Section 19.6. Exercises
| 1. | Compare table-driven and source-initiated routing algorithms in terms of
|
| 2. | Suppose that we have the ad-hoc network shown in Figure 19.7. The number on each link indicates the strength of the signal on that link. At time t 1 , the threshold value of 2.5 is applied on all links as the minimum good connection. Use the DSDV protocol to Figure 19.7. Exercises 2 and 3 ad-hoc network
|
| 3. | With the same conditions stated in exercise 2, use the AODV protocol to
|
| 4. | Consider an ad-hoc network consisting of users spread randomly in locations with Poisson distribution, where there are n users per square meter. Each user transmits with 40 percent probability and receives data with 60 percent probability in an assigned time slot. Make an assumption that the path loss exponent is ² .
|
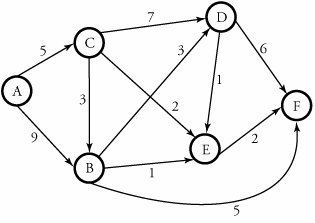
| 5. | Consider Figure 19.3. We want to make a more detailed assignment to each node for routing from node A to F, using CGSR. Assume that the energy of cluster heads is normalized to A = 23, B = 18, C = 15, D = 16, E = 25, and F = 14. Find the best path from A to F. Assume that cluster heads have bidirectional links. |
| 6. | Computer simulation project . Consider the ad-hoc network shown in Figure 19.5. We want to implement AODV on this network. We first apply distance-vector routing to discover routes on an interconnected network. The primary distance vector routing uses the Bellman-Ford algorithm. Consider the network to be subject to topological changes at any time. You assign these times. Changes include a link to fail unexpectedly or a new link to be created or added. Let your program discover these changes, automatically update nodes' routing tables, and propagate these changes to the other nodes. |
| 7. | Computer simulation project . Now consider the network you analyzed in exercise 6. We want to test the AODV route-discovery procedure and the ability of AODV to handle link and node failures. At the network level, design a least-cost algorithm that gives the shortest path, taking failing nodes (malicious nodes) into account. If one of the nodes in the shortest path is a bad one, the next available shortest path must be found in the algorithm. In the algorithm you develop, the failure of a link should not affect the shortest-path determination. If a malicious node is in the network, that node is being discarded, and fresh routes are determined that have shortest path to the destination requested by the source node in the network. Assign faults deterministically, starting from the best path, and determine the shortest paths available. Determine how the best paths vary when the number of failing nodes is assigned randomly. Study how the network topology changes for a given n nodes with k failing nodes in the network. You will see that the total costs of the shortest paths between the sources and the destinations gradually increase with the number of fault nodes in the network if the fault nodes are assigned starting from the best path. |
EAN: 2147483647
Pages: 211
 t
t