Lesson 4: Designing Remote Access Policy
Remote access policy provides more control to remote access connections than was previously available in Microsoft network solutions. With remote access policy, instead of defining whether a user account has dial-in permissions, you can define conditions and profiles that must be met before the connection is established. This allows you to define the criteria for allowing remote access and ensure that security is maintained at the desired level.
After this lesson, you will be able to
- Design remote access policies to provide secure connectivity for remote clients
Estimated lesson time: 45 minutes
Designing Remote Access Policy Condition Attributes
You can define remote access policies to grant or deny remote access based on several specified conditions. The remote access server evaluates the existing conditions of the remote access request and compares it to the conditions defined in the remote access policy. If all conditions are matched, the remote access policy is applied to the request.
You can define the following condition attributes to identify which remote access policy to apply to a remote access connection.
- Called-Station-ID. The phone number of the network access server connected to by the remote access client. This condition allows you to identify which remote access policy to apply if a specific phone number is dialed by the remote access connection.
- Calling-Station-ID. The phone number from which the call originated.
- Client-Friendly-Name. The name of the RADIUS client that's forwarding the authentication request. This condition allows you to apply differing remote access policies based on the RADIUS client connected to by the remote access client.
NOTE
Designing RADIUS security for a network is discussed in Lesson 5, "Planning RADIUSSecurity."
- Client-IP Address. The IP address of the RADIUS client that forwarded the authentication request. This condition is used to identify RADIUS clients for VPN authentication requests.
- Client-Vendor. Identifies the manufacturer of the RADIUS client that forwarded the authentication request. You can use this condition to apply manufacturer-specific remote access policies.
- Day-And-Time-Restrictions. Allows you to restrict connections to specific days of the week or times of day.
- Framed Protocol. Allows you to define which remote access protocols are allowed for connections. For example, you could restrict connections to use only PPP and X.25 while preventing SLIP connections.
- NAS-Identifier. Allows you to identify the RADIUS client that forwarded the request by comparing the string sent by the RADIUS client to a string defined in the remote access policy.
- NAS-IP-Address. Allows you to identify the RADIUS client by its IP address. This is useful if you want to apply different remote access policies to a specific VPN server.
- NAS-Port-Type. Allows you to identify the medium used by the remote access client. You can indicate dial-up, ISDN, or VPN connections.
- Service-Type. Allows you to identify the service requested by the client. For remote access clients, the type of service will typically be framed.
- Tunnel-Type. Allows you to restrict which protocol a client uses for a VPN connection. You can restrict the connection to use PPTP or L2TP subject to the existing network infrastructure.
- Windows-Groups. Allows you to restrict access by Windows 2000 group membership. It's recommended to use Windows 2000 Universal groups as the group type.
WARNING
You can't use groups from the remote access server's local security account management (SAM) database in the Windows-Groups condition. All groups must be from the domain.
Making the Decision
When designing conditions for remote access policy, make sure that you consider the following design points in the development of your remote access policy:
- Don't include too many conditions in the remote access policy definition. For the remote access policy to be applied, all conditions in the remote access policy must be met. If a single condition isn't met, the remote access policy isn't applied.
- Remote access policies are processed in order from the top of the list to the bottom. Make sure that you apply the correct conditions to each remote access policy and order the remote access policies so that remote access policies with more specific conditions are evaluated before ones with more general conditions.
- Remote access policies can be defined to both allow and deny remote access to the network. It may be easier to develop a set of condition that, if matched, result in remote access being denied. If you design a remote access policy that implements a deny action, make sure that you place a less-restrictive remote access policy below the remote access policy that defines a deny access condition.
- If no remote access policies exist, all remote access is denied. By default, a remote access policy exists that allows connections 24 hours a day. If you delete this default remote access policy and don't define additional remote access policies, all remote access attempts are denied.
- Don't define a remote access policy condition that can't be met. For example, don't require all connections to use L2TP as the tunnel type if the RADIUS client is located behind a firewall or perimeter server that performs NAT.
Applying the Decision
Different remote access policies are required for the three remote access scenarios presented for Hanson Brothers. Table 13.12 outlines the conditions required for each remote access policy.
Table 13.12 Designing Remote Access Policies for Hanson Brothers
| Remote Access Policy | Required Conditions |
|---|---|
| Employees | Windows Groups: Member of the Remote Users group. Day-and-Time Restrictions: Access for all hours except 6 P.M. to midnight on Saturdays. |
| Administrators | Members of the Administrators group. Day-and-Time-restrictions: Allow access at all hours and on all days of the week. |
| Adventure Works | Calling-Station-ID: Must match the phone number used at Adventure Works to connect to the remote access server. |
| Montréal office VPN | You can't set conditions for the Montréal office VPN because IPSec tunnel mode connections don't utilize RRAS. |
Designing Remote Access Policy Profiles
Once a remote access connection attempt is found to match the conditions defined for a specific remote access policy, the remote access policy profile is applied to the connection. While conditions are used to identify a remote access connection attempt, the profile defines the security settings that the remote access connection must implement. These security settings can include the authentication method and encryption level required to proceed with the connection. You can define the following properties for a remote access policy profile to secure remote access connection attempts, as shown in Figure 13.10.
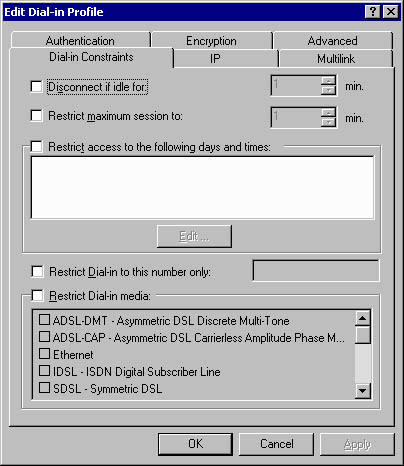
Figure 13.10 Defining remote access policy profile settings
- Dial-in Constraints. You can define how long a connection can remain idle before it's disconnected, the maximum time for session lengths, day and time limits, dial-in number constraints, and dial-in media. Commonly, you use the dial-in constraints to ensure that remote access sessions are terminated if they're idle for a long time.
- IP. You can define packet filters to restrict access to the network for the remote access client. You can define the packet filters on an Allow All Except For The Listed Protocols or a Deny All Except For The Listed Protocols basis.
- Multilink. No security-related settings can be defined for multilink attributes.
- Authentication. Allows you to define the authentication protocols required for a connection. If the connection doesn't support the defined authentication protocols, the connection will be dropped.
- Encryption. Allows you to define the required encryption levels. You can choose no encryption, basic encryption (40-bit keys for DES and MPPE), strong protection (56-bit keys for DES and MPPE), or strongest encryption (3DES and 128-bit MPPE).
NOTE
MPPE provides encryption services for dial-up and PPTP-based VPN connections. DES and 3DES provide encryption for L2TP/IPSec connections. - Advanced. Allows you to define advanced RADIUS attributes that are used when remote access connections use RADIUS authentication.
Making the Decision
Table 13.13 outlines scenarios in which you can use remote access policy profile settings to restrict remote access to the network.
Table 13.13 Using Remote Access Policy Profiles to Restrict Connections
| To | Use the Following Profile Settings |
|---|---|
| Prevent idle remote access connections from using up the available remote access ports | Configure dial-in constraints to drop idle connections after a specified time has passed. Configure dial-in constraints to define maximum session lengths. This requires the remote client to reconnect after the maximum session length is reached. |
| Restrict remote access connections to a specific phone number | Configure dial-in constraints to limit connections to a specific phone number and to require that the connection uses dial-in, referred to as asynch, media. |
| Restrict a remote access connection to a single computer or specific computers | Define IP packet filters that restrict access to specific IP addresses. Define the filters to deny all access except for the filters defined in the packet filter list. |
| Restrict a remote access connection to specific protocols | Define IP packet filters to allow only the protocols defined in the packet filter listing. |
| Require a specific authentication mechanism | Configure the profile to accept only connections using the desired authentication protocols. A connection attempt using a different authentication protocol will be dropped. |
| Require a specific level of encryption | Configure the profile to use the desired encryption level settings. Remember that the use of strongest encryption requires the Windows 2000 High Encryption Pack to be installed at both the remote access server and the remote access client. |
Applying the Decision
Hanson Brothers must configure profiles for each of the client's remote access policies. Table 13.14 outlines the profile configuration required for each remote access policy.
Table 13.14 Designing Remote Access Policies Profiles for Hanson Brothers
| Remote Access Policy | Required Profile Configuration |
|---|---|
| Employees | Only accept MS-CHAPv2 or EAP authentication protocols to ensure mutual authentication of user and server. Allow both asynch and virtual network connections under dial-in constraints. This will provide support for both dial-up and VPN clients. Prevent connections on Saturdays between 6:00 P.M. and midnight under dial-in constraints. |
| Administrators | Only accept MS-CHAPv2 or EAP authentication protocols to ensure mutual authentication of user and server. Allow both asynch and virtual network connections under dial-in constraints. This provides support for both dial-up and VPN clients. |
| Adventure Works | Only accept MS-CHAPv2 or EAP authentication protocols to ensure strong authentication of the remote user account. Require that MPPE 128-bit encryption is required for the connection by requiring that only strongest encryption be accepted. Only accept connections from the phone number supplied by Adventure Works by configuring the dial-in number under dial-in constraints. Only accept asynch connections in the dial-in media property of dial-in constraints. This ensures that VPN connections will fail. Limit access to the remote access server by configuring IP filters that only allow access to the remote access server. If the stock application listens for connections on a known port, limit connections to that port only so that the remote access client can connect only to the stock application on the remote access server. |
| Montréal office VPN | No conditions can be set to match the Montréal office VPN because IPSec tunnel mode connections don't use RRAS. |
Planning Remote Access Policy Application
Remote access policy application varies depending on whether the domain is in native or mixed mode.
NOTE
If your organization wants to centralize remote access policy management, consider using RADIUS servers. Details on RADIUS design are covered in Lesson 5, "Planning RADIUSSecurity."
Remote Access Policy Application in Mixed Mode
In a mixed-mode domain you don't have the Control Access Through Remote Access Policy option available in a user account's properties. By default, every user is set to Allow Access, but remote access policy is still applied.
IMPORTANT
The default remote access policy, Allow Access If Dial-In Permission Is Enabled, will grant access to all users if left unmodified. You must delete or modify the default remote access policy if you need to be able to restrict remote access to the network.
Whenever a connection attempt occurs, the remote access policy whose conditions match the attempt evaluates the remote access policy profile to determine whether to allow the connection. The connection attempt will end in one of two outcomes.
- The connection attempt will succeed. Success occurs when the user's account is configured to allow dial-in access and the remote access client meets the remote access policy profile settings.
- The connection attempt will fail. Failure occurs in the following circumstances:
- The user is denied dial-in permissions in her user properties.
- The connection attempt matches the conditions of a policy but not the profiles settings for the remote access policy.
- The connection attempt doesn't match the conditions of any of the existing remote access policies.
Remote Access Policy Application in Native Mode
In a native mode domain, user accounts are configured to Control Access Through Remote Access Policy in the user account property pages. With this setting, all remote access permissions are determined through remote access policy settings. The connection attempt will result in one of three outcomes.
- Allowed by policy. The connection attempt will succeed if the remote access connection attempt matches the conditions and the remote access policy profile settings for a remote access policy that's set to Grant Remote Access Permission.
- Denied by policy. The connection attempt will fail if the remote access connection attempt matches the conditions and the remote access policy profile settings for a remote access policy that's set to Deny Remote Access Permission.
- Denied implicitly. If the connection attempt doesn't match the conditions defined for any of the existing remote access policies, the connection attempt will be denied.
Making the Decision
To provide remote access to the network, you must determine how you will apply remote access policy. Although remote access policy is applied in mixed mode, native mode provides the most flexibility.
When deciding how to use remote access policy in your domain, consider the following design points:
- In mixed mode, you should delete or modify the default remote access policy. By default, all users are allowed dial-in access. The only exceptions are the built-in Guest and Administrator accounts.
- If you don't want to allow all users dial-in permissions in a mixed mode domain, modify the default remote access policy or change the dial-in permissions for the user accounts that should not have dial-in permissions.
- To prevent specific connection attempts in a native mode domain, configure a remote access policy that defines the conditions of the remote access policy. Configure the remote access policy to deny access if the connection attempt is met.
- In mixed mode or native mode, remote access policy is evaluated to determine whether remote access should be granted to the network.
- To prevent all remote access to the network in mixed mode or native mode, remove all remote access policies from the remote access server.
Applying the Decision
To take full advantage of remote access policy, Hanson Brothers should ensure that their domain is in native mode. Native mode allows Hanson Brothers to take full advantage of remote access policy for dial-up access determination.
Hanson Brothers should verify that each user account that requires dial-up access to the network is configured to Control Access Through Remote Access Policy. This ensures that remote access policy is used to determine access settings. In addition, all other accounts should be configured to Deny Access.
Lesson Summary
Remote access policy provides more flexibility for securing remote access policies than was ever possible in a Windows NT 4.0 network. Make sure that your design includes refining the conditions and profiles that must be matched for remote access to the network. By spending the time to properly define remote access policy, you ensure that security is maintained when access to the network is extended to remote users and networks.
EAN: 2147483647
Pages: 172