Troubleshooting Caching and Publishing Problems
|
In this section, we examine some common problems involving two important ISA Server functions: caching and publishing.
Caching Problems
When ISA Server is installed in caching or integrated mode, it caches objects to accelerate client access. In some cases, you might encounter problems with the caching function. In this section, we look at some common cache-related problems.
All Web Objects Not Being Cached
You might find that client access to Internet objects does not seem to enjoy any noticeable improvement with ISA Server. This could be due to the fact that your clients are commonly requesting objects that are not in the cache. ISA Server caches only the objects that meet the caching criteria you have configured.
The solution could be to adjust the cache content specifications. You can determine which HTTP objects will be cached according to several factors. To configure which content should or should not be cached, right-click Cache Configuration in the left console pane of the ISA Management MMC under the name of the server or array. Select Properties.
Select the Advanced tab of the Properties sheet, shown in Figure 26.15. You can make adjustments here that result in caching of more (or fewer) objects.
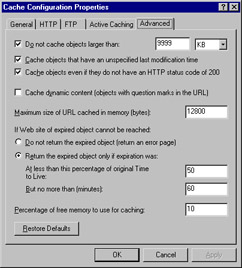
Figure 26.15: You Can Configure Which Content Will Be Cached Using the Cache Configuration Properties Sheet
Web Proxy Service Does Not Start
If the Web Proxy Service will not start, this can be due to the fact that the cache contents file has become corrupted. The cache file is stored on a drive on which space has been allocated for this purpose. To correct this problem, you might need to reconfigure the cache drive(s). Remember that the cache drive(s) must be formatted in NTFS.
Publishing Problems
Publishing makes servers on the internal network available to users outside the LAN (on the other side of the ISA server). Publishing problems can involve the inability of authorized clients to access the published servers.
In this section, we look at some specific scenarios that involve publishing problems and how you can correct them.
Inability of Clients to Access Published Web Server
If clients are unable to access a published Web server and they receive a 403 ("Access Forbidden") error, this could be due to the fact that an access policy requires authentication. If no authentication method is configured for the listener, clients will not be able to authenticate, and thus access will be explicitly denied.
The solution is to configure one or more authentication methods for the listener. Clients' browsers will have to support one of the configured authentication methods in order to be authenticated. Authentication methods are configured on the Incoming Web Requests and Outgoing Web Requests tabs of the array's Properties sheet, as described earlier in this chapter.
Some of the more commonly encountered HTTP error codes include:
-
302 Redirection to a new URL. The resource has moved and the new URL is presented.
-
400 Bad request. The server did not understand the URL entered due to incorrect syntax.
-
401 Unauthorized. The user requested a document and did not provide authentication credentials.
-
403 Forbidden. Access is explicitly denied.
-
404 Not found. The document does not exist on this server.
-
500 Internal server error. The system administrator should check the error log.
-
8181 Certificate has expired (secure servers).
An HTTP 200 code indicates a successful transmission. All codes in the 3xx range indicate redirection messages; those in the 4xx range indicate client errors of some type; those in the 5xx range indicate server errors of some type. Messages in 1xx range are informational (for example, 101: switching protocols).
Inability of External Clients to Send E-Mail Via Exchange Server
If you have external clients who need to send e-mail via an internal Exchange Server and they are unable to do so, the cause and solution could depend on how the Exchange Server is set up, either as a firewall client or a SecureNAT client.
Exchange Server Set Up as Firewall Client
If the Exchange Server is a firewall client, there could be a conflict between a server publishing rule and a firewall client configuration file.
The solution is to remove the Wspclnt.ini file from the publishing server and run the Mail Server Security Wizard. The wizard allows you to host and secure a mail server behind the ISA server and easily configures ISA rules to publish the mail services to the external users.
To run the wizard, right-click Server publishing rules under the Publishing object for the server or array. Select Secure Mail Server, as shown in Figure 26.16.
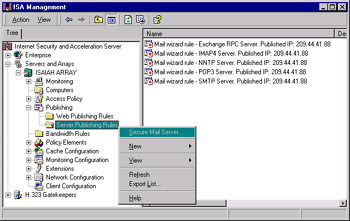
Figure 26.16: Use the Secure Mail Server Option to Publish a Mail Server to External Clients
Another cause of this problem is the inability of the Exchange server to bind to the SMTP port on the ISA server due to another local or service or application on the ISA server that is binding to port 25 before the Exchange server has a chance to do so. Ensure that no other services or applications are using port 25 on the ISA server.
| Note | If the connection between the ISA server and the Exchange server is broken momentarily, you need to restart the Exchange services in order for the Exchange server to bind to the appropriate ports on the ISA server. |
Exchange Server Set Up as SecureNAT Client
If the Exchange server is a S-NAT client, this problem can be caused by incorrect configuration of the server publishing rules. The solution is to see that the publishing rules are configured to allow the external interface to pass SMTP traffic on port 25 and POP3 traffic on port 110 to the IP address and port of the internal Exchange server.
You should also check to ensure that the publishing rule is configured to apply to all Internet clients or that a client address set is specified that includes the addresses of the clients who need to use the server. Note that IP packet filtering must be enabled in order to use client address sets; if IP packet filtering is not enabled, the rule will apply to all clients.
|
EAN: 2147483647
Pages: 240