Lesson 1: Understanding Remote Access Connectivity
Lesson 1: Understanding Remote Access Connectivity
One of your responsibilities as a network administrator is to provide connectivity to your network for users from remote locations. This might include remote offices as well as individual users who are connecting to the network from their homes or while traveling.
After this lesson, you will be able to
-
Understand the security implications of providing users remote access over telephone lines
-
Understand the security implications of providing users remote access across the Internet
Estimated lesson time: 15 minutes
Two security concerns to consider when providing these connectivity solutions are how to manage devices not physically connected to your network and how to secure the communications link between the remote computer and your network. Because the remote computer might be a user's personal computer or device, and you might not have physical access to the system, the system might not be as secure as the computers directly attached to your network. Viruses can infect the remote system and spread to systems on your network, and possibly open an access point for hackers to exploit. You should be aware of the following when providing remote access:
-
Remote access computers with sensitive documents might be exposed.
-
The remote user could lack awareness of security concerns.
-
The remote computer can be an avenue for unauthorized access to critical systems.
-
Modems are vulnerable to dial-in attacks.
-
The remote access computer might harbor malicious code.
-
Remote access computers typically lack proper backups.
Remote Connections
Telephone lines and the Internet are public communications mediums that hackers can exploit to take advantage of any weaknesses in your remote access or wireless access solution. There are several ways to provide remote connectivity to your network, but the communications medium choices for remote users are typically limited to access over telephone lines or across the Internet. Examples of remote connections include the following:
-
Public Switched Telephone Network (PSTN) connections use modems and standard telephone lines to transmit data. They are relatively slow, but also flexible and universal.
-
Integrated Services Digital Network (ISDN) is a digital dial-up service provided by telephone companies that offers greater speeds than PSTN, but this service is also more expensive.
-
Digital Subscriber Line (DSL) is a point-to-point connection that also uses standard telephone lines to carry digital signals at much higher speeds than PSTN connections.
-
Community antenna television (CATV) networks use cable television technology to provide users with economical high-speed Internet access. However, CATV is a shared service, which can mean that bandwidth diminishes as more local users concurrently access the Internet.
Once a remote user is connected, there are several ways to limit the resources he or she can access. In deciding what resources to provide access to, you need to balance the capabilities the remote users require, how secure the connection must be, and the cost of providing the secure solution. For instance, if all your remote users require only access to their corporate e-mail, you can configure a Web server to provide access to the e-mail using a Web browser. By configuring e-mail access through the Web browser, you don't have to open more ports through your firewall, and you can control how the users gain access. This also limits the access they have to other networked resources and allows you to provide a relatively inexpensive solution and mitigate many of the security risks.
To implement a cost-effective solution that provides the services your remote users require while maintaining security, you must understand the connectivity technology available along with the protocols and standards used. You also need to be aware of the security risks you must minimize.
Remote Connection Mediums
Telephone lines and the Internet are two communications mediums that are used by businesses to provide remote access capabilities. As shown in Figure 5-1, the remote access server can be made accessible by connecting telephone lines to modems, which are then managed by the remote access server, or the remote access server can be connected to the Internet in some manner. With both types of connections the user is required to form a connection, but the connection can be directly to a remote access server, or to the Internet (through a service provider) and then to the remote access server. Each type of connection is explained in greater detail in the following sections.
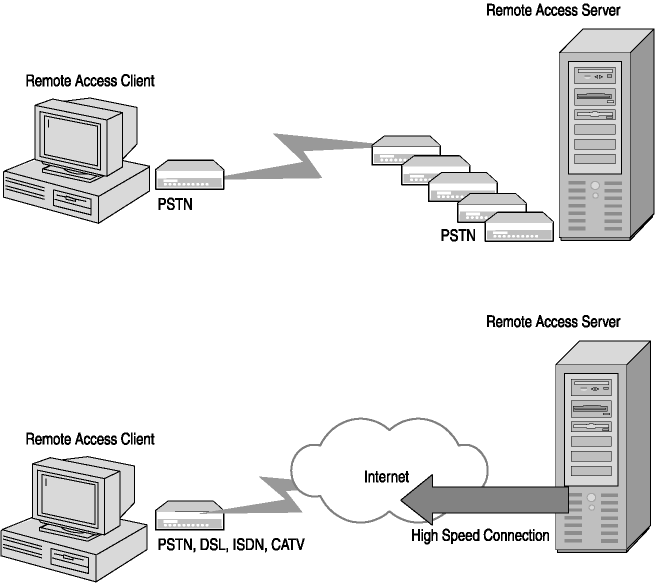
Figure 5-1. Two types of remote access server connectivity
The connection type depends on the high-speed connectivity solutions available, the cost of the service, and the reliability of the service. Each has strengths and weaknesses, costs and vulnerabilities, and security concerns that must be mitigated.
Telephone Connections
With telephone lines, modems are installed in a remote access server, telephone lines are connected, users are provided a telephone number, and they use a notebook computer, their home computer, or other dial-capable devices to gain access to the corporate network and its resources. Examples of protocols used with this type of connection include Serial Line Internet Protocol (SLIP) and Point-to-Point Protocol (PPP). PPP is the predominant protocol in use and it supports TCP/IP communications, authentication mechanisms, and several encryption methods.
When modems are used to connect to a remote access server, you can configure some additional features to provide connection-level security for your remote access clients. The Callback Control Protocol (CBCP) allows your remote access servers or clients to negotiate a callback with the other end. When CBCP is enabled, either the client or the server can request that the server call the client back either at a number supplied by the client or a prearranged number stored on the server. By configuring the server with a prearranged number to call back, you can ensure that the remote access users can call only from a specific location. The remote access server can also be configured to accept or reject calls based on the Caller ID or Automatic Number Identification (ANI) information transmitted by the phone company.
The advantages of using dial-up remote access instead of providing access across the Internet include the following:
- Limited hacker access.
The Internet spans the entire world and the number of users is astounding. Many of the computers connected to the Internet have modems, and they typically dial a local number to gain access to the Internet. By providing access to your network through a dial-up solution, you will likely curb the number of hackers that attempt to hack your network, and they will probably be localized to a smaller geographic location, namely where the number is a local telephone call.
- Less likelihood of being sniffed.
Although it is possible to sniff communications across telephone lines, it requires that the hacker gain access to the telephone lines between the remote user and the remote access server. All telephone calls are routed through telephone switching equipment and the hacker can intercept the communication there, but the chances of that are less likely. You should still encrypt communication over public telephone lines to be safe.
Disadvantages of using dial-up lines to provide a remote access solution include the following:
- Costs for long-distance connections.
If all of the remote access users are within the local calling area, there will be no toll charge for long-distance calling, but if you are supporting users that travel or those based in different geographical locations, the cost of providing the solution is greatly increased.
- Lower productivity.
Because the connection speed is limited, remote users might not be as efficient and productive as they would be using a higher speed solution.
- War dialing.
A technique known as war dialing can be used to dial all of the telephone numbers in a specified range and record those that have a modem connected. Once the phone numbers that have modems are identified, a hacker can redial the system and attempt to break into the computer system. Because the telephone prefix exchange for most organizations is easy to discover, modems that allow users to dial in present a risk.
Internet Connections
When accessing your company's network across the Internet, you connect a remote access server to the Internet, typically through a secure interface such as a firewall. Users connect to the Internet through an Internet service provider (ISP), and a virtual private network (VPN) connection is established between the remote user's computer and the remote access server.
The remote access user can connect to the Internet using a number of different connection devices, including a telephone modem, ISDN modem, DSL modem, or cable modem. Regardless of how the remote user connects to the Internet and how your server is connected to the Internet, the communications link is established across the Internet. Some of the advantages of using Internet-based remote access include the following:
- Lower costs.
If remote access users are based in a widespread geographical area or if they travel, providing access through the Internet can be less costly because long-distance charges can be minimized. Because most areas have Internet access without incurring toll charges, using an ISP that supports your remote user base can be a cost-effective solution.
- Fewer external connection points.
Because most companies require access to the Internet, using a single Internet connection that is secured for access to your company's internal network as well as access to the Internet from the internal network provides a single connection point. This limits the number of connection points a hacker can attempt to exploit and requires you to maintain and monitor fewer access points.
Disadvantages of using the Internet to provide access to your internal network include the following:
- More attacks.
Because you are connecting your internal network to the Internet through a secured communications link, hackers from around the world can attempt to break into your network. Similarly, because connections over cable modems and DSL are much faster than dial-up connections, hackers can carry out more attacks, and more sophisticated attacks, in a shorter period of time than they can over dial-up connections.
- More accessibility to sniffing.
The traffic generated between your remote users and your remote access server is more susceptible to sniffing. A hacker can intercept the communications traffic and, even if it is encrypted, attempt to decrypt the information.
- Increased exposure to attackers.
Before a user makes a VPN connection to the company network, he or she must first connect his or her computer to the Internet securely. If the user's computer is not secured, his or her computer and the company's network are susceptible to any attacker on the Internet.

In the following exercise, you learn how to configure a remote access connection on a computer running Microsoft Windows 2000. (This exercise should work similarly on Windows ME, Windows 98, and Windows XP, although the steps may vary slightly.)
-
From the Start menu, click Settings, then Control Panel.
-
Open Network And Dial-up Connections.
-
Create a new connection by running the Make New Connection Wizard.
-
Complete the Create a New Network Connection Wizard to create a dial-up connection using the following information:
-
Dial-up to private network
-
Use a modem for the dial-up connection
-
Any phone number
-
Allow only yourself to use the connection
-
Use the default name for your new connection
-
-
Start the Create a Connection Wizard by following steps 1-3 and then create another connection using the following information:
-
Connect to a private network through the Internet
-
Do not dial the initial connection
-
IP Address of 192.168.0.1
-
Allow only yourself to use the connection
-
Use the default name for your new connection
-
-
Compare the two connections that you created and review the information necessary to create each and answer the following questions:
-
Did you need to provide a telephone number for each type of connection? If not, which did you have to provide the telephone number for?
-
Did you have to dial an initial connection for both of them?
-
Did you have to provide an IP address for both connection types?
-

The following questions are intended to reinforce key information presented in this lesson. If you are unable to answer a question, review the lesson and then try the question again. Answers to the questions can be found in Appendix A, "Questions and Answers."
-
What are two types of remote access connectivity solutions?
-
What security concerns must you consider when providing remote access connectivity solutions?
-
A technique used to identify modems connected to telephone lines is known as
-
Callback Control Protocol
-
War dialing
-
War driving
-
War walking
-
Lesson Summary
As a network administrator, you will most likely be required to provide remote access to your network, and with wireless communications becoming common, you must understand both technologies. In this lesson you learned the following:
-
When you provide remote access to your network, the computers used by remote users might not be as secure as the computers on your local network.
-
Dial-up connections can be used to provide users remote access to your network. If this is the only link used to provide external access to your network, the number of hackers that attempt to break into your network might be reduced. The cost associated with providing this type of connectivity might be higher than providing access across the Internet due to higher long-distance charges.
-
War dialing is a programmatic technique used to dial every possible telephone number in a specified range. Therefore, keeping your remote access telephone numbers unpublished cannot be considered a reliable method of securing your remote access telephone number against hackers.
-
The Internet can be used to provide remote access to your network. This can be a more cost-effective way to provide access, especially if your company requires Internet connectivity for day-to-day operations. This can also increase the number of hackers that attempt to gain access to your network.
EAN: 2147483647
Pages: 55