Taking a Tour of the Registry
To launch the Registry Editor, open the Run dialog box, type regedit, and click OK. Figure 2-1 shows the Registry Editor window that appears.
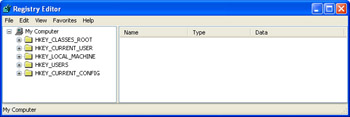
Figure 2-1: : Running the REGEDIT command launches the Registry Editor, a front end that enables you to work with the registry’s data.
The Registry Editor is reminiscent of Windows Explorer, and it displays information in basically the same way. The left side of the Registry Editor window is similar to Windows Explorer’s Folders pane, except that rather than folders, you see keys. For lack of a better phrase, we’ll call the left pane the Keys pane.
Navigating the Keys Pane
The Keys pane, like Windows Explorer’s Folders pane, is organized in a treelike hierarchy. The five keys that are visible when you first open the Registry Editor are special keys called handles (which is why their names all begin with HKEY). These keys are referred to collectively as the registry’s root keys. We’ll tell you what to expect from each of these keys later (see the section called “Getting to Know the Registry’s Root Keys,” later in this chapter).
These keys all contain subkeys, which you can display by clicking the plus sign (+) to the left of each key, or by selecting a key and pressing the plus- sign key on your keyboard’s numeric keypad. When you open a key, the plus sign changes to a minus sign (–). To close a key, click the minus sign or select the key and press the minus-sign key on the numeric keypad. (Again, this is just like navigating folders in Windows Explorer.)
You often have to drill down several levels to get to the key you want. For example, Figure 2-2 shows the Registry Editor after you’ve opened the HKEY_ CURRENT_USER key, then the Control Panel subkey, and then clicked the Mouse subkey. Notice how the status bar tells you the exact path to the current key, and that this path is structured just like a folder path.
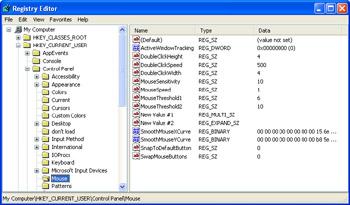
Figure 2-2: Open the registry’s keys and subkeys to find the settings you want to work with.
| Note | To see all the keys properly, you likely will have to increase the size of the Keys pane. To do this, use your mouse to drag the split bar to the right. Alternatively, select View, Split, use the Right arrow key to adjust the split bar position, and then press Enter. |
Understanding Registry Settings
If the left side of the Registry Editor window is analogous to Windows Explorer’s Folder pane, the right side is analogous to Windows Explorer’s Contents pane. In this case, the right side of the Registry Editor window displays the settings contained in each key (so we’ll call it the Settings pane). The Settings pane is divided into three columns:
-
Name This column tells you the name of each setting in the currently selected key (analogous to a file name in Windows Explorer).
-
Type This column tells you the data type of the setting. There are five common data types:
-
REG_SZ This is a string value.
-
REG_MULTI_SZ This is a series of strings.
-
REG_EXPAND_SZ This is a string value that contains an environment variable name that gets “expanded” into the value of that variable. For example, the %SystemRoot% environment variable holds the name of the folder in which Windows XP was installed. So if you see a registry setting with the value %SystemRoot%\System32\, and Windows XP is installed in C:\Windows, then the setting’s expanded value is C:\Windows\System32\.
-
REG_DWORD This is a double word value: a 32-bit binary value arranged as eight hexadecimal digits. For example, 11 hex is 17 decimal, so this number would be represented in DWORD form as 0x00000011 (17). (Why “double word”? A 32- bit value represents four bytes of data, and because a word in personal-computer programming circles is defined as two bytes, a four-byte value is a double word.)
-
REG_BINARY This value is a series of hexadecimal digits.
-
-
Data This column displays the value of each setting.
Getting to Know the Registry’s Root Keys
The root keys are your registry starting points, so you need to become familiar with what kinds of data each key holds. The next few sections summarize the contents of each key.
HKEY_CLASSES_ROOT (HKCR)
HKEY_CLASSES_ROOT—usually abbreviated as HKCR—contains data related to file extensions and their associated programs, the objects that exist in the Windows XP system, as well as applications and their Automation information. HKCR also contains keys related to shortcuts and other interface features.
The top part of this key contains subkeys for various file extensions. You see .bmp for BMP (Paint) files, .doc for DOC (WordPad) files, and so on. In each of these subkeys, the Default setting tells you the name of the registered file type associated with the extension. (We discuss file types in Chapter 7, “Getting the Most Out of Files and Folders.”) For example, the .txt extension is associated with the txtfile file type.
These registered file types appear as subkeys later in the HKEY_CLASSES_ ROOT branch, and the registry keeps track of various settings for each registered file type. In particular, the shell subkey tells you the actions associated with this file type. For example, in the shell\open\command subkey, the Default setting shows the path for the executable file that opens. Figure 2-3 shows this subkey for the txtfile file type.
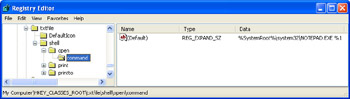
Figure 2-3: The registered file type subkeys specify various settings associated with each file type, including its defined actions.
HKEY_CLASSES_ROOT is actually a copy (or an alias, as these copied keys are called) of the following HKEY_LOCAL_MACHINE key:
HKEY_LOCAL_MACHINE\Software\Classes
The registry creates an alias in HKEY_CLASSES_ROOT to make these keys easier for applications to access and to improve compatibility with legacy programs.
HKEY_CURRENT_USER (HKCU)
HKEY_CURRENT_USER (usually abbreviated as HKCU) contains data that applies to the user that’s currently logged on. It contains user-specific settings for Control Panel options, network connections, applications, and more. Note that if a user has group policies set on his or her account, those settings are stored in the HKEY_USERS\sid subkey (where sid is the user’s security ID). When that user logs on, these settings are copied to HKEY_CURRENT_USER. For all other users, HKEY_CURRENT_USER is built from the user’s profile file, Ntuser.dat.
| Note | NoteHow do you find out each user’s SID? First, open the following registry key: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList\ Here you’ll find a list of SIDs. The ones that begin S-1-5-21 are the user SIDs. Select one of these SIDs and then examine the ProfileImagePath setting, which will be of the form %SystemDrive% \Documents and Settings\user, where user is the user name associated with the SID. |
Here’s a summary of the most important HKEY_CURRENT_USER subkeys:
-
AppEvents Contains sound files that play when particular system events occur (such as maximizing of a window).
-
Control Panel Contains settings related to certain Control Panel icons.
-
Identities Contains settings related to Microsoft Outlook Express, including mail and news options and message rules.
-
Keyboard Layout Contains the keyboard layout as selected via Control Panel’s Keyboard icon.
-
Network Contains settings related to mapped network drives.
-
Software Contains user-specific settings related to installed applications and Windows XP.
HKEY_LOCAL_MACHINE (HKLM)
HKEY_LOCAL_MACHINE (HKLM) contains non–user-specific configuration data for your system’s hardware and applications. HKLM contains three subkeys that you’ll use most often:
-
Hardware Contains subkeys related to serial ports and modems, as well as the floating-point processor.
-
Software Contains computer-specific settings related to installed applications. The Classes subkey is aliased by HKEY_CLASSES_ROOT. The Microsoft subkey contains settings related to Windows XP (as well as any other Microsoft products you have installed on your computer).
-
System Contains subkeys and settings related to Windows XP startup.
HKEY_USERS (HKU)
HKEY_USERS (HKU) contains settings that are similar to those in HKEY_ CURRENT_USER. HKEY_USERS is used to store the settings for users with group policies defined, as well as the default settings (in the .DEFAULT subkey) that get mapped to a new user’s profile.
HKEY_CURRENT_CONFIG (HKCC)
HKEY_CURRENT_CONFIG (HKCC) contains settings for the current hardware profile. If your machine uses only one hardware profile, HKEY_ CURRENT_ CONFIG is an alias for HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001. If your machine uses multiple hardware profiles, HKEY_CURRENT_CONFIG is an alias for HKEY_LOCAL_MACHINE \SYSTEM\ControlSetnnn, where nnn is the numeric identifier of the current hardware profile. This identifier is given by the CurrentConfig setting in the following key:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\IDConfigDB
Understanding Hives and Registry Files
The registry database actually consists of a number of files containing a subset of the registry. This subset, called a hive, consists of one or more registry keys, subkeys, and settings. Each hive is supported by several files that use the extensions listed in Table 2-1. Be aware, though, that other programs use the same file name extensions, but for other purposes.
| Extension | File Contains |
|---|---|
| None | A complete copy of the hive data. |
| .alt | A backup copy of the hive data. |
| .log | A log of the changes made to the hive data. |
| .sav | A copy of the hive data as of the end of the text mode portion of the Windows XP setup. |
Table 2-2 shows the supporting files for each of the major system-default hives. (Note that not all of these files may appear on your system.)
| Hive | Files |
|---|---|
HKLM\SAM | %SystemRoot%\System32\config\Sam %SystemRoot%\System32\config\Sam.log %SystemRoot%\System32\config\Sam.sav |
HKLM\Security | %SystemRoot%\System32\config\Security %SystemRoot%\System32\config\Security.log %SystemRoot%\System32\config\Security.sav |
HKLM\Software | %SystemRoot%\System32\config\Software %SystemRoot%\System32\config\Software.log %SystemRoot%\System32\config\Software.sav |
HKLM\System | %SystemRoot%\System32\config\System %SystemRoot%\System32\config\System.alt %SystemRoot%\System32\config\System.log %SystemRoot%\System32\config\System.sav |
HKU\.DEFAULT | %SystemRoot%\System32\config\Default %SystemRoot%\System32\config\Default.log %SystemRoot%\System32\config\Default.sav |
Also, users each have their own hives, which are mapped to HKEY_CURRENT_ USER during logon. The supporting files for each user hive are usually stored in \Documents and Settings\user, where user is the user name. In each case, the Ntuser.dat file contains the hive data, and the Ntuser.log file tracks the hive changes. (As we mentioned earlier, if a user has group policies set on his or her account, the user data is stored in an HKEY_USERS subkey.)
| Tip | You can also work with a registry on a remote computer over a network. See Chapter 16, “Setting Up and Administering a Small Network,” for details. |
EAN: 2147483647
Pages: 126