Scenario 8-1: Securing the Management Interface
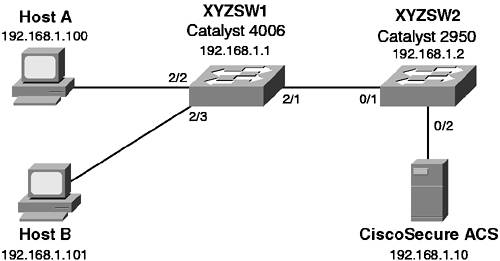
| In this scenario, you secure both a CatOS-based switch and an IOS-based switch. By securing each switch, you are not only reducing their vulnerabilities, but also increasing the security of the entire network. Scenario ExerciseFigure 8-3 illustrates the scenario topology used for Scenarios 8-1, 8-2, and 8-3. Corporation XYZ requires their existing switches to be secured using best practices. They are also about to acquire a larger corporation and need to add new switches to the network. The Corporation XYZ CIO has specified that the current network must be secured, to ensure the new network maintains a tight security policy. Figure 8-3. Scenarios 8-1, 8-2, and 8-3 Topology
A Catalyst 4006 (XYZSW1) provides access for Hosts A and B. Host A is a dedicated network administration workstation that is used to manage the network. Host B is a user's PC, and should not be allowed management access to any network devices. A Catalyst 2950 (XYZSW2) provides connectivity to the company servers, including a recently installed CiscoSecure asynchronous communications server (ACS). Both switches are interconnected by a single Fast Ethernet trunk. Scenario ObjectivesThe scenario objectives are as follows:
Equipment NeededThe equipment needed is as follows:
Command SyntaxThis covers the following:
CatOS Command SyntaxThe following new CatOS commands are introduced in this scenario:
The set authentication Command SyntaxLogin authentication is configured using the set authentication login command. You can also control access to privileged configuration mode (enable mode) separately by using the set authentication enable command. You can individually specify the maximum number of unsuccessful login or enable attempts using the following syntax: set authentication {login | enable} attempt maximum_attempts [console | telnet] Once the maximum number of attempts is reached, you can define a lockout policy by using the following syntax: set authentication {login | enable} lockout time [console | telnet] The time parameter is configurable between 30 and 600 seconds, with a value of 0 disabling any lockout; 0 is the default configuration. NOTE Unlike a console lockout, which completely blocks console access, a Telnet lockout blocks only the IP address from which the login attempts failed. The set banner motd Command SyntaxYou configure a login banner on CatOS using the set banner motd command, as shown in Example 8-1 Example 8-1. Configuring a Banner on CatOS Switch (enable) set banner motd # ********************************** * Unauthorized access prohibited * ********************************** # MOTD banner set Notice the use of the # character as a delimiter, which allows you to enter a banner as free text until you terminate the input with the same delimiter. The delimiter can be any character, as long as it does not appear in the desired banner. The set logout Command SyntaxThe set logout command controls how long a session (e.g., a console or Telnet session) can remain idle before being disconnected by the system: set logout timeout The timeout parameter is specified in minutes and is configurable from 0 (no timeout) to 10000 minutes. The default setting is 20 minutes. The set ip permit Command SyntaxThe set ip permit command restricts management access for Telnet, SSH, and SNMP on CatOS. All restrictions are controlled by the set ip permit command. You must initially specify which hosts are to be permitted management access: set ip permit ip-address [mask] [telnet | ssh | snmp | all] You can specify network address ranges by configuring the optional mask parameter and you can specify different access policies based upon each management access protocol (e.g., Telnet or SNMP). Once you have defined your permitted hosts, you then need to enable the permit list: set ip permit enable [telnet | ssh | snmp | all] You can selectively enable the permit list based upon management protocol, or you can enable all permit lists. The set crypto key rsa Command SyntaxTo enable SSH support, you must create a public/private key pair on the switch using the following syntax: set crypto key rsa nbits The argument nbits is used to specify the length of the key in bits; valid values are from 512 to 2048. Once this key pair has been created, you are able to connect to the switch using a SSH client. Cisco IOS Command SyntaxThe following new Cisco IOS commands are introduced in this scenario:
The username Command and login local Command SyntaxWhen enabling user-level authentication, the first step is to create user accounts for each user that requires access to the switch. This is achieved by executing the username global configuration command: username name password secret Next you need to configure each management interface to use local authentication. This is achieved by executing the login local line configuration command, as shown in Example 8-2. Example 8-2. Enabling Local User-Level AuthenticationSwitch(config)# line con 0 Switch(config-line)# login local Switch(config-line)# line vty 0 4 Switch(config-line)# login local In Example 8-2, both the console and vty ports are configured to use the local user account database to authenticate users. The banner Command SyntaxYou configure a login banner on Cisco IOS using the banner motd global configuration command, as shown in Example 8-3 Example 8-3. Configuring a Banner on Cisco IOS Switch(config)# banner motd # ********************************** * Unauthorized access prohibited * ********************************** # Notice the use of the # character as a delimiter, which allows you to enter a banner as free text until you terminate the input with the same delimiter. It is also possible to display other banners by using one of the arguments to the banner global configuration command listed in Table 8-6.
The exec-timeout Command SyntaxThe exec-timeout command is used to control how long a session (e.g., a console or telnet session) can remain idle before being disconnected by the switch. The command is applied in line configuration mode as shown in Example 8-4 Example 8-4. Configuring Session Timeouts on Cisco IOSSwitch(config)# line con 0 Switch(config-line)# exec-timeout 20 30 The first numeric parameter of the exec-timeout command specifies the number of minutes, while the second numeric parameter specifies the number of seconds. In Example 8-4, the console idle session timeout is set to 20 minutes and 30 seconds. The privilege Command SyntaxThe privilege global configuration mode command is used to define custom, local authorization levels for Cisco IOS commands. You can assign a particular command (or set of commands) to a particular privilege level using the following syntax: privilege {configure | exec | interface} level privilege-level command You must specify which configuration mode the command exists in (e.g., configure, exec, interface); indicate the desired privilege level; and then specify the command you want to assign. You can replace the level privilege-level portion with the reset keyword to reset the command to its default privilege level. Once you have assigned the appropriate commands to the privilege level, you must now create an enable password for the new privilege level. This is configured by using the enable password or enable secret (recommended) command: enable secret level privilege-level secret To access the new privilege level, a user simply appends the desired privilege level when executing the enable command in user mode as shown in Example 8-5 Example 8-5. Accessing a Custom Privilege LevelSwitch> enable 10 Password: ******** Switch# By adding the level to the enable command (e.g., enable 10), the desired level is accessed rather than the default enable mode (level 15). TIP If you access a higher privilege level, you can use any commands specified in lower privilege levels. When creating privilege levels, it is a good idea to simulate all the commands a user would execute and then add them to the privilege level. Don't forget commands such as configure terminal and exit. The access-class Command SyntaxThe access-class line configuration command is used to apply access lists to management interfaces such as vty ports. To restrict Telnet and SSH access, you first create a simple access list that defines the source addresses of authorized hosts and then apply that access list to the management interface (e.g., line vty 0 4), as shown in Example 8-6. SSH connections are treated as coming in via the virtual terminal (vty) ports and, hence, are configured identically Example 8-6. Restricting Telnet and SSH Access on Cisco IOSSwitch(config)# access-list 1 permit 192.168.1.0 0.0.0.255 Switch(config)# line vty 0 4 Switch(config-line)# access-class 1 in In Example 8-6, only hosts on the 192.168.1.0/24 subnet are able to access the switch via Telnet or SSH. You must bind the access list that defines the source hosts to the vty ports using the access-class command. Configuration TasksIn this scenario, you perform the following tasks:
Step 1Preparing the SwitchesIn this step you:
Configuring the System name and Management IP AddressOn each switch, ensure you can access the switch via the console port.
Interconnecting the switchesFor this scenario you interconnect the switches using crossover unshielded twisted-pair (UTP) cables between Fast Ethernet 802.1Q trunk ports (you can use gigabit Ethernet trunks if you have these). Refer to Figure 8-1 for port assignments.
Once these configurations are complete, wait for at least 50 seconds to allow the spanning-tree state of the trunk ports to transition to forwarding.
Connecting the Hosts and AAA ServerEnsure all hosts are configured with an IP address, as shown in Figure 8-3. Then, connect each host as shown in Figure 8-3 to the appropriate switch and port.
Step 2Securing the Catalyst OS Switch (XYZSW1)On XYZSW1, you now perform minor security configurations to enhance the security of Telnet and console access to XYZSW1. In this step you:
Setting Banner, Lockout, and Session Timeout Parameters
Restricting Telnet Access on XYZSW1For this scenario, you permit Telnet access only from Host A (192.168.1.100), SNMP access from an SNMP management system at 192.168.1.20, and block Telnet access from all other hosts for both switches.
As you can see, the Telnet and SNMP permit lists are enabled, and the switch has logged the unauthorized Telnet connection attempt from Host B. Example 8-20 shows what a denied host receives when trying to Telnet to XYZSW1. Example 8-20. Denied Telnet Connection C:\>telnet 192.168.1.100 Connecting To 192.168.1.100... Access not permitted. Closing connection... Connection to host lost. C:\> Enabling SSH SupportFor this section, you enable SSH support and then disable Telnet access to XYZSW1.
Step 3Securing the Cisco IOS Switch (XYZSW2)On XYZSW2, you now perform minor security configurations to enhance the security of Telnet and console access to XYZSW2. In this step you:
Setting Banner, Lockout, and Session Timeout Parameters
Restricting Telnet Access on XYZSW2In this section, you permit Telnet access only from Host A (192.168.1.100), SNMP access from an SNMP management system at 192.168.1.20, and block Telnet access from all other hosts.
Configuring Privilege Levels to Provide Command AuthorizationFor this section, you configure privilege levels that allow network operators to view the system configuration and allow the operator to add a description to an interface. The following commands are added to a custom privilege level; then a password is assigned to allow operators to gain access to the command set:
Be sure that you understand the configuration mode (e.g., global configuration or exec) of the commands that you want to add.
In Example 8-31, a password of "cisco123" is assigned to privilege level 5.
In Example 8-32, you access the custom privilege level by using the enable 5 command. Notice that you can execute all the required commands, but when you try to execute an unauthorized command (e.g., erase), IOS notifies you that the command is invalid. |
EAN: 2147483647
Pages: 135