3.5 Characterizing Behavior
3.5 Characterizing Behavior
Characterizing behavior is representing how users and applications use the network; being able to characterize behavior helps you develop and understand their requirements. These representations range from very simple, such as estimating user session duration, number of active sessions, and data sizes, to more difficult, such as building complex and detailed models of user and application behavior. The goal of characterizing behavior for your network is to determine whether you can estimate network performance requirements through understanding how users and applications behave across the network.
In this section, we will examine some of the characteristics of users and applications that can be used to modify and better estimate network performance requirements. We will then apply these user and applications characteristics during the flow analysis process.
Types of behavior that we will examine include:
-
User behavior
-
Application behavior
-
Network behavior
3.5.1 Modeling and Simulation
Developing models or simulations of user, application, and network behavior is often useful in predicting, determining, or estimating requirements and data flows. Models can range from easy, simplistic, first-order approximations to highly complex and time consuming. What you get out of a model or simulation depends on the amount of time and effort you put into it.
Modeling and simulation are useful throughout the analysis process for characterizing user, application, and existing network behaviors. They are also useful during the architecture and design processes for understanding the temporal and spatial behaviors of traffic flows, as well as understanding equipment type, placement, configuration, and behavior under stress or failure.
Figure 3.8 shows an example of a simulation of a simple network. This example shows several devices connected to a shared media network and is based on a model developed to show performance characteristics of this network under stress.
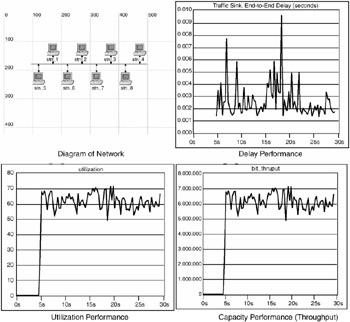
Figure 3.8: Simulation of network performance behavior.
The displays in Figure 3.8 show the results of performance tests run on this simulation. Throughput, utilization, and delay are displayed graphically over time to represent the temporal behavior of the network.
Models and simulations can be developed by using proprietary or publicly available tools. One clear benefit from having such models is that, once developed, they can be used again and again to help tune the system for optimal performance. Thus, although such models and simulations may take time and effort to develop, their payback over time can be substantial.
3.5.2 User Behavior
In conjunction with identifying service metrics for your network, it will be useful to understand how users of the system will apply applications. Simple usage patterns can include user work times and durations, and for each application, the total number of users, the frequency at which a user is expected to have an application session running (usually as number of sessions per user, per day), how long an average application session will last (usually on the order of minutes), and an estimate of the expected number of simultaneous user sessions for that application.
The logic here is that we can develop a rule of thumb for scaling the expected performance of the network by examining user and application behavior. Figure 3.9 shows the characteristics of how a user uses an application. This is an example of a simple, first-order approximation of user and application behavior. In this figure, an application session is described by some common characteristics. First, the sessions are shown with the times that the session is active (as boxes). The size of each box indicates the duration of activity, and the number of boxes per unit time indicates the frequency of activity. Also shown in this figure is the number of simultaneous sessions that are active at any given point in time.
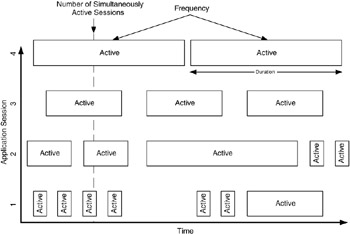
Figure 3.9: Characterization of user behavior.
Estimating the frequency and duration of application sessions and the number of simultaneous sessions will allow you to apply a modifier to the performance requirement for each application (or at least those applications you consider important enough to characterize). For example, if you can estimate the number of simultaneous sessions for an application, that estimate can be used as a multiplier for that application's capacity requirement. Similarly, if you know the duration of an application session, you can use that to help estimate the amount of time that service for that application will need to be configured within the network.
3.5.3 Application Behavior
It will also be useful to determine the behavior of application sessions. Along with user behavior, application behavior can help you to modify performance requirements to achieve a better estimate of which services and performance levels you will need for your network.
In characterizing application behavior, you want to consider the data sizes the application will be processing and passing across the network; the frequency and time duration for data to be passed across the network; any traffic flow characteristics you can get for the application, such as flow directions (e.g., from client to server); and any requirements for multicasting (including broadcasts).
In applying user and application behavior, you can go from a fairly simple approximation to a very complex model. For example, you can make some simplifying assumptions about usage patterns and application behavior. One simple model is to assume that only one session of an application will be active at any time. Another model is to apply statistical formulas to the usage pattern and application behavior. This can be quite successful when the application is well understood, such as with telephony applications.
Although you can attempt to characterize behavior for all users and applications for your network, you will usually get the greatest benefit by applying this analysis to the most important (mission-critical, rate-critical, real-time, interactive, high-performance) applications and their users, as their requirements typically drive the network architecture and design. Although characterizing usage patterns and application behavior can be both difficult and time consuming, you will find that doing so will greatly help your understanding of the system's requirements and how to apply them. However, you should be sure that you could afford the time and effort it will take. From personal experience, I have seen quick first-order approximations developed in days and complex, detailed models and simulations that have taken months to refine. However, many good approximations can be done on the order of a few weeks.
EAN: 2147483647
Pages: 161