Security Concepts
After you've developed a rough organization model with information about the different types of users in your system, you must translate that information into Microsoft CRM security settings. Before we explain how to configure the security settings in the software, let's explain two of the key topics related to Microsoft CRM security:
-
Security model concepts
-
Integrated Windows authentication
Once you understand these concepts, we'll get into the details of configuring the software to meet your specific needs. Because of the many security customization options offered in Microsoft CRM, very rarely do we see an organization structure that Microsoft CRM's security settings can't accommodate.
Security Model Concepts
The Microsoft CRM security model uses two main concepts:
-
Role and object-based security
-
Organization structure
Role-Based and Object-Based Security
Microsoft CRM uses security roles and role-based security as its core security management techniques. A security role describes a set of access levels and privileges for each of the entities (such as Leads, Accounts, or Cases) in Microsoft CRM. All Microsoft CRM users must have one or more security roles assigned to them. Therefore, when a user logs on to the system, Microsoft CRM looks at the user's assigned security roles and uses that information to determine what the software will allow that user to do and see throughout the system. This is known as role-based security.
The security model also allows you to define different security parameters for the various records (such as Lead, Account, Contact, and so on) because each record has an owner. By comparing the business unit of the record owner with the security role and business unit of a user, Microsoft CRM determines that user's security privileges for a single record. You can think of configuring access rights on the individual record level (not the entity level) as object-based security. Figure 3-2 illustrates this concept.
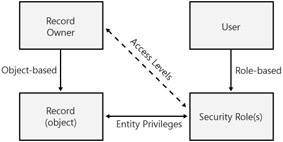
Figure 3-2: Role-based security and object-based security combine to determine user privileges
In summary, Microsoft CRM uses a combination of role-based and object-based security to manage access rights and privileges throughout the system.
Organization Structure
In addition to security roles, Microsoft CRM uses an organization's structure as a key concept in its security model. Microsoft CRM uses the following definitions to describe an organization's structure:
-
Deployment A single installation of Microsoft CRM.
-
Organization The company that owns the deployment. The organization is the top level of the Microsoft CRM business management hierarchy. Microsoft CRM automatically creates the organization based on the name that you enter during the software installation. You cannot change or delete this information. You can also refer to the organization as the root business unit.
-
Business unit A logical grouping of your business operations. Each business unit can act as parent for one or more child business units. In the sample organization in Figure 3-1, you would describe the Customer Care business unit as the parent business unit of the Customer Support and OEM Support business units. Likewise, you would refer to the Customer Support and OEM Support business units as child business units.
-
User Someone who typically works for the organization and has access to Microsoft CRM. Each user belongs to one (and only one) business unit, and each user is assigned one or more security roles.
Later in this chapter, we'll explain how these terms relate to setting up and configuring security roles.
Integrated Windows Authentication
Microsoft CRM uses Integrated Windows authentication (formerly called NTLM, and also referred to as Microsoft Windows NT Challenge/Response authentication) for user security authentication in the Web browser and Microsoft Office Outlook interfaces. By using Integrated Windows authentication, users can simply browse to the Microsoft CRM Web site and Internet Explorer automatically passes their encrypted user credentials to Microsoft CRM and logs them on. This means that users log on to Microsoft CRM (authenticate) by using their existing Microsoft Active Directory directory domain accounts, without having to explicitly sign in to the Microsoft CRM application. This integrated security provides great convenience for users, because there's no need for them to remember an additional password just for the CRM system. Using Integrated Windows authentication also helps system administrators, because they can continue to manage user accounts from Active Directory services. For example, disabling a user in Active Directory prevents him or her from logging on to Microsoft CRM, because the user's logon and password will not work anymore.
| More Info | Disabling or deleting users in Active Directory prevents them from logging on to Microsoft CRM, but it does not automatically disable their user records in Microsoft CRM. Because all active users count against your licenses, make sure that you remember to disable their user records in Microsoft CRM to free up their licenses. Also, if you change a user's name in Active Directory, you must manually update it in Microsoft CRM. |
Most companies install Microsoft CRM on their local intranet in the same Active Directory domain to which users log on. By default, the User Authentication security settings in Microsoft Internet Explorer 6.0 automatically log users on to any intranet site to which they browse, including Microsoft CRM. This default setting will work fine for almost all of your users.
However, you might find that you want to alter the default security settings to change how the Internet Explorer browser handles user authentication. Typical reasons to modify the Internet Explorer security settings include:
-
You want to log on to Microsoft CRM impersonating one of your users during setup and development.
-
Your Microsoft CRM deployment resides in a different Active Directory domain (or on the Internet) and you want to change the log on settings.
-
You want to explicitly trust the Microsoft CRM Web site to allow for pop-up windows.
To view your Internet Explorer 6 security settings, click Internet Options on the Tools menu in Internet Explorer. The Security tab in the Internet Options dialog box displays Web content zones, including Internet, Local Intranet, Trusted Sites, and Restricted Sites, as shown in Figure 3-3.
Figure 3-3: Web content zones in Internet Explorer
By altering the security settings, you can change how Internet Explorer passes your logon information to various Web sites, such as your Microsoft CRM Web site.
Turning Off Automatic Logon in the Local Intranet Zone
-
On the Security tab, click Local intranet, and then click Custom Level.
-
In the Security Settings dialog box, scroll down until you see the User Authentication section, and then select Prompt for user name and password.
When you disable automatic logon, Internet Explorer does not automatically pass your user credentials to Microsoft CRM (or any other Web site on your local intranet). Instead, it prompts you to enter your user name and password when you browse to the Microsoft CRM server. This prompt gives you the opportunity to enter any user credentials that you want, including user credentials from a different domain. As an administrator, you might want to log on as a different user during your setup and configuration phase to confirm that your security settings are correct.
| Warning | The Microsoft CRM client for Outlook requires automatic logon, so you should not set this value to Prompt for user name and password if you need to use the Microsoft CRM client for Outlook. |
In addition to disabling automatic logon, you might want to add Microsoft CRM as a trusted site in Internet Explorer or list it as part of your Intranet zone. The steps and benefits of either are almost identical, but we'll review adding Microsoft CRM as a trusted site.
Adding a Trusted Site to Internet Explorer
-
On the Security tab, click Trusted sites, and then click Sites.
-
In the Trusted sites dialog box, enter the address of your Microsoft CRM server (include the http:// portion of the address), and then click Add. You might need to clear the Require server verification check box if your Microsoft CRM deployment does not use https://.
-
Click OK.
Adding a trusted site to Internet Explorer will accomplish two things in regard to Microsoft CRM:
-
Internet Explorer will automatically pass your user credentials to the Web site and attempt to log you on. You might want to set this up for your Microsoft CRM users who are not located on your local intranet (such as offsite or remote users) so that they do not have to enter a user name and password each time they browse to Microsoft CRM.
-
The Internet Explorer Pop-up Blocker allows pop-up windows for any Web site listed in your Trusted Sites zone.
| Caution | Intranet sites and trusted sites in Internet Explorer 6 become quite powerful, so you must use caution when deciding which sites you will trust. For example, the default security settings for trusted sites in Internet Explorer 6 automatically install signed Microsoft ActiveX controls on your machine. |
Many users install a pop-up blocker add-in for Internet Explorer in an attempt to limit the number of pop-up advertisements they see when browsing the Internet. Unfortunately, some of these pop-up blockers might also block some of the Web browser windows that Microsoft CRM uses. Consequently, you'll probably need to let your users know how to configure their pop-up blockers to allow pop-up windows from the Microsoft CRM application.
The most common problem caused by pop-up blockers manifests itself when users initially log on to Microsoft CRM. If your users say something like, "the window just disappeared," you can pretty safely assume that pop-up blocker software caused the problem. When users log on to Microsoft CRM, a new browser window pops up, and the original browser window closes. However, if the user's pop-up blocker stops the new window from appearing, it appears to the user that the original window simply disappeared, because Microsoft CRM closed their original browser window.
Internet Explorer 6.0 on Microsoft Windows XP SP2 includes a pop-up blocker, but the default setting allows sites in the Intranet and Trusted Sites zones to launch pop-up windows. If Internet Explorer doesn't recognize Microsoft CRM as an intranet site, or if you don't want to add it as a trusted site, you can configure the pop-up blocker to allow popup windows form the Microsoft CRM Web site (on the Tools menu, point to Pop-Up Blocker, and then click Pop-up Blocker Settings to enter the Microsoft CRM address).
Some pop-up blockers do not allow you to manually enter a trusted address like the Internet Explorer pop-up blocker. Therefore, you have to browse to the Web site you want to allow and then click some sort of "Allow Pop-ups" button. However, because the Microsoft CRM window disappears on initial log on, you might wonder how you could ever open the Web site to allow pop-ups. A simple trick is to browse to http://<crmserver>/loader.aspx, and then Microsoft CRM will launch in the same Internet Explorer window instead of popping up a new one. From this page, you can click the Allow Pop-ups button to always allow pop-ups for your Microsoft CRM Web site. Here's another trick related to pop-up windows: you can reference the same Microsoft CRM Web site by using several different URLs. For example, you could access Microsoft CRM by using any of the following:
-
NetBIOS name (Example - http://crm)
-
IP address (Example - http://127.0.0.1)
-
Fully qualified domain name (Example - http://crm.domain.local)
-
A new entry in your Hosts file (add by editing C:\WINDOWS\system32\drivers\etc\hosts)
Although all of these URLs take you to the same Microsoft CRM server, Internet Explorer 6 treats each of these as different Web sites. Therefore, you could configure different security settings in Internet Explorer for each of these URLs. For example, you might browse to the NetBIOS name by using Integrated Windows authentication to log on as yourself, but configure Internet Explorer to prompt for a log on when you browse to the IP address to impersonate a user.
EAN: 2147483647
Pages: 120