Token Ring Technical Overview
| < Free Open Study > |
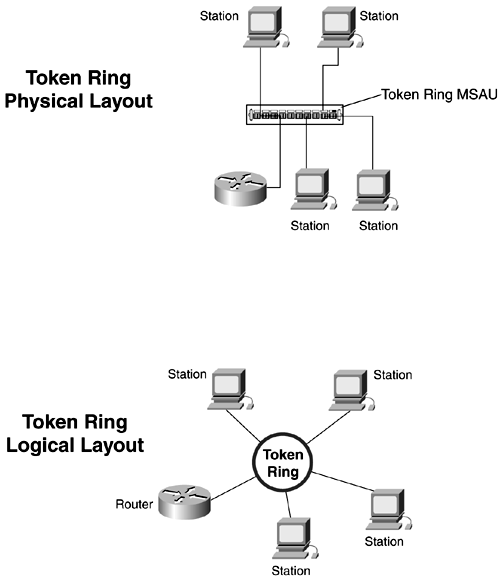
| The IEEE officially adopted Token Ring as IEEE 802.5. The specifications are almost identical, with a few minor differences. IBM Token Ring calls for the stations to be attached by twisted-pair cable to a multistation access unit (MSAU) in a physical star topology. The IBM 8228 is a common example of a MSAU. The IEEE committee chose not to specify a medium or topology, allowing Token Ring networks to be more flexible. Token Ring/IEEE 802.5 operates strictly at Layer 2, like most LAN protocols. Like Ethernet, the IEEE committee divides the data link layer into two sublayers : 802.5 as the MAC layer and 802.2 as the LLC layer. Functionally, IEEE 802.5 Token Ring parallels IEEE 802.3. The LLC layer ”802.2, in this case ”is a standardized interface between a hardware-specific MAC and a Layer 3 protocol. Token Ring OperationToken Ring networks have a physical topology of a star, but the network is treated as a logical ring. Figure 2-17 shows the logical and physical Token Ring topologies. Figure 2-17. Token Ring Topologies Token Ring networks utilize a token-passing technology on the ring. Token-passing networks move a small frame, called a token, around the ring. Token Ring uses two types of frames, a token and an information/data frame. Token frames contain a start delimiter, an access control field, and an end delimiter . The data/command frames contain the same fields, plus a few more for user data, and also contain a source and destination address. When a station wants to transmit information, it must posses the token. Possession of token grants the right of the station to transmit data. If the station has no data to transmit, it simply passes the token along to the next station on the ring. When a station posses the token and wants to transmit, it changes a single bit in the access control field, the T bit. The station then appends its information to the frame and sends it on to the next station on the ring. The frame circulates the ring until it reaches the destination station, where the frame is then copied by the station and tagged as having been copied . The frame continues around the ring until it reaches the station that originated the frame. At this point, it is removed from the ring by that station. The concept of early token release allows a station that seizes a token to transmit a new token onto the ring after first sending its information frame. The following list describes some other important features that Token Ring employs to help data circulate throughout the ring:
Table 2-15. A and C Bit Modification by Receiving Station
NOTE Canonical Versus Noncanonical Address Format Ethernet networks transmit data in what is called a canonical address format. This means is that if you have the bit stream 0110 1010, the most significant bit (MSB) is on the left and the least significant bit (LSB) is on the right. Ethernet networks transmit data in a canonical form, with the least significant bits get transmitted first. If an Ethernet network is sending the previous data steam , it would send 0 1 0 1 0 1 1 0. Token Ring and FDDI networks transmit data in a noncanonical format. Noncanonical format transmits the most significant bit first. If a Token Ring network were transmitting the original bit stream mentioned, it would transmit 0 1 1 0 1 0 1 0. Source-route translation bridges and DLSw will perform address translation when needed. |
| < Free Open Study > |
EAN: 2147483647
Pages: 283