Lab 12-1: Designing IPSec Security

Lab Objectives
This lab prepares you to design an IPSec solution for Contoso Ltd. The lab meets the following objectives:
- Design IPSec filters to apply IPSec only to desired network traffic
- Plan IPSec deployment
About This Lab
This lab looks at the planning that Contoso must do to protect their Web server that's exposed to the Internet and to secure a server that hosts a sales tracking application on the internal network. The lab outlines security requirements that will act as design inputs for your solution.
Before You Begin
Make sure that you've completed reading the chapter material before starting the lab. Pay close attention to the sections where the design decisions were applied throughout the chapter for information on building your administrative structure.
Scenario: Contoso Ltd.
Contoso Ltd., an international magazine sales company, wants to design an IPSec solution to protect two servers on its network. The first server that requires protection is the Web server. The Web server has been the focus of several attacks from the Internet and management wants to lock down the server to reduce the chance of a successful attack.
The second server that requires additional security is the Sales Tracking application server. Salespeople at the London office use the Sales Tracking application to record all sales activity during the day. The application also provides a query engine that allows salespeople to query the stored data to determine sales patterns and quota status.
Protecting the External Web Server
The Web server that's hosting the subscription and back-issue ordering site has been the target of several attacks. The Web administrator installed an intrusion detection application at the Web server and found that most attacks start with a port probe that determines which ports are open on the Web server. The attacks then target known vulnerabilities with each open port.
Management would like to lock down the Web server to expose only the ports that are necessary to the Internet. If a port probe is launched against the Web server, all other ports should be configured to appear as if they don't exist.
The Information Technology (IT) department plans to deploy the Web server in a DMZ, as shown in Figure 12.22.
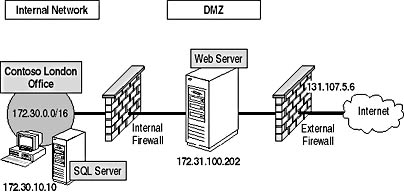
Figure 12.22 The Contoso Web server security configuration
The Web server is located in the DMZ. On the Internet, the Web server is advertised to be at the IP address 131.107.5.6. All incoming traffic to the address 131.107.5.6 is translated to the internal IP address 172.31.100.202. In researching the security of the Web server, the IT department has identified the following business objectives that your design must meet:
- The Web server allows connections from the Internet only to the HTTP (TCP port 80) and HTTPS (TCP port 443) services. All other services must be hidden from Internet users.
- The Web server must store subscription and back-issue orders information on the Microsoft SQL server located on the London network at IP address 172.30.10.10. The Web server will connect to the SQL server using the TCP protocol connecting to the SQL-Data port (TCP 1433). Due to the confidential information that's inputted at the Web server, all data that's transmitted to the SQL server must be encrypted using 3DES. The data that's entered must be protected against modification as well.
- The Web server's administrators are located at the London office in the 172.30.0.0/16 subnet. Administrators need to be able to connect to all services on the Web server. The connections require full encryption. In addition, the entire data packet should be protected against modification to prevent source routing attacks that may compromise the Web server. Source routing attacks attempt to modify the IP header to change the routing of an IP packet.
- Any other connection attempts to the Web server should be prevented.
- Only computers that support strong forms of encryption will be allowed to connect to the Web server for administrative tasks.
- The computers designated for Web server administration are all members of a global group named Web Server Administrators.
Securing the Sales Application Server
The Sales application server is stored on a secure network segment at the London office. All traffic that enters the secured segment must pass through a firewall that separates the secure segment from the public segment. The client-side application is installed on Windows 2000–based computers at each of the three offices, as illustrated in Figure 12.23.
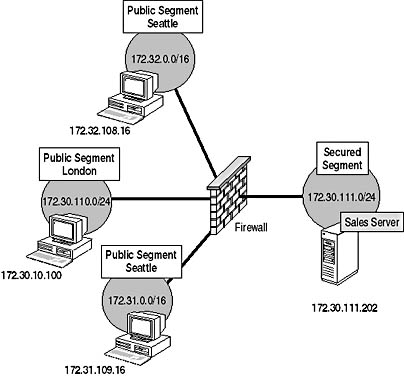
Figure 12.23 Contoso's Sales Tracking application deployment
Management requires you to meet the following business objectives when you design secure access to the Sales server:
- The Sales application server listens for sales updates on TCP port 77889.
- All updates to the server must be encrypted to ensure that other salespeople don't see the data included in the update.
- The update must ensure that both the client computer and the server are mutually authenticated.
- The update packet must be entirely protected from modification of any sort. The sales program uses the IP address of the client computer to identify which salesperson sent the update. Last month a salesperson attempted to replay another salesperson's updates in an attempt to claim the sales as his own. You must prevent attacks of this kind.
- The Sales application server listens for sales queries on TCP port 77890.
- All query information must be protected against inspection when the data is transmitted from the server to the computer. The data payload must be protected against modification as well.
- Connection attempts to the Sales application server must be limited to salespeople. All salespeople are assigned to the global group named Sales Staff that's created in each of the three domains: seattle.contoso.tld, lima.contoso.tld, and london.contoso.tld.
- The Sales application server is dedicated to running the Sales application. No other applications are running on the server. All management of the server is performed locally at the server.
- You must configure the firewall protecting the secure segment to ensure that only updates and queries are passed to the Sales application server in the secure segment. All other requests to the Sales application server must be blocked at the firewall.
Exercise 1: Designing IPSec Policies for Contoso Ltd.
This exercise looks at the design of the IPSec policies required to meet the business objectives outlined for the two projects. Answers to these questions can be found in the appendix.
Designing IPSec Policies for the Web Server
The Contoso Web server is located in the DMZ of the company's network. Assume that the Web server isn't a member of the contoso.tld forest but is a stand-alone server in the workgroup named Internet. The Web server is configured in this manner to prevent attacks from revealing account information from the internal network.
- Does the network architecture prevent you from implementing an IPSec solution? Provide details on why the network architecture does or doesn't allow you to deploy IPSec.
- Could an administrator connect to the Web server and perform administrative tasks from a computer connected directly to the Internet? Why or why not?
- What IPSec protocols are required to meet the business objectives drafted by the IT department?
- What IPSec mode is required to meet the business objectives drafted by the IT department?
In the following table, enter the required filters and actions that must be assigned to the Web server to meet the defined business objectives.
Protocol Source IP Destination IP Protocol Source Port Destination Port Action HTTP HTTPS SQL-Data Any 172.30.0.0/16 Any Any - What must you configure to allow response packets to be secured when returned to connecting client computers?
- To maintain the highest level of security, what authentication protocol must be used to authenticate the computers used by the administrators at the London office with the Web server?
- What encryption algorithm(s) must be supported to meet the business requirements?
- What must you install at all client computers to support 3DES encryption?
Designing IPSec Policies for the Sales Order Server
Answer the following questions based on the scenario presented at the beginning of the lab. Answers to these questions can be found in the appendix.
- Does the network architecture prevent you from implementing an IPSec solution? Provide details on why the network architecture does or doesn't allow IPSec to be deployed.
- What IPSec protocols are required to meet the business objectives drafted by the IT department?
- What IPSec mode is required to meet the business objectives drafted by the IT department?
In the following table, enter the required filters and actions that must be assigned to the Sales server to meet the defined business objectives.
Protocol Source IP Destination IP Protocol Source Port Destination Port Action Sales Updates Sales Queries Any - If Contoso wants to authenticate the computer accounts with no additional configuration, what authentication protocol must be used?
- What filters must be applied at the firewall to allow Sales Application server updates and to allow queries to pass between the public network segments and the secured segment?
- What risk is there in passing IPSec packets through a firewall?
Answers
Exercise 2: Planning Deployment of the IPSec Policies
This exercise looks at the deployment of the IPSec policies required to protect data transmission to the Web server and the Sales server. Answers to these questions can be found in the appendix.
- How can you use the default IPSec Policies to protect access to the Web server?
- Assuming that public key authentication will be used to authenticate the IPSec connection, what planning is required for certificate deployment?
- Assume that the OU structure shown in Figure 12.24 exists for the london.contoso.tld domain. The computers that will manage the Web server are located in the IT OU, but the IT OU has other computers that shouldn't be allowed to connect to the Web server.
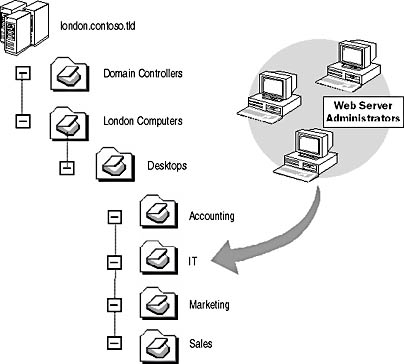
Figure 12.24 Locating the Web server administrator computers in the IT OU
What strategy can you use to ensure that designated computers can negotiate IPSec agreements with the Web server without moving the computer accounts to a different OU?
- If Contoso intends to use IPSec certificates for authentication, what additional design modifications must you make to the PKI to support the automatic issuance of IPSec certificates?
- A new administrator is assigned to manage the Web server. The administrator was just issued a newly installed computer and the computer account for the computer is placed in the IT OU. You've verified that an IPSec certificate is installed to the computer account and that the Client (Respond Only) IPSec policy is assigned to the computer. But the IPSec SA fails to be established. How would you troubleshoot this problem? What's the probable cause?
Answers
EAN: 2147483647
Pages: 172