Defending Your Mac from Net Attacks
| The Internet is a major source of threat to the health and well-being of your Macs and the network to which they are connected. You face two fundamental types of threats: viruses and hackers. Although viruses receive more media attention, it is easier to defend against viruses than against attacks from hackers. However, with some relatively simple activity, it is possible to protect yourself from either threat. Defending Your Mac from Virus AttacksNo matter what level of computer user you are, because of the extensive media hype about viruses, you are likely to be keenly aware of them. Although many viruses are relatively harmless, some viruses can do damage to your machine. Part of practicing smart computing is understanding viruses and taking appropriate steps to protect your machine from them. CAUTION Under previous versions of the Mac OS, there were many fewer viruses on the Mac platform than for Windows or other operating systems. However, because Mac OS X is based on Unix, it is possible that Unix viruses will be a threat to machines running Mac OS X. Until this threat is more fully understood, Mac OS X users would do well to pay additional attention to virus threats. Understanding the Types of VirusesAlthough there are many types of individual viruses, there are two major groups of viruses of which you need to be aware:
Covering the multitude of viruses that are out there is beyond the scope of this book, and besides, there is no real need to become an expert on the viruses that exist. It is more important that you understand how to protect yourself from these viruses and be able to recover from an infection should one occur. Preventing Virus InfectionI hate to use this cliché, but when it comes to viruses, an ounce of prevention is indeed worth a pound of cure. The main way to avoid viruses is to avoid files that are likely to have viruses in them. Following are some practices to help you "stay clean":
Identifying Virus InfectionEven with good preventive measures, you might occasionally become infected. Hopefully, you will find out that you have been infected by being notified by your antivirus software that means it is doing its job. But if you suddenly notice that your computer is acting peculiarly, you might have become infected. What does acting peculiarly mean? Viruses can have many different effects on your computer; some of the more common effects are the following:
Using Antivirus SoftwareAlthough the best defense against viruses is being very careful about the files you transfer onto your machine, you should also obtain and use a good antivirus application. Good antivirus applications generally perform the following functions:
NOTE Most viruses are identified by their code. The antivirus software knows about the virus's code through its virus definition file. As new viruses appear, this virus definition file needs to be updated so that the new viruses will be recognized as being viruses. You can usually obtain an updated virus definition file from the Web site of the manufacturer of your antivirus software. Most programs automate this process and can update the virus definition at intervals that you set. NOTE One of the important things to look for in an antivirus program is that it can detect and repair macro viruses. Macro viruses are easy to create and spread, and some of them are quite nasty. As with previous versions of the Mac OS, there are several major antivirus applications, which include Norton AntiVirus for Mac and Virex. These applications provide most of the features in the previous list, and they work well. You should obtain and use one of these applications to protect your Mac against viruses and to repair your Mac should it become infected.
To get more information about Virex and to download it (if you have a .Mac account), visit www.mac.com.
Defending Your Mac Against Net HackersIf you have a broadband connection to the Internet such as a cable or DSL modem, being attacked by hackers is a much more real threat than are viruses. And with a broadband connection, you will be attacked, daily if not hourly or even more frequently. Hackers are continuously looking for machines that they can exploit, either to do damage to you or to use your machine to do damage to others (such as using your machine to launch a spam attack). Most of these attacks are carried out by applications, so that they can be both automatic and continuous. CAUTION Never expose a machine containing sensitive or production data to a broadband connection without protecting that machine from network attack. Doing so makes everything on such a machine vulnerable to exposure to a hacker, and the machine itself can be used to carry out attacks on other networks and machines. There are two fundamental ways you can prevent your Mac from being hacked through your broadband Internet connection: Use a server/hub to isolate the machines on your network from the outside world or use a software firewall to protect each machine on the network from attack. Using a Server and Firewall to Protect Your NetworkYou can isolate the machines on your network from attack by placing a physical barrier between them and the public Internet. You can use a Dynamic Host Configuration Protocol (DHCP) server that provides Network Address Translation (NAT) protection for your network, or you can add and use a hub that contains a more sophisticated firewall to ensure that your network can't be violated. A benefit to these devices is that you can also use them to share a single Internet connection.
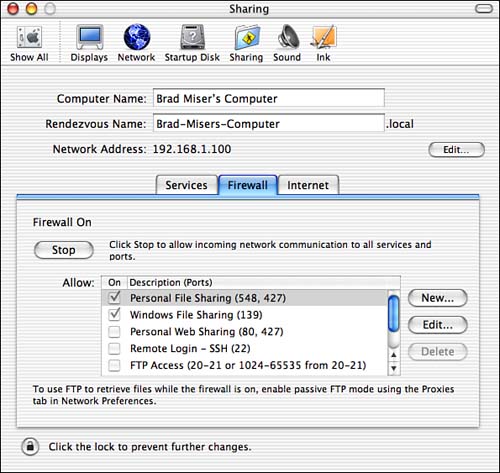
NOTE One of the easiest and best ways to protect machines on a local network from attack and to share an Internet connection is to install an AirPort Hardware Access Point. These devices provide NAT protection of any computers that obtain Internet service through them, and for most users, this is an adequate level of protection from hacking. Using a Software Firewall to Protect Your NetworkYou can also install and use a software firewall; a software firewall prevents unexpected access to your Mac from the Internet. Software firewalls can be quite effective and might be the best solution if you have only a single Mac connected to the Internet. CAUTION Unlike a hardware firewall or NAT hub, a software firewall must be installed on each computer that is attached to your network. A software firewall works by blocking access to specific ports on your Mac; these ports are linked to specific services. If hackers can access these ports on your machine, they can use them to attack your machine directly to launch attacks on other computers, servers, and networks (such as Denial-of-Service attacks, in which a system is overloaded by repeated requests from many machines).
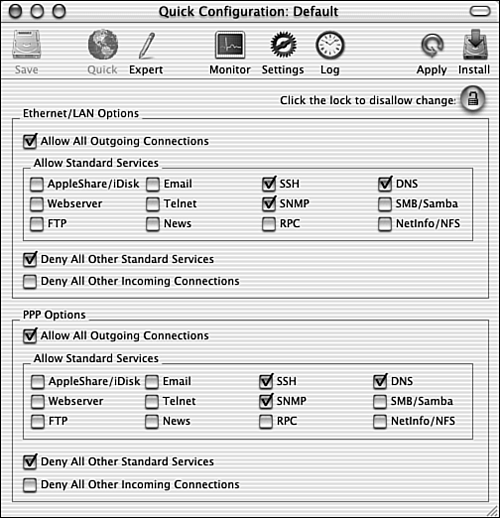
Only the services you allow will be permitted to access your Mac. All others will be denied. This provides more than adequate protection for most Mac users. You can gain more specific control over the firewall if you choose to. However, configuring this firewall directly requires a fairly complete understanding of Unix and firewalls and requires more energy and time than most Mac users will care to spend on it. A better solution is to use an application that provides an interface for the firewall so that it is much easier to configure. One such application is Brian Hill's Brickhouse. NOTE
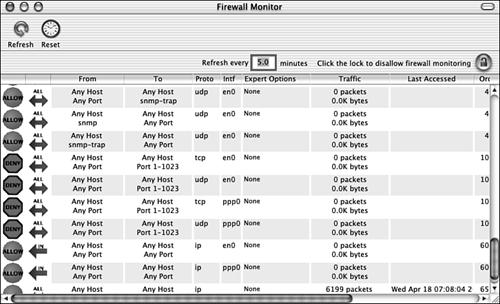
NOTE Brickhouse is shareware; the registration fee is $25. If you use the application, you should register it by going to http://order.kagi.com/?5MG. Using Brickhouse to protect your Mac requires two tasks: install the application and then configure it. After it is running on your machine, you can use its log feature to monitor attacks on your machine. NOTE Brickhouse includes documentation that provides details about how to use it. You can access this information by choosing Help, Brickhouse Help. You should refer to this help to get more detailed information about how to configure the firewall than I have room to provide here. Install and configure Brickhouse with the following steps:
TIP You can learn more about each service listed in the Configuration window by pointing to it and reading the information window that pops up. Following are some other features of Brickhouse you should explore:
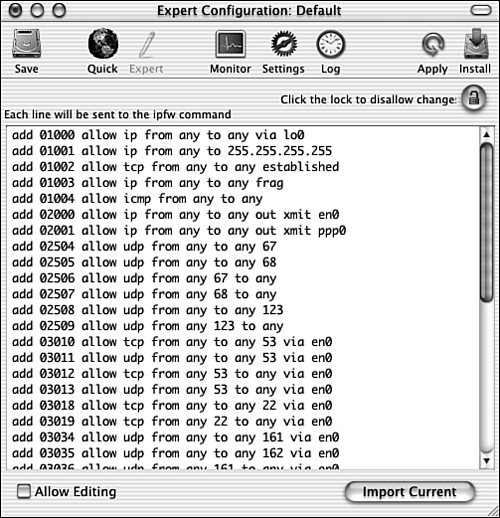
NOTE One of the services most used by hackers is the Network News Transfer Protocol (NNTP). If you don't use this service, you should make sure that it is disabled by Brickhouse. After you have applied and installed the firewall configuration, its protection remains on until you disable it. The configuration you install applies to all user accounts for your Mac; in other words, this is a system-level service, not a user account level service. The firewall configuration is stored in the directory Mac OS X/Library/StartupItems/Firewall, where Mac OS X is your Mac OS X startup volume. You can disable the firewall by deleting this directory or by choosing Options, Remove Startup File from within Blockhouse. You can also control the firewall directly by using the command-line interface. You can do this from within Brickhouse by choosing Options, Expert Configuration or by clicking the Expert button. In the Brickhouse window, you will be able to directly enter commands. To see how the current configuration translates into commands, click the Import Current button (see Figure 27.11). You can modify the commands directly in this window and apply them just as you would apply settings using the GUI window. Figure 27.11. You can configure the firewall by typing commands in the Expert mode.
TIP You can also configure the firewall in the Terminal application. To see the commands that are available, in the Terminal, type man ipfw.
|
EAN: 2147483647
Pages: 260
 To learn how to install and use a DHCP server or firewall,
To learn how to install and use a DHCP server or firewall,