Understanding Rogue Access Points
A rogue access point can be a couple of different things. Often, you’ll hear the term used when referring to an unauthorized access point added to a corporate network by an employee. Usually, the employee is on a wired local area network (LAN) and wants wireless connectivity. Perhaps his company hasn’t adopted wireless or doesn’t plan to, so the employee takes it upon himself to install his own access point at his desk and connect it to the corporate LAN. This is a problem, and it can create serious security issues for the company’s IT department.
Another definition of a rogue access point is an access point set up by a cracker to collect data such as passwords, usernames, or credit card numbers. This is the one I will concentrate on. It is a growing threat in public places and one that you need to take seriously. A rogue access point masquerades as a legitimate access point, often as part of a commercial wireless network. Incidents involving rogue access points have been popping up all over the country, particularly in urban areas and in places where business travelers congregate.
Wi-Fi hotspots are quickly becoming ubiquitous across the country. Companies like Wayport, Boingo, and T-Mobile offer service nationwide. Crackers take advantage of peoples’ implicit trust in these commercial wireless offerings. They do this by setting up rogue access points that look like access points belonging to commercial Wi-Fi networks.
The cracker sets up the rogue access point and names it with the same SSID as a commercial access point. The name might be Wayport or T-Mobile. When you are near one of these access points and you start up your wireless device, you’ll see the rogue access point, but because the cracker has used the name of your wireless service provider’s legitimate access points, you connect to it (see Figure 4-9).
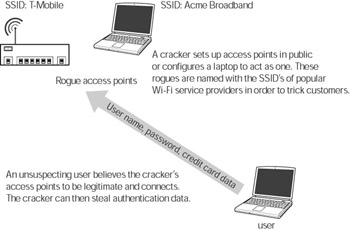
Figure 4-9: A rogue access point
The rogue access point can eavesdrop on all of the traffic sent to it by client machines. WEP or WPA encryption offer no protection here because you are associating with the access point and machines on both ends of the connection have the encryption key and can decrypt all of the data.
The cracker may also configure the rogue access point to provide a new-user registration service so that it can collect credit card numbers and personal information from unsuspecting people who think they are signing up for wireless service on a legitimate provider’s network.
Unfortunately, there is little that you can do to expose this type of wireless attack. IT personnel in companies can use hand scanners to detect and locate access points added to their networks. They know if an access point should be there or not, so if they detect one they know it’s a rogue.
Unfortunately, there isn’t a similar solution for discovering rogue access points masquerading as legitimate ones. A scanner is expensive, and even if you know how to use one, all it does is tell you that an access point is there, not whether or not it’s legitimate.
The best method of protection is to be cautious and educate yourself. Download a list of the locations of all hotspots and access points offered by your carrier. Look for signs that indicate your carrier offers service at a particular location. When you turn on your laptop and see an access point available or if there is a sign present that indicates there should be an access point there, check to see if it is on the hotspot list you downloaded. If neither of these conditions is true, be cautious and don’t connect to the access point in question. To protect yourself at a hotspot, you should follow the instructions that I gave earlier in this chapter.
EAN: 2147483647
Pages: 145