Firewall Management and Rule Building
|
| Of course when it comes to managing multiple or extremely complex firewall environments, some of the goals are automating away the drudgery and hopefully eliminating "fat-finger" mistakes in firewall rules. While not as flexible as creating your own rules by hand, these tools go a long way in abstracting away the vast majority of the situations you will run into when building and integrating several firewalls together. ISCS, available from http://iscs.sourceforge.net/, is probably one of the more exciting open source projects we've run into in a while. ISCS (Integrated Secure Communications System) is a management infrastructure for firewalls, VPN's, PKI, and eventually IDS systems such as snort. When you're creating a large network of multiple VPN's, distributed DHCP servers, hundreds of firewalls, and a Public Key Infrastructure (PKI), this is the kind of tool you're not going to be able to live without. If you're only running a single firewall, ISCS is not really going to be all that useful to you. However, if you're in a multiple firewall environment where you need to compartmentalize departments from one another (an environment where cheap Linux firewalls excel!) or perhaps a business with offices distributed all over a region or even the world, ISCS provides a great interface to create and manage a distributed infrastructure. The following screenshot is just one example of a business with multiple departments and the access policies between each group, in this case, a default ALLOW policy. You can see how quickly you could use this system to compartmentalize different departments or regions from one anotheror perhaps even just specific services, such as filtering common worm ports between departments, a dirt cheap and highly effective method of defending large networks against worm infections. Figure 8.5. Graphic depicting the iscs interfaces' visualization of a default allow policy.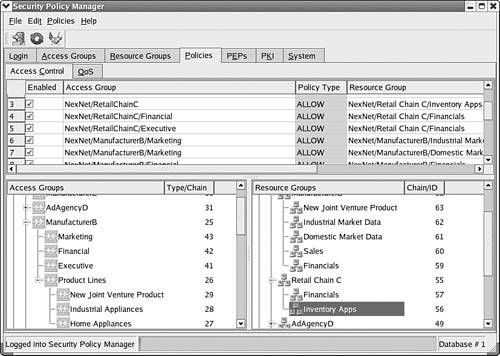 ISCS provides a very reliable mechanism for rolling out an initial deployment of internal firewalls into a business for the first time, and frankly this is probably one of the most important uses for low cost, highly configurable devices such as a Linux firewall. If you're in an environment where you're considering (or presenting!) the use of Linux firewalls, this is one potential way of demonstrating a low-impact rollout of firewall devicesfor example, deploying multiple internal Linux firewalls as primarily a worm-defense system. Over time, more stringent firewall rules could be applied to restrict access between networks (or Quality of Service...ISCS does that too!). This is a far lower impact strategy than implementing a strict firewall policy from the get-go, which while more secure, is typically politically sensitive or even more likely, prone to cause issues with your users due to some unknown network behavior. This is just one example of where we used ISCS to save both time and moneyand it worked. Of course, you'll also run into environments where you have a mix of firewalls and don't need the management infrastructure of something as powerful as ISCS. That's where Firewall Builder (fwbuilder) comes in. fwbuilder (http://www.fwbuilder.org/) is a firewall rule generation interface that supports both open source (Linux, BSD) and commercial firewalls (Cisco PIX). It's a graphical front end that allows you to quickly create complex firewall rule policies. Until we discovered ISCS, we used fwbuilder for large corporate rollouts, and we still do for what we call the "Diet-Coke" firewall implementations, "Just one firewall! Not enough for ISCS!" Obviously, this tool is another X11-based interface for rule generation. It's absolutely fantastic when you're faced with the problem of creating and maintaining rules on a Linux firewall in conjunction with another firewall (like a PIX, they're everywhere). ISCS, like fwbuilder, can control the rules on multiple types of firewalls, not just Linux-based firewalls. This tool also includes a Druid, an open source speak for what Windows users would call a "wizard" for rapidly creating a basic firewall ruleset. In addition, there is a drag-and-drop interface for more common rules such as IPSEC or Voice-over IP, for example. The open source community is not the only source of useful technologies to help you with the process of managing and troubleshooting your firewalls. However, we chose to cover only those technologies we felt would always be within the reach of all our readers, so the focus will be on open source tools. Additionally, we have not been found wanting for lack of commercial tools. We have not encountered any problem we could not diagnose and resolve through the sole use of open source tools. Figure 8.6. From the fwbuilder website documentation.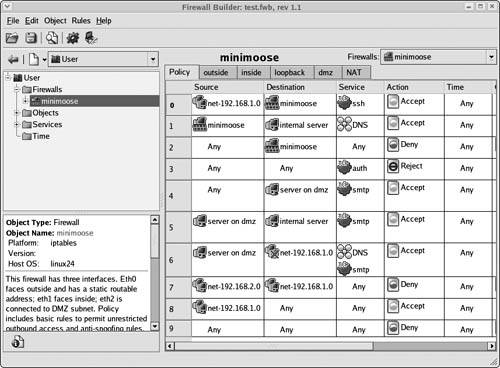 With that said, we don't want to diminish the efforts of the many fine companies out there that make useful tools that may assist you as well in your troubleshooting efforts. There are many excellent commercial software packages and tools that also can help in this regard, and we leave it as an exercise for the reader to explore these alternatives. You can find all the tools we use in this book, plus some other useful tools for other system-related tasks, on our website (www.gotroot.com) and also on our FTP server, ftp.gotroot.com. |
|