Troubleshooting Guidelines
|
Many professions exist for the purpose of solving problems of one sort or another. When people have legal problems, they call an attorney. When they have medical problems, they visit a doctor. When they have problems with their computers or the network, they turn to you—the administrator—to solve those problems. Doctors, lawyers, and other professionals learn, as part of their formal education and practical training, the importance of following a step-by-step procedure that can be applied to most problem-solving situations.
This basic process applies to troubleshooting problems with computer software programs such as ISA Server. In essence, you are the doctor of the ISA server. We have also another step, which the other professionals also practice but which is rarely mentioned in formal problem-solving models: documentation. Police officers file reports, doctors complete medical charts, and attorneys decimate entire forests to create the mass of paperwork that document every step of the legal process. IT professionals—although not required to do so by law, as those in the other professions are—should get into the habit of thoroughly documenting troubleshooting incidents. This practice will benefit you as well as others who encounter the same problem in the future.
The Five Steps of Troubleshooting
Our systematic approach to troubleshooting involves five basic steps:
-
Information gathering
-
Analysis and planning
-
Implementation of a solution
-
Assessment of the effectiveness of the solution
-
Documentation of the incident
In the following sections, we address each of these steps individually.
Information Gathering
Before we can determine how to address a problem—or even assess what the problem is—we must gather information. Doctors do it by asking questions of their patients, observing physical signs and symptoms, and conducting lab tests. Detectives do it by interviewing witnesses, personally examining the crime scene, and gathering evidence. Attorneys do it by taking depositions, researching the facts of the case, and studying prior court decisions.
An ISA Server administrator can gather information by observing the undesirable behavior of the software, questioning users who are experiencing problems, and using common tools and utilities to monitor the server's and network's activity (see Figure 26.1).
Figure 26.1: Information Gathering Can Take Many Forms
Log files comprise an important source of information you should consult during the data-gathering stage. Both the Windows Server logs (accessed via Event Viewer) and the ISA Server logs (by default, located in the ISA Server Installation folder, in the ISALogs subfolder) can provide valuable information and a starting point for troubleshooting problems. An example of an IP Packet Filter log is shown in Figure 26.2.
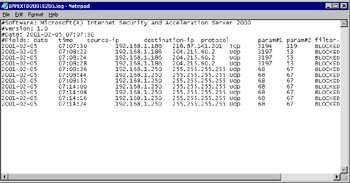
Figure 26.2: ISA Log Files Can Be Useful in Troubleshooting Various Problems
ISA logging can be configured for the Proxy Service, Firewall Service, and Web Proxy Service, in W3extended format or ISA Server format. Performance logs can also be useful in troubleshooting performance-related problems.
Analysis
Once you've gathered all the information possible regarding the problem (including attempting to reproduce it), it's time to analyze the data. This phase is also called the diagnostic or the problem isolation phase. The first step is to sort through all the information collected and determine which is relevant and which is not.
The primary task in this phase is to look for patterns. Do the "symptoms" match something you've experienced, heard about, or read about? Organize the relevant information—on paper, on screen, or in your head—and determine which facts fit each of your possible theories as to the cause of the problem.
An important part of the analysis phase involves prioritizing. This includes prioritizing the problems, if there are multiple problems (and often there are). Performance problems are generally less urgent than access problems, for example. You also need to prioritize the possible solutions. Time, cost, and ease of implementation are all factors to consider. A good rule of thumb is to try the simplest, least expensive, and quickest solutions first.
Your analysis of the data will lead you to formulate a logical plan based on your diagnoses, possible solutions, and priorities.
Solution Implementation
Although there could be several possible solutions to a problem, you should always implement one change at a time. Assess the results of that change before trying something else. This will save you much grief in the long run; there is nothing more frustrating than changing several different settings, discovering that the problem has been solved, and not knowing which of your actions solved it.
Assessment
This is also called the follow-up stage. It is vital that you assess the results of your actions and determine whether your "fix" worked, whether it was only a temporary workaround or actually solved the problem, whether it caused other problems while correcting the original one, and what can be done in the future to prevent the problem from recurring.
Documentation
After completing your assessment, you should develop a succinct summarization of the problem, which should include:
-
The reported and observed symptoms of the problem
-
Causation theories and the reasoning behind them
-
Corrective actions taken
-
Results of those actions
-
Recommendations for prevention of a recurrence of the problem
This summarization should be in written form and kept in a permanent log. You might also want to distribute copies of the report to others, such as your superiors within the company, the affected users, other members of the IT department, and so forth. Documentation is a very important but often-overlooked step in the troubleshooting process.
ISA Server and Windows 2000 Diagnostic Tools
The Windows 2000 operating system and the ISA Server software include a number of tools and utilities that will help you gather information for troubleshooting purposes. These tools include:
-
Event Viewer logs
-
Performance Tool
-
Network Monitor
-
Various log files
In this section, we look briefly at the Event Viewer logs and the Network Monitor.
Event Viewer Logs
The Windows 2000 Event Viewer monitors application, security, and system events and records information to log files, which you can examine for clues to the causes of hardware and software problems. The Event Viewer is accessed via Start | Programs | Administrative Tools | Event Viewer or through the Computer Management MMC.
Three basic logs are available in the Event Viewer.
-
The Application log contains information about events logged by programs (for example, ISA Server). Events logged by the application are determined by the developer of the application.
-
The System log contains information about events that are logged by the Windows 2000 system components, such as driver failures, failure of a system service to load, and so forth.
-
The Security log records security-related events. Auditing must be enabled in order for events to be logged to the Security log.
Depending on what other services you have installed on the Windows 2000 Server, there could be other logs in the Event Viewer (for example, the Directory Service log, DNS Server log, or the File Replication Service log).
The event types recorded depend on the log type. Event types are identified by special icons. For example, the Application log records three event types:
-
Error Identified by a red circle with a white X, this event type indicates a significant problem that could result in loss of functionality or data.
-
Information Identified by a white balloon with a blue i, this event type indicates successful completion of an operation.
-
Warning Identified by a yellow triangle with a black exclamation point, this event type indicates a potential problem, although not as serious or imminent as events tagged as errors.
Events in the log are listed in the right detail pane of the Event Viewer. Additional information can be viewed in the event's Properties sheet, accessed by double-clicking the event. Each event is identified by an Event ID. In the Help files subsection of the next section, we discuss how to interpret ISA Server event IDs.
| Note | When troubleshooting network problems, always start by checking the Event Viewer and other logs. In many cases, the information that will point you in the right direction is there waiting for you. |
Network Monitor
The Windows 2000 Network Monitor is a built-in packet sniffer that can be used to capture and display frames (packets) that pass to or from the Windows 2000 server. Network Monitor can be invaluable in troubleshooting network-related problems.
The Network Monitor tool uses the Network Monitor driver to receive frames from a network adapter and display statistics relating to specified frames (which can be displayed according to protocol, sending/receiving computer, and other criteria).
Network Monitor's capture filters are configured by the administrator to specify the types of network information that should be monitored (for example, only the packets received from a particular IP address or using a specific protocol). Network Monitor's display filters allow you to sort data that has already been captured, to display only specified information.
Network Monitor can be used to view the packets that are sent to or from the ISA server. For example, you could monitor packets to determine what port is being used by a particular protocol or application.
| Note | The version of Network Monitor included with Windows 2000 has limited functionality. It captures only frames sent to or from the computer on which Network Monitor is running, and it does not allow you to edit and transmit frames. Another version of Microsoft's Network Monitor provides these functions and will capture packets sent to and from all computers on the network segment. The full-featured version is included in Microsoft System Management Server (SMS). |
ISA Server Troubleshooting Resources
As ISA Server is implemented on more and more networks, the amount of formal and informal documentation available is sure to increase. Meanwhile, there are already a number of resources (in addition to this book) to which you can turn when you need troubleshooting help. These include:
-
ISA Server Help files
-
Microsoft Tech Support
-
Web resources
-
Books and magazines
-
Internet mailing lists and newsgroups
In the following sections, we discuss each of these resources in more detail.
ISA Server Help Files
The ISA Server Help files provide a wealth of information on both concepts and the how-to of configuration. The organization of the Help files makes them easy to navigate. You will find useful checklists to ensure that you don't omit important steps during installation, configuration, and other tasks. The "How To…" section guides you step by step through important procedures. In the "Concepts" section, you will find background information to help you understand how various ISA components operate and interoperate. Finally, a separate "Troubleshooting" section addresses specific reported problems and what to do about them (see Figure 26.3).
Figure 26.3: The ISA Server Help Files Contain a Special "Troubleshooting" Section
Under the "Additional Resources" heading in the Help files, you will find a glossary of terms relating to ISA Server. An especially important resource that is listed under "Additional Resources" is a list of event messages that will help you decipher those sometimes-mysterious ISA-related messages that appear in the Event Viewer logs.
Event messages are broken into the following categories:
-
Alert event messages
-
Bandwidth event messages
-
Caching event messages
-
Common service event messages
-
Dial-up connection event messages
-
Intrusion detection event messages
-
ISA Server Control Service event messages
-
ISA Server Firewall Service event messages
-
ISA Server Web Proxy Service event messages
-
Log event messages
-
Packet filter event messages
-
Server event messages
Within the categories, event messages are identified by the event ID. This ID number identifies the event type and is shown in the Event Properties sheet when you click the event (information, warning, or error) in the right pane of the Event Viewer in the Application log.
For example, in Figure 26.4, we can select an event from the right context pane. In this example, we have selected the Warning event recorded by the Microsoft Web Proxy Service at 3:01:46 p.m.
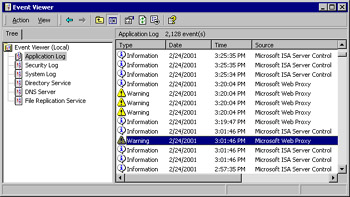
Figure 26.4: Select an Event from the Right Context Pane in the Application Log
When you double-click the selected event, you will see its Properties sheet, as shown in Figure 26.5.
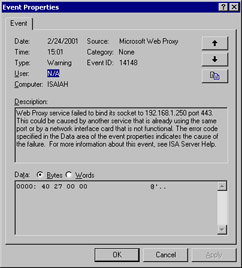
Figure 26.5: The Event's Properties Sheet Gives You a Great Deal of Information, Including the Event ID
On the Properties sheet, you will see a summary of pertinent information about the event, including the date and time of occurrence, warning type, user or computer from which the event originated, source/service, category (if applicable), and the Event ID. There is also a description of the event, which refers you to the ISA Server Help file.
If we then go to the Help file and look under the event category (Web Proxy Service), we will find the ID (14148) in the list, as shown in Figure 26.6.
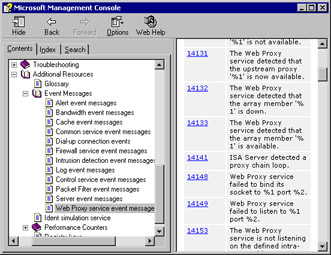
Figure 26.6: You Can Use the Event Category and ID to Locate the Event Message in the Help Files
Clicking the Event ID will provide you with information about the event message, an explanation of the message, and suggested user action(s) to rectify the problem, as shown in Figure 26.7.
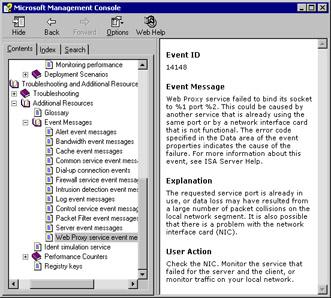
Figure 26.7: The Help File Provides Information about the Event Message, an Explanation, and Suggested User Action(s)
Another useful source of information included in the "Additional Resources" section is the list of all ISA performance counters and the descriptions and explanations of how each works. These are categorized according to the associated performance objects.
Finally, there is a list of Registry keys that can be modified to fine-tune ISA Server performance.
Microsoft Documentation and Technical Support
Microsoft provides a wealth of support resources on its Web site (http://support.microsoft.com/directory), where you will find two categories of available support options:
-
Self-support resources
-
Assisted-support information
The self-support resources include the searchable knowledge base (see Figure 26.8), which provides technical support information based on known problems and their solutions (organized as "Q" articles because of their numbering scheme; for example, Article Q257218).
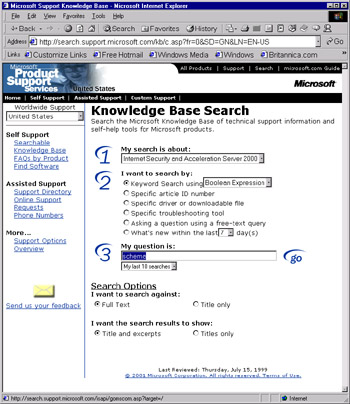
Figure 26.8: The Searchable Knowledge Base Provides Technical Support Information and Self-Help Tools
The self-support section also includes a set of lists of FAQs and a Download Center where you can find service packs, patches, and updates.
The assisted-support section provides support phone numbers and online support request forms for registered products. Additional assisted-support resources include the Microsoft Gold Certified Support Partner program, Expired Warranty options, and Microsoft Certified Partners (independent experts you can hire to provide solutions to your problems with Microsoft products).
| Note | Professional support services do not come cheap. Telephone support from Microsoft costs $245 per incident if the product is not under warranty. Web-based support requests are $195 each. Pricing for certified partner support varies, ranging from $99 per incident and up. |
Premier and Alliance support packages are available to enterprise-level businesses. More information on these offerings can be found on the Microsoft Web site.
Another excellent source of support information is TechNet Online, at www.microsoft.com/technet. Here you will find security bulletins, planning and deployment guides, white papers, and announcements of upcoming professional and training events as well as evaluation kits for new software packages.
Microsoft maintains Web resources for each of its product lines. ISA Server is featured on its own Web site at www.microsoft.com/isaserver. Here you will find information and updates about ISA Server issues.
Third-Party Web Resources
Third-party Web sites can come and go, but a good search engine will turn up several sites that provide information on ISA Server or add-on products that work with it. One of the best third-party Web sites is www.isaserver.org. This site features current ISA Server-related news, tutorials and advice on deploying ISA Server, ISA Server FAQs, pointers to relevant articles and books, the newest bug fixes, white papers, and certification information. The site also provides message boards and instructions for joining an ISA Server discussion list (discussed in the "Internet Mailing Lists and Newsgroups" section of this chapter).
Books and Magazines
Specific issues (such as deploying ISA in a DMZ or perimeter network or configuring ISA servers in a chained hierarchy) could be the subject of articles in popular Windows 2000-oriented technical magazines. As the use of ISA Server becomes more widespread, you will see more information about it in both print publications and online "e-zines" and tech Web sites. Here are a few of the good online sources of technical articles on Microsoft products:
-
www.swynk.com Microsoft-related articles and columns.
-
www.brainbuzz.com IT career network, certification study aids, and IT resources.
-
www.techrepublic.com Information site for IT professionals.
-
www.w2knews.com The Sunbelt Software W2K Electronic Newsletter.
Internet Mailing Lists and Newsgroups
One of the most diverse sources of information for current and aspiring IT professionals is Internet mailing lists. There are literally hundreds of thousands of lists, powered by automated mailing list software such as Listserv, Majordomo, and Lyris, as well as those hosted through Web-based mailing list services such as Yahoogroups.com and Topica.com. There are mailing lists devoted to almost any IT (or other) topic imaginable, including ISA Server.
The premier ISA-specific mailing list is hosted by www.isaserver.org. It is a fairly high-volume list, membership is open, and list members share their experiences installing, configuring, and using ISA Server, posting their questions and problems and assisting one another with ISA-related issues.
Those who don't want to receive the large amount of mail generated by some mailing lists might find it more convenient to subscribe to Internet newsgroups. With a newsreader such as Outlook Express, you can subscribe to as many newsgroups as you like and read the messages only when you like. There are no mail messages to clutter up your inbox.
Microsoft hosts several public newsgroups devoted to discussions of ISA Server:
-
ISA Server General Support group (microsoft.public.isa)
-
ISA Server Enterprise (microsoft.public.isa.enterprise)
-
ISA Server newsgroup (Microsoft.public.isaserver)
The newsgroups often generate a very high volume of posts. Most newsreaders allow you to sort posts by thread (subject line) to better organize the information, as shown in Figure 26.9.
Figure 26.9: Microsoft's ISA Server Newsgroups Provide an Excellent Source of Troubleshooting Information
Although Microsoft does not monitor the content of its public newsgroups, they are often populated by Microsoft Most Valuable Professionals (MVPs), who provide informal leadership.
Microsoft newsgroups can be downloaded from the msnews.microsoft.com news server. You can visit http://support.microsoft.com/default.aspx?scid=/support/news/howto/default.asp on the Web for information about how to view the newsgroups.
|
EAN: 2147483647
Pages: 240