9.9 Exercises
9.9 Exercises
For Exercises 1 through 3, refer to Figure 9.16.
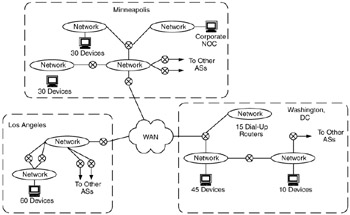
Figure 9.16: Network for Exercises 1 through 3.
-
Develop a sample threat analysis for the network in Figure 9.16 or for a network with which you are familiar. Show assets and potential threats as in Figure 9.2.
-
Apply the security mechanisms from this chapter to support the following requirements. Show where each mechanism might be applied.
-
An intranet between each of the routers connected to the WAN.
-
Remote access security must be provided for each of the 15 dial-up routers connected to the LAN in Washington, DC.
-
All traffic flows between Los Angeles and Minneapolis must be encrypted.
-
-
Outline the development of DMZs that would be applied at each site where connections are made to other autonomous systems (AS). What types of devices would be used at these sites?
-
Figure 9.17 shows five security zones required by the customer. These zones are prioritized, such that security zone 5 provides basic security for the entire network, and zones 2, 3, 4, and 5 have increasing degrees of security, and security zone 5 has the highest level of security. For this network:
-
What security mechanisms can be applied within each security zone and at the interfaces between security zones, to achieve increasing degrees of security?
-
Which architectural models are most applicable to this network? Show how each model can be applied.
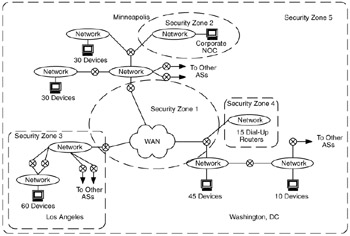
Figure 9.17: Network for Exercise 4. -
EAN: 2147483647
Pages: 161