Changing Dangerous Default Settings
The majority of Wi-Fi hardware is user friendly. Most people can set up an access point and Wi-Fi cards even if they are networking novices. This user friendliness has helped to drive adoption of Wi-Fi networks; but it may also leave many WLANs vulnerable unless users take steps to secure them.
Users create some of the biggest security problems when they set up their wireless networks and fail to change the default settings. These defaults, including SSID,IP subnets, and administrative usernames and passwords, are well known to wardrivers and crackers, and are available on the Internet. Failing to change these settings invites disaster.
| On The Web | For lists of known default settings for Wi-Fi equipment visit www.cirt.net. |
Taking the time to follow the steps in this chapter will make your WLAN reasonably secure, and will deter casual wardrivers and inexperienced crackers. However, a skilled and determined cracker can still get around some of these measures, soyou’ll need to be diligent in checking your security periodically to make sure.
Rethinking the SSID
Every Wi-Fi access point has an assigned Service Set Identifier (SSID) that identifies the network. Leaving the default SSID in place when you set up your WLAN can help crackers or wardrivers identify which hardware you are using. A wardriver or cracker can discover the SSID of your network using an application like NetStumbler (see Figure 11-1). For example, the default SSID for most Linksys hardware is “Linksys,” for Netgear access points it’s “netgear.” These default SSIDs clearly identify the hardware. Once a cracker knows that, he can look up the default administrative usernames and passwords, allowing him to compromise the network with minimum effort.
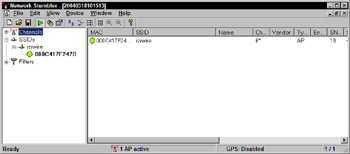
Figure 11-1: Discovering an SSID with NetStumbler
Fortunately, you can change the SSID on your access points at any time (see Figure 11-2). You just have to be sure to change the SSID on your wireless adapters as well. When you are change the default SSID, avoid using something that identifies your residence or business. Some of the best practices for changing your SSID are:
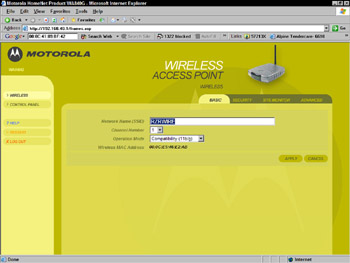
Figure 11-2: Changing the default SSID
-
Never use personal information in your SSID (name, birth date, phone number, or street address).
-
Don’t use any of your usernames or passwords.
-
Don’t use an SSID that identifies your hardware (for example, Linksys BEFW11S4).
-
Create long SSIDs that are composed of both letters and numbers.
-
Don’t use an SSID that identifies the access point’s location or dept (for example, “accounting”).
Note The SSID must be all caps for MS-DOS clients to be able to recognize it.
Changing the default SSID is the first and easiest step to deterring casual wardrivers and inexperienced crackers from trespassing on your WLAN.
Changing passwords and usernames
In addition to the default SSID, all hardware comes configured with a default administrative username and password. It’s especially important that you take the time to change these settings (see Figure 11-3) because, like the SSID, default administrative usernames and passwords are common knowledge to crackers and wardrivers and are available on a number of Web sites. If you neglect to change the settings, a cracker can determine which hardware you are using and use the default username and password to take over the access point and compromise your WLAN.
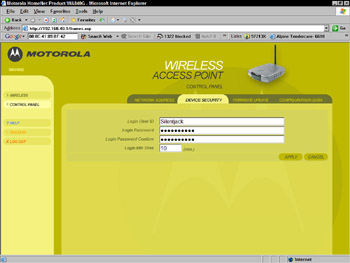
Figure 11-3: Changing the default administrative username
Some of the best practices for choosing a username and password are:
-
Use passwords that are at least six characters long.
-
Use passwords that contain both letters and numbers.
-
Use a mix of upper- and lowercase letters.
-
Don’t use common names, places, or “dictionary” words.
-
Don’t use personal data as a password (birth date, address, or name)
-
Don’t use your username as a password in any form (doubled, tripled, or reversed).
-
Don’t use keyboard keys in sequence (“12345”, “QWERTY”, etc).
-
Don’t use acronyms.
-
Don’t reuse your old passwords.
-
Don’t write down passwords.
-
Change your password frequently.
Using password-cracking utilities and any desktop computer, a cracker can dis- cover passwords created with English or foreign dictionary words in a matter of seconds. During audits of some networks, I have been able to recover as many as 90 percent of users’ passwords in less than one minute. Most had ignored common- sense best practices when choosing their passwords.
Editing IP addresses
Any device connected to the Internet or to a routed TCP/IP network (like a WAN) needs to have an IP address assigned to it in order for it to connect to the network. Wi-Fi access points have a default Internet Protocol (IP) address assigned by the manufacturer, as well as a default IP subnet and gateway address.
This can be a problem because, like everything else, the default network settings on access points are common knowledge. For example, the default network settings on a Motorola access point are:
-
IP address: 192.168.40.1
-
Default gateway 255.255.255.0
Almost all access points available have a Web interface that allows you to configure the device through a Web browser. All you need to do is enter the device’s IP address in your browser’s address window, and you will connect to the access points built-in Web server, which will display a login and configuration page (see Figure 11-4).
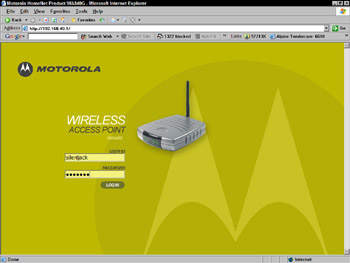
Figure 11-4: Connecting to an access point via a Web browser
If a cracker knows the default network settings for a particular manufacturer’s equipment, and he identifies which type of access point you are using (that is, through SSID broadcast), he can connect to the access point through a browser. If you haven’t changed the username and password, he can log into the access point and take control of it.
When you set up your access point, change the default IP address and the IP subnet to make it more difficult for trespassers and crackers to guess your access point’s IP address and attempt to connect to it (see Figure 11-5). Don’t assign an IP address from the first few addresses in the subnet range. For example, if the address range of your WLAN is 192.168.0.0 to 192.168.255.255, don’t assign your access point192.168.0.1 or something close.
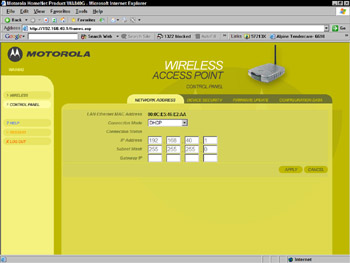
Figure 11-5: Changing network settings on an access point
Access points typically have an address in the beginning of the subnet range, and any cracker knows this. For example, if you change the default IP address from 192.168.0.1 to 192.168.0.3, a cracker can still try the first few numbers in the address range and he will find your access point. Change the address to something less obvious to make it more difficult for a cracker to guess.
EAN: 2147483647
Pages: 145