Filtering on Source and Destination Ports
Earlier in this book, we looked at building some standard protocol filters. You simply checked off the protocol you were interested in and voila, the filter was built.
Those filters were based on a predefined set of port numbers that the analyzer knows about. Easy enough, but what if the analyzer doesn’t have a predefined protocol setting for one of the protocols you want to catch? For example, perhaps you want to catch all the Morpheus traffic on port 1214 (Morpheus is a peer-to-peer application that poses a significant security risk). Or... maybe you want to catch traffic to and from your Fluke OptiView system running OptiView Remote (port 1695).[6]
In this case, we need to build a pattern for all traffic to port 1214 and another filter for all traffic from port 1214. This enables us to catch the traffic that goes to or from any proxy server.
This type of filter can be built to catch any traffic as long as you know the port number that is used. Refer to the Protocol Number Assignment available online at www.iana.org for a great list of port numbers.
First, we need to know the offset of the source and destination port fields for our application. Interestingly, note that the port field offsets are the same when the packet uses TCP or UDP.
Check back on Figure 8 in Chapter 1, “Packet Filtering and Offsets.” Note that the offsets are shown as follows:
-
Destination Port Number: offset 14 hex or 22 decimal
-
Source Port Number: offset 16 hex or 24 decimal
Figures 24 and 25 show the patterns used to catch all traffic to port 1214. Remember that 1214 is a decimal value. Sniffer wants a hex value for that field, so we had to do a conversion to get the hexadecimal value 0x04BE.
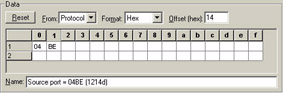
Figure 24: Convert the port number to hexadecimal and then place it at the appropriate offset for the source port field. If you use EtherPeek you don’t need to convert to hex or use the hex offset value.
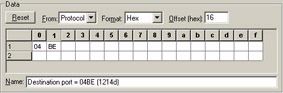
Figure 25: The destination port field follows the source port field by 2 bytes.
This is a pretty simple filter to make, eh? Just make sure you set them up using the OR operand. Using the Sniffer, your filter should look like the window shown in Figure 26.
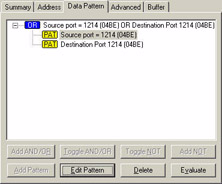
Figure 26: The OR operand indicates that an acceptable packet must match one or the other pattern.
It’s much easier to build port filters on the EtherPeek analyzer. They put in a simple “port” option under the advanced filter type. Figure 27 shows how simple it is (dang, it’s wonderful to just type in the decimal values, eh?).
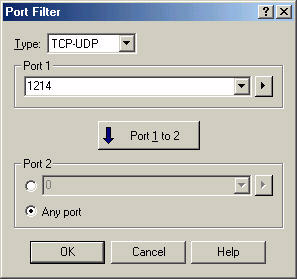
Figure 27: Just enter in the port value in decimal and you’re done! Simple, eh?
Figure 28 shows the summary window that indicates this filter would accept traffic that matches either pattern (traffic to or from port 1214/Morpheus, or ports 6346 or 6347/Gnutella.
You’ll learn more about these two applications at the end of this chapter.
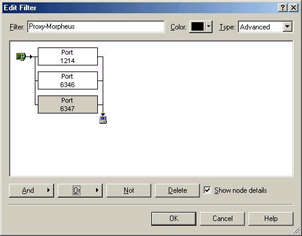
Figure 28: Just click OR > Port and then enter the port number to build port filters in Ether- Peek -- really easy.
Jot down a few of the other port filters that you’d like to build:
-
________________________________________
-
________________________________________
-
________________________________________
-
________________________________________
-
________________________________________
-
________________________________________
[6]Cool product, by the way... check it out.
EAN: 2147483647
Pages: 65