Forwarding SMTP to an Internal Mail Server
|
| In this configuration, our firewall, Host-A, receives and forwards SMTP connections on its external interface to an internal server using DNAT. Ideally in this configuration, you want your SMTP server (192.168.1.25) to exist on its own DMZ segment (192.168.1.0/24). Forwarding these connections directly to an internally hosted SMTP server, however common, is not recommended. It absolutely opens your internal systems to secondary exploitation through the SMTP server if/when it is compromised. The following illustration serves to show the recommended design. Figure 14.1. Demonstrates the logical layout of a mail server located on a DMZ segment.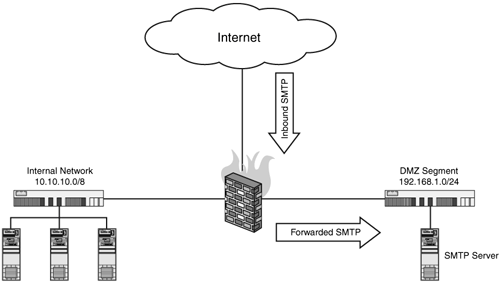 This is accomplished through the following firewall rules: # where eth0 is the external interface on the firewall # where eth1 is the internal interface on the firewall (10.10.10.0/24) # where eth2 is the DMZ interface on the firewall (192.168.1.0/24) EXTERNAL=eth0 INTERNAL=eth1 DMZ=eth2 MAILSERVER=192.168.1.25 $IPTABLES -A FORWARD -i $EXTERNAL -o $DMZ -p tcp \ --dport 25 -m state \ --state NEW,ESTABLISHED,RELATED -j ACCEPT $IPTABLES -t nat -A PREROUTING -i $EXTERNAL -p tcp \ --dport 25 -j DNAT --to-destination $MAILSERVER Figure 14.2. Outbound SMTP filter rules.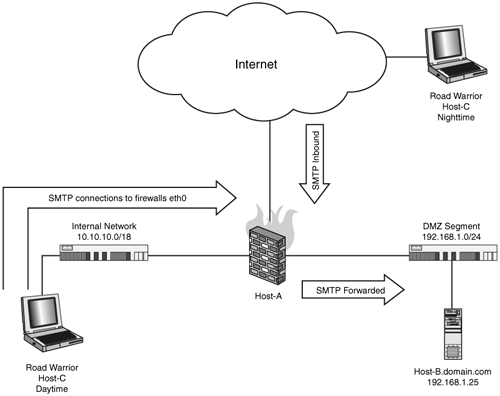 |
|