Understanding Malicious Software
Computer viruses, worms, and other malicious programs are a major headache as well as security problem. In addition to the threats that come from the Internet, your Wi-Fi network can be exposed to viruses by other avenues. The fundamental advantage of Wi-Fi is mobility, the ability to roam within and between networks. Wi-Fi exposes your computers to viruses in a completely new way. This chapter examines viruses, worms, and other malicious code, as well as virus writers and hoaxes.
Malicious software, malicious code, or malware is software created to undermine security, damage systems, steal information, make you miserable, or all of the previous.
Twenty years ago, most people working with computers were primarily worried about computer viruses that spread mainly via infected floppy disks and computer files. Today’s threats have evolved to include computer worms, Trojans, Bots, and blended threats.
Malware can spread or attack in different ways, so it’s important to familiarize yourself with the types of threats that you are likely to face in order to take proper steps to secure your systems and protect your data.
Malware is a significant threat to wireless networks and devices. In addition to all of the threats that Ethernet networks face, wireless opens up new avenues of attack for malware to exploit. However, the situation isn’t completely dire, and you can correct these problems.
On a wired network, the most likely vector for infection by malware is the Internet. However, on a WLAN there are additional vectors to worry about (see Figure 7-1). It’s possible for malware from outside wireless sources to attack your network. Some of these sources include:
-
Wardrivers and crackers
-
Cross-contamination from adjacent WLANs
-
Infected mobile clients
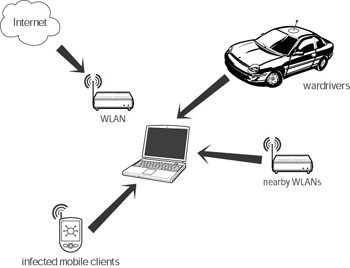
Figure 7-1: Possible vectors for infecting a WLAN
Wardrivers and crackers can purposely infect your wireless clients after accessing your WLAN. This doesn’t even have to be intentional; individuals who are only looking to use your Internet connection could possibly infect your computer if they haven’t taken steps to defend their own.
Often, neighbors may have WLANs operating on the same channel and even using the same default SSID. Because Windows XP automatically attempts to connect to detected wireless networks, a neighbor could inadvertently connect to your WLAN rather than his own, creating an avenue for infection through his computers (see Figure 7-2). You may even inadvertently connect to a neighbor’s WLAN, creating the same problem in reverse.
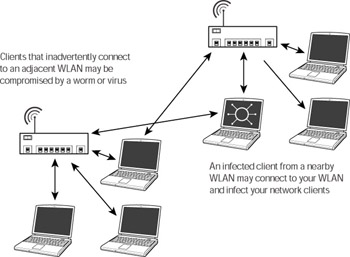
Figure 7-2: Cross-contamination between WLANs
A mobile wireless client like a laptop or PDA can also introduce an infection into your network. Although there are few viruses that affect PDAs, your PDA can carry a virus that affects your PCs. For example, if you downloaded a ZIP file or a Word document to your PDA and then transferred it to you PC, it’s possible that the file could be infected with a virus that targets your PC (see Figure 7-3).
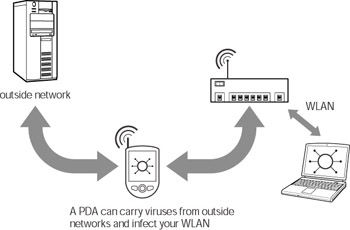
Figure 7-3: A PDA as a vector for infection
| Note | Even though there still aren’t many viruses that target PDAs, the possibility of introducing a PC (or Mac) virus onto your network through your PDA is real. Install antivirus software on your handheld devices to detect viruses, and scan all files that you transfer to your computer from a PDA. |
While your wireless network is vulnerable to different types of attack, you can close many of these avenues of vulnerability by taking simple steps to secure your WLAN.
| Cross-Reference | Read more about taking steps to secure your WLAN in Chapter 11. |
EAN: 2147483647
Pages: 145