| The preceding sections of this chapter have provided an overview of the functions that underlie SELinux. This section provides an overview of the architecture of SELinux. SELinux consists of the following major components : 2.6.1 Kernel-Level Code When active, the SELinux kernel code monitors system activity and ensures that requested operations are authorized under the currently configured SELinux policy, disallowing any operations not expressly authorized. It also generates system log entries for certain allowed and denied operations, consistent with policy specifications. Originally, the SELinux kernel-level code was implemented as a patch to the Linux 2.2 kernel, and later the Linux 2.4 kernel. More recently, much of the SELinux kernel-level code has been integrated within the Linux 2.6 kernel. The Linux Security Modules (LSM) feature of Linux 2.6 was expressly designed to support SELinux and other potential security servers.  | The principal SELinux facility omitted from Linux 2.6 concerns the labeling of network objects and the security decisions pertaining to them. Some Linux distributors have plans to make the missing SELinux capabilities available as one or more kernel patches, or otherwise . | |
Despite the integration of SELinux with the Linux 2.6 kernel, a given operational Linux 2.6 kernel may or may not support SELinux. Like many kernel features, the level of SELinux support can be configured when the kernel is built. SELinux can be: Therefore, before attempting to configure SELinux on a system, you should determine whether any of the available kernels supports SELinux and, if not, obtain an appropriate kernel. Chapter 3 explains how to build a Linux 2.4 or Linux 2.6 kernel that supports SELinux. 2.6.2 The SELinux Shared Library Most non-kernel SELinux components are linked against an SELinux shared library, currently named libselinux1.so . This library makes available the functions associated with the SELinux application programming interface (API). This library must be installed and available or programs linked against it will fail.  | It might seem that the absence of the SELinux shared library would be a relatively minor matter inhibiting the full and correct functioning of SELinux. However, as explained subsequently in this chapter, implementation of SELinux entails installation of modified versions of several critical system executables, which are linked against the SELinux shared library. Generally , if the SELinux shared library is not available, the system will be crippled. Recovery procedures will be necessary to restore proper system operation. | |
2.6.3 The SELinux Security Policy As explained, the SELinux security server bases its decisions on a policy file that can be configured by the administrator. The policy file provides flexibility, enabling SELinux administrators to implement customized security policies that suit local needs, rather than one- size -fits-all boilerplate policies provided by a Linux distribution. When an SELinux system starts up, it loads the local security policy from a binary policy file, which typically resides in /etc/security/selinux ; however, a Linux distributor may choose to place the file in another location. The SELinux binary policy file is generated by a Makefile , which resides in the SELinux source directory, typically /etc/security/selinux/src/policy or /etc/selinux . Some Linux distributions, such as Fedora, do not install the SELinux source directory by default, so the directory and the Makefile may be absent from your system. The Makefile concatenates a variety of source files, expands the M4 macros they contain, and places the result in a file named policy.conf , which resides in the SELinux source directory. It then compiles the resulting SELinux policy statements within policy.conf into binary form. Figure 2-7 illustrates this process. Figure 2-7. Creating and loading the SELinux binary policy file 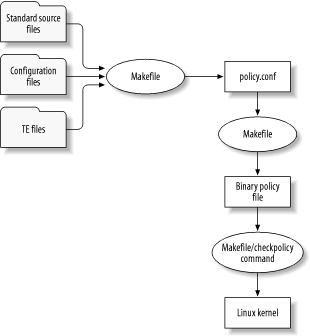
 | make is a Linux/Unix application that compiles source code ”such as the Linux kernel ”and performs other useful operations, under control of a configuration file called a Makefile . You don't need a detailed understanding of make to work with SELinux. M4 is a macro processor commonly used in support of Linux applications, such as Sendmail. M4 is explained more fully in Chapter 5. | |
Roughly speaking, the SELinux source files are of four major types: -
- Standard source files that are seldom modified by the SELinux administrator
-
These files include such files as the SELinux Makefile , files defining standard M4 macros, and files that contain boilerplate policy language. Administrators may find it necessary to modify these files to support special, unusual policy requirements. These files typically reside in the SELinux source directory and a variety of subdirectories, including domains , file_contexts , flask , macros , and types . -
- Source files that are typically modified by the SELinux administrator during initial configuration of SELinux
-
These include such files as those defining the authorized SELinux users and their associated roles. They are few in number, relatively short, and easy to modify and maintain. The source files most likely to be modified reside in the SELinux source directory and its types subdirectory. -
- Type-Enforcement (TE) source files
-
Each TE file contains most of the policy language statements related to a particular domain. The package maintenance utilities of some Linux distributions have been modified to install automatically the TE file related to a package at package installation time. SELinux administrators may find it necessary to create TE files for programs lacking them, or to modify existing TE files to meet special policy requirements. These files typically reside in the domains/programs subdirectory of the SELinux source directory and have the file extension .te .  | SELinux administrators may also find it necessary to modify TE files to resolve problems arising from SELinux policy bugs. Unfortunately, SELinux policies are relatively large, typically consisting of over 10,000 source lines. Consequently, the typical SELinux policy contains a significant number of bugs , some of which an SELinux administrator may be compelled to fix in order to achieve satisfactory system operation. As SELinux matures, we can expect that the incidence of such problems will decrease significantly and that many SELinux users will be satisfied with default SELinux policies. | |
-
- File Context (FC) source files
-
Each FC file contains specifications for labeling (that is, assigning types to) a related set of files and directories. The FC files are used to initially label filesystems and may be used to relabel all or part of a filesystem at special times, such as installation of a software package that creates new files or directories. The FC files typically reside in the file_contexts/programs subdirectory of the SELinux source directory and have the file extension .fc . 2.6.4 SELinux Tools SELinux includes three main categories of tools: -
Special commands used to administer and use SELinux -
Modified versions of standard Linux commands and programs -
Supplementary SELinux tools, used for purposes such as policy analysis and development The following sections describe these tool categories. 2.6.4.1 SELinux commands SELinux includes a variety of tools for its administration and use. Chapter 4 describes these tools in detail. Among the principal tools are these: -
- chcon
-
Labels a specified file, or set of files, with a specified security context. -
- checkpolicy
-
Performs a variety of policy-related actions, including compiling policy sources to binary and loading a binary policy into a kernel. The command is typically invoked via the SELinux Makefile rather than directly. -
- getenforce
-
Displays a message indicating whether SELinux is currently in permissive mode or enforcing mode. Useful only for kernels compiled with support for permissive mode. -
- newrole
-
Enables a user to transition from one authorized role to another. -
- run_init
-
Used to start, stop, or otherwise control a service. Ensures that the operation is executed in the same context used when services are automatically started, stopped , or controlled by Init. -
- setenforce
-
If given the argument , places SELinux in permissive mode; if given the argument 1 , places SELinux in enforcing mode. -
- setfiles
-
Sets file labels for a specified directory and its subdirectories, based on the specifications provided in FC files. The command is typically invoked via the SELinux Makefile rather than directly, and is generally used only during initial SELinux configuration. Older versions of SELinux included the following commands, which have been retained in the current version for the convenience of users familiar with them: -
- avc_enforcing
-
Equivalent to getenforce . -
- avc_toggle
-
Switches the system from enforcing to permissive mode, or vice versa. 2.6.4.2 Modified Linux commands and programs In addition to special commands related to SELinux, an SELinux implementation typically includes modified versions of several Linux commands. Among these are the following commands: -
- cp, mv, install, and other basic commands
-
Modified to label the new file with the security context of the source. -
- id
-
Modified to include an option for displaying the user's current security context. -
- ls
-
Modified to include an option for displaying a file's current security context. -
- ps
-
Modified to include an option for displaying a process's current security context. Several common programs are generally modified to support SELinux, including: -
- cron
-
Modified to set a standard security context for all cron jobs. -
- login
-
Modified to set the initial security context of a user when the user logs in. -
- logrotate
-
Modified to preserve the security context of log files being rotated . -
- pam
-
Modified to set the initial security context of a user and to use the SELinux API to obtain privileged access to password information. -
- ssh
-
Modified to set the initial security context of a user when the user logs in. -
- various programs that modify /etc/passwd or /etc/shadow
-
Modified to preserve the security context of the modified file. 2.6.4.3 Supplementary SELinux tools A variety of supplementary SELinux tools is available, and others are under development. Among the most noteworthy are the tools provided by Tresys (http://www. tresys .com) and distributed under the GNU General Public License. These tools include: -
- Apol
-
A tool for analyzing the SELinux policy.conf file. Figure 2-8 shows a typical Apol screen. -
- SeAudit
-
A graphical user interface (GUI) tool for analyzing SELinux log entries. -
- SeCmds
-
A set of non-GUI tools for analyzing the SELinux policy.conf file. -
- SePCuT
-
A GUI tool for browsing and editing SELinux policy files. -
- SeUser
-
A pair of GUI and non-GUI tools for managing Linux and SELinux user accounts. Figure 2-8. The Apol policy analysis tool by Tresys 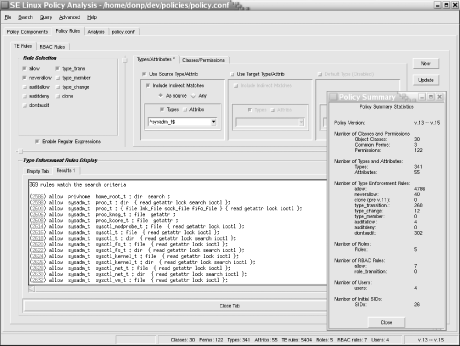
2.6.5 References To learn more about the SELinux security model, you can read Chapter 5 of this book. The description of the SELinux security model presented in this book is based primarily on the paper "Configuring the SELinux Policy," by Stephen Smalley. It is available on the NSA's SELinux web site, http://www.nsa.gov/selinux/index.cfm. The paper is somewhat out of date because SELinux has been developed further since its publication. However, for the most part, the information presented in the paper remains accurate, even if somewhat incomplete. |


