Group Policy Options
Recovery
Ever misplace your car keys?
With BitLocker protecting the data on your laptop, there are a few situations that might come up, where suddenly, you (or one of your users) is locked out. Situations might be:
-
A forgotten PIN (in the TPM+PIN scenario)
-
A lost startup key (TPM+USB startup key or non-TPM computer)
-
Integrity check failure (TPM only, TPM+PIN or TPM+USB startup key)
In any of these cases, BitLocker will refuse to unlock the Windows OS volume, and you will not be able to start that installation of Windows Vista. Even if you start another installation of Windows Vista (or another OS) from a different partition, or swap the disk into a different machine, you still will not be able to access the data.
This is a good thing-if it means an attacker is being thwarted. It would be a bad thing, though, if it means you can't get to your data because you've simply made a mistake or a piece of hardware has failed. (For maintenance, hopefully, if it is a planned situation, you've disabled BitLocker previously with a clear key, but sometimes, unplanned things happen.)
Instead of simply unlocking the disk, BitLocker code (running in the Boot Manager), will display a screen called the "recovery console," which looks like this:
Windows bitlocker Driver Encryption key needed. Insert key storage media. Press ESC to reboot after the media is in place. Drive Label: BHYNES-VISTABDE OS 10/1/2006 Key Filename: .BEK ENTER=Recovery ESC=Reboot
If you encounter the recovery console, you have only a few options:
-
Can you fix the situation? In other words, can you undo whatever caused BitLocker to go into recovery? Can you find the missing startup key? Can you connect the drive back to the original computer? If so, restart the computer and proceed as normal. If that is not possible, answer questions 2 and 3.
-
Do you have a recovery key? Recall that a recovery key is the recovery password stored on a USB drive during BitLocker setup, or the USB startup key used with BitLocker on a computer without a TPM. If there is no recovery key, then continue: ask yourself question 3.
-
Do you have the recovery password? These 48 numeric digits have now become important to you. They might be in some of the following places:
-
Stored in Active Directory
-
Stored in a text file in a folder specified during the BitLocker Setup wizard
-
Stored in physical, paper file or binder, as the page printed during the BitLocker Setup wizard
-
Carried in your wallet, purse, or briefcase: if you ensure it is separate from your computer.
-
Chances are that if you are part of an enterprise deployment, either the recovery key or recovery password will be stored centrally and managed through the company's help desk or similar organization. If you are reading this book, you might well be one of the administrators responsible for setting up that central system.
Let's take a closer look at some possible recovery scenarios that could occur in the real world.
Recovery Example 1: Desktop Hardware Failure (Stand-Alone System without a TPM)
Alice is self-employed and depends every day on her desktop computer. It's an older model, so it doesn't have a Vista-compatible TPM. Alice has upgraded to Windows Vista Ultimate Edition, and because she works with clients that store confidential information, she has encrypted her disk with BitLocker, configured to use a USB startup key.
One afternoon, Alice is shocked to find that her display is acting oddly. By the end of the day, it is no longer showing her any information. It is unusable. Alice eyes the computer belonging to her husband, Bob, and decides he won't mind if she puts her drive into his computer long enough to get this urgent proposal finished. (Since they bought their two computers together, they happen to be identical models-which makes this scenario oh so much easier to write.)
When she starts Bob's computer with her disk, she is prompted with a BitLocker screen, prompting her to insert her key media. Alice inserts her USB startup key, and restarts the computer. At startup, BitLocker finds the correct startup key for the disk, located on Alice's USB flash drive, and unlocks the hard disk. Alice finishes her proposal and lands a lucrative contract.
Recovery Example 2: Laptop Hardware Failure (TPM-based)
Alice's contract is so lucrative, and both computers are so old, that Alice and Bob decide to head out to buy new computers. Bob selects a top-of-the-line laptop, complete with a TPM 1.2 chip and a TCG-compatible BIOS. Bob configures his laptop to use BitLocker in the default TPM-only mode, and relies on a strong Windows password to guard access to his computer.
| Note | Any truly overboard geeks who want to know what things happen to Alice and Bob when they go out together can visit http://www.rogers.phy.bris.ac.uk/denzil/denweb4.html. |
Bob spends several weeks using his new laptop; then one day, it just totally dies. Bob rushes back to the vendor, and learns that a manufacturing defect has taken out his mainboard. The board is replaced in record time, and Bob leaves happy…except that when he starts his computer, he receives the following BitLocker prompt:
Windows BitLocker Drive Encryption key needed. Insert key Storage media. Press ESC to reboot after the media is in place. Drive Label: BHYNES-VISTABDE OS 10/1/2006 Key Filename: .BEK ENTER=Recovery ESC=Reboot
Bob realizes that since his TPM was a permanent part of his old mainboard, there is no way to unseal the VMK that was protected by the TPM.
Bob is a bit obsessive, so when he configured BitLocker, he saved a recovery password to a file, he printed a copy, and he also created a USB recovery key. Since the USB recovery key is in his locked filing cabinet, he retrieves it, inserts it into the USB port on his laptop, and restarts the computer. Bob is thrilled to see how easily BitLocker recovery works and returns the USB key to the filing cabinet.
The next morning, however, Bob is surprised to see the save prompt return again. Each time he restarts his computer, he has to perform the same recovery steps. Since Bob is a clever fellow, he surmises that his BitLocker keys have not been sealed by this new TPM.
Since Bob doesn't really want to invest the time to decrypt and re-encrypt his drive, he remembers a clever thing he learned by reading ahead in this chapter to the section on the command-line interface, so he launches an elevated command prompt and types:
manage-bde.wsf -protectors -delete -type tpm c: manage-bde.wsf -protectors -add -tpm c:
It only takes an instant to create the new key protector. After that, BitLocker reliably unlocks his encrypted disk, based on the integrity check performed by the new TPM.
Recovery Example 3: Lost USB Key (Computer with a TPM)
Bob's sister Carol works for a multinational corporation that manufactures shoelaces. Carol has a domain-joined laptop computer that-in the face of stiff competition from Velcro, zippers, and the whole sandals-with-socks movement-has been configured to use BitLocker with a TPM and a USB startup key. Upon arriving at her destination, the she turns on her laptop, and is greeted with the request for storage media, similar to this:
Windows Bitlocker Drive Encryption key needed. Insert key storage media. Press ESC to reboot after the media is in place. Drive Label: BHynes-VISTABDE OS 10/1/2006 Key Filename: . BEK ENTER=Recovery ESC=Reboot
The USB media must be present during the early stage of startup to be used; if you insert the media after the boot manager code has begun, you need to restart the computer. Carol suddenly realizes that the last time she started the computer (with her USB key) was while waiting for her flight in the airport waiting lounge. A sinking feeling hits her as she remembers the USB key sitting on the chair beside her in the lounge. A thorough check of bags and pockets indicates it has been left behind.
Since there is no practical way to recover the missing USB key in any reasonable amount of time, Carol knows that she must use BitLocker recovery, and presses the Enter key.
When this particular drive was encrypted, Carol did not save a recovery key to a USB drive (although she did use a TPM+USB protector), so the USB recovery password entry screen immediately appears, and looks like this:
Windows Bitlocker Drive Encryption password Entry Enter the recovery password for this drive. ----- ----- ----- ----- ----- ----- ----- ----- Drive Label: BHYNES-VISTABDE OS 10/1/2006 Password ID: 107241EE-A2F1-4553-978C-BC758F24D95 Use the function keys F1 - F9 for the digits 1 - 9. Use theF10 key for 0. Use the TAB, SHIFT-TAB, HOME, END and ARROW keys to move the cursor. The UP and DOWN ARROW keys may be used to modify already entered digits. Enter=Continue ESC=Exit
Carol seems to recall that she printed out a page when she encrypted her disk, but that was a long time ago. Not being sure of what else to do, she calls her company's help desk. A pleasant young engineer makes her verify her identity by confirming the last digit of her zip code and the date of her cat's last tetanus shot, and then reads her a string of 48 digits that he has retrieved from the company's AD DS database. He encourages her to type each block of six numbers as he reads them so that they can be checked for typos.
| Note | Ever wanted to know the mathematics behind checking for typographical errors, or why entry screens like this often use short blocks? Surf on over to http://www.blogs.msdn.com/si_team/archive/2006/08/10/694692.aspx. |
After Carol types her recovery password, her computer starts normally. So that she doesn't need to do this again, she has the hotel concierge fetch her a new USB drive, then uses the Manage BitLocker Keys option in the BitLocker section of the control panel (shown below) to create a new USB startup key, and then sends an e-mail to her vet because Fluffy needs a booster shot.
There are some other places where a recovery password can be stored. Notice that the recovery password entry screen shows a GUID for the password, called the Password ID. If you save a recovery password to a disk file, that Password ID is recorded in the file, and also used as the file name.
Recovery Example 4: "Found" Laptop
Alice's arch-rival, Eve, has been sneaking around, following Alice's friend, Dave. Dave is VP of research for a company that competes with Eve. Eve has been stalking Dave, hoping to steal his company's latest ideas. Eve sees Dave pop into a bar after a long day at an industry conference and follows him along. She strikes up a conversation, buys him a few beverages, and he becomes…um…distracted. When Dave is otherwise occupied, Eve slips his laptop into her own briefcase.
Later that night, Eve opens the cover of her long-sought prize, and gets ready to read up on the latest news. But when she powers up the Dave's computer, she is greeted with a prompt for a PIN. She tries Dave's birth date, and then his home phone number…after more random tries, she figures she can just spend all night trying 1111, then 1112, and so on…but she soon notices that the TPM's anti-hammering response makes this approach impossible.
Next she decides to just rip open the laptop and attach Dave's hard drive to another computer. But no matter which computer or which OS she tries, she can see only encrypted data. Finally, she puts the drive back in the original computer and chooses the recovery option. "Now we're talking" she thinks, and she calls Microsoft Product Support to have them help her "recover" her Vista installation. She is disappointed to learn that it doesn't quite work that way, and that even if she could ever succeed in convincing them to help, there is no way they can get her a key or decrypt the drive.
Recovery Summary
It's impossible to list all of the possible scenarios that might occur. Hopefully, from these examples you can extrapolate to similar situations.
If the disk ends up being unlocked by a recovery key stored on a USB drive, the process is the same as that used by a startup key without a TPM, shown previously in Figure 5.6.
On the other hand, if the user has entered the numerical recovery password (and it's correct) the recovery password is translated into the cryptographic keys required as shown in Figure 5.7. In this case, there are a couple of extra immediate keys, and a dash of salt. (In cryptographic terms, a salt is extra information added to increase the complexity of a key, usually to add entropy.)
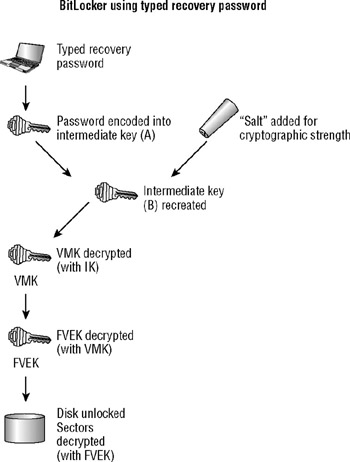
Figure 5.7: Using a recovery password
Recovery is not hard, provided you have a USB recovery key or a numeric recovery password. If you don't, there is no backdoor or secret way to get the information decrypted. So, as the administrators of systems, you need to prepare before disaster strikes. Here are some basic preparation tips:
-
If you have an Active Directory domain (Windows Server 2003 SP1 or newer), then store the recovery passwords in Active Directory. There is no reason not to do this. It provides an automatic solution, and this is discussed in the next section of this chapter.
-
If you do not have an Active Directory domain, but you are responsible for more than one computer, use WMI or the command-line tool to make backup copies of the recovery password, because you can do this remotely, or even in a startup script.
-
If you are responsible for your own computer: make more than one copy of a recovery key (a recovery password moved to a USB drive by the BitLocker setup wizard). You can make as many of these as you want, but keep two contradictory things in mind: you don't want these easily accessible by an attacker, but you do want to be able to get one if you need to. Perhaps keep one in the office safe or a locked desk drawer; or perhaps frequent travelers may leave one in their hotel room while the laptop is out with them in the taxi.
-
Use the BitLocker console to create additional recovery keys. Copying the text file with a recovery password to a USB drive is not enough to create the binary file needed to start the computer. Do not leave the recovery key with the computer.
-
Also make a copy of the recovery password and store it in an accessible place, but not with the computer. Note that "store" has some interesting possibilities: you could read it to yourself in your own password-protected voicemail. You could keep it in your wallet with your credit cards. The recovery password can be stored in a backup file in a local or on a network drive. Again, though, make sure it is separated from the computer.
You need to spend a bit of time thinking about recovery policies for your organization. We need to be clear: BitLocker does not randomly decide to go into recovery mode just to annoy a user. When BitLocker goes into recovery, it means a security incident has been detected. That may be simple incident as someone forgetting their PIN, or something more complicated, such as an attacker attempting to install a rootkit. Perhaps, though, the "right thing to do" is not to immediately use recovery and to continue as if nothing had happened. Consider policies and practices around determining the cause of BitLocker going into recovery mode, and the proper, safe way to protect that computer, the data it contains, and your network, as you recover that laptop.
EAN: 2147483647
Pages: 101