Standard NAT Defined
Standard NAT Defined
The traditional definition of NAT is contained in the very term itself. Network Address Translation is the act of changing an address from one to another within the packet. While this change is usually of the source address, there is no restriction. This address changing function is essentially a router function when you consider the mechanisms. Any router, due to its very nature as an intermediary between networks, may perform the NAT function.
The early history of IPv4 networking did not need to consider this type of routing function very often. Occasionally the subject would come up, but those discussions usually were centered within fairly convoluted reasoning. The IPv4 address space does contain over 4 billion addresses and until the explosion of the Internet in the early 1990s, there was no solid reason to play with the addressing space. Thus, while NAT existed and was used it was not what is popularly referred to today as NAT.
Think of the traditional proxy server. Considering the entire sequence of events as seen from outside the server, it is essentially performing NAT. The request is made to the inside of the proxy from some client with some source address. The proxy then turns around and sends out a packet with its own source address. When the proxy receives the response, it responds back to the client.
This transaction is NAT as it fits all aspects of the definition. An address is translated by a router that spans two disparate networks. While you may not think that this scenario is a routing scenario, it certainly is. Remember that a router is defined as a system that allows traffic to be sent between networks. Traffic exists to request and receive services. So if you can sit at a machine on an IP network, make a request for a service on another network from some device, and receive that service, then you have used a router.
This is the core of considering NAT as a legitimate function within the scope of an IP network. IP addresses define service location. Receiving a service from a disparate network to your network requires a router. Whether that service provider actually saw your real source address is irrelevant to the networking. All that matters is that a service was transacted across network boundaries.
Seen in this light, the function of a NAT firewall is fairly obvious, especially when you consider the popular IP Masquerade. IP Masquerade is merely a many-to-one NAT. In the sense in which it is used in a Masquerading firewall, you can consider the firewall to be performing a proxy service. However, the proxy service is not specific to an application or protocol, but rather to an address.
These concepts are so important because of the misconception within the networking community that NAT is somehow dirty or evil because it supposedly breaks the end-to-end model originally proposed for IP networking. The end-to-end model is the function whereby any given service transaction is performed between two, and only two, entities. But the end-to-end model is an interpretive assumption of the communication structure. For example, consider the actual communication structure of a proxy system.
The communication is initiated by a client wanting a service. The client sends a request for that service to the original service location defined by the service's IP address. This request reaches the proxy system. The proxy system intercedes into the communication. Under most protocols, the proxy system at this point would complete the initial handshake with the client on behalf of the final service. This is important because at this point the end-to-end model is satisfied from the client's point of view as the two ends, client and service, are negotiated. From the original service's point of view noth ing has yet happened . So now the proxy initiates the communication with the service on behalf of the client. From the original service's point of view, the end-to-end model is complete because the client is the proxy.
Stepping back a level there are two distinct end-to-end connections that have been formed from one original request. Think of the true communication structure between two clients on either side of a router. From the layer 2 perspective, which is where the actual packet communication takes place within a local network, there are two end-to-end communications made out of one request.
Now substitute NAT for proxy. In both cases the end-to-end model is satisfied providing that the communication always includes the middle. So you must always have a bottleneck point for NAT. Or must you?
Consider the three main types of NAT: One-to-One, Many-to-One, and One-to-Many. Both Many-to-One and One-to-Many NAT are best considered as mapping types of NAT. They take a single address and spread it across many addresses. Both of these types require a single point at which to perform the mapping and through which the reverse mapping must occur. But One-to-One NAT does not require the same location to perform the mapping.
The very name One-to-One NAT implies that there is a unique correlation between two addresses. The only differentiation is direction. In one direction, address A becomes address B and in the other direction, the reverse is true. Since NAT may be considered a router function, this map function may exist in every router that crosses the boundary defining the edge over which direction changes.
Consider the network illustrated in Figure 8.1. This is a fairly typical large corporate network with three primary sites. Each of the primary sites has a Policy Routing system connecting them to the Internet. Internally, all three sites are connected either through dedicated lines or VPN structures. Now imagine that there is a Web server at each location that will provide the location unique Internet services.
Figure 8.1. MultiRouter NAT network.
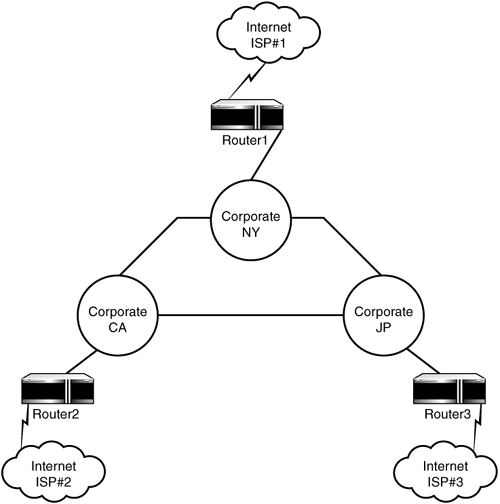
Each of these Web servers, call them WebA, WebB, and WebC, are addressed with internal addresses appropriate to the location. From the Internet's perspective there are three addresses assigned in DNS to each of these Web servers. The company has a registered block of IP addresses that it uses for all of its Internet- related activities. All three ISPs allow any of these addresses to enter or leave the local connection.
Since the internal addresses are in compliance with Private IP addressing (RFC-1918), the Web servers must be NATed when they route to the Internet. But which router should perform the NAT? All of them.
Think for a minute about the routing structure as it pertains to the Internet traffic. Each local machine within a corporate sector may route to the Internet by whatever path is specified as default according to the local internal router. But Internet traffic may enter the network by the closest router in relation to the traffic's origination. That is, traffic to the corporation that originates in Japan (JP) will enter the corporate network through Router3. But what if that traffic is destined for WebA?
In this scenario, under traditional routing all traf fic destined for WebA is given a single connection point. So consider that under traditional routing all traffic destined for WebA must be routed through RouterA whether or not RouterA is available. But under Policy Routing the traffic may enter at any of the three routers because the NAT may be performed at any of the three routers. Remember that NAT is a router function and that this is One-to-One NAT.
In the Policy Routing scenario, all three routers will contain the NAT definitions. All three routers contain the NAT map function as each router spans the boundary defining the edge over which traffic direction changes. NAT is truly a router function and Policy Routing provides the framework for defining the entire routing function scope of application.
| Top |