Potential Security Risks with a VPN
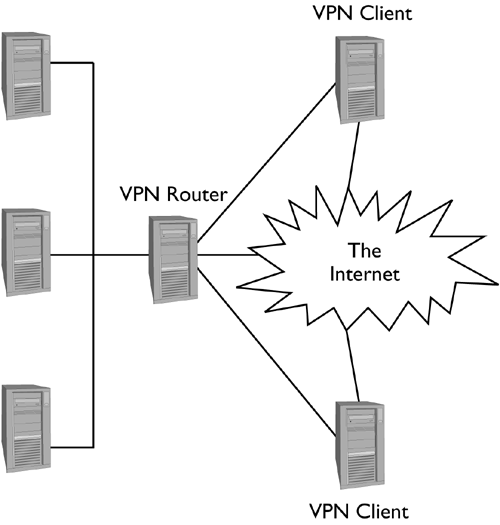
| VPNs are intended, in part, as a tool for increasing a network's security. They can easily become a doorway through which intruders can enter, though. VPNs are frequently explained through diagrams like Figures 26.1, 26.2 and 26.6. These show the way the various VPN components are tied together. Such figures don't emphasize strongly enough that many of the links are actually two links. For instance, consider a PPTP VPN in which a central network uses a VPN router to communicate in a secure way with Windows computers. Those Windows computers actually have two network interfaces ”one for the VPN and one for their normal Internet connections. Depending upon the firewall rules on the VPN router itself, the logical configuration of such a network might more closely resemble that shown in Figure 26.7. Figure 26.7. Although a VPN provides secure links between systems or networks, both sides of the VPN link normally have direct Internet connections, and those can be abused. Normally, the VPN is configured to trust its VPN clients more than it trusts hosts on the Internet at large. The VPN clients, though, have their own independent links to the Internet (in fact, those links are usually the means by which the VPN connection is established). Thus, unless security on the VPN clients is quite strong, they can become a means of attack. If the VPN or any other intervening firewalls or security tools treat VPN clients as truly local, the security provided by those firewalls and other security measures isn't nearly as good as it might at first appear. For instance, consider the case of an Internet worm or virus that attacks random computers. You might build protections from such attacks into your regular firewall. If a VPN client is compromised, though, and if the firewall protection doesn't apply to VPN clients, the worm or virus will quickly find its way into your allegedly protected network. There are two approaches to restoring security in the face of potential VPN bypasses:
In many cases, a combination of these two approaches is appropriate. You might insist that employees who use PPTP client software install firewall packages as well, and give them access only to particular local computers or protocols. You can use the Linux iptables command (described in Chapter 25) to configure these restrictions. When both ends of the VPN are under your complete control, you can rely more upon the first approach, because you can configure identical security measures on both Internet access points. |
EAN: 2147483647
Pages: 203