Lesson 1: Attacks and Malicious Code
Lesson 1: Attacks and Malicious Code
Throughout this book you've learned about various types of attacks that can be conducted against your organization. This lesson adds to and organizes previous discussions of attacks. The main objective of this lesson is to bring all of these topics together to improve your understanding of the many different ways in which your network might be attacked.
After this lesson, you will be able to
-
Identify different network scanning methods to discover security weaknesses
-
Recognize and help to protect your organization from denial of service (DoS) and distributed denial of service (DDoS) attacks
-
Reduce the chance of successful password guessing attacks
-
Compare and contrast different types of malicious code
Estimated lesson time: 60 minutes
Scanning
Scanning might not always be considered an attack. Web search engines scan the Internet looking for pages to index. Some Internet users scan the Internet looking for publicly accessible resources, such as game servers. However, attackers also use scanning to identify potential targets for attack and to locate vulnerable resources. Scanning can provide attackers with the following information:
-
Network topology
-
Types of traffic allowed through the firewall
-
Active hosts on a network
-
Operating systems running on a target computer
-
Types of connectivity devices present on a network
-
Type of applications that are running on a network
-
Software version numbers and patch levels
-
Account information
Attackers also use vulnerability scanners that probe for specific exploits that could exist on any computer or connectivity device on the network. By collecting all of this information, an attacker can begin to craft a specific attack. When scanners are used for this purpose, the act of scanning is considered part of the attack. In the following section you learn about scanning utilities and different types of scans that can be used to find security holes on your network.
Laura Chappell provides a good overview of scanning techniques and consequences in her article "You're Being Watched: Cyber-Crime Scans," available at http://www.nwconnection.com/2001_03/cybercrime.
Scanners
As mentioned in Chapter 8, you should use vulnerability scanners on your own network to identify vulnerabilities and fix them before attackers can exploit them. There are many different network scanners that can be downloaded from the Web. These are some examples:
-
Advanced Administrative Tools from G-Lock Software.
-
Xprobe2 from Sys-Security Tools.
-
GFI LANguard Network Security Scanner.
-
Network Mapper (NMAP), a network scanning utility that runs on a wide variety of operating systems.
-
Computer Cops, which provides several different scanners, including a Web-based version of NMAP.
-
Foundstone offers several scanning tools, such as BOping, SuperScan, ScanLine, SNScan, and DDosping. Each tool includes a description of its scanning capabilities.
-
Nessus offers a free vulnerability scanner.
-
The Arirang CGI scanner is designed specifically to identify Common Gateway Interface (CGI) vulnerabilities.
-
Internet Security Scanner (ISS) and Security Administrator Tool for Analyzing Networks (SATAN).
-
Microsoft Baseline Security Analyzer (MBSA) and the Microsoft Network Security Hot Fix Checker (HFNetChk).
-
EtherPeek and AiroPeek are available from WildPackets Inc.
-
Sniffer software products are available at http://www.sniffer.com.
Once you've acquired the appropriate scanning tools, you can begin to check your network for vulnerabilities. The following sections discuss types of scanning that might be performed against resources on your network.
ARP Scanning
As discussed in earlier chapters, Address Resolution Protocol (ARP) addresses are used in all Internet Protocol (IP)-based communication between computers. ARP converts IP addresses into media access control (MAC) addresses so that network adapters can communicate with one another on a network. Attackers can use ARP to map out the number of active hosts on a network by sending ARP broadcast packets to all the possible address of a particular segment. By design, all active hosts must respond to the ARP broadcast with their MAC addresses. Although you would not want to prevent hosts from responding to ARP broadcasts, you could set your intrusion detection system (IDS) to trigger an alert if a particular host sends an excessive number of ARP broadcasts.
Figure 11-1 shows evidence of an ARP scan as captured by Microsoft's Network Monitor. In the figure, the local host is sending ARP scan, which you can see in the Source MAC Address column (Src MAC Addr). The scan proceeds sequentially from the local host through all possible addresses. If this were an actual attack, the attacker would be monitoring ARP replies to determine which hosts were active. An attacker might also use the discovered MAC addresses to spoof the MAC address on his or her computer to defeat MAC address filtering, which can be enabled on many types of switches and wireless access points.
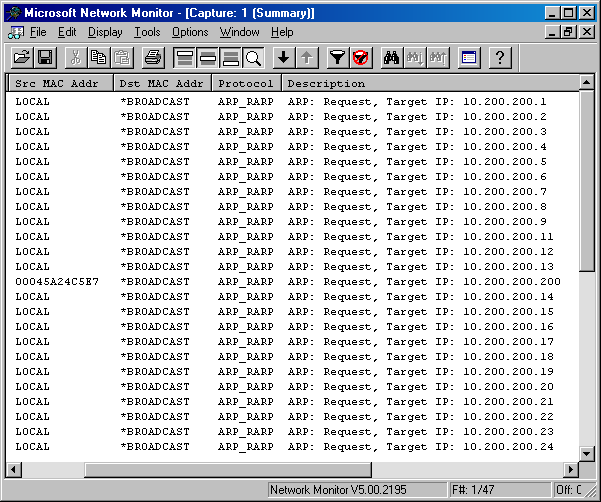
Figure 11-1. Evidence of an ARP scan
ICMP Scanning
Internet Control Message Protocol (ICMP) provides error and information messages for IP-based networks. ICMP scans, like ARP scans, can also be used to identify active hosts on the network. The following ICMP scans can be used to detect devices on your network:
- ICMP echo.
This type of scan is also known as a ping sweep or ping scan because the ping utility utilizes ICMP echo requests to locate hosts. Attackers looking for targets often attempt use a ping sweep to find hosts that respond to ICMP echo requests, which identifies them as active devices on the network. Request for Comments (RFC) 792 describes the ICMP echo request and reply. (RFC articles can be found at http://www.icann.rfceditor.org.) Figure 11-2 illustrates a ping sweep using the NMAP port scanner.
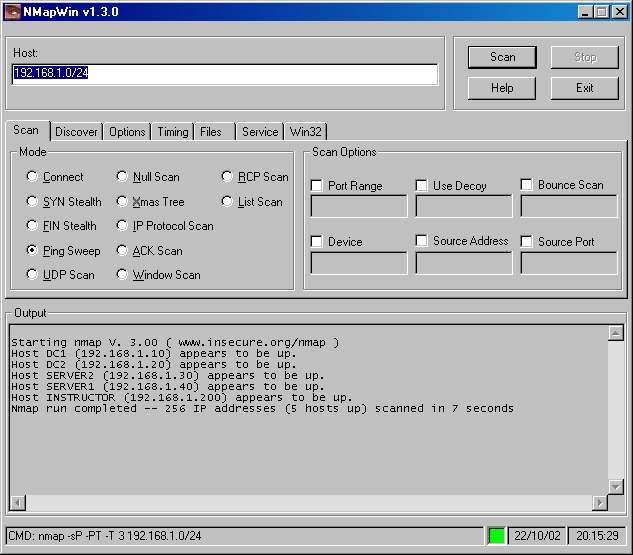
Figure 11-2. Ping sweep example
- ICMP router solicitation.
Often, routers are configured not to respond to ping sweeps, but another type of ICMP request can be used to locate routers on the network. Client systems use this to locate routers on the network, but so can attackers. ICMP router solicitation is described in RFC 1256.
- ICMP address mask scan.
Hosts that cannot determine the appropriate IP subnet mask for their subnet use the ICMP address mask request. This type of request is not typically used today because hosts are configured with their IP addresses and subnet masks locally or from Dynamic Host Configuration Protocol (DHCP) servers. However, because the functionality still exists within the IP version 4 (IPv4) protocol stack, attackers can try to utilize these messages to receive replies from active hosts on the segment. RFC 950 describes ICMP address mask request and reply messages.
UDP Scanning
Attackers use User Datagram Protocol (UDP) port scans to identify potentially exploitable services that a target is running. Exploitable services such as chargen, daytime, and echo (discussed in Chapter 8) run over UDP and could be discovered in such a scan. Figure 11-3 illustrates a UDP scan against a single target host using the NMAP port scanner.
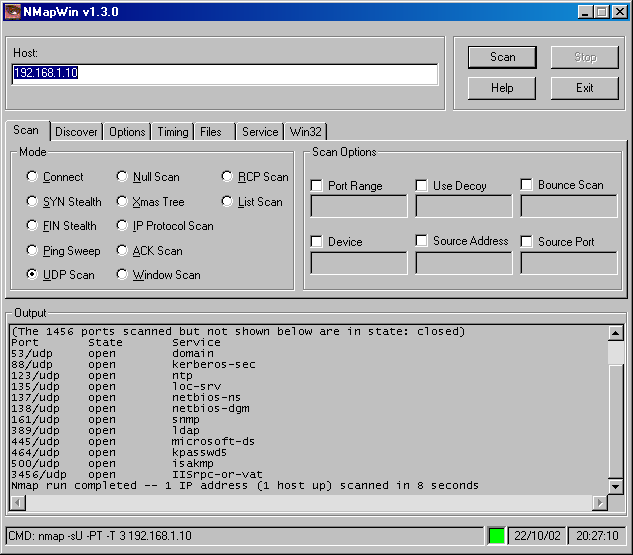
Figure 11-3. Example of a UDP scan
As you can see in the figure, the target of the scan, which is a Microsoft Windows 2000 Server computer, has 12 different UDP ports open. By examining these ports, a skilled attacker can determine many things about the target, including these:
-
UDP port 53 (domain) indicates that the target is a Domain Name System (DNS) server.
-
UDP port 161 is used for Simple Network Management Protocol (SNMP), a management service that the attacker could potentially exploit to find out even more information about the host and potentially the network.
-
UDP port 3456 is used for IISRPC, indicating that the server is running Internet Information Services (IIS) Remote Procedure Call (RPC). Based on this, the attacker could make a good guess that the system is likely a Microsoft operating system and might be running Web and File Transfer Protocol (FTP) services. The attacker could follow up by attempting exploits against all of these services and focused attacks for Microsoft systems.
-
UDP ports 88 for Kerberos, 123 for Network Time Protocol (NTP), 389 for Lightweight Directory Access Protocol (LDAP), and 464 for Kerberos passwords (kpass) are indications that the target is probably an Active Directory domain controller.
-
UDP ports 137 and 138 are used for Network Basic Input/Output Service (NetBIOS). UDP 445 is used for Server Message Block (SMB) over TCP/IP. The presence of these ports and services is indicative of a server that is enabled for Microsoft networking.
Attackers might be able to use UDP ports 137 and 138 to conduct NetBIOS enumeration, which allows them to list users, groups, shares, and other resources available on such servers. The NetBIOS enumeration (NBTEnum) utility written by NTSleuth helps to exploit NetBIOS services. Microsoft has implemented additional security features in its latest products to better protect systems from such exploits. To prevent NetBIOS enumeration from external networks, close these ports on your firewall. To reduce the exploitation of NetBIOS enumeration of Microsoft systems on internal networks, disable file and printer sharing and increase the RestrictAnonymous value in the Windows registry. See Microsoft Knowledge Base Article Q246261, "How to Use the RestrictAnonymous Registry Value in Windows 2000."
The results of this UDP scan tell the attacker a lot and present several avenues for attack. If you are a security administrator and you see such results, you should first seek to remove or disable all unnecessary services. Once all unnecessary services are removed or disabled, ensure that the latest security updates have been applied.
TCP Scanning
Attackers use Transmission Control Protocol (TCP) scans to identify active hosts and connectivity devices on the network. Like UDP scans, TCP scans also identify potentially exploitable services on the network. As described in Chapter 2, TCP uses a three-way handshake process to create a connection between client and server. Once the connection is created, TCP maintains the connection until it is terminated by either host. TCP scans can exploit the connection-oriented behavior of TCP. The following sections describe different TCP scans that can be used to identify active hosts and services on a target system or network.
Connect
TCP connect scans (also called vanilla TCP connect scans) are used to identify potential targets and services. This type of scan utilizes the full TCP three-way handshake. The attacker sends a TCP connection request with synchronize (SYN) segment and awaits a synchronize-acknowledgment (SYN-ACK) or reset (RST) response from the target host. If the target's TCP port is closed, the response is RST. If the target's TCP port is open, then a SYN-ACK is returned. If the attacker receives a SYN-ACK, the attacker knows the service is available. The attacker then sends the final ACK segment to complete the TCP handshake. Although most IDS implementations can detect TCP connect scans, successful connections are less likely to be identified as suspicious. However, if many connections are made sequentially, in a short period of time, or from a single host, these connections could trigger an IDS alarm. Many attackers know this and consequently spread their scans over a day, a week, or an even longer period of time. Sometimes the only way to identify a scan is to look historically at all the ports a particular host has attempted to contact. Of course, a savvy attacker would try to bounce scans off different hosts or use spoofed addresses to make identifying and tracking the scan much more difficult.
FTP bouncing was discussed in Chapter 8. FTP bounce is a method that attackers use to protect their identity when scanning your network, by bouncing the scan off a vulnerable FTP server.
Half-Open
Half-open scans (also called SYN or SYN stealth scans) achieve the same goal as TCP connect scans: identifying potential targets and listening TCP services. However, the half-open scan is not as "polite" as the connect scan because the scanning device or attacker never sends the final ACK packet. This leaves the target of the scan with several TCP ports in a half-open state, hence the name of this type of scan. Half-open scans reduce the amount of time the attacker has to wait to get scan results, because the scanning tool doesn't need to send the final ACK packet. The net effect is that the target service in this case waits for an ACK response, but eventually gives up and expires (times out) the connection request.
Half-open TCP ports are also symptoms of a SYN flood or SYN-ACK attack. SYN floods are classified as DoS attacks because their objective is to stop the server from responding to legitimate client requests. During a SYN flood, the attacker attempts to send TCP connection request packets to a specific TCP port or ports faster than the target server can expire them. A SYN flood consumes all of the server's available TCP connection resources so that it is unable to service new client requests. One way to reduce the effects of such an attack is to reduce the time that a TCP port waits for an ACK response.
For more information on SYN attacks, review CERT Advisory CA-1996-21, "TCP SYN Flooding and IP Spoofing Attacks," available at http://www.cert.org/advisories/CA-1996-21.html.
FIN
When a basic firewall or router blocks other TCP scans, the TCP FIN scan might succeed. The FIN scan, like other TCP scans, is used to identify listening TCP ports based on a response, or lack of a response, to a finish (FIN) packet. Attackers send the TCP FIN packet to the target host, even though they haven't previously made any connections to the target. If the target responds with an RST packet, the TCP port solicited is closed. If the target has an open TCP port, it discards the packet and doesn't respond. No response is an indication of an open port (or at least a potentially open port), so an attacker can then follow up with other scans, connection attempts, or attempts to exploit services on the target system.
XMAS
Another derivative TCP scan designed to bypass basic firewalls or routers with filtering capabilities is the XMAS scan (also called a Xmas tree scans). This scan uses a series of varied TCP packets to identify listening TCP ports on target devices. Some characteristics of XMAS scan packets include TCP sequence numbers of zero, and FIN, urgent (URG), or push (PSH) flags set. Target devices send a TCP RST packet if their ports are closed. Target devices discard XMAS packets and provide no response when the TCP port is open.
A derivative of the XMAS scan, known as a Full-XMAS scan, sends packets with all TCP flags set (FIN, URG, PSH, ACK, RST, and SYN).
NULL
Yet another TCP scan designed to penetrate firewalls and filtering routers is the TCP NULL scan. A NULL scan is similar to the XMAS scan in that TCP sequence numbers are zero, but the NULL scan passes no flags at all. As with the XMAS and FIN scans, if a port is closed, the target sends an RST packet. If the port is open, the target discards the packet without a response.
ACK
TCP ACK scans are often used instead of ping sweeps to identify active hosts on the network. If an RST packet is returned, the client port is unfiltered by a firewall and might even have a service available on that port. If no response is returned, or the response returned is an ICMP destination unreachable message, then the port is probably filtered by a firewall.
A derivative of the ACK scan called the Window scan identifies active hosts on the network and tries to further identify the host operating system or device manufacturer by its default TCP window size.
Fragmentation
Fragmentation, described in Chapter 2, is the process of dividing one large packet into two or more smaller packets. This is legitimately done to send packets from a network that supports large packet sizes to a network that supports smaller packet sizes. For example, fragmentation is commonly used between Token Ring networks and Ethernet networks because Ethernet networks typically support a maximum packet size of just over 1500 bytes, whereas Token Ring networks support packet sizes of 4500 bytes or more.
Attackers might try to use fragmentation to allow SYN, FIN, XMAS, or NULL scans to bypass a filtering firewall, router, or IDS. In this case, the purpose of fragmentation is to hide the true intention of the packets traveling into the network. If the router or firewall doesn't reject fragments or doesn't reassemble the fragmented packets, it cannot protect hosts on the other side of the device from being scanned.
DoS/DDoS
DoS and DDoS attacks were first introduced in Chapter 1, and they are mentioned throughout the book. As you know, DoS and DDoS attacks seek to disrupt normal operations. Essentially, a DoS attack is any attack that consumes or disables resources in an attempt to hinder or disrupt some operation or function. Some DoS attacks target specific software flaws and others attempt to consume resources so that legitimate users cannot utilize a service.
DDoS attacks are DoS attacks conducted simultaneously from multiple computers. DDoS attacks are often conducted using other compromised computers running zombie software, which is any software under the remote command of an attacker. A computer running zombie software is known as a zombie or zombie host. Zombies are often computers that don't belong to the attacker, but instead are computers that the attacker was able to compromise. The actual owner of the computer often does not know that his or her system is running zombie software and attacking other computers.
Trinoo and Tribe Flood Network (TFN) are two DDoS tools that attackers can use to take over client computers and make them zombie hosts. You can learn more about these tools from the CERT article "Distributed Denial of Service Tools," available at http://www.cert.org/incident_notes/IN-99-07.html.
Spoofing
Spoofing attacks are discussed throughout this book. As you know, spoofing is pretending to be someone else by impersonating, masquerading, or mimicking that person. Here are some of the forms of spoofing discussed in this book:
-
IP address spoofing is forging the IP source address in one or more IP packets to show that the packet came from a source other than the true source of the packet.
-
ARP cache poisoning or spoofing is a method for placing incorrect information in computers' ARP caches to misroute packets.
-
RIP spoofing uses the Routing Information Protocol (RIP) to update routing tables with bogus information.
There are other forms of spoofing as well. For example, Web spoofing occurs when an attacker sets up a Web page or Web site that looks like a legitimate Web site. The attacker then attempts to redirect other systems to this location in an attempt to steal passwords, credit cards, or other potentially valuable information. In the following sections, you'll see how spoofing is used in several different types of DoS attacks.
DoS Examples
There are two basic types of DoS attacks: those that attack a specific software flaw, called flaw exploitation attacks, and those that seek to consume resources, called flooding attacks. You've already seen an example of each type of attack in this book. An example flaw exploitation attack is the echo and chargen attack described in Chapter 8, which places those services in continuous loops. The SYN flood attack, mentioned earlier in this chapter, is an example of a flooding attack. There are several well-known types of DoS attacks that can help to further your understanding. The following list describes several examples of both types of DoS attacks:
-
The ping of death (POD) is a flaw exploitation attack in which the attacker sends an ICMP echo request that is larger than 65,536 bytes to a target. Of course, the attacker cannot send a single oversized packet to a remote location because it wouldn't be routable or legal on the network. The attacker fragments the oversized packet into smaller packets. Several vendor implementations of the IP protocol stack were not originally designed to handle oversized packets. Some targets of POD attacks would become unresponsive, crash, or restart. All major software and network equipment vendors have since updated their IP protocol stacks so that they are not vulnerable to POD attacks. Alternate names and derivatives of the POD attack include long ICMP, jolt, sPING, ICMP bug, and IceNewk. For more information on POD, see CERT Advisory CA-1996-26, "Denial-of-Service Attack via Ping," available at http://www.cert.org/advisories/CA-1996-26.html.
-
Teardrop (also called a fragmentation attack) is a flaw exploitation attack that involves two or more IP fragments that cannot be properly assembled due to improperly configured fragment offset numbers. Some targets of the teardrop attack would become unresponsive, crash, or restart. All major software and network equipment vendors have since updated their IP protocol stacks so that they are not vulnerable to teardrop attacks. Alternate names or derivatives of the teardrop attack include targa, SYNdrop, Boink, Nestea Bonk, TearDrop2, and NewTear. For more information on teardrop, see CERT Advisory CA-1997-28, "IP Denial-of-Service Attacks," available at http://www.cert.org/advisories/CA-1997-28.html.
-
Land is a flaw exploitation attack in which an attacker sends a forged packet with the same destination and source address and port. Some targets of the land attack would become unresponsive, crash, or restart. All major software and network equipment vendors have since updated their IP protocol stacks so that they are not vulnerable to land attacks. For more information on land attacks, see CERT Advisory CA-1997-28, "IP Denial-of-Service Attacks," available at http://www.cert.org/advisories/CA-1997-28.html.
-
ICMP flood is a DoS attack that attempts to overwhelm the target with ICMP packets so that it cannot service them, making it unresponsive. This can be done as a DDoS attack using multiple zombie hosts or by spoofing the source address of an ICMP echo request packet, as discussed later.
-
UDP flood is very much like an ICMP flood, except that the protocol attacked is UDP. The attacker sends a large number of UDP packets to random ports on the target. The target responds with RST packets or ACK packets, depending on whether a service is configured for the particular port. If an attacker is able to send enough of these packets, the target system could become unresponsive, crash, or reboot. This can be done as a DDoS attack using multiple zombie hosts or by spoofing the source address of a UDP service request packet, as discussed later. For more information on UDP floods, see CERT Advisory CA-1996-01, "UDP Port Denial-of-Service Attack," available at http://www.cert.org/advisories/CA-1996-01.html.
-
Smurf is a specific type of ICMP flood attack that involves sending spoofed ICMP echo packets. In this attack, the attacker spoofs the IP address of the target in an ICMP echo request packet to the broadcast address of a segment where the target is a zombie network on the Internet. For example, if the target is 192.168.1.1 on segment 192.168.1.0, the attacker would send an ICMP echo request with the forged source address 192.168.1.1 to a destination address 192.168.1.255, which is the broadcast address for the segment on which the host is located. Every system on that segment then replies to the target with an ICMP echo reply message. If the attacker sends enough of these packets, the target could be overwhelmed by ICMP echo replies and become unresponsive. For more information on smurf attacks, see CERT Advisory CA-1998-01, "Smurf IP Denial-of-Service Attacks," available at http://www.cert.org/advisories/CA-1998-01.html and the Smurf FAQ at http://www.iops.org/Documents/smurf-faq.html.
-
A fraggle is a variation of the smurf attack that uses UDP service request packets instead of ICMP packets. The details and method of the attack are identical, except that the UDP protocol and UDP echo packets are used.
Protection
Protecting systems from DoS flaw exploitation attacks usually involves applying a security update to the system or removing the attacked service. Protecting systems from DoS and DDoS floods is not as simple because the functionality exploited is not a flaw. However, firewalls and filtering routers can sometimes be used to help prevent certain DoS attacks. Here are three basic firewall and router measures that can be used to mitigate the effects of a DoS attack:
- Egress filtering.
Place a filter on outgoing traffic to prevent internal subnet addresses from being spoofed. If a packet coming from a specific internal subnet doesn't have a source address from that subnet, have the firewall or router drop the packet. This prevents resources from your organization from being used to attack resources on other internal subnets or even resources that belong to other organizations outside of your network.
- Ingress filtering.
Packets from external sources with IP source addresses from internal subnets are usually DoS attacks. Configure your routers to drop all incoming packets with source addresses of internal systems or private IP address sources (as defined in RFC 1918).
- Disable IP-directed broadcasts.
As you read earlier, smurf attacks use a ping to the broadcast address of an IP subnet. Routers should be configured to drop such packets and not respond to these requests.

IDS software, covered in the next lesson, also helps to alert you to and might even automatically respond to a DoS attack. Some software vendors have created anti-DoS tools that might also help to protect your network from DoS attacks. Here are some examples:
-
Asta Networks' Vantage Systems
-
Arbor Networks' Peakflow
-
Captus Networks' CaptIO
-
Top Layer's AppSafe
In addition to configuring filters and adding software to help protect against DoS attacks, you should develop an understanding with your Internet service provider (ISP). If all of your efforts to prevent a DoS attack fail, you can then get help from your ISP to reduce the effects of a DoS attack. The ISP's help is useful when external attacks are inbound or when you discover that your internal clients are compromised and attacking resources of other organizations. Of course, your ISP can't help you if your internal hosts and subnets are under attack from one another (using only the internal network).
When it comes to DoS attacks that rely on half-open ports, such as SYN floods, reducing the amount of time that a port waits for an ACK helps to reduce or prevent that type of attack. For more information on what you can do to reduce or prevent DoS attacks, see "Managing the Threat of Denial-of-Service Attacks," available from CERT at http://www.cert.org/archive/pdf/Managing_DoS.pdf.
Source Routing


Man-in-the-Middle
In Chapter 1 and Chapter 2, you learned that man-in-the-middle attacks occur when an attacker successfully inserts an intermediary system between two communicating hosts. This allows the attacker to listen to and possibly modify communications passing between the two systems. There are several different tools that an attacker can utilize to conduct a man-in-the-middle attack, including the following:
- SMBRelay.
Mentioned in Chapter 8, the SMBRelay tool is used between two SMB hosts (typically Microsoft or Microsoft-compatible networking systems). Windows 2000 and later Microsoft operating systems allow for SMB signing, which helps to thwart man-in-the-middle attempts.
- SSHmitm.
SSHmitm is part of the dsniff toolkit (mentioned in Chapter 4, Chapter 6, and Chapter 8). SSHmitm exploits Secure Shell (SSH) version 1 traffic by acting as a proxy between SSH sessions. This tool can capture information and encrypted logins. To prevent this exploit, use SSH version 2. See CERT Vulnerability Note VU#684820 at http://www.kb.cert.org/vuls/id/684820 for more information.
- webmitm.
webmitm is also part of the dsniff toolkit. This tool proxies Hypertext Transfer Protocol (HTTP) version 1.0 and Secure HTTP (HTTPS) communications and captures information and encrypted logins. To prevent this exploit, use HTTP version 1.1 compatible Web clients and servers.
Back Door
A back door is a program or account that allows security measures to be circumvented. At one time, back doors were common in many products because vendors installed them to make supporting clients easier. Of course, once attackers discovered them, attacking that equipment or software was also easier. In addition to finding pre-established back doors, many attackers can create or obtain back door software that helps them exploit systems.
For instance, Trojan horse programs might be used as back doors. An example of this is a program called Apher Trojan, which was advertised as a virus scanner update to several victims. Instead, the Apher Trojan installed Backdoor.Death.25, a back door program that allows an attacker to remotely control the victim's computer.
A root kit is a type of back door that is used to give root access to UNIX and Linux computers. The "root" user is the unrestricted account for managing all aspects of the system. There are root kit programs for other operating systems as well, even though these operating systems call their unrestricted user account something else, such as administrator or superuser. Root kits often replace multiple programs on their target operating systems so that attackers can access and remotely control the target easily through several different services. Some files are also used to repair each other. In this way, if the victim discovers one of the replaced files and deletes it, the other root kit files on the system can re-create or repair the deleted file. Most antivirus scanners are able to detect back doors and root kits.
You can learn more about back doors and root kits from any major software vendor that has virus-scanning products. Symantec, McAfee, and Panda Security all maintain virus lists that you can search. For example, a search on Symantec's virus encyclopedia for "back door" yields 576 results. Other well-known back door programs include NetBus, SubSeven, and BackOrifice.
Password Guessing
Password guessing attacks are discussed throughout this book. Chapter 1 introduced the concept of dictionary attacks, in which a password-guessing or password-cracking program uses a preexisting list of words to try to guess a password. Originally, dictionary attacks were limited to words found in a dictionary, but they have since evolved to include names, numbers, and special characters. Further, modern dictionary attacks are not limited to any type of character set or combination. For example, a user named Sharon might decide that $haRon54 is a good password because it includes a dollar sign, an uppercase letter, and two numbers. However, a dictionary attack might discover such a password quite easily because the substitution of $ for S is so common that dictionary scanners often include this feature. Further, the numbers in this password are likely Sharon's birth year without the leading two digits (presumably 19). Here again a dictionary attack would likely add two- and four-digit years to the end of common names.
Where the dictionary attack fails, the brute force attack usually succeeds. A brute force attack goes beyond using a substitution list by running different combinations of characters until they compromise the password using mathematical algorithms. Cracking a complex password (described in Chapter 4) can take a long time, possibly as long as many years. However, the amount of time that it takes depends on how many systems are attempting to crack the password. If an attacker is able to compromise 20,000 host computers to try different password combinations, the time it might normally take could be reduced to minutes.
Crack, John The Ripper, passwd, and other password-checking tools for UNIX systems are available from ftp://coast.cs.purdue.edu/pub/tools/unix/pwdutils. The L0phtcrack password-checking tool for Windows is available from @stake at http://www.atstake.com.
Password guessing is made much more difficult when system administrators use secure password policies (as described in Chapter 4 and again in Chapter 10). If the attacker is only allowed to take three guesses per hour, and the password is complex, there is a greatly reduced chance the password can be cracked. This is especially true if there is a system administrator or IDS watching for password threshold violations. The password policy might even specify that the account be locked out after a certain number of incorrect guesses within a specific time span. This makes online guessing of complex passwords virtually impossible. In such a case the attacker might attempt to capture a packet exchange that includes a password hash being passed across the network. The attacker could then attempt to decode the password offline.
If an attacker attempts to guess the password for a user account that is used for a service (such as an account that is used to automatically back up servers), a password guessing attack could become a DoS attack. If the service account is locked out, then the service cannot perform its job. The same principal could be applied to all user accounts. If an attacker obtained a list of user accounts and then attempted to log on incorrectly to each account multiple times, each user could be prevented from logging on for a certain period of time. Administrators must monitor account lockout activity to mitigate the effect of such attacks.
Another way to thwart password guessing is to simply not use passwords. For example, many organizations implement smart cards to increase security. These credit-card-sized access cards contain a computer chip that stores a digital certificate. This digital certificate is used to grant access to a system or network. Smart cards typically require an additional form of security such as a personal identification number (PIN) or biometric identifier. This reduces the chance that an unauthorized individual could use the card if it is lost or stolen. For example, when the user inserts the smart card into the reader, he or she must enter a PIN, provide a thumbprint, or have a retinal scan performed before accessing the network. If a smart card is lost or stolen, the security administrator can revoke the certificate as soon as he or she is aware of the loss.
Replay Attack
Replay attacks involve listening to and repeating data passed on the network. An attacker tries to capture packets containing passwords or digital signatures as they pass between two hosts on the network using a protocol analyzer. The attacker then filters the data and extracts the portion of the packet that contains the password, encryption key, or digital signature. Later, the attacker resends (replays) that information in an attempt to gain access to a secured resource.
An actual replay attack is more difficult than just capturing and repeating information. The attacker must accurately predict or guess TCP sequence numbers to make this work. However, it is possible for an attacker to guess correctly or use a script or utility that automatically makes guesses until the correct sequence is determined.
The following is a list of reported replay vulnerabilities that might help to further your understanding of these attacks:
- Compromise SSH passwords.
The CERT vulnerability note (VU#565052) titled "Passwords Sent Via SSH Encrypted with RC4 Can Be Easily Cracked" describes how SSH sessions can be replayed (http://www.kb.cert.org/vuls/id/565052). The actual solution to this problem is not to use the weak RC4 encryption algorithm, which is discussed in the next section.
- Compromise Web sessions.
Attackers who are able to capture packets between Web clients and servers using nonencrypted session identifiers or unsecured cookies are vulnerable to replay attacks. This is further described on the Open Web Application Security Project (OWASP) Web site at http://www.owasp.org/asac/auth-session/replay.shtml.
- Compromise SMB authentication.
CVE-1999-0391, available at http://icat.nist.gov, describes how SMB authentication packets from Microsoft Windows 95 and Microsoft Windows 98 can be reused, which could allow an attacker to gain access to a system.
- Compromise virtual private network (VPN) connections.
The Internet Security Systems report titled "vpn-replay-attack (7870)" describes a VPN exploit for UNIX and Linux systems, available at http://www.iss.net/security_center/static/7870.php.
To protect yourself and your organization's network from replay attacks, ensure that the latest security updates are applied to your existing software. Use the latest and most secure encryption techniques for all connections that involve authentication. For example, IPSec (covered in Chapter 5, "Communications Security") can provide antireplay services through the Authentication Header (AH) or Encapsulating Security Payload (ESP).
Encryption Breaking
Researchers and attackers have broken many encryption algorithms. For example, the RC4 encryption standard and the Wired Equivalent Privacy standard (based on RC4) implement weak encryption keys that can be broken in a very short time. In 1997, Ian Goldberg, at that time a graduate student at the University of California, Berkeley, used 250 computers to break 40-bit RC4 in less than four hours.
Mathematical Attacks
Time and processing speed are the only factors determining the security of an encryption algorithm. Mathematical or brute force attacks can be used to break any encryption algorithm. As you read in the previous section, 40-bit encryption was quickly broken in 1997. Two years later, the 56-bit Data Encryption Standard (DES) was broken in less than 23 hours by a team from the Electronic Frontier Foundation and Distributed.Net. Although every algorithm is vulnerable to brute force attacks, longer key lengths provide better security. Visit http://www.eff.org/DESCracker for more information on this topic.
Birthday Paradox
The birthday paradox or birthday attack is more of a theory than an actual attack. The birthday paradox, simply stated, is that in every group of 23 people there is more than a 50 percent chance that two people share the same birthday. If you translate this concept into password or encryption breaking, there is better than a 50 percent chance that two passwords in any group of 23 are the same. Of course, that alone doesn't allow you to discover a password or encryption key, nor does it tell you which two of the possible 253 pairs match. Remember also that there is better than a 40 percent chance that none of the pairs match in that particular group.
Theoretical examples of the birthday paradox are not typically applied to breaking passwords or encryption keys. Instead, they are usually proposed as methods for deception on digitally signed documents. A common scenario used to explain how a birthday attack might be carried out is as follows:
-
An unscrupulous person (attacker) creates two contracts: one that is acceptable to the target of the attack and one that is unacceptable.
-
The attacker then creates multiple subtly different versions of each document until a document pair with matching hash codes is produced (think back to your experience with MD5 encryption in Chapter 8).
-
The sender then submits the acceptable contract to the recipient for approval.
-
If the recipient doesn't make any changes to the contract, but does acknowledge that he or she agrees to the terms, the attacker can substitute the unacceptable document for the acceptable document at some future time (because they both have matching hash codes).
One way to avoid a birthday attack is for a document recipient to always make a change to that document and compute a hash value. This way, the recipient also has a digital record of the transaction. Further, the stronger the encryption algorithm, the more costly and difficult it is for the attacker to create a false version.
Hijacking
Session hijacking was described in Chapter 2 as a situation in which communications between two computers (client and server) are taken over by a third (attacker's) computer. The session is essentially stolen from the client. The attacker's computer bumps the client system off its session and begins communicating with the server without going through the full authentication process, gaining access to a secured resource without authentication.
Researchers and attackers discovered methods for hijacking TCP connections, terminal connections, and wireless connections. The following documents describe hijacking exploits in greater detail:
-
CERT Advisory CA-1995-01, "IP Spoofing Attacks and Hijacked Terminal Connections," at http://www.cert.org/advisories/CA-1995-01.html
-
CERT Advisory CA-2001-09, "Statistical Weaknesses in TCP/IP Initial Sequence Numbers," at http://www.cert.org/advisories/CA-2001-09.html
Software Exploitation
Software exploitations were covered in detail in Chapter 6 and Chapter 8. As you probably recall from those chapters, buffer overflows are the most common exploit discovered. In addition to buffer overruns, there are many other types of software vulnerabilities, including cross-site scripting, in which Web sites inadvertently include malicious Hypertext Markup Language (HTML) code in their Web pages. Attackers often place the code there in successful attempts at compromising the Web page. This issue is described in CERT Advisory CA-2000-02, "Malicious HTML Tags Embedded in Client Web Requests," available at http://www.cert.org/advisories/CA-2000-02.html. The SANS organization and the United States Federal Bureau of Investigation (FBI) maintain a list of the top 20 reported vulnerabilities at http://www.sans.org/top20. This Web location also includes links to resources to help you discover these vulnerabilities and increase the security of your network.
Social Engineering
Social engineering was introduced in Chapter 1, and subsequently discussed throughout the book, as any method of attack that relies on the deception or exploitation of people. The example scenario presented in Chapter 1 illustrates a situation in which an attacker could compromise a user's password. A common way for an attacker to do this is to pretend to be part of the technical support staff for the organization. The attacker then contacts a user, explaining that he or she needs the user's password to perform some maintenance or troubleshooting activity on that user's system or the network.
Many other forms of social engineering exist, most conducted over the telephone. However, an attacker might be bold enough to take a part-time job cleaning offices, for example, to search for passwords that are written down. Employees should be advised that company security is in their hands (as explained in Chapter 10). They must realize that writing a password down or giving it to someone else puts the whole organization's information security systems at risk.
One devious example of how networks can be compromised is something that happened to a large ISP. An attacker called an ISP pretending to need technical support. During the conversation, the attacker mentioned that he was selling his car. The technical support person expressed interest in the car, so the attacker said that he would send a picture of the vehicle attached to an e-mail. The technical support person opened the attachment, believing it was a picture of an automobile. However, the attachment was instead a back door program that gave the attacker access to the entire internal network.
You can learn more about social engineering and see more examples of social engineering attacks from the following sources:
-
CERT Incident Note IN-2002-03, titled "Social Engineering Attacks Via IRC and Instant Messaging," available at http://www.cert.org/incident_notes/IN-2002-03.html
-
CERT Advisory CA-1991-04, titled "Social Engineering," available from http:// www.cert.org/advisories/CA-1991-04.html
-
VIGILANTe Corporation's Security Resources Social Engineering information page located at http://www.vigilante.com/inetsecurity/socialengineering.htm
The main method for protecting your organization from social engineering attacks is educating users about these attacks. Also, ensure that there is a clear organizational security policy that explains precautions users must take in handling their passwords, including simple rules, such as the following:
-
Don't give your password to anyone for any reason.
-
Don't write your password down.
-
Don't allow others to watch you enter your password.
-
Don't allow security cameras or video cameras to be aimed at your keyboard when you enter your password.
-
Report any suspected password violations or attempts to violate passwords to your security administrator.
Malicious Code
Malicious code, or malware, is a common name applied to all forms of unwanted and destructive software, such as viruses, worms, and Trojans. The best way to protect yourself and your organization from malicious code is to install virus scanners and keep definition (signature) files current. You can deploy individual virus scanners on each computer and install virus-scanning gateways at your network perimeter (as mentioned in Chapter 6).
Various types of malicious code have been discussed throughout this book. The remainder of this section brings all of that information together in a simple bulleted list. There are also a few new terms in this list. You should commit all of the following terms and definitions to memory:
- Dropper.
A dropper is a virus carrier program or file. When the dropper is executed or opened, it creates a virus. Virus authors often use droppers to shield their programs from virus scanners. Droppers are also called injectors.
- Hoax.
A hoax is false virus warning that people believe is real. These hoaxes are typically spread through e-mail messages. Hoaxes were discussed in Chapter 6.
- Joke.
A joke is a nondestructive program that is propagated like malicious code. People usually consider this type of program annoying or funny.
- Logic bomb.
A logic bomb is a destructive program that goes off when a predetermined event takes place, such as the user typing a certain series of keystrokes, changing a file, or occurrence of a certain time and date. A logic bomb that is triggered at a certain date and time is also called a time bomb.
- Multipartite virus.
A multipartite virus infects multiple locations on a system. These viruses typically infect memory first and then copy themselves to multiple other locations, such as the boot sector of each hard disk, files, and executables on the system.
- Polymorphic virus.
A polymorphic virus, or mutating virus, changes or mutates as it copies itself to other files or programs. The goal is to make it difficult to detect and remove the virus.
- Sparse virus.
A sparse virus doesn't immediately infect files. Instead, it waits a certain period of time (or for some other condition to be met) before it infects a program. For example, the sparse virus might wait until a file is accessed 50 times or until it reaches 500 MB in size. This makes the virus more difficult to detect. A sparse virus is also called a sparse infector.
- Stealth virus.
A stealth virus attempts to hide itself from detection attempts by deceiving people or virus scanning software. When a person or virus scanner attempts to view the virus-infected file, the stealth virus intercepts the disk access request and feeds the person or virus scanner an uninfected version of the file. The virus might also report the uninfected file size of certain files, which prevents people and virus scanners from noticing that a file is too large. Of course, the virus must be resident in memory to perform this action, so a good virus scanner can detect a stealth virus. Stealth viruses are also called interrupt interceptors.
- Trojan horse.
A Trojan horse is a seemingly useful (or harmless) program that performs malicious or illicit action when activated, such as destroying files.
- Virus.
A virus is malicious code that infects or attaches itself to other objects or programs. All viruses have some form of replication mechanism, which is how they propagate.
- Wild.
Wild is a descriptor for malicious code that exists outside of virus and antivirus labs. Malicious code is "in the wild" when it is infecting unsuspecting computer users. The opposite of malicious code in the wild is malicious code in the zoo, discussed later. You can learn more about viruses reported to be in the wild from the WildList Organization International at http://www.wildlist.org.
- Worm.
A worm is malicious code that replicates by making copies of itself on the same computer or by sending copies of itself to another computer. Worms, unlike viruses, do not infect other program files on a computer. All worms have some form of replication mechanism, which is how they propagate.
- Zoo.
Zoo is a descriptor for malicious code that only exists inside a virus or antivirus lab. The opposite of malicious code in the zoo is malicious code in the wild.
The terms and definitions you need to know are covered in this section. For more comprehensive and up-to-date lists of malicious code terminology, visit virus-scanning software vendor Web sites, such as Symantec, McAfee, F-Secure, and Panda Security. You can also find several glossaries online by performing a search for "virus glossary" at your favorite Internet search engine. If you would like to test your virus-scanning software, you can download the European Institute of Computer Anti-Virus Research (EICAR) Standard Anti-Virus Test File, which is available from http://www.eicar.org.

Match the types of attacks or scans in the left column with the appropriate descriptions in the right column.
|
|

The following questions are intended to reinforce key information presented in this lesson. If you are unable to answer a question, review the lesson and then try the question again. Answers to the questions can be found in Appendix A, "Questions and Answers."
-
What are some ways you can combat DoS attacks?
-
How can LSRR be used to avoid security devices?
-
What can attackers use replay attacks to compromise?
-
What type of attacks can be waged against encryption keys and secure hashes?
-
What type of sessions can be hijacked?
Lesson Summary
-
Attackers typically use scanners to locate potential targets and security weaknesses. You can better protect your network by running scanners on it to find and correct weaknesses before attackers. Remove all unnecessary services and patch all discovered vulnerabilities.
-
There are numerous types of DoS and DDoS attacks that attackers can use in attempts to hinder business operations of a target organization. You can reduce the effectiveness of many of these attacks by configuring appropriate filtering rules on your firewalls and routers. Also, maintain a good relationship with your ISP to ensure that you can mitigate a successful DoS attack.
-
Source routing can be used by an attacker to route packets around security devices on your network. To prevent this, configure your routers to drop packets that contain LSRR information.
-
Password guessing and encryption breaking can both be accomplished by brute force. To prevent such attacks from being successful, employ the latest and strongest encryption mechanisms and longest key lengths practical. If you must use passwords, ensure that you educate your users on creating secure passwords that cannot be easily broken by a dictionary attack. Ensure that users know not to write passwords down or share them with other people. Implement strong password policies, so that users must change their passwords frequently.
EAN: 2147483647
Pages: 55