Lesson 1: Network Analysis and Network Monitor Tools
SMS Network Monitor is a robust and configurable tool for viewing network traffic and diagnosing network problems. The Network Monitor Control Tool compliments Network Monitor by watching network traffic and alerting you to potentially harmful events.
After this lesson, you will be able to
- Describe the various functions of Network Monitor, Experts, and Monitors.
Overview
Network Monitor is used to collect and view network frames (packets) as they traverse the network (Figure 7-1). After the packets are captured, copied, and stored, they are broken down into their separate protocol entities by modules known as protocol parsers. SMS includes approximately 100 different parsers. The protocol parser's job is to determine if the frame contains a particular protocol (for example, IP, NetBIOS or SMB) and to return properties about that protocol. These properties are then used to query for specific frames from the entire set of acquired frames. Network Monitor provides a full Application Programming Interface (API) set for controlling the capturing, querying, and displaying of frame information.
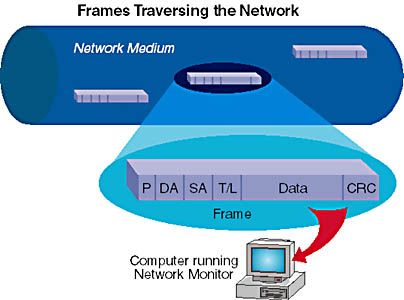
Figure 7-1. Network frames traversing the network.
Hardware and Software Requirements
Network Monitor runs on Windows NT version 4.0 with Service Pack 3 or later and Windows 2000. The Network Monitor Experts and Monitors require WBEM and IE 4.01 or later.
Network Monitor runs on common industry-standard PCs containing network interface cards. The network interface card on the computer running Network Monitor must support promiscuous mode to capture all network traffic on the local network segment. When a NIC runs in Promiscuous mode, it copies all packets that travel on its network segment into a storage location on the computer.
The LocalOnly bit supported in Windows NT 4.0 and later enables Network Monitor to acquire network traffic to and from the local computer using network adapters that do not support promiscuous mode. The LocalOnly feature does not allow the computer to monitor all network traffic on the local segment. To capture all local traffic the NIC must support promiscuous mode.
NOTE
To configure the LocalOnly bit in the registry, read Q152643.DOC in \CHAPT07\ARTICLES on the SMS Training Supplemental CD-ROM.
Dedicated Capture Mode
In a busy network, the computer running Network Monitor may drop frames. The Dedicated Capture Mode feature in Network Monitor frees resources on the computer for capturing data so that fewer frames are dropped. Figure 7-2 shows Network Monitor's console and dedicated capture mode. Dedicated capture mode is selected from the Capture menu - `Dedicated Capture Mode' option in the Network Monitor console.
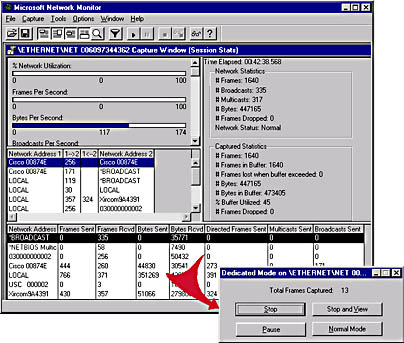
Figure 7-2. SMS Network Monitor console and the dedicated capture mode status box.
Using dedicated capture mode, capture statistics are not displayed or refreshed, as frames are copied to the capture buffer.
Remote Capture
The version of Network Monitor bundled with Windows NT Server version 4.0 supports capturing network traffic on a local network segment, but it does not support capturing network traffic on remote network segments. SMS Network Monitor allows for capturing network data on a computer remote to the Network Monitor console. The remote network monitor agent captures network traffic that is generated on segments that are remote or local to the management console. The version of Network Monitor bundled with SMS 2.0 includes the Network Monitoring Agent version 2 driver. This driver can be installed on a Windows NT version 4.0/2000 computer as part of a full installation of Network Monitor. This driver is also bundled with Windows 2000. Therefore, on Windows 2000, a full installation of Network Monitor isn't necessary in order to capture network traffic on remote segments.
NOTE
The NIC in the computer running the network monitor agent must support promiscuous mode to capture all traffic on the remote network segment.
Capture Filters and Triggers
By default, Network Monitor makes a copy of every frame it sees on the network. Capture Filters allow Network Monitor to capture specific frames based on computer address, protocol, and data patterns to be captured. Filtering out extraneous network traffic during the capture process reduces the possibility of missed packets and facilitates the quick analysis of captured data.
Network Monitor is configured with a capture trigger to monitor and respond to certain network events as soon as they are detected. A capture trigger is similar to an alert, but is designed to respond to certain events, such as a capture file reaching a specified size or a specific data pattern occurring in a captured frame. A capture trigger performs a specified action, such as starting an executable file when a capture trigger condition is detected.
Router and Address Discovery
Network Monitor can be configured to detect and display addresses of all SAP, Browser, RIPX, IP, OSPF, and RIP routers on the network. This allows an administrator to identify which network addresses are associated with routers on the network.
Identifying computers on the network can be difficult. For example, you may know the media access control address of a NIC, the protocol addressees configured on a computer, or the NetBIOS name of a computer; but all pieces of information may not be available at the same time. The `Resolve Address From Name' option allows you to collect all this information and display it in one place. After entering a NetBIOS name in the Resolve Address From Name dialog box, the addresses associated with the computer appear (Figure 7-3). Alternatively, the media access control address of a computer can be entered to obtain the computer's NetBIOS name.
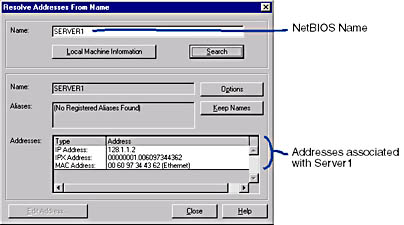
Figure 7-3. Resolving addresses for Server1 using Network Monitor.
NOTE
Because this address is a unique, 12-digit hexadecimal ID that identifies the manufacturer of the device and the device itself, no spaces are used when specifying a media access control address in the `Name' field.
Resolving a NetBIOS name given only an IP address is particularly useful in solving IP address conflicts. Such conflicts are commonly encountered in TCP/IP networks.
Network Monitors and Experts
Network Monitor is a mature network analysis tool that is available in earlier versions of SMS. New to Network Monitor in SMS 2.0 are network monitors and experts. Monitors are used during capture of network data, while experts are used to analyze network data after it has been captured. Monitors and experts require Windows NT version 4.0 or later running WBEM and Internet Explorer 4.01 or later.
Monitors are tools that watch the network for the occurrence of specific types of events. Monitors are configured from the Network Monitor Control Tool, as shown in Figure 7-4.
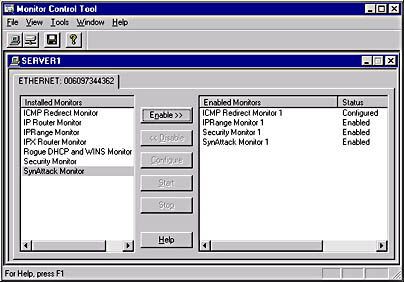
Figure 7-4. The Network Monitor Control Tool accessed from the Systems Management Server program group.
When an event occurs that Network Monitor has been configured to detect, an alert is generated. This allows the administrator to react to the event before it impacts normal network operation.
The monitors included with Network Monitor are:
- Rogue DHCP and WINS
- IPRange
- SynAttack
Detects any Dynamic Host Configuration Protocol (DHCP) server or Windows Internet Name Service (WINS) Server activity that is not from an authorized DHCP/WINS server. The administrator configures the Internet Protocol (IP) addresses of known DHCP/WINS servers, and if the monitor detects a DHCP/WINS server with an address outside the list of addresses, it generates an event.
Allows the administrator to configure a valid range of IP addresses for the network, and generates an event when an IP address outside the configured range appears on the network. This could be a signal that an intruder is attempting to gain access to intranet resources.
Monitors the network for SYN attacks, which have become prevalent as hackers attempt to shut down network servers. A SYN attack occurs when a hacker sends packets to a web server, often with bogus source addresses. These packets cause the server to allocate resources for connections that are not real, which affects server performance.
NOTE
For more information on SYN attacks, read Q142641.DOC, in \CHAPT07\ARTICLES on the SMS Training Supplemental CD-ROM.
- Security
- IPX Router and IP Router
- ICMP Redirect
Monitors the network for unauthorized users capturing data using Network Monitor.
Monitors the network for routers that fail. The IPX Router monitors routers running IPX/SPX and the IP Router monitors routers running TCP/IP.
Monitors the network for any routers redirecting ICMP network traffic. The Internet Control Message Protocol (ICMP) is an integral part of the TCP/IP suite, and is located in the Internet Layer. ICMP is responsible for packet control and status reporting. Part of its packet control function is to handle redirect messages sent from a router to a host. These redirect messages inform hosts to use a different router. If the monitor detects ICMP redirects, a network router may be experiencing trouble reaching a destination.
NOTE
For more information on ICMP redirects, read Q195686.DOC in \CHAPT07\ARTICLES of the SMS Training Supplemental CD-ROM.
Network Monitor Experts are used to analyze network traffic patterns after a capture file is created with Network Monitor. Experts are run from within Network Monitor, as shown in Figure 7-5. To run an expert, open a capture and choose the summary view (labeled 1 in Figure 7-5). Click Experts on the toolbar (2) or choose the `Experts' option from the Tools menu. When the Network Monitor Experts dialog box appears (3), choose an expert (4) and click Add to Run List (5). Click Run Experts (6) to run all experts listed in the 'Run List.'
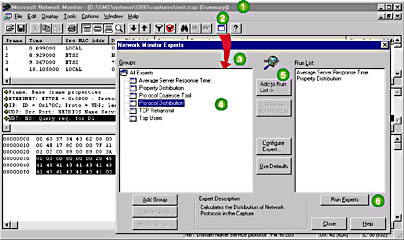
Figure 7-5. From the frame view in Network Monitor, experts are selected and run against captured data.
Each expert tells you something important about the network. The experts included in SMS 2.0 are:
- Average Server Response Time
- Property Distribution
- Protocol Coalesce Tool
- Protocol Distribution
- TCP Retransmit
- Top Users
Determines the average response time of the server in responding to requests during the capture session. The results window displays server addresses, average response time, and the number of computer resources interacting with the server during the capture.
Calculates statistics for specified protocol properties during a capture. For example, the expert can determine statistics for all frames that were Address Resolution Protocol (ARP) frames with a property of a specific operation code.
Combines data segments for a single transmission if they were fragmented into multiple frames. This expert creates a new capture file containing the coalesced data. This new capture file combines all frames of a single transaction into a single frame. The new coalesced capture file is opened in the Network Monitor console for analysis.
Determines which protocols (upper-layer or lower-layer) have generated the most traffic during the capture session.
Analyzes the traffic to determine if any Transmission Control Protocol (TCP) retransmissions have occurred. Retransmissions often indicate network congestion or physical connectivity problems in a TCP/IP network.
Determines which users generated or received the most network traffic in the capture. This is based on either percentage of total frames or bytes, or the total number of frames or bytes.
EAN: 2147483647
Pages: 107