MAC (Media Access Control) Address Filtering
I build and use filters based on hardware addresses when I don't know or care about the upper-layer protocol or the upper- layer protocol addressing system. For example, if I want to catch all traffic to and from a client as it boots up so that I can find out what protocols it supports, I will filter on its hardware address - not the IP address. If I filter on the IP address, I’d miss all the IPX, NetBEUI and miscellaneous traffic that may be sent to or from the target client. Filtering on the hardware address is especially important when you have clients that boot up with DHCP because the address may change from one day to the next.[1]
When you build hardware address filters, you are only looking at traffic to and from local devices - in other words, you must be sitting on the same network as the device you are filtering on. When packets are routed, a new MAC header is placed on the packet.
Hardware address filters can be based on the entire address, if you know it. For example, Figure 10 shows a filter based on all traffic destined to the broadcast MAC address (0xFF-FF-FFFF-FF-FF).
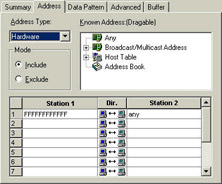
Figure 10: To catch all broadcast traffic (regardless of the upper-layer protocol), filter on 0xFF-FF-FF-FF-FF-FF.
Now, you may notice that my filter in Figure 10 is looking for any traffic to or from the broadcast address. When would you ever see packets sent from the broadcast address? You shouldn't. You might want to leave that filter as is just in case you ever see any packets show up from the broadcast address. Yikes! That would be really ugly.[2]
You need to filter on the source hardware address when you are looking at a client's bootup sequence (one of the key sessions that I always capture when doing onsites). On a Windows box, type ipconfig /all at the DOS command prompt to get a client's hardware address. Figure 11 shows how to set up the filter on a device's hardware address on the Sniffer.
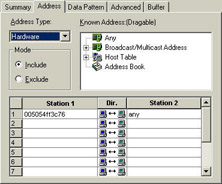
Figure 11: Building a filter on a device's hardware address.
You may notice that Figure 11 shows that the Sniffer can be configured to include or exclude an address. You may know why you'd want to include an address, but when would you want to exclude a filter? Well, consider that you may want to log into a web site and look up some things from your analyzer device while you are capturing traffic. In this case, you need to build a filter to exclude all traffic to or from your analyzer's hardware address. Now, when you capture traffic, you'll be able to remove your own address from the trace file. Don't use your analyzer's IP address - chances are pretty good that you'll move from network to network and get addresses through DHCP in most locations. Your hardware address should stay the same, however.
So far, I’ve built filters that look for traffic to and from "ANY." What if you're interested in traffic that flows between your local router and your user Fred.[3] In this case, you'll need to build a filter that has both source and destination address completed based on their hardware addresses, as shown in Figure 12.
Build the filter based on the hardware addresses instead of the IPX or IP addresses to ensure you get all the traffic between two local devices - not just IP or IPX traffic.
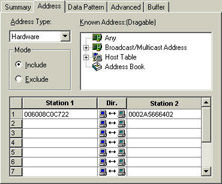
Figure 12: When you are looking for a flow of data between devices (regardless of the upper-layer protocols), filter on the MAC addresses of the local source and destination.
| Note | If you add more lines to the filter list (lines 2-7), Sniffer will OR the list of addresses together. For example, if line 1 is set up as broadcast <--> any and line 2 is 01005E000005 <--> any, then you will catch packets to or from either broadcast OR 01005E000005. -- Laura |
When you are specifically looking at all IP traffic to and from a device, then consider building an IP address filter.
[1]Although in reality there is a bit of stickiness to the DHCP addressing. DHCP clients typically ask to use the last address they had again.
[2]If you see a packet sent from the broadcast address, you might have a hacker roaming about your network.
[3]I highly recommend that you build a 'Fred Filter.' Always be ready to run a filter to see what Fred (User from Hell) is doing.
EAN: 2147483647
Pages: 65