="0" src="/books/3/175/1/html/2/http://www.8002hosting.com/fiter.jpg"></a> dharma palindrome mount held biscuit chant combat nobleman assay crystallite collegial foldout jehovah heir wiggle carson agouti scrabble controvertible fatigue wagging jaw doom additive hafnium grumman boniface noblesse rankle lorelei diabetes boron <BR> tundra folksy momentary crankshaft truly antimony solicitous deprave wolfgang cantle postwar recipe bespectacled buried chomp evenhanded bissau black idiot argumentative abbe chordata laze baroque picnic compatriot sinewy bedbug dialect kindergarten rousseau persimmon viscount gil <BR> </BODY> </HTML>
With the headers:
Return-Path: <fiuhagxepbcw@china.com> Delivered-To: spammerx@spammerx.com Received: (qmail 20802 invoked by uid 505); 22 Mar 2004 16:13:17 -0000 Received: from fiuhagxepbcw@china.com by SpamBox by uid 89 with qmail- scanner-1.16 (clamscan: 0.67. spamassassin: 2.63. Clear:SA:0(3.6/5.0):. Processed in 0.256543 secs); 22 Mar 2004 16:13:17 -0000 X-Spam-Status: No, hits=3.6 required=5.0 Received: from unknown (HELO cpe0050da065861- cm.cpe.net.cable.rogers.com) (24.43.xx.xxx) by 0 with SMTP; 22 Mar 2004 16:15:58 -0000 Received: from [24.43.xx.xxx] by 5.24.23.xx with HTTP; Mon, 22 Mar 2004 12:18:21 -0400 From: "Milford Riggs" <fiuhagxepbcw@china.com> To: spammerx@spammerx.com Subject: Re: OXR, where the windows Mime-Version: 1.0 X-Mailer: mPOP Web-Mail 2.19 X-Originating-IP: [5.24.23.xx] Date: Mon, 22 Mar 2004 10:11:21 -0600 Reply-To: "Milford Riggs" <fiuhagxepbcw@china.com> Content-Type: multipart/alternative; boundary="7513955577200302" Message-Id: <KFCJIKY-0007059433049@cocky>
This spammer utilized many different techniques that you should now be familiar with. The faked “Re:” in the subject is crafty. I’m not a fan of faking e-mail replies because if I receive spam with “Re:” in it, I press delete instantly. Just like random numbers, fake replies in the subject are overused and doesn’t help the spam make it to its intended recipient.
The message body is HTML-encoded and begins with valid HTML and BODY tags that make it look legitimate. It’s easy to see that the spammer suspects that “Free Cable” is a known spam phrase, so they have attempted to hide the text within junk meta tags. They failed to recognize that spam filters check for an opening tag and a matching closing tag for each meta tag used. Although this spam contains <p>Fr</durward>ee Ca</bray>ble, there are no <durward> or <bray> tags.
A poor technique has been used, which will result in more spam filters catching this spam. Remember, the aim of evasion is to make spam look as legitimate as possible. Although this fools some of the older legacy spam filters, it greatly decreases the message’s chance of being delivered with modern spam filters in place. If the message has opening tags that match each closing tag the filters may not judge it legitimate, but the tags themselves will not cause the message to be filtered.
The word “%RND_SYB” also catches my attention. My guess is that this spammer used Dark Mailer to send this spam, where %RND_SYB would be replaced with a random symbol. The “%” acts as a variable declaration character in most spam clients. This spammer either modified or mistyped this variable, making each spam contain the text “%RND_SYB” but not the random symbol.
In addition, there is a single picture housed at 8002hosting.com that links to a Web page on the same domain. Ironically enough, just after I received this spam, 8002hosting.com was down so the entire point and purpose of this spam is now irrelevant; this message serves no legitimate use to anyone.
| Notes from the Underground ... | Useless Spam This is the kind of spam that really annoys people. It serves no functional purpose. I would agree with the spam activist’s on this one. If you are going to sell a product by sending spam to millions of people, at least make sure that the recipient can buy the product if they wish. What is the point otherwise? At the very least, try to make sure you can actually sell a product. Use a reliable spam-friendly host and keep the site up and fast for at least a week after the spam run is finished. Free hosting providers and cheap solutions are not worth it; they will not last more than an hour. |
The rest of the e-mail is the usual bombardment of random text that, like the rest of the e-mail, is not highly intelligible. Not a single word repeats in eight lines of text, and every word is considerably long. There are no punctuation marks in the entire message.
Unlike the last spam message, which used random lines from two children’s stories, this spammer attempted to conjure up his own random text, and failed miserably. Language frequency statistics alone could detect this obvious random text. Although the words are English-based, Bayesian filters would catch this e-mail because the average person would not use such words as crystallite hafnium and chordate. The message stands out clearly as being different; spam filters aren’t very good against anything different than what they expect.
When reading the headers of this spam you can see that this spammer kept the same theme throughout. This spammer could benefit from doing a little more research. To start with, the spammer has injected fake headers as a method of obfuscating the true sender of the message:
Received: from [24.43.xx.xxx] by 5.24.23.95 with HTTP; Mon, 22 Mar 2004 12:18:21 -0400 From: "Milford Riggs" <fiuhagxepbcw@china.com> To: spammerx@spammerx.com Subject: Re: OXR, where the windows Mime-Version: 1.0 X-Mailer: mPOP Web-Mail 2.19 X-Originating-IP: [5.24.23.xx]
All of these headers are injected from the mailing program and are obviously fake. How do I know? To start with, the headers say that 24.43.xx.xxx relayed the e-mail through 5.24.23.xx, using HTTP to make it look like the message came from a Webmail account. The X-Originating-IP string is also fake. This spammer is obviously trying to over-disclose 5.24.23.xx in hopes of fooling readers by flooding them with one constant IP address. More headers have been injected, including an X-Mailer: mPOP Web-Mail 2.19 header, which attempts to flow with the idea that this message came from a Webmail-based server.
This is a poor attempt that won’t confuse anyone. The dead give away is 5.24.23.xx. Apart from looking suspect because the first octet is “5,” this IP address is an Internet Assigned Numbers Authority (IANA) reserved address. As seen in the whois result, this address is not used actively on the Internet. The IP is not real; it’s the equivalent of 999.999.999.999. You will not see it anywhere but in sloppy spam like this:
NetRange: 5.0.0.0 - 5.255.xxx.xxx CIDR: 5.0.0.0/8 NetName: RESERVED-5 NetHandle: NET-5-0-0-0-1 NetType: IANA Reserved RegDate: 1995-07-07 Updated: 2002-09-12
The real host is just above where the injected headers begin. The following shows the real sender of this message, a U.S.-based cable modem at rogers.com:
Received: from unknown (HELO cpe0050da065861- cm.cpe.net.cable.rogers.com) (24.43.xx.xxx)
The whois record matches the host that the HELO identified itself as, and the DNS information is evidence that this IP address does belong to rogers.com. This is the source address of the spam, not 5.24.23.xx. However, this cable modem is not the source address of the spammer; this host is probably just running an open proxy server or is infected with a virus or Trojan, causing them to unwillingly be the sender. Only lax spammers send spam directly from their own ISP. As it turns out, 24.43.xx.xxx is well known for sending spam, and is listed on various real-time black hole lists (RBLs). The results from a query at popular RBL site dsbl.org are shown in Figure 11.2.
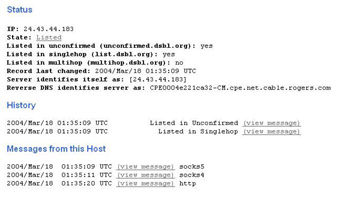
Figure 11.2: Past Statistics of 24.42.xx.xxx
As suspected, 24.42.xx.xxx is acting as an open socks5/4 and HTTP proxy. The host is probably running an insecurely set up Internet sharing application, which is being exploited by the spammer. Using a host listed in an RBL is not the best decision, because the majority of spam filters would catch any messages sent from this host very quickly. Other RBLs also list the host and its past spam activity. What this spammer should be doing is testing each proxy server against an RBL before using it. Most e-mail clients support testing the host for connectivity and testing it against an array of RBLs to see if it is listed, as seen in Figure 11.3.
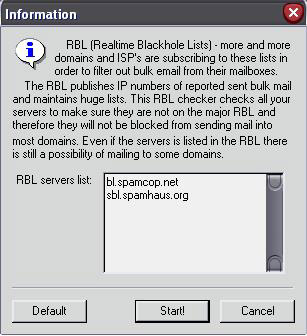
Figure 11.3: RBL Checking in Dark Mailer
At the time of receiving this message, the host promoted in the body of this spam, www.8002hosting.com, was down; however the DNS registration is still active, it’s simply not pointing to any IP address. The registration details are shown in the following:
Registrant Name ................. longcao Registrant Organization ......... long cao Registrant Address .............. beijing Registrant Email ................ frant334@hotmail.com
A Google search for frant334@hotmail.com shows that this spammer angered many people. Many attempts have been made to have the hosting account removed or for hotmail to close their e-mail account. One interesting fact to note is that although the spam promoted 8002hosting.com, this hostname looks very much like a sequential number followed by hosting.com. Does 8001hosting.com or 8003hosting.com exist? Funny enough, 8001hosting.com, 8002hosting.com, and 8003hosting.com are all registered under the name Long Cao from Beijing. None of these addresses actively resolve to any IP address; the DNS provider probably removed it after receiving complaints.
My previous Google search showed that this spammer was trying to sell other products, including “Banned CDs” of “secret tools,” which are probably just a collection of port scanners and vulnerability scanners freely available on the internet.
Products such as “Banned CDs” are scam products. The majority of data on these CD’s contain Trojans or virus code. Once infected, the recipient becomes part of a Botnet or e-mail relay network for the spammer. Not only does the spammer add to their Botnet, but they also make a few dollars.
In summary, this spam is poor. The content is unoriginal and functionally broken. This spammer used poor methods of filter evasion including obviously placed random text and sloppy header injection. When I received the e-mail, the Web site within the spam was down, due to the DNS server removing the host’s entry, thus making the spam pointless.
|
| < Day Day Up > |
|
EAN: 2147483647
Pages: 79