Using BitLocker without a TPM
Authentication or Access Control
BitLocker doesn't replace Authentication or Authorization (or Access Control).
In this default configuration, the TPM provides validation of the pre-OS boot process-and that can be very valuable-but the security of your systems absolutely depends on the security of the OS as well. You must configure user accounts, strong passwords, and NTFS permissions as appropriate. BitLocker does not replace any of those items.
For example, if a laptop is configured to automatically log on a particular user, BitLocker does not interfere with that process. When that user then leaves the laptop in a hotel bar, yes, the data is encrypted, but-big deal-as soon as someone turns the computer on, the automatic logon would just happen-with or without the authorized user's presence. What the default BitLocker configuration does do, however, is prevent an attacker from succeeding in bypassing the Windows Vista logon screen by removing the hard drive and attaching it to their own computer.
There is no doubt that the default configuration was the result of some security tradeoffs. Many users were simply unwilling to perform extra steps at startup; you will need to evaluate your environment, and determine if the default configuration meets your needs.
Increasing Security with Additional Key Protectors
In many cases, the protection offered by BitLocker in its default configuration will be a vast improvement, and is probably enough for most day-to-day routine business information. But in those cases where the information stored on a computer has a high value, or you just want to increase the security, then you can configure BitLocker to use key protectors that work with the TPM, but add a second layer or factor.
Because these two types of key protectors work with a TPM-and only with a TPM-sometimes they are called "TPM+" or "TPM plus" protectors. BitLocker gives you the option of using a PIN or USB-based cryptographic key (called a startup key) that is then required, in addition to the TPM, before the disk can be unlocked.
To be sure, this adds an extra step at startup and means that the system cannot start without the user providing the correct input or presenting the correct USB device. Some users will resist this and complain about the inconvenience. Others will actually embrace it, and be pleased to see the evidence that their confidential data is more protected.
Without a TPM or startup key, everything needed to decrypt the disk is stored on the disk, albeit protected by the TPM, and even the TPM is guaranteed to be with the computer. When you use a PIN or startup key, you are able to physically remove some of the required information, and make it impossible to start the computer when that information is not present. This is a form of two-factor authentication.
PINs
When configured to use a PIN, the Windows Vista boot manager interrupts the boot process and prompts the user to enter a PIN. The PIN can be from 4 to 20 digits long. This happens long before any Windows shell or graphical user interface is loaded, so the prompt looks something like this:
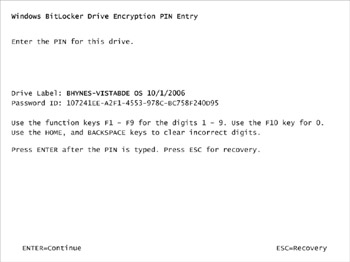
The PIN is not a password that can unlock the drive (or decrypt the VMK, and certainly not the FVEK), and it must have the TPM available as well. (This means that the PIN is not a recovery password.)
The TPM has a secured storage area used to hold authorization data (or "auth data," as you may sometimes see it called), and PINs are the primary use of this area. When a PIN is set, a version of the PIN is stored in the TPM's auth data. When the TPM is asked to unseal a key, it can compare the PIN being entered by the user to the information stored in the auth data storage. If they entries do not match, the keys are not unsealed, and the disk remains locked. The PIN is not stored on the disk (neither in the volume metadata, nor in a file under the control of the OS).
Because the PIN system is hardware based, it is well protected. The TPM specification includes an "anti-hammering" feature. If an attacker tries to guess the PIN by entering random or sequential numbers, the TPM will detect this and make it more and more time consuming to enter PINs.
Startup Keys
If you prefer to have a physical "key" required to be present each time the computer is started, you can use a startup key. A startup key is a cryptographic secret stored on a USB flash drive (also called a "USB key" or "USB stick"). It is important to note that the startup key-by itself-is not enough to unlock the disk. The TPM must still unseal keying information. (When BitLocker is configured to operate on a computer without a TPM, a startup key works differently. That kind of startup key is discussed a bit later in this chapter.)
In this configuration, it is not the VMK itself that is sealed and wrapped by the TPM. Instead, BitLocker encrypts the VMK with a new key (usually just called an "intermediate key" or IK) and writes that encrypted version to the volume metadata. The intermediate key is then made into two parts. One part is sealed and wrapped by the TPM. The other part is turned into a 256-bit structure and written in plaintext to the USB flash memory device. When the computer starts, the BitLocker code in the boot manager checks to see if the required startup key is present. If it is, BitLocker combines the key on the USB flash memory device with the key information unsealed by the VMK, and recreates the intermediate key. This intermediate key is then used to decrypt the VMK.
With the first release of Vista, you cannot use both a PIN and startup key, although that has been announced for Vista Service Pack 1. You cannot use a PIN unless your computer has a compatible TPM (see Figure 5.5).
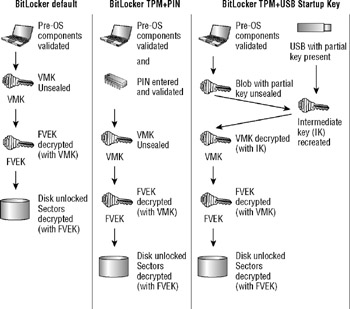
Figure 5.5: BitLocker TPM and TPM+ key protectors
The choices you make about PINs or startup keys will affect what your users need to do when a computer is started. You probably do not want to use either for computers that must restart automatically when a user is not present. While you could use a USB startup key and simply leave it in the USB port, that would rather defeat the purpose of using one, wouldn't it?
There are also a couple of obvious security considerations (well, they seem obvious to me, but somehow escape some end users): If you have a PIN, you should not tell it to other people or write it on a sticker on the laptop cover. If you are using a USB startup key, you should not store the USB key in the laptop bag, because, when you leave the laptop in the taxi, you'll leave the key with it. Maybe you should use that little loop and put your USB startup key on your keychain, and treat it like your other keys.
Boot Process Validation (Integrity Check)
Before we end our discussion of BitLocker and TPMs, it's time to delve a bit more into what "pre-OS component validation" is. The concept behind BitLocker is not just about encrypting data; in fact, the encryption was almost a means to an end. What BitLocker strives to deliver is a trusted computing experience, in which you can be assured that your computer is trustworthy, that it has not been compromised. This is a tough goal.
The TPM architecture includes 24 platform control registers (PCRs). Each PCR holds a specific measurement representing the state of a component of the system (or "platform"). Most of the measurements stored in the PCR are calculated with some form of hash. Table 5.1 shows what is measured by each PCR.
| PCR | Measurement |
|---|---|
| PCR 0* | Core Root of Trust Measurement (CRTM), which includes the BIOS and any platform extensions |
| PCR 1 | Platform and Motherboard Configuration and Data |
| PCR 2* | Option ROM Code |
| PCR 3 | Option ROM Configuration and Data |
| PCR 4* | Master Boot Record (MBR) Code |
| PCR 5 | Master Boot Record (MBR) Partition Table |
| PCR 6 | State Transition and Wake Events |
| PCR 7 | Computer Manufacturer Specific |
| PCR 8* | NTFS Boot Sector |
| PCR 9* | NTFS Boot Block |
| PCR 10* | Boot Manager |
| PCR 11* | BitLocker Access Control |
| PCRs 12–23 | Reserved for Future Use |
| The PCRs with * are those that BitLocker uses by default. | |
As the early startup process begins, the TPM first measures each component and stores the measurement in the appropriate PCR. In each case, the component is measured before control is given to that component. A component cannot change any earlier PCR value, so if an attacker inserted malicious code in the Boot Manager (PCR 10), that change would make the measurement stored in PCR 10 different from what it was before, and the malicious code could not change what was recorded as its measurement, or the earlier measurements, either.
The importance of this is easy to grasp: the OS can now reliably know if the components loaded before the OS have been changed. Changing one of these components could be a legitimate part of computer maintenance, but it could also indicate a concerted attempt to attack the OS, by installing a virus, spyware, or a rootkit, for example.
You can configure BitLocker to be more restrictive or less restrictive by telling it to examine a different set of PCRs; however this might not be what you really want. For example, you could configure BitLocker to include PCR, which would detect the addition of a PCMCIA card. For many laptop users, this would be too cumbersome, but perhaps in your situation, that's exactly what you want: to ensure no PCMCIA cards are added.
EAN: 2147483647
Pages: 101