Section 2.3. The Role of Roles
2.3. The Role of RolesSELinux also provides a form of role-based access control (RBAC). The RBAC feature of SELinux is built upon type enforcement; access control in SELinux is primarily via type enforcement. Roles limit the types to which a process may transition based on the role identifier in the process' security context. In this manner, a policy writer can create a role that is allowed to transition into a set of domain types (assuming the type enforcement rules allow the transition), thereby defining the limits of the role. Take our password program example in Figure 2-5. Although according to the type enforcement rules, the password program can be executed by the user_t domain type to enter the new passwd_t domain, Joe's role must also be allowed to be associated with the new domain type for the transition to occur. To illustrate, we extend the password program example in Figure 2-6. Figure 2-6. Roles in domain transitions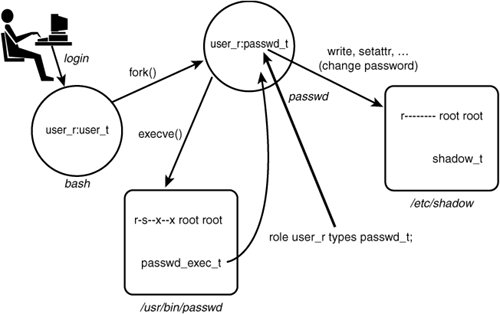 We have added the role portion (user_r) of the security contexts for the processes depicted. We also added a new rule, specifically the role statement: role user_r type passwd_t; The role statement declares role identifiers and associates types with the declared role. The previous statement declares the role user_r (if it has not already been declared in the policy) and associates the type passwd_t with the role. What this association means is that the passwd_t type is allowed to coexist in a security context with the role user_r. Without this role statement, the new context joe:user_r:passwd_t could not be created, and the execve() system call would fail, even though the TE policy allows Joe's type (user_t) all the necessary access. A policy writer can define roles that are further constrained and then associate these roles to specific users. For example, imagine that in our policy we also create a role called restricted_user_r, identical to user_r in all regards except that it is not associated with the passwd_t type. Thus, if Joe's role is restricted_user_r instead of user_r, Joe would not be authorized to run the password program even though the TE rules would allow his domain type the access. Chapter 6, "Roles and Users," discusses in detail the purposes of roles in SELinux and in particular how they are created and associated with users. |
EAN: 2147483647
Pages: 154