Planning for Remote Administration by Using Terminal Services
|
EXAM 70-293 OBJECTIVE 3, 5.4.2
Most of what is new in Windows 2003 Terminal Services relates to remote administration. Microsoft has really listened to customer feedback from previous versions of the operating system, and has created some major improvements in this area. The test objectives focus on two major Terminal Services components, Remote Desktop for Administration and Remote Assistance. Although a predecessor to Remote Desktop for Administration (Terminal Services in Remote Administration mode) existed in Windows 2000, it has received many changes in the current release. RA is a new component for Microsoft’s server operating systems. It was initially released with Windows XP.
Using Remote Desktop for Administration
As we’ve mentioned, no installation is necessary for the Remote Desktop for Administration component of Terminal Services. It is installed with the operating system by default. However, for security purposes it is not enabled by default. After it is enabled, members of the administrators group can connect and use it by default. Non-administrators must be specifically granted access. Let’s take a look at how to enable and configure this critical component.
Configuring RDA
To configure Remote Desktop for Administration, select Start | Control Panel | System and click the Remote tab. To enable the feature, simply check the box next to Allow users to connect remotely to this computer located in the Remote Desktop section of the tab, as shown in Figure 7.30.
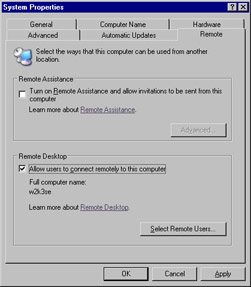
Figure 7.30: The System Properties Window
Setting Up Authentication
When RDA is enabled, any user accounts that are members of the Administrators built-in group on the server will be allowed to establish a remote session. However, other accounts must be explicitly approved for access. There are two different ways this can be accomplished. The first is to simply add any accounts that require access to the Remote Desktop Users group on the server. To grant a user access using this method, perform the following steps:
-
Open Computer Management and expand the Systems Tools, Local Users and Groups, and Groups nodes in the console tree on the left side of the utility.
-
Right-click the Remote Desktop Users group.
-
Select Add to Group from the context menu, and then click the Add button.
-
Type (or search for and select) the account name of the user to whom you wish to grant access.
-
Click the OK button.
The second, simpler way to access the Remote Desktop Users group and grant access is to use an option provided in the Remote tab in the System properties located in Control Panel. To use this method, perform the following steps:
-
In the Remote Desktop section of the Remote tab, click the Select Remote Users… button.
-
In the Remote Desktop Users dialog box that appears, click the Add button.
-
Type (or search for and select) the account name of the user requiring access. (See Chapter 4, Managing User, Group, and Computer Accounts, if you need additional information on group management and how to add users to groups in Windows 2003).
-
Click the OK button.
Advantages of RDA Over Other Remote Administration Methods
Windows Server 2003 includes many ways to remotely administer your servers. You can install server administration tools (including Active Directory Users and Computers, Active Directory Sites and Services, Active Directory Domains and Trusts, and many others) on a client computer. You can use the Computer Management console on one computer on the network to connect to and manage another. You can use command line tools to connect to and manage computers across the network. What are the advantages of using Remote Desktop for Administration?
Many administrators prefer RDA because you are able to see and use the entire server desktop, exactly as if you were sitting there at the console. You can do things such as promote or demote a domain controller or defrag the server’s disk, install applications, run a backup job, or even upgrade the operating system. You can change configurations, such as Control Panel settings, that are difficult or impossible to configure by other remote methods. You can control the server from a computer on which you would not want to install the administrative tools. With the Remote Desktop Web Connection, you don’t even have to have RDC or the Terminal Services client installed on the computer from which you initiate a terminal session; only MSIE v5.0 or later is required. Because of the efficiency of the latest version of RDP, performance over the LAN is almost as fast as if you were physically sitting at the server.
Remote Desktop Security Issues
When enabled, Remote Desktop for Administration opens port 3389 and listens for connection requests. This port is a significant target and is often sought during port scans. Most open ports link to applications that must be attacked in complex ways to permit administrator level access to a computer. This service is designed to actually provide it, which makes it a prime target for attackers. There are several best practices that you should follow to maximize the security of this component.
Remember, with the exception of administrators, users must be authorized to connect using Remote Desktop for Administration. This is accomplished by adding a user’s account to the Remote Desktop Users group using one of the methods previously mentioned. If a user does not require this access, his or her account should never be a member of this group. You should control membership in this group through Group Policy or review it manually on a regular basis.
It is important to enforce strong security precautions on all accounts that are enabled to connect using Remote Desktop for Administration. Strong passwords and the use of account lock out are essential to make it difficult for an attacker to successfully use a brute force attack to gain system access. Administrators should be required to log on using a standard user account and perform administrative duties in the session using the Run as… feature. This will ensure maximum security of the administrator credentials, minimal damage to the Windows Server 2003 computer if the session is hijacked, and make it more difficult to accidentally install Trojans and other malicious code.
All users should be required to use the most recent client available for their platform. This will ensure that the latest security features are available to them. It should be standard policy to check frequently for software updates to both client and server components, because these may contain critical security fixes. In addition, users should be discouraged from storing their log-on credentials in the properties of the client. This enables anyone with physical access to the user’s machine to establish a session. It also stores sensitive information such as the user’s username and domain in a clear text file with an RDP extension in the user’s My Documents folder.
Finally, denial of service is a significant possibility when using Remote Desktop for Administration because it enables only two sessions to exist on the server. Both active and disconnected sessions count. So, if your company has three administrators and two of them leave disconnected sessions, the third will not be able to connect using Terminal Services until one of the existing sessions has been terminated. The solution to this may appear to be setting the time out settings so that sessions are reset shortly after they enter the disconnected state. However, this can cause serious problems.
An administrator may establish a session, begin an installation process and then disconnect to enable the installation to finish unmonitored. The previous settings would terminate the session, including the installation routine it was running, with potentially disastrous effects for the server. Special circumstances like these must be taken into account when configuring your policies. Because session timeout settings can be set at the user property level, Microsoft recommends the use of a special shared administrative account for circumstances like this. The strategy applies a timeout for disconnected sessions that are started by every user account except the shared account, which has no timeout settings applied. In this way, there should always be one connection available to a server, even though the second allowed connection is being consumed by a session involving the shared administrative account.
|
EAN: 2147483647
Pages: 173
- Chapter VI Web Site Quality and Usability in E-Commerce
- Chapter X Converting Browsers to Buyers: Key Considerations in Designing Business-to-Consumer Web Sites
- Chapter XII Web Design and E-Commerce
- Chapter XIV Product Catalog and Shopping Cart Effective Design
- Chapter XVII Internet Markets and E-Loyalty