Lab 6-1: Securing File and Print Resources

Lab Objectives
This lab prepares you to secure file and print resources by meeting the following objectives:
- Design share and NTFS permissions to provide required security for file resources
- Design print permissions to secure data submitted to a printer
- Design EFS encryption for a domain
About This Lab
This lab looks at three topics:
- Designing security for user's home directories and a shared data store location
- Securing the printing of confidential documents by the legal department that must not be intercepted when sent to the printer
- Designing EFS security for mobile computer users
Before You Begin
Make sure that you've completed reading the chapter material before starting the lab. Pay close attention to the sections where the design decisions were applied throughout the chapter for information on building your administrative structure.
Scenario:Contoso Ltd.
Contoso Ltd., an international magazine sales company, wants to design security for all user home directories, security for a transfer file location, print security for the legal department, and EFS security for the mobile sales people.
Folder Structure
The following folder structure will exist on a DC located at either the Seattle, Lima, or London location. The user's home folder is stored on a DCat his location.
You will create a folder structure on each of the DCs, as shown in Figure 6.13.
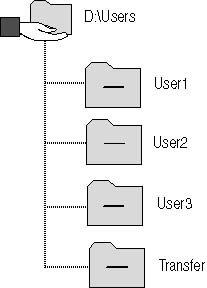
Figure 6.13 The users' directory structure
The d:\Users folder will be located on an NTFS partition to allow local file security to be defined for all folders in the hierarchy.
Shared Folders
You will define the following shared folders on the network to allow administrators to access all folders and to allow users to access their home folders and the shared folder.
| Shared Name | Location | Purpose |
|---|---|---|
| Users | D:\users | To provide an entry point that allows access to all user home directories and the shared folder (subject to NTFS permissions). Must be accessible by all users of the network. |
| User# | D:\users\User# | The personal home folder for User#. In practice, User# would be replaced with the user's logon name. Should only be accessible by the user associated with the personal home folder. |
NTFS Permission Requirements
To provide more specific security, Contoso has defined the following NTFS permissions requirements:
- The Users share should allow users to see only the subfolders that they have permissions to. For example, if User1 is the current user, he should only see the User1 and Transfer folders when connected to the Users share.
- Administrators of the network must have Full Control of all folders in the d:\Users folder hierarchy.
- In the Transfer folder, the following requirements have been defined:
- A global group named SharedFilesAdmins exists. This group must be able to modify and read any documents stored in the d:\Users\Transfer folder.
- The creator of the document must be able to modify or delete the document once it's placed in the folder.
- All other users should be able to read only documents posted by other users. This allows the users to copy a file posted by another employee to their personal folder.
Print Security for the Legal Department
In a separate case, the legal department is concerned that highly confidential documents related to the acquisition of another company may have been compromised when a printed copy of a document went missing.
The legal department wants to have a printer available that can be used only by itself, that's physically accessible only by its members, and that isn't subject to inspection as the print job is sent to the printer.
Mobile Computer Security
Contoso has several salespeople who use a laptop computer as their primary computer. The salespeople connect to the network every day to download their latest pricing database. This database is key to the salespeople because it sets the pricing for that day for the products that they will sell.
The Driving Force
Over the past few months laptops have been stolen from some of Contoso's salespeople. While it may be just a coincidence, a competing magazine sales company has released a pricing strategy that undercuts all Contoso pricing.
Management is concerned about the effects of the stolen laptops and wants to better secure the pricing database and other key documents found on the salespeople's laptops. Management isn't concerned about desktop computers located at Contoso offices.
IT's Perspective
The IT department must design local file security for the pricing database so that only the laptop's user can access the data. In addition, a folder must be provided to allow documents to be encrypted when placed within the folder. The IT department wants to ensure that only salespeople have this ability. They want to prevent all other users from using EFS to encrypt data on their computers until they develop a recovery strategy for the EFS encryption.
Additional Requirements
For each domain, you must define a recovery agent account that allows recovery of encrypted data on the salespeople's laptops. The recovery agent must not exist as an account on the network. If data must be recovered from a user's laptop, the user must go into her home office in London, Seattle, or Lima. A network administrator then uses the recovery key to recover any encrypted files. The administrator must work with another administrator to attach the EFS recovery private key to the administrative account. Once the recovery is performed, a second administrator must verify the removal of the EFS recovery private key from the administrator's account.
Exercise 1: Planning File Security
This exercise looks at the design of Share and NTFS permissions to protect the d:\Users folder hierarchy based on the design requirements outlined in the lab scenario.
Planning Share Security
This exercise looks at designing the share permissions necessary for meeting Contoso's requirements for providing user home folders and a transfer folder. Answers to these questions can be found in the appendix.
- What share permissions must be established on the Users folder to allow users to access their personal folder and the transfer folder?
- What share permissions must you establish for each user name share?
- Under what circumstances would you not need to create individual user shared folders?
Planning NTFS Security
This exercise looks at designing the NTFS permissions necessary for meeting Contoso's requirements for providing user home folders and a transfer folder. Answers to the questions can be found in the appendix.
- Will default NTFS permissions meet all security requirements, or must you define special permissions?
- Complete the following table to define NTFS permissions for each folder in the D:\Users folder hierarchy. Assume that the global group named SharedFileAdmins is a member of the domain local group named TransferAdmins.
Folder Permissions D:\Users D:\Users\User1 D:\Users\User2 D:\Users\User3 D:\Users\Transfer - Where would the home folders be defined for each user account?
Answers
Exercise 2: Planning Print Security
This exercise looks at planning security for the legal department to secure the printing of highly confidential legal documents. Answers to these questions can be found in the appendix.
- What can you do to limit who can print to the Legal printer?
- Complete the following table to document the required permissions for the Legal printer.
Group Permissions Administrators Print Operators Legal Department Creator Owner - What planning is required to prevent output to the Legal printer from being viewed by unauthorized personnel?
- What can you do to protect documents as they are sent to the Legal printer?
Answers
Exercise 3: Planning EFS for Laptops
This exercise looks at planning the EFS deployment to provide local file encryption to laptop users. Answers to these questions can be found in the appendix.
- What must you do to provide EFS capabilities only to laptop computers at Contoso?
- Assuming that you've created the OU structure for Contoso's London domain as shown in Figure 6.14, where would you apply the Group Policy object that designates the EFS recovery agent?
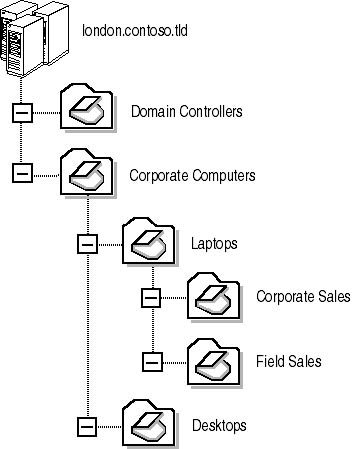
Figure 6.14 The OU structure of Contoso's London office
- What must you do to prevent all other computers in the domain from using EFS encryption?
- How can you enforce the requirement to have two administrators verify the attachment of the EFS recovery private key to an administrator's account?
- What's another method you could use to protect the private key in addition to storing it in a safe?
Answers
EAN: 2147483647
Pages: 172