Computer Architecture
A basic computer (system) architecture refers to the structure of a computer system and comprises hardware, firmware, and software.
Tip The CompTIA A+ certification exam covers computer architecture in depth and is an excellent way to prepare for this portion of the CISSP examination.
Hardware
Hardware consists of the physical components in a computer architecture. This broad definition of hardware can include keyboards, monitors, printers, and other peripherals. However, in this context, only concern yourself with the main components of the computer architecture itself, which include the CPU, memory, and bus.
CPU
The CPU (Central Processing Unit) or microprocessor is the electronic circuitry that performs a computer’s arithmetic, logic, and computing functions. As shown in Figure 9-1, the main components of a CPU include
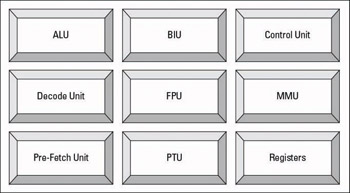
Figure 9-1: The main components of a CPU.
-
Arithmetic Logic Unit (ALU): Performs numerical calculations and comparative logic functions, such as ADD, SUBTRACT, DIVIDE, and MULTIPLY
-
Bus Interface Unit (BIU): Supervises data transfers over the bus system between the CPU and I/O devices
-
Control Unit: Coordinates activities of the other CPU components during program execution
-
Decode Unit: Converts incoming instructions into individual CPU commands
-
Floating Point Unit (FPU): Handles higher math operations for the ALU and control unit
-
Memory Management Unit (MMU): Handles addressing and cataloging of data stored in memory and translates logical addressing into physical addressing
-
Pre-Fetch Unit: Preloads instructions into CPU registers
-
Protection Test Unit (PTU): Monitors all CPU functions to ensure that they’re properly executed
-
Registers: Buffers used to temporarily hold CPU data, addresses, and instructions
The basic operation of a microprocessor consists of two distinct phases: fetch and execute (it’s not too different from what our dog does: we throw the stick, and he fetches the stick). During the fetch phase, the CPU locates and retrieves a required instruction from memory. During the execute phase, the CPU decodes and executes the instruction. These two phases comprise a basic machine cycle that’s controlled by the CPU clock signals. Many complex instructions require more than a single machine cycle to execute.
The four operating states for a computer (CPU) are
-
Operating (or run) state: The CPU executes an instruction or instructions.
-
Problem (or application) state: The CPU calculates a solution to an application-based problem. During this state, only a limited subset of instructions ( non-privileged instructions) is available.
-
Supervisory state: The CPU executes a privileged instruction: that is, available only to a system administrator or other authorized user/ process.
-
Wait state: The CPU hasn’t yet completed execution of an instruction and must extend the cycle.
The two basic types of CPU designs used in modern computer systems are
-
Complex-Instruction-Set-Computing (CISC): Can perform multiple operations per single instruction. Optimized for systems in which the fetch phase is the longest part of the instruction execution cycle.
-
Reduced-Instruction-Set-Computing (RISC): Uses fewer, simpler instructions than CISC architecture, requiring less clock cycles to execute. Optimized for systems in which the fetch and execute phases are approximately equal.
Microprocessors are also often described as scalar or superscalar (no, you can’t tell which they are by looking at them). A scalar processor executes a single instruction at a time. A superscalar processor can execute multiple instructions concurrently.
Finally, many systems (microprocessors) are classified according to additional functionality as follows (must be supported by the installed operating system):
-
Multitasking: Alternates execution of multiple subprograms or tasks on a single processor
-
Multiprogramming: Alternates execution of multiple programs on a single processor
-
Multiprocessing: Executes multiple programs on multiple processors simultaneously
Two related concepts are multistate and multiuser systems that, more correctly, refer to operating system capabilities:
-
Multistate: The operating system supports multiple operating states, such as single-user and multi-user modes in the UNIX/Linux world and Normal and Safe mode in the Windows world.
-
Multiuser: The operating system can differentiate between users. For example, it provides different shell environments, profiles, or privilege levels for each user.
An important security issue in multiuser systems is privileged accounts and programs or processes that run in a privileged state. Programs such as su
(UNIX/Linux) and RunAs (Windows) allow a user to switch to a different account, such as root or administrator, and execute privileged commands in this context. Many programs rely on privileged service accounts to function properly. Utilities such as Superzap (developed by IBM) are used to install fixes to the operating system or other applications.
Bus
The bus is a group of electronic conductors that interconnect the various components of the computer, transmitting signals, addresses, and data between these components. Bus structures are organized as follows:
-
Data bus: Transmits data between the CPU, memory, and peripheral devices
-
Address bus: Transmits addresses of data and instructions between the CPU and memory
-
Control bus: Transmits control information (device status) between the CPU and other devices
A computer bus is not painted yellow, nor does it have red flashing lights and a stop sign!
Memory
Memory is used to store programs, instructions, and data. The two basic types of physical (or real) memory are
-
Random Access Memory (RAM): Volatile memory (data is lost if power is removed) that can be directly addressed and stored data can be altered. RAM is typically implemented in a computer architecture as cache memory and primary memory. The two main types of RAM are
-
Dynamic RAM (DRAM) must be refreshed (contents rewritten) every two milliseconds because of capacitance decay. Refreshing is accomplished using multiple clock signals known as multiphase clock signals.
-
Static RAM (SRAM) is faster than DRAM and uses circuit latches to represent data; that is, it doesn’t need to be refreshed. Because SRAM doesn’t need to be refreshed, a single-phase clock signal is used.
-
-
Read-Only Memory (ROM): Nonvolatile memory (data is retained even if power is removed) that can be directly addressed but stored data can’t be easily altered. ROM is typically implemented in a computer architecture as firmware (as we discuss later in the section “Firmware”). Variations of ROM include
-
Erasable Programmable Read-Only Memory (EPROM)
-
Electrically Erasable Programmable Read-Only Memory (EEPROM)
-
Electrically Alterable Read-Only Memory (EAROM)
-
Programmable Logic Device (PLD)
-
Flash Memory
-
Secondary memory is a variation of these two basic types of physical memory. It provides dynamic storage on nonvolatile magnetic media, such as a hard drive or tape drive (considered sequential memory because data can’t be directly accessed - instead, you must search from the beginning of the tape media). Virtual memory (such as a paging file, swap space, or swap partition) is a type of secondary memory that uses both installed physical memory and available hard drive space to present a larger, apparent memory space to the CPU.
Two important security concepts associated with memory are the protection domain (or protected memory) and memory addressing.
A protection domain prevents other programs or processes from accessing and modifying the contents of address space that’s already been assigned to another active program or process. This protection can be performed by the operating system or implemented in hardware.
Memory space describes the amount of memory available in a computer system (for example, 256MB), whereas address space specifies where memory is located in a computer system (a memory address). Memory addressing describes the method used by the CPU to access the contents of memory. A physical memory address is a hard-coded address assigned to physically installed memory. It can only be accessed by the operating system that maps physical addresses to virtual addresses. A virtual (or symbolic) memory address is the address used by applications (and programmers) to specify a desired location in memory. Common virtual memory addressing modes include
-
Base addressing: An address used as the origin for calculating other addresses.
-
Absolute addressing: An address that identifies a location without reference to a base address - or it may be a base address itself.
-
Indexed addressing: Specifies an address relative to an index register. (If the index register changes, the resulting memory location changes.)
-
Indirect addressing: The specified address contains the address to the final desired location in memory.
-
Direct addressing: Specifies the address of the final desired memory location.
Remember Don’t confuse the concepts of virtual memory and virtual addressing. Virtual memory combines physical memory and hard drive space to create more apparent memory (or memory space). Virtual addressing is the method used by applications and programmers to specify a desired location in memory (address space).
Firmware
Firmware is a program or code that is stored in ROM memory. These types of programs are typically changed infrequently or not at all. A computer’s BIOS is a common example of firmware. Firmware is also found in devices such as digital cameras, DSL routers, and MP3 players.
Software
Cross-Reference Software includes the operating system and programs or applications that are installed on a computer system. We cover applications security in Chapter 7. The focus on software in this domain is the operating system.
The operating system (OS) controls a computer’s resources. The four main functions of the operating system are
-
Process management
-
I/O device management
-
Memory management
-
File management
EAN: 2147483647
Pages: 242