| As Figure 6-15 shows, there are four types of RBAC declarations: -
- role_type_def
-
Role type declarations -
- role_dominance
-
Role dominance declarations -
- roletrans_def
-
Role transition declarations -
- role_allow_def
-
Role allow declarations Figure 6-15. RBAC declarations (rbac_decl) 
6.5.1 Role Type Declarations A role type declaration specifies the set of domains for which a role is authorized. They have the form shown in Figure 6-16. The symbol identifier specifies the role and the symbol names specifies the authorized domain or domains. Figure 6-16. Role type declaration (role_type_def) 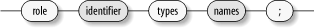
Role type declarations typically appear in type enforcement files, where they specify the roles that are authorized to enter the domains defined by the TE files. For instance, the ping.te file contains the following role-type declarations: role sysadm_r types ping_t; role system_r types ping_t;
The first declaration authorizes the sysadm_r role to enter the ping_t domain. The second declaration authorizes the system_r role to do likewise. 6.5.2 Role Dominance Declarations Role dominance declarations can be used to specify a hierarchy among roles. However, existing implementations of SELinux policies do not specify role hierarchies. 6.5.3 Role Transition Declarations At one time, role transition rules were used to specify the new role of a process based on its current role and the type of executable being executed. Role transition declarations were deprecated and dropped from SELinux, which used domain transitions instead. However, the Fedora Core 2 implementation of SELinux resumed use of role transitions. Fedora Core 2 provides a transition from sysadm_r to system_r designed to avoid the need for the administrator to execute run_init when invoking a SysV init script. 6.5.4 Role Allow Declarations Role allow declarations specify authorized transitions between roles. A transition refers to someone in a source role (an existing role) choosing to enter a target role (a different role). Figure 6-17 shows their syntax. Two instances of names appear; the first, designated source_names , specifies the source role and the second, designated target_names , specifies the target role. Figure 6-17. Role-allow declaration (role_allow_def) 
Role allow declarations appear in the rbac file and in TE files. However, if you inspect the TE files in domains/program , you likely won't find many role allow declarations. They're generally created indirectly, by invoking M4 macros such as the base_user_domain in macros/base_user_macros.te . As an example, the rbac file contains the following role allow declaration: allow sysadm_r system_r;
This declaration allows transition from the sysadm_r role to the system_r role. If you inspect the policy.conf file, you can view policies after M4 macro expansion. There, you're likely to see role allow declarations such as these: allow staff_r sysadm_r; allow sysadm_r staff_r; allow sysadm_r user_r; allow system_r staff_r; allow system_r sysadm_r; allow system_r user_r; allow user_r sysadm_r;
|