Lab 31: Configuring Dynamic NAT and Using Non-Standard FTP Port Numbers-Part II
| < Free Open Study > |
NAT Technical OverviewRFC 1631, "The Network Address Translator (NAT)," outlines NAT, which is most often installed on a router in a stub domain ”that is, a network with a single exit point. Specifically, NAT handles two types of translations:
To explain how these translations work, it is important to understand NAT terminology. NAT TerminologySome terms mentioned earlier apply to all NAT configurations. The term inside refers to networks that are private and that reside inside your routing domain. The inside is the address that you will be translating. The term outside refers to networks that are "visible" and most often routable to the outside world. The term global is used with inside and outside as well; think of the term to mean that this address space is assigned by NIC. Table 15-1 details how the words are used together. Table 15-1. NAT Terminology
NAT processes a packet that originates from an inside network in the following manner:
NAT processes a packet that originates from an outside network in the following manner:
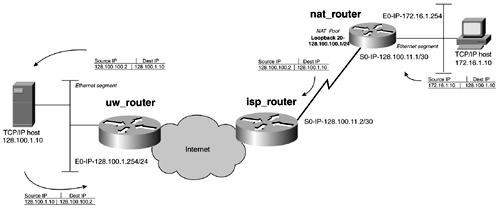
Figure 15-1 shows a workstation on a private network of 172.16.1.0/24 that it is running a TCP application that needs to reach a public university network of 128.100.1.0/24. Figure 15-1. NAT Translation Example The public network of 128.100.1.0/24 or the UW has no visibility to the private network 172.16.1.0. However, 172.16.1.0 does have a route to the 128.100.1.0/24 subnet. As a packet originates from the host 172.16.1.10 to 128.100.1.10, it will have a source IP address of 172.16.1.10 and a destination IP address of 128.100.1.10. As the packet enters the NAT inside interface (E0) of the NAT router, it is routed through an NAT outside interface, S0. When this happens, the router follows a list of user -defined criteria to determine whether address translation should take place. This is usually accomplished by checking an access list. If translation is to happen, the router translates according to how NAT is configured. This example uses a NAT pool of 254 addresses in the 128.100.100.0/24 range. These are the inside global addresses. NAT now makes an association table between 172.16.1.10 and 128.100.100.2. It replaces the source IP address 172.16.1.10 of the packet with 128.100.100.2 and forwards the packet out its S0 port. This example uses a loopback interface for a NAT pool; the IP address is 128.100.100.1. NAT uses the next available address on this subnet for its association ”in this example, it uses 128.100.100.2. When the UW router receives the packet, it will have appeared to come from the subnet 128.100.100.0/24. This network is reachable by this router, and it can service the request. On the NAT router, you must have at least one globally reachable IP address; in this example, this is referred to as an inside global address. This address or pool of addresses is where NAT replaces the original source IP address with a new source IP address specified by NAT. When this packet reaches its destination, the host on the other side thinks that the packet comes from the global inside address, or the pool. Example 15-1 shows the results of a ping from 172.16.1.10 to 128.100.1.10. You can see the translations taking place by using the debug ip nat command along with the show ip nat translations command. Example 15-1 NAT Translation Examplenat_router# deubg ip nat 00:17:30: NAT*: s=172.16.1.10->128.100.100.2, d=128.100.1.10 [4097] 00:17:30: NAT*: s=128.100.1.10, d=128.100.100.2->172.16.1.10 [4097] 00:17:31: NAT*: s=172.16.1.10->128.100.100.2, d=128.100.1.10 [4353] 00:17:31: NAT*: s=128.100.1.10, d=128.100.100.2->172.16.1.10 [4353] 00:17:32: NAT*: s=172.16.1.10->128.100.100.2, d=128.100.1.10 [4609] 00:17:32: NAT*: s=128.100.1.10, d=128.100.100.2->172.16.1.10 [4609] 00:17:33: NAT*: s=172.16.1.10->128.100.100.2, d=128.100.1.10 [4865] 00:17:33: NAT*: s=128.100.1.10, d=128.100.100.2->172.16.1.10 [4865] nat_router# nat_router# show ip nat translations Pro Inside global Inside local Outside local Outside global --- 128.100.100.2 172.16.1.10 --- --- For reference, this type of NAT is called dynamic translation, and it is discussed in greater detail in a later section. Example 15-2 lists the configuration of the nat_router from Figure 15-1. Example 15-2 NAT Dynamic Pool Configuration for the nat_routerhostname nat_router ! ip subnet-zero ! interface Loopback20 ip address 128.100.100.1 255.255.255.0 no ip directed-broadcast ! interface Ethernet0 ip address 172.16.1.254 255.255.255.0 no ip directed-broadcast ip nat inside ! interface Serial0 ip address 128.100.11.1 255.255.255.252 no ip directed-broadcast ip nat outside ! <<<text omitted>>> ! router eigrp 2001 network 128.100.0.0 ! ip nat pool publicpool 128.100.100.2 128.100.100.254 netmask 255.255.255.0 x |
| < Free Open Study > |
EAN: 2147483647
Pages: 283