Basic Protocol Behavior
A network based on the OSI model is segregated into layers. Each layer has its own protocol, which performs a specific set of functions to enable data transfer from source to destination. The characteristic of most protocols can be divided into two categories: connection-oriented and connectionless.
Connection-oriented protocols are also called reliable protocols, because the sequence of data packets is the same at the source and destination nodes. On receipt of data packets, the destination node sends an acknowledgment to the source node. If any data packet is lost or corrupted during transmission, connection-oriented protocols demand retransmission of the missing data packet. However, a few connection-oriented protocols, such as Frame Relay (FR), are unreliable, because they require virtual connectivity for sending data packets and do not have to depend on any reliability mechanism. In connection-oriented protocols:
-
The path taken by data packets from source to destination is established before actual data transfer.
-
The resources required for a connection are reserved in advance.
-
Resource reservation of a connection is active throughout the life of that connection.
-
The allocated resources are available for use after the connection is terminated.
On the other hand, connectionless protocols are unreliable, because data packets sent using these protocols might not be received in the same sequence. The receiver does not send any acknowledgment on receipt of data packets. In addition, connectionless protocols do not demand retransmission of missing or corrupted data packets. Therefore, there is no guarantee that all the data packets have actually reached the destination. This is similar to sending mail without receiving a return receipt.
For reliability, connectionless protocols depend on protocols residing in the higher layers of the OSI model. The higher layer protocols arrange the data packets in the appropriate sequence, handle timeout counters, and demand retransmission of missing data packets. For example, in the TCP/IP protocol suite, IP is a Layer 3 connectionless protocol, and TCP is a Layer 4 connection-oriented protocol. However, there are a few exceptions. For example, Open Shortest Path First (OSPF) is a reliable connectionless protocol, which demands acknowledgments from its neighbors when it multicasts routing updates. In connectionless protocols:
-
Each message is independent of other messages.
-
The destination node manages nonsequential arrival of data packets.
-
The protocols provide dynamic flow through the network. This is because connectionless protocols are always in the data transfer phase with no explicit setup or the release phase (like connection-oriented protocols).
-
The protocols provide alternate paths for data transfer.
Types of Connectionless and Connection-Oriented Protocols
Connectionless protocols transfer data packets independently without establishing a logical connection between the source and destination nodes. Therefore, the protocol sends data packets with all the information about the destination node. This information includes the destination address and the services required by the data packet.
Some connectionless protocols are:
IEEE 802.2: Provides three types of services, of which Type 1 and Type 3 are connectionless. The Type 1 service is an unacknowledged connectionless service, whereas Type 3 provides acknowledged connectionless services. Type 3 service is also referred to as a Logical Link Control (LLC). (Type 2 service of IEEE 802.2 is a connection-oriented service.)
Connectionless Network Protocol (CLNP): Provides connectionless service at the Network layer.
IP: Functions at the Network layer of the TCP/IP protocol suite and is connectionless.
UDP: Resides at the Transport Layer of the TCP/IP protocol suite, and provides connectionless services.
Fast Sequenced Transport (FST): Functions above the Network layer and is a connectionless transport protocol. The FST protocol uses the IP header to implement sequencing of the data packets being transferred.
Protocols using connection-oriented data transfer services establish a logical connection between the source and destination nodes. This logical connection consists of three phases: connection establishment, data transfer, and connection termination.
The main connection-oriented protocols are:
Type 2 service of IEEE 802.2: Is widely used in LAN networks, and also called the LLC2 connection-oriented data-link layer protocol.
ATM: Transfers data packets using the concept of Virtual Circuits (VC).
TP0, TP1, TP2, TP3, and TP4: Are a part of the Connection-Oriented Network Services (CONS) of the OSI model. For this, the OSI uses the X.25 packet-level protocol to provide connection-oriented data transfer.
TCP: Provides reliable and connection-oriented data transfer. It specifies the data format of the data packets being transferred and controls the entire data transfer operation.
| Note | A VC provides a private connection between any two nodes in an ATM network to facilitate data transfer between the nodes. A VC consists of a Virtual Path Identifier (VPI) and a Virtual Channel Identifier (VCI). |
However, most networks use a combination of connectionless and connection-oriented protocols. This ensures that advantages of both the connectionless and connection-oriented services are used by networks during data transfer.
Like protocols, the different layers in a protocol display two types of behaviors to the above layers:
-
Connectionless
-
Connection-oriented
Connectionless Behavior
In connectionless behavior, there is no dedicated setup between communicating layers. Each data packet is independent of other data packets placed before and after it. This process is known as connectionless data transfer. For example, consider a courier service that forwards packets from one branch office to another. When branch office A sends a set of packets to branch office B, each packet is treated as a separate entity. Office A sends packets nonsequentially; it is the responsibility of office B to arrange them in the correct sequence. Even if two packets are sent to the same destination, they are considered different entities. The first packet is processed and sent to the destination first, followed by the second packet. However, there might be a situation in which the second packet reaches the destination prior to the first packet. This happens if there is some error in delivery. After office B receives the packets, it arranges them in a sequence, detects the missing packet, and demands retransmission.
In the same manner, a layer in a protocol sends packets to the layer above it, nonsequentially. After the upper layer receives the data packets, it arranges them in the correct sequence, detects the missing packets, and demands retransmission from the lower layer.
Connectionless data transfer offers two important advantages:
-
Easy implementation
-
Decreased network traffic as compared to connection-oriented data transfer
While troubleshooting connectionless data transfer, you should check the areas where:
-
Data packet receipts are not acknowledged.
-
Data packet errors are not reported to the sender.
-
Data packets are not in correct sequence.
-
Flow control is missing.
Connection-Oriented Behavior
In connection-oriented behavior, there is a dedicated setup between the communicating layers. Data is transmitted sequentially in streams of packets or frames over a single path through the network. Examples of connection-oriented protocols are TCP and ATM.
Connection-oriented behavior is similar to a telephone system. To make a telephone call, you:
-
Pick up the receiver and dial the destination number.
-
Converse with the person at the destination.
-
Disconnect the call when information exchange is complete.
Similarly, in a connection-oriented behavior:
-
The connection is established.
-
Data is transferred.
-
The connection is terminated.
The essential aspect of connection-oriented behavior is that it acts like a tube when the source node sends data packets from one end and the destination node receives them at the other end, in the same order. This process, also known as a handshake, is depicted in Figure 2.1.
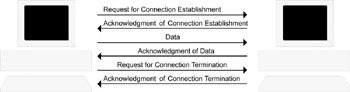
Figure 2.1: The handshake process in a connection-oriented behavior.
The services offered by connection-oriented protocols are:
Flow Control: Implemented by specifying definite space for data packets. There may be situations in which the source node sends the data at a transmission speed that is higher than what the destination node can handle. This leads to network congestion. To avoid this, connection-oriented protocols use the Windowing technique, in which the receiver specifies the space available for a data packet. The sender sends the data packet pertaining to the specified space and waits for an acknowledgment. The acknowledgment ensures that the recipient has received the data packet and can receive more.
Sequenced Delivery: Ensured by assigning a connection identifier and a sequence number to each data packet. In addition, if data packets are not received in the correct sequence, the receiver uses a unique sequential numbering scheme. This scheme is decided during the Request for Connection (RFC) establishment phase.
Error Control: Ensured when the receiver sends a request for retransmission, if the data packet received is damaged.
| Note | The receiver checks whether the data packet received is damaged or not, with respect to the number of bits received. |
While troubleshooting connection-oriented data transfer, you need to monitor the:
-
Number of data packet retransmissions in the network. If there is an excessive number of retransmissions, you need to inspect why the upper layer protocols are requesting them.
-
Parameters of protocols such as level of incrementing and controlling of sequence numbers.
Connection-Oriented Behavior Versus Connectionless Behavior
There are many differences between connection-oriented and connectionless protocols. Table 2.1 lists the major differences between connection-oriented and connectionless behavior.
| Connectionless Behavior | Connection-Oriented Behavior |
|---|---|
| Data packets are sent non-sequentially; that is, a packet that is sent later reaches the destination first. | Data packets are sent sequentially, by assigning a connection identifier and a sequence number. |
| Unreliable and nonsequential delivery. | Reliable and in-order delivery. |
| Simple to implement and has comparatively low requirement for network traffic. | Comparatively complex to implement and has high requirement for network traffic. |
| No dedicated link between the communicating layers. | A dedicated link is established between the communicating layers. |
| No acknowledgment is sent by the destination node on receipt of data packets. | An acknowledgment is sent by the destination node on receipt of each data packet. |
| Does not allocate resources to connections. | Allocates resources to connections at switches. |
| A route packet is based on the destination address, which is in every packet. | A route packet is based on an identifier (connection ID is in every packet). |
| Per packet routing; that is, data packets are rerouted if a failure occurs. | Per connection routing; that is, in case of failures, connection should be re-established. |
| Examples of connectionless protocols are Ethernet, Frame Relay, and IP. | Examples of connection-oriented protocols are Token Ring, X.25, and TCP. |
Table 2.2 lists the examples of connection-oriented and connectionless protocols.
| Connectionless Protocols | Connection-Oriented |
|---|---|
| UDP | ICMP |
| XDR | DVMRP |
| NetBIOS | RSVP |
| DNS | SLIP |
| DHCP | CSLIP |
| NTP | IP |
| BOOTP | X.25 |
| TFTP | TCP |
| SNMP | ISO-DE |
| Remote Unix Services | PPTP LDAP RPC LPP HTTP FTP SMTP Telnet |
EAN: 2147483647
Pages: 130