Appendix A: Self Test Questions, Answers, and Explanations
|
This appendix provides complete Self Test Questions, Answers, and Explanations for each chapter.
Chapter 1: Using Windows Server 2003 Planning Tools and Documentation
Overview of Network Infrastructure Planning
| 1. | You are proposing the purchase of a new e-mail server for your corporate network. You have specified a new server from a major OEM manufacturer that is configured with a powerful quad-processor configuration, hot-swappable hard drives, and redundant power supplies and network adapters, with a three-year onsite warranty. Due to a budget crunch, the chairperson of the budget committee has suggested that the company can make do with a less powerful workgroup server from a local computer store. This server has only a single processor and no redundancy features, and a one-year onsite warranty. What reasons can you provide the budget committee members that might convince them to authorize the purchase of the server that you specified, even though it has a higher price tag?
| |
| 2. | You are the network administrator of a Windows NT 4 domain for a shipping warehouse that operates 24 hours a day, 6 days a week. You perform a full nightly backup of all user files at 3:00 a.m. Users on the overnight shift are complaining that they are often locked out of files that they need access to while the backup process is running. You are proposing a network upgrade to Windows Server 2003 in the near future. What Windows Server 2003 feature will assist you in addressing this problem?
| |
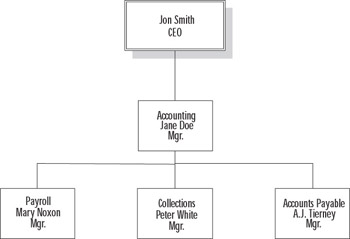
| 3. | A portion of your company’s organizational structure is shown in Figure 1.14. Third-level department managers report to the second-level department managers directly above them in the organizational chart. Second-level managers report to their corresponding vice presidents, who then report to the company CEO. Your company CEO would like a consistent security policy to be implemented across the entire network, but each subdepartment has specific desktop and application installation settings that you would like to be able to control and deploy centrally. What is the most efficient AD structure to design for this company?
| |
| 4. | You are the administrator for a network that supports a mixture of Windows NT 4 Workstation, Windows 2000, and Windows XP Professional. You are preparing to upgrade your network servers from Windows NT Server to Windows Server 2003. What is the strongest level of network authentication that you can configure your Windows domain to use in its current configuration (without installing third-party software)?
| |
Answers
| 1. | A, B. When calculating total cost of ownership (TCO), you should take into account the potential that your company will outgrow a less powerful server, and thus you will need to replace it more quickly. This has the potential to cost the company more money over time than if they had made the initial investment in more powerful hardware. TCO should also take into account “soft costs,” such as lost productivity and lost customer revenue due to downtime caused by hardware malfunction. Redundant hardware features will help to decrease this potential for downtime and increase the server’s overall availability. C, D. Answer C is incorrect because an extended warranty will likely reduce support costs over time, since repairs and parts will be covered for a longer period. Answer D is incorrect because Windows Server 2003, although it will offer better performance in a multiprocessor configuration, requires only a single processor to meet the installation requirements. |
| 2. | C. Volume Shadow Copy is a new feature in Windows Server 2003 that allows users to access files and folders on a server while they are being backed up, thus increasing the availability of centrally stored information on a Windows file server. A, B, D. Answer A is incorrect because disk quotas will assist you in monitoring and limiting disk usage on your network, but they will not address the issue of users being locked out of files that are being backed up. Answer B is incorrect because NTFS file permissions can dictate only which users or groups can read, modify, and/or delete a file or folder. The users are not being locked out of the files due to permissions issues. Answer D is incorrect because Network Load Balancing is a server clustering technology; it does not address the issue of accessing files that are being backed up. |
| 3. | A. A hierarchical organizational structure such as the one described in this question lends itself to a domain structure with nested OUs. Using OUs will also allow you to apply departmental settings centrally through GPOs. B, C, D. Answer B is incorrect because a single domain is more efficient if a network environment has unified security requirements. Answer C is incorrect because GPOs cannot be linked to group objects; they can be linked to only sites, domains and OUs. Answer D is incorrect because it creates more administrative overhead than is necessary for the environment described in the question. |
| 4. | D. The strongest authentication type that Windows NT 4 Workstation or Server can use without installing a third-party Kerberos client is NTLM version 2. A, B, C. Answer A is incorrect because Kerberos authentication can be used only by the Windows 2000 and Windows XP Professional workstations on your network, not the NT 4 workstations. Answer B is incorrect because LM authentication is a weaker authentication protocol than NTLM or NTLM version 2. Answer C is incorrect because NTLM, while stronger than LM authentication, is still not as effective as NTLM version 2. |
Analyzing Organizational Needs
| 5. | You are the administrator of a Windows 2000 network and are planning an upgrade to Windows Server 2003. As part of the upgrade process, you are attempting to determine whether you need to upgrade your network cabling from Token Ring cabling to 100MB Ethernet. What is the best way to go about making this determination?
| |
| 6. | After returning from a two-day technology management seminar, your CEO tells you that he would like to create a fault-tolerant configuration for the company’s heavily trafficked Web and database servers. Your network is currently running the Standard Edition of Windows NT 4. You have recently proposed an upgrade to Windows Server 2003. What features offered by this proposed upgrade would provide an attractive option to meet your CEO’s request?
| |
| 7. | You are the network administrator for a medium-sized company that consists of Sales, Customer Service, Accounting, Human Resources, and Data Entry departments. You have been receiving complaints that your company’s e-mail server has been performing more slowly than usual over the past several weeks. Several users have mentioned that their e-mail clients have “frozen” in the middle of sending an e-mail message, forcing them to reboot their machines. Upon investigating, you find that one user’s mailbox is roughly ten times the size of the second largest mailbox on the server, and this user is receiving approximately 1000 messages per day, compared to a company average of 46. The user in question is a data-entry clerk who does not use e-mail for sales inquiries or other business-related contacts. When you ask the user about her e-mail usage, she reports that she has been surfing the Web signing up for Internet coupons and contests, and she has been deluged with spam as a result. Since the user does not require e-mail access to perform her job function, you disable her e-mail account, and server performance slowly returns to normal. What measures can you implement to prevent this sort of incident from recurring? (Select all that apply.)
| |
Answers
| 5. | A. To obtain a network baseline, you need to view network utilization over an extended period of time, to get an accurate picture of your network’s overall bandwidth utilization. You can use the Windows Performance Monitor utility to collect this information quickly and easily. B, C, D. Answer B is incorrect because you would use the Performance Monitor utility to view network bandwidth utilization most efficiently. Network Monitor is used to capture individual packets. Although it does provide some bandwidth usage information, it does not directly monitor network performance. Answer C is incorrect because the IPSec Monitoring utility will examine only the IPSec protocol, not overall network utilization. Answer D is incorrect because taking only a single snapshot of network traffic will not provide an accurate picture of network utilization, which can fluctuate throughout the course of a day and week. |
| 6. | C, D. Windows Server 2003 provides the ability to configure Network Load Balancing and server clustering to increase the fault tolerance of your network services and resources. A, B. Answer A is incorrect because SMP processing allows a Windows server to effectively utilize hardware with multiple processors, but it does not provide fault tolerance. Answer B is incorrect because Volume Shadow Copy is used to provide uninterrupted file and folder access during network backups. Although regular backups are part of your disaster recovery solution, a backup solution should be implemented in addition to fault-tolerance schemes, not in place of them. |
| 7. | A, C. Implementing disk quotas will prevent a single user’s disk usage from interfering with the operation and performance of the entire server. An Acceptable Use Policy will provide all of your users with a list of appropriate uses for their office computers so that they can make the correct decision regarding their e-mail, Web, and other computer use. B, D. Answer B is incorrect because the level of user authentication was not the source of the problem; inappropriate use of the company’s computer resources is what caused the performance slowdown on the e-mail server. Answer D is incorrect because this solution will adversely affect the network access of the other users on your network who require network access. |
Developing a Test Network Environment
| 8. | You are the network administrator for a law firm that has multiple locations throughout the United States. Your firm has purchased a customer relationship management (CRM) application that will be hosted in the firm’s main office in Key Biscayne, Florida, and accessed by other offices using dedicated WAN links. You would like to test the performance of this software over a WAN link before deploying it to the other offices in the firm. Unfortunately, you only have access to test equipment in the Key Biscayne office location. What is the best way to test the performance of this application?
| |
| 9. | You are in the process of building a lab environment to test a new network application. You would like to isolate the test environment from your production equipment as much as possible to prevent any test changes from affecting your users’ daily tasks. What can you do to protect your production environment from changes performed in your test lab? (Select all that apply.)
| |
| 10. | You are designing a lab environment to test a proposed upgrade to Windows Server 2003. You are in the process of creating a domain structure in the test lab to assess various features and functions of the upgrade process, including switching the domain from mixed mode to native mode and moving from a standard DNS zone to AD-integrated DNS. At the same time that the Windows Server 2003 testing is taking place, you would also like to use the test lab to evaluate a new accounting package that will be implemented on the production network before the Windows Server 2003 upgrade takes place. You do not want the two batteries of tests to interfere with each other. Which of the following would be good design choices for the domain structure of the test lab? (Select all that apply.)
| |
| 11. | You have received a critical software update from the vendor of your accounting software suite. The software vendor has indicated that you should apply this patch as quickly as possible to correct a potential security breach. As the administrator for your network, what should you do when you receive this notice?
| |
| 12. | You are the network administrator for a small company that is considering purchasing a Windows 2003 Server machine to replace an aging Windows NT 4 Server machine. The client workstations run a mix of Windows 98, Windows NT Workstation, and Windows XP Professional. Each network client needs to be able to access the network server after it is upgraded, since the client workstations will be upgraded on a one-by-one basis over the course of several months. You have been informed that you will need to use the production server itself for testing, and that there is only sufficient budget to allot one representative workstation PC for test purposes. What is the best way for you to test client connectivity to Windows Server 2003?
| |
Answers
| 8. | B. You can simulate WAN traffic in a single location by installing routing equipment identical to the equipment used to connect the remote offices to the main headquarters where the application is being housed. A, C, D. Answer A is incorrect because this will provide only the bandwidth usage on each office’s LAN; it does not analyze the traffic that would be passed over the WAN link. Answer C is incorrect because you would be using a different access method than the one your offices would be using. This would not give you an accurate indication of the performance of the application over the dedicated WAN links. Answer D is incorrect because you should not introduce untested technologies into a production environment if you have the ability to assess them in a test environment first. |
| 9. | A, B. To prevent unauthorized network traffic from traversing between test environment and production equipment, you can place a router or firewall between the two locations to control network traffic between the two. You can also completely segregate the two environments by using two completely disconnected cabling systems. C, D. Answer C is incorrect because separating the test lab into an OU in an existing domain will not do much, if anything, to protect the production environment from changes made to the test lab. Answer D is incorrect because using two different speeds of Ethernet cabling will not prevent traffic from passing between the two environments. |
| 10. | A, D. Changes to DNS settings, as well as switching from mixed mode to native mode functionality, will affect all users and computers in an entire domain. To isolate these changes, you should create a separate domain or forest to test them. B, C. Answer B is incorrect because, in a single domain, the Windows Server 2003 testing might adversely affect the accounting software testing. Answer C is incorrect because a switch from mixed mode to native mode will still affect an OU within a single domain. |
| 11. | B. Even when a patch is designed to correct a potential security breach, you should still test it for proper functionality before applying it to your production network. A, C, D. Answer A is incorrect because you should test any patches before applying them to any production computers. Answer C is incorrect because installing a patch on even a single production workstation without testing it first can adversely affect your entire network. Answer D is incorrect because you should test the software patch in-house before applying it to your production network. |
| 12. | B. When you are working with limited hardware resources, a third-party utility like VMware will allow you to mimic several different operating systems on a single machine, allowing you to test the interoperability of multiple client operating systems with Windows Server 2003. A, C, D. Answer A is incorrect because configuring the test workstation with Windows Server 2003 will not give an accurate representation of how the actual server hardware will behave. Since you have the new server that will later be placed into production, it will be the most accurate server hardware to test with. Answer C is incorrect because testing each client operating system one at a time is an inefficient method. Using a utility like VMware will allow you to test far more conveniently and quickly. Answer D is incorrect because you should not use current production equipment for testing, since you don’t know how it will affect the behavior of the systems and hence the productivity of your users. |
Documenting the Planning and Network Design Process
| 13. | You have recently started working as a network administrator for a company whose network consists of multiple Windows Server 2003 domains. The previous network administrator left you with little documentation detailing how the network is configured, and you’ve discovered that many client workstations are behaving inconsistently—sometimes the Run line is unavailable, sometimes a user cannot access the Control Panel, and so on. You suspect that this is the result of Group Policy settings, and want to put together a list of all GPOs that are present within each domain on your network. What is the most efficient way of accomplishing this task?
| |
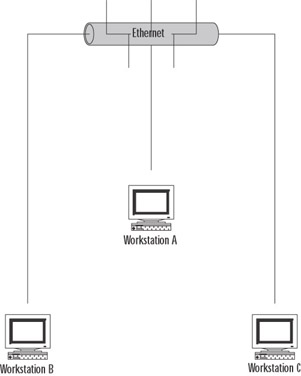
| 14. | A portion of your network is shown in the Figure 1.15. You are using Network Monitor from WorkstationB to capture network traffic for analysis. You suspect that there is an Internet Relay Chat (IRC) connection between WorkstationA and WorkstationC, but the Network Monitor trace does not show any sign of that connection. What is the most likely reason for this?
| |
| 15. | Your company, airplanes.com, has recently undergone a merger with southern-airplanes.com, and you have taken over the network management of both halves of the newly formed company. Airplanes.com has a strict policy of desktop and software installation restrictions, while southern-airplanes.com has historically been more lenient with allowing users to customize their computers and install personal software. Several of the users from southern-airplanes.com have complained about the policy restrictions that have been placed on their desktops. You have been asked to present a report to the management group detailing which restrictions are in place on various OUs. What is the most efficient way to present this information to the management group in an easily readable format?
| |
Answers
| 13. | B. A significant advantage to GPMC is that it includes several preconfigured scripts to ease and automate many administrative tasks, one of which will allow you to list all GPOs that are present in a given domain. A, C, D. Answer A is not the most efficient way to determine the total number of GPOs present on your network. Answer C is incorrect because this will indicate only the “winning GPO” that applied each setting; there might be other GPOs that exist elsewhere in the domain structure. Answer D is also inefficient and will require more manual intervention than using an easily automated script like the one suggested in Answer B. |
| 14. | C. In order to capture and analyze all traffic on a network segment, you need to use a network traffic analyzer that can operate in promiscuous mode, such as the one that ships with Microsoft Systems Management Server (SMS). The version included in Windows Server 2003 captures only packets going directly to or from the machine on which it is running. A, B, D. Answer A is incorrect because Network Monitor will capture any network packets that are directed towards the network adapter on the machine running the monitor. Answer B is incorrect because Windows workstations support IRC chat and relay applications. Answer D is incorrect because Performance Monitor is used to analyze performance metrics on a given machine, including (but not limited to) processor speed, RAM, paging file, and hard drive usage. |
| 15. | D. The GPMC presents GPO settings in a unified and easy-to-read format that can be saved as an HTML file and printed or published to a Web page. A, B, C. Answer A is incorrect because an OU’s Properties sheet will show only which GPOs have been applied against the OU; it will not list the settings that are in effect. Answer B is not as efficient as using the GPMC to generate a preformatted HTML report of GPO settings. Answer C is incorrect because this will not provide the management group members with the most complete information available to them; they will see only the GPO settings that you demonstrate to them. |
|
EAN: 2147483647
Pages: 173
- Chapter I e-Search: A Conceptual Framework of Online Consumer Behavior
- Chapter VII Objective and Perceived Complexity and Their Impacts on Internet Communication
- Chapter VIII Personalization Systems and Their Deployment as Web Site Interface Design Decisions
- Chapter XII Web Design and E-Commerce
- Chapter XVIII Web Systems Design, Litigation, and Online Consumer Behavior