Appendix A -- Questions and Answers
Questions and Answers
Chapter 1 Introduction to Windows 2000 Migration
Lesson 2: Migration Terminology
Practice: Scenario Analysis
Migration Case Study 1
Consider each of the following five migration methodologies and identify the advantages and disadvantages of each one for the company.
A pure upgrade
An in-place upgrade would meet the needs for a Windows 2000 environment. There's no pressing need to restructure the domain arrangement in use. If the upgrade succeeds, the users could continue to use the system in the previous way. However, if the upgrade fails, serious disruption could occur to all operations in the company.
An upgrade followed by a restructure
An in-place upgrade followed by a restructure that reduces the number of domains would allow a design that better matches the requirements of the company and could reduce the loading on support staff. The users wouldn't have to change the way they access the system until the restructure. However, the failure of the upgrade would result in the same problems as a pure upgrade, and the restructure would change the users' working environment.
A restructure (or consolidation of NT domains) and then an upgrade
It might not be possible to consolidate the users before the upgrade if the domains are large. Furthermore, attempting to consolidate the domains could result in too much disruption to the user environment because the users would have to change the way that they access the system. The upgrade itself still gives a single point of failure for the migration.
A partial upgrade/partial restructure
A partial upgrade of some domains would remove the risk of an upgrade failure disrupting all operations. Domains could be upgraded in a phased way. However, this approach might not allow you to take advantage of the benefits of a complete native-mode Windows 2000 environment.
A total restructure into a pristine Windows 2000 infrastructure
The creation of a pristine environment into which the users and resources are migrated would meet the requirements of minimal interruption of service. It would also provide a phased migration of the users and resources. However, it would require substantial additional hardware and extra planning to support both the old and the new environments in parallel during the migration.
Migration Case Study 2
Consider each of the following five migration methodologies and identify advantages and disadvantages of each for this company.
A pure upgrade
There's no requirement to retain the existing domain arrangement; in fact, the company is actively seeking to reorganize its infrastructure. Therefore, an in-place upgrade isn't a good idea, except as the first phase of a migration.
An upgrade followed by a restructure
An in-place upgrade of the largest account domain followed by a restructure of the existing domains into this domain might be one solution.
A restructure (or consolidation of NT domains) and then an upgrade
The poor design of the present infrastructure means that consolidation of the existing domains prior to restructure might not be possible. Restructuring might also result in too much network traffic on WAN links between sites. It might be possible to consolidate domains on particular sites, but this might result in too much disruption to the user environment.
A partial upgrade/partial restructure
A partial upgrade of some domains followed by a restructure might be the best solution for this company. The domains at a particular site could be upgraded and consolidated by moving domain members into one of the upgraded domains.
A total restructure into a pristine Windows 2000 infrastructure
The company is creating new corporate headquarters that will require the installation of a new infrastructure. This could be the basis of the pristine environment into which users and resources in the existing domains could be migrated.
Review Questions
- What are four core phases of a Windows 2000 migration?
Analysis, design, testing, and production.
- Which phase is likely to take the most time and why?
Depending on the size and complex nature of your migration, any phase could take the most time. For example, analysis could take substantial time because of a lack of automated resources; design, because of liaison and involvement with the many different departments, working through the various iterations of Active Directory design, and planning for as many disaster recovery eventualities as possible; testing, if any significant problems require liaison with vendors and programmers; or production, because of the size of the corporation and the sheer numbers of systems requiring the new Windows 2000 facility.
- What is an upgrade?
An upgrade is the replacement of the Windows NT operating system with the Windows 2000 operating system. Upgrading a server doesn't change its role within the environment, as it can still participate in Windows NT domains and security authentication when it's running Windows 2000.
- What is a restructure?
A restructure is a consolidation of the Windows NT domain environment to the Windows 2000 Active Directory–based mechanisms that makes domain management simpler.
- List five migration strategies.
A restructure, a restructure followed by an upgrade, an upgrade, an upgrade followed by a restructure, and a partial upgrade/partial restructure.
- Corporation X has 30 domains: 3 account domains consisting of 39,000 users each, and 27 resource domains containing minimal resources. Which methodology or combination of methodologies would you implement and why?
Upgrade account domains followed by a restructure. An initial restructure into one or two Windows NT account domains wouldn't work because of the 40-MB limitation of the Windows NT Security Account Manager (SAM) database. A restructure into a pristine environment could wreak untold havoc with hundreds of users calling your help desk should anything go wrong. The safest method would be to upgrade the account domains and then restructure into a single Windows 2000 domain if that's required.
The resource domains could be either restructured and then upgraded or restructured into a pristine environment. An initial upgrade of each would take too much time and should be avoided unless there's a very good reason for it (for example, you can't physically access them for consolidation because they are geographically dispersed and lack remote access).
Chapter 2 Project Planning
Lesson 1: The Migration Project
Practice 1: Goals and Priorities
Consider the following list of goals and decide which are business goals, which are migration goals, and which might be mutually conflicting:
- The migration project will be completed in 20 months.
- Business disruption will be minimized.
- Name resolution will be performed by DNS in place of WINS.
- Security of user information will be maintained at all times during the migration.
- Better support will be provided for geographically dispersed users.
- No information will be lost as a result of the migration.
- The domain organization of servers will be replaced by Active Directory.
Goals 1, 2, and 5 are business goals as they relate to corporate productivity. The remaining goals 3, 4, 6, and 7 are migration goals in that they relate to specific deliverables of the migration project.
Any goal involving a set time frame or budget could conflict with others. For example, the need to improve backup provision during the upgrade might conflict with the need to maintain security of information.
Practice 2: Vision and Scope
Consider the following statements and decide whether they are concerned with vision or scope:
- The migration process will result in a system that has high integrity. Overall ownership costs will be reduced and management of the installation will be delegated to appropriate levels within the organization.
This statement is a vision of the future deployment, which sets broad aims for the project in hand. Such statements are important because they explain why the effort is being performed.
- The payroll and invoicing systems are to be upgraded to the Windows 2000 platform to allow better management of remote access to them. Printing is to be integrated around a single shared server pool.
This statement sets the scope of a part of the migration process. It also mentions specific deliverables and the particular systems that will be affected.
Review Questions
- What does vision mean? What does scope mean?
A vision is a broad statement of a goal. A statement such as "provide the best possible service to our customers" is a vision. Scope places limits on the vision by mapping the vision to a particular scenario and creating thereby a specific goal; for example, "process customer transactions in less than 20 seconds."
- Is "decrease overall cost of ownership" a goal or an objective?
This is best described as a goal. It states a desired endpoint but doesn't identify a specific deliverable. "Reduce the number of servers in use by 25 percent" is an objective that might contribute to meeting this goal.
- What are business and migration goals?
The migration project will be undertaken to produce a number of deliverables for the organization. These are business goals. However, the team performing the migration will also set migration goals to meet during the process, for example "upgrade all servers to Windows 2000 in the first six months."
- When should you consider risk in a project?
You should consider risk from the very start and monitor it throughout. You should build a risk management procedure into the project, along with other crucial issues such as testing and communication.
- List at least five issues that having a test program will resolve.
Identify potential showstoppers from application, security, integration, network, performance, and capacity perspectives. Other answers should include phrases like these: to test whether domain and OU infrastructures map to the actual business processes; to test group policies, logons, and discretionary access control lists (DACLs) in the new environment; to verify the amount of replication traffic to determine whether increases in bandwidth are required; and to validate hardware compatibility where noncompliant hardware exists on the desktops.
- Why would you need the security leader in the same meeting as the corporate standards leader?
To ensure that all corporate standards for the new Windows 2000 regime also comply with the organization's security standards.
- How would a network infrastructure leader be useful to a training and help-desk leader?
To organize training on Windows 2000 network traffic and infrastructure design; to resolve which problems will go to the help desk and which will go to the network support team.
Chapter 3 Assessing Your Current Infrastructure
Lesson 3 Security Assessment
Practice: Assessing Hardware
Exercise 1: Obtaining Information Manually
- Which tab contains the same information as the bottom half of the Performance tab in Task Manager?
The Memory tab. When upgrading, all systems need to have the minimum memory required to run the applications within your organization.
- Click the Services tab. From a migration perspective, why is it important to know which services are running on Windows NT?
Specialized services might be installed on the system that will need to be duplicated in the migrated environment. Some examples of these include security devices, Microsoft BackOffice applications, and antivirus programs.
Exercise 2: Creating a Hardware Report
- What has been created in the Reports folder?
A .txt file named after the computer; in this case, Migkit1.txt.
- Open the file by typing notepad migkit1.txt and examine the content of the file. What does it contain?
Hardware information, running services, running devices, and a network report.
- Return to the command prompt and type winmsd /?. How could you use this technique to obtain information about remote computer systems?
Type Winmsd \\computername /f to create a file called computername.txt. You'll need to have sufficient privileges on the other system to do this.
- Speculate on how you could use logon scripts to collect a picture of the systems in your network.
Automate the previous process by copying the files from their location on the various hard disks to a centralized repository on the network. You could then write a Microsoft Visual Basic application that would collect all the information and write it to a central database.
If your servers are numbered consecutively and you have an account that has administrative privileges to all servers, you can write a batch file using the For … In … Do loop to collect this information about all systems in your environment. For example, the following command would collect information about server1, server2, server3, and server4:
For %n in (1 2 3 4) do winmsd \\server%n /f
Lesson 2: Application Assessment
Practice: Analyzing Application Compatibility
- Use the document to answer the following questions:
- Which hardware needs further investigation?
The LuxSonor DVD decoder card (LS242)
- Which software might not be supported?
McAfee Virus Scheduler
- Which software will need to be reinstalled after an upgrade?
Microsoft Outlook and Microsoft Internet Explorer 5.5
- Which hardware needs further investigation?
Lesson 3: Security Assessment
Practice: Checking Windows NT User Accounts
Exercise 1: Using the NET Command to Analyze a Server's Security
- What information does the file contain?
A list of all users in your SAM database, information about the administrator and guest accounts, a list of shares on your system, and who can access the Netlogon share.
Exercise 2: Assessing User Accounts
- What information about users does users.txt contain?
Information about local groups, global groups, logon scripts, profiles, and home folders is listed.
Exercise 3: Detecting Unused Accounts or Falsely Used Accounts
- Which accounts have never been used?
The Guest account should be one of them.
Review Questions
- Why is hardware and software assessment important to a migration?
Such assessment can provide details of hardware or applications that could potentially slow the migration. Without the assessment, you might jeopardize your company's day-to-day running of the business, if you find in the middle of a migration that Windows 2000 suddenly cannot work with proprietary hardware or a strategic line-of-business application.
- Corporation X doesn't have any software installed for taking inventory of enterprise hardware and software. Assuming the IT department isn't able to deploy such software before the migration, what alternative strategies do they have?
Taking inventory can be automated using scripts along with utilities such as Windows NT Diagnostics (WinMSD), and by creating a list of all files with the extension .exe, .com, and, in some cases, .dll files. These files can then be matched against an in-house database.
- When designing an application test plan, in what order would you put the following components?
- Create a timetable for testing.
- Inventory applications.
- Resolve application incompatibilities.
- Design an application test plan.
- Test and record results.
- Prioritize and classify applications.
- Declare ready to start migration.
b, f, d, a, e, c, g
- List five security components that you need to consider when designing your security migration plan.
Discretionary access control lists
User accounts and groups
Third-party security devices
Delegation of management
Use of certificates within the new environment
Potential security loopholes in the middle of the migration
Mapping current security policy to Windows 2000 group policies
- What's the most important resource that you need to budget for in the Windows 2000 migration?
Reliable, skilled personnel
Chapter 4 Assessing Your Network Infrastructure
Lesson 2: Assessing TCP/IP Services
Practice: Evaluating TCP/IP Services
Exercise 1: Installing and Configuring Windows NT DHCP
To use the Dhcpcmd command-line utility
- Type the following commands from the C:\Tools folder:
dhcpcmd 192.168.0.100 serverconfig dhcpcmd 192.168.0.100 mibcounts
What results did you get?
The serverconfig parameter returns the current DHCP server parameters and the mibcounts parameter returns the current DHCP server statistics.
- What information does the Dhcprpt.txt file contain?
It numbers each DHCP client and lists its Assigned IP Address, NetBIOS name, and network interface card (NIC) media access control (MAC) address.
- What does the Dhcprpt.txt file show now?
The same client information as before in a more textual format, plus the expiration dates for the lease, and which DHCP server (Owner host IP Address) owns the lease.
Review Questions
- List five critical issues that you should consider when assessing the network for migration.
a. Whether to restructure domains into OUs
b. Whether authentication services will be available during migration (in other words, the ability to obtain an IP address, resolve host names, and run a logon script)
c. Where site boundaries are likely to be implemented
d. Whether extra traffic will be caused during and after the migration, and whether this will impact network performance
d. How to subnet TCP/IP for optimal network performance
e. How to migrate services such as RRAS and directory replication
- Think of at least three types of traffic you should monitor.
Logon authentication, logoff for profile uploading, machine registration for WINS and DHCP, and application traffic such as database, line-of-business access, and e-mail.
- Why is it important to take stock of your DNS servers?
Windows 2000 Active Directory depends on DNS. You need to ensure that your existing DNS servers can support Windows 2000, or you'll have to migrate them to Windows 2000 DNS.
- A company's sales staff needs to dial in to the network's routing and remote access servers for e-mail, inventory levels, current prices, and specials offered by the company. When considering the migration of their RRAS, DHCP, and DNS servers, think of and write down as many settings as possible that you will need to consider if a restructure involves the total reinstallation of all the services from Windows NT to Windows 2000.
RRAS servers: Consider the number of connections supported, dial-in protocols used, whether users are able to see the entire network or just the server, which users have dial-in access, user security settings, whether dial-in clients are assigned an IP address dynamically, and, if so, whether the IP address comes from a reserved list or whether it is DHCP-assigned. Consider such security settings as type of authentication, specified callback telephone numbers, third-party security, and multiserial port devices (such as Digiboards) that might require further testing under Windows 2000. Ascertain whether RAS or RRAS services are located on a domain controller.
DHCP servers: Consider IP address ranges, subnet masks, and excluded addresses. Review all DHCP options, including the DHCP Server name, gateway addresses, DNS servers, WINS servers, node types, and whether IP conflict detection is enabled.
DNS servers: Examine BIND files containing all the zone information details, DNS Server IP address details, and the DNS server computer name.
- When using the Windows NT file and folder replication service, when would you make an exception to migrating the export server last?
If no updates are occurring to the files in the export folder. For example, if you're only replicating logon scripts that are unlikely to be changed for the foreseeable future.
- Why might keeping RRAS available during the migration to Windows 2000 create a potential security risk?
To do this, you might need to relax the Windows 2000 Active Directory security to allow the Everyone group network access. The Everyone group also includes anonymous users who could potentially try to dial in during a migration.
Chapter 5 Active Directory Design and Migration
Lesson 1: Windows NT and Trusts
Practice: Issues in Planning the Migration
- Which domains will you migrate first?
In general, you should aim to migrate the account domains first followed by either the Exchange or Web Access domain, and finally, the resource domains.
- What potential problems exist when migrating two Windows NT account domains into a single Windows 2000 domain?
Because the two domains were previously separate, there could be duplicate user and group names when the domains are combined.
- Draw a diagram of three potential Windows 2000 network designs to which you might migrate the Windows NT network.
The figure below shows some structures you might have thought of—each has its own advantages and disadvantages. However, wherever possible, you should try to reduce the number of domains.
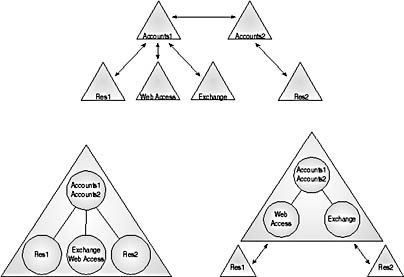
- If you perform an in-place upgrade of your Windows NT environment,
- What characteristic of an in-place upgrade cannot be changed without a complete reinstallation of the entire system and must therefore be resolved before the upgrade is performed?
The first domain you upgrade will become the forest root, so you need to carefully consider which one to upgrade first.
- What would change about the domain relationships after they're upgraded?
All the domain trust relationships will become two-way transitive trusts. This essentially means that anyone can be authenticated anywhere. If you don't want this to happen for security reasons, you'll need to design a security policy that will limit where users can log on as part of your migration plan. The alternative would be to have two separate forests.
- What characteristic of an in-place upgrade cannot be changed without a complete reinstallation of the entire system and must therefore be resolved before the upgrade is performed?
- List three pros and three cons of performing an in-place upgrade and then three pros and three cons for a complete restructure into a parallel, pristine Windows 2000 infrastructure.
Pro Con In-Place Upgrade - DACLs migrate smoothly
- You don't need to reinstall or reconfigure application software
- Easier to perform
- The risk is greater if the upgrade fails because of the time that might be required to locate the problem or rebuild the server to its original state.
- Does not take advantage of domain consolidation.
- The upgrade might contain old registry settings, files, and folders that could potentially cause problems and inconsistencies later.
Parallel, pristine restructure - There's less risk to the current running of the business because you have another system running in parallel
- You might be able to consolidate all domains into a single domain and thus free up domain controllers for other pursposes.
- No old files, folders or unused dregistry settings will be carried over from the old system.
- You can build greater flexibility into the new design.
- You can make better use of group policy objects.
- Faster disaster recovery is available should anything go wrong.
- You need substantially more time to plan the migration.
- There is more post-migration work if applications, DACL's and so forth, haven't been reconfigured correctly or migrated properly
- Sometimes only an in-place upgrade will work: for example, where there are no Windows 2000 drivers for an essential peice of hardware and Windows 2000 setup is unable to detect the Windows NT driver.
- Comparatively more difficult to perform and a greater chance for errors.
- List at least five questions that you would need to ask to produce a more relevant design and what you gain by answering each question.
Where are the domains located? This information will tell you whether slow WAN links are involved.
How fast are the links across the LAN and (if one exists) the WAN? This information is important for assessing domain replication traffic—it might be more efficient to have separate domains across a slow WAN link than congesting the link with the domain replication traffic involved in maintaining a single domain.
What sort of OU structure is required? OU information will determine whether you can migrate a domain into an OU.
What sort of security is required? Security requirements are important in determining group policy objects, domain boundaries, enabling of Encrypting File System (EFS), IPSec, certificate services, biometric devices, DHCP integration into Active Directory, etc.—see Chapter 3, Lesson 3, "Security Assessment," for more information.
How many corporate subsidiaries will want to control the contents of the Active Directory schema? This information determines whether you'll need a forest for each subsidiary.
Lesson 6: Planning and Prioritizing the Migration of Domains
Practice: Evaluating Migration Scenarios
Company One Migration Goals
- Consider each of these goals. Specify whether each design meets the goals and then explain why or why not. Assume an in-place upgrade takes place for all systems.
- A reduction in the number of domain controllers
No. The number of domains in the installation hasn't been reduced, so the number of domain controllers is unlikely to be reduced.
- Minimal impact on the employees in the company
Yes. Assuming that the upgrades proceed satisfactorily, all user names, passwords, and resources will remain intact. Users won't have to change their practices after migration.
- Minimal additional hardware
Yes. Assuming that the systems in place are able to support Windows 2000, the hardware requirements will be minimal, although as a precaution, it would be advisable to purchase an extra server which will act as a backup domain controller. Once installed and fully synchronized with the PDC, take it offline while the upgrade is proceeding. If anything goes wrong and clients can no longer log on, the BDC will be a useful fallback device. However, once each domain is upgraded successfully, this spare BDC can be rebuilt and reused in other domains being migrated.
- A simpler setup for authentication procedures
Yes. The two-way and transitive nature of Windows 2000 trusts makes it possible for users to be authenticated in any domain.
- A highly scalable platform for expansion of the IT infrastructure throughout the company
Yes. Further geographical regions can be added as OUs into the existing domains or as new domains in the tree, below the account domain.
- A reduction in the number of domain controllers
- Determine which domain should be upgraded first and explain why.
The Accounts domain should be upgraded first because it contains the user accounts and will be required by each of the migrated resource domains. It will also serve as the root of the Company One namespace.
- Determine which domain should be upgraded next and explain why.
Any of the resource domains can be upgraded next, in any order. It's advisable to start with the smallest one, especially if it's the most geographically convenient, which might be a resource domain whose servers are located physically next to the servers and PDC of the Accounts domain. Once this resource domain upgrades successfully, you can move on to the larger or more distant ones.
- Identify any points of risk in this migration and how to reduce them.
If upgrading the PDC in the account domain fails, this will impact the authentication of resource access and also the ability to manage the system. A spare BDC should be synchronized with the PDC and all policies, profiles, and logon scripts copied into the appropriate folders of the spare BDC. Once completed, the BDC should be shut down or disconnected from the network so that it can be brought online quickly and promoted to the PDC if problems arise. You should also follow this practice for any resource domains going through an in-place upgrade.
- Evaluate whether the pristine restructure design will meet the following migration goals and explain why or why not.
- A reduction in the number of domain controllers
Yes, potentially. The number of domains has been reduced to one, which should reduce the number of servers required. For example, four PDCs are no longer required and can be replaced with a single domain controller, assuming the appropriate number of domain controllers exist for the number of BDCs that used to exist in the original NT environment.
- Minimal impact on the employees in the company
Yes. Because both the Windows NT and the Windows 2000 infrastructures will be running in parallel, there will be minimal impact on the provision of IT services during the migration.
- Minimal additional hardware
No. If the migration is performed by the creation of a parallel, pristine environment, extra server and network hardware will be needed to support the migration for as long as both environments are operating in parallel.
- A simpler setup for authentication procedures
Yes. This is even simpler than an upgrade design because no trust relationships are involved.
- A highly scalable platform for expansion of the IT infrastructure throughout the company
Yes. New OUs can be created to delegate management of new divisions, and new domains can be created if further security boundaries are required.
- A reduction in the number of domain controllers
- Identify at least six additional questions you would ask the management of this company when deciding the suitability of any Active Directory design.
Some questions you might come up with include the following:
Can the company afford new hardware? If not, it will be impossible to implement a pristine environment and an upgrade might be the only option.
Will the network connections between sites be working at capacity? If so, you should look at ways to reduce traffic, such as removing WINS, examining the affordability of higher bandwidth cabling, or creating separate domains.
What's the cost and speed of site connections in use? A change in the pattern of replication between sites during and after an upgrade might alter the traffic patterns between them.
Do you want to have both centralized and decentralized control of users? If so, take this into account when designing the OU hierarchy.
Must the users be able to log on 100 percent of the time throughout the migration? If so, you should consider setting up a pristine restructure; at the least, extra BDCs should be ready if an in-place upgrade fails.
Do you want users from different geographical areas to be managed independently? If so, this might rule out the creation of a single-domain forest.
Do you want to use existing DNS names in the final environment? If so, you might not be able to create a pristine environment. You might have to perform an upgrade instead.
Are you on a tight timetable to migrate from Windows NT to Windows 2000? If so, your only recourse might be to upgrade first and then to restructure later when time permits.
- In general, which domains should be copied into the pristine environment first: resources or accounts?
Accounts should be copied first.
- Identify any points of risk in this migration and how they can be reduced.
Operating with a pristine environment reduces the risks to the production environment. The connection of the pristine environment to the production network is a potential source of problems that should be resolved in the pilot program. The user applications must also all be tested to ensure that they work correctly in the pristine environment.
Company Two Restructure Migration
- Explain why the arrangement shown in Figure 5.11 is a poor one in terms of how the authentication of resource access is performed. Suggest how this can be improved and suggest the next step in a phased upgrade involving this configuration.
The new management domain will be passing through all authentication requests from the new production domain. Performance can be improved by setting up shortcut trust relationships between the production domain and the resource domains, but this isn't a sensible design. The next stage should be the movement of accounts from the Production domain into the Management domain.
- What are the DNS names of each of the domains? How do the names relate to the domain design?
The DNS names reflect each of the positions in the tree. The root domain is msn.com and the subdomains are paris.msn.com, london.msn.com, newyork.msn.com, and production.msn.com. To make life easier, the root domain is normally named after the corporation and the second-level domains, if any, usually reflect a subsidiary or international operating unit.
- The design shown in Figure 5.12 is quite strange. What additional goals would justify creating the two account OUs and the three resource subdomains?
The separate OUs for management and production would allow different administrators and group policies for each OU.
The three subdomains might have been designed because large numbers of user objects could potentially overload site links if a WAN is in place; cultural or language differences might cause conflicts if every server were a part of the same domain; or the IT administrators of each domain might need complete autonomy of resource assignment that can't be overridden by someone higher up in an OU tree structure.
- Examine this configuration and explain why this arrangement is poor as a final design. Hint: Consider the trust referrals that will occur during authentication.
Any attempt by an account in the production.msn.com domain to access resources in the newyork.msn.com domain will result in a referral to the msn.com domain that will then pass through the request. In this situation, Company Two could consider using shortcut trusts that mirror the trust relationships in the original domains. However, it is not a good idea to create a new design and then add shortcut trusts as a way of making it work.
- One of the IT managers at Company Two wants to make Company One and Company Two separate forests rather than combining them. List as many reasons as you can to support this strategy and then list reasons to refute the strategy.
Advantages of having separate forests include these:
- Company One and Company Two IT divisions can be managed independently. The Active Directory in each forest can contain different schemas and global catalog objects.
- The use of nontransitive one-way trusts between domains in separate forests allows the system managers to rigidly control access to resources in their own forest.
- There will be no replication traffic between servers in the two forests.
Disadvantages of having separate forests include these:
- System management will be more complex because explicit trusts must be set up for each resource domain that is to be accessed from the other forest.
- Two separate environments will require maintenance instead of one.
Review Questions
- List three kinds of Windows 2000 trust mechanisms that you might see during a migration.
A one-way trust from a Windows NT domain to a Windows 2000 domain
A two-way transitive trust between two Windows 2000 domains
An explicit trust from a Windows 2000 domain to another Windows 2000 domain. This could be used to speed up resource access by connecting two separate forests or by connecting two domains in different trees of the same forest.
- What are five default Active Directory containers that are created at installation?
Built-in, Computers, Domain Controllers, Foreign Security Principals, and Users
- Which migration methodology is the easiest to perform but can contain a higher element of risk?
An in-place upgrade
- List at least three questions to answer that will help determine the order of priority for migrating domains.
Which domain should be the root domain?
Is the desired root domain an account domain or a resource domain?
Which domain contains the most accounts (or resources)?
Which domain will cause the least problems if it's migrated first?
Which domains have easy physical access?
- Why might you need to migrate a resource domain before an account domain?
If there were dependencies with distributed applications in a previously migrated account domain that a resource domain is dependent on, then the resource domain will need to be migrated before other accounts domains can be migrated. For example, if a critical application running on a resource domain is dependent on an account domain A, which has just been migrated, then the resource domain will need to be migrated prior to migrating account domain B.
- What's the advantage of migrating a Windows NT environment to two separate Windows 2000 forests?
Separate global catalogs provide for creating different schemas and replicated attributes, and two forests separate security boundaries and enterprise administrators.
Chapter 6 Performing an Upgrade
Lesson 2: Upgrading a Primary Domain Controller
Practice 2: Verifying the Upgrade
- Select MIGKIT2 and try to promote it to a PDC by selecting Promote To Primary Domain Controller from the Computer menu. Explain what happens.
The promotion fails. The Netlogon service will not start on the Windows 2000 server. Once the PDC in a Windows NT domain has been promoted to Windows 2000, it's not possible to promote a BDC to a PDC while the Windows 2000 domain controller is connected.
- Add a comment to the Market.bat logon script held in C:\Winnt\System32\Repl\Export\Scripts on the former MIGKIT1 (now migkit.microsoft.com). Then log on to MIGKIT2 and see whether the Market.bat file has been updated in the C:\Winnt\System32\Repl\Import\Scripts folder. Explain what you see. As a hint, open Server Manager on MIGKIT2 and try to configure replication on MIGKIT1. Suggest an answer to the problem.
The logon script will not be replicated. Even when you've waited long enough for a replication to complete, the logon script will not appear on the BDC. Windows NT file replication is stopped when the PDC is upgraded and must be performed manually on Windows NT servers remaining in the Windows NT domain. It's not possible to configure replication on the PDC because the Windows NT Directory Replicator Service is no longer running. The Lbridge.cmd file discussed in the next lesson can be used to perform this replication from a Windows 2000 domain controller to a Windows NT system.
- Were there any problems obtaining your normal Windows NT profile?
No. The Windows 2000 upgrade preserves Windows NT profiles. (See Chapter 7, Lesson 1, "User Profiles in an Upgrade, " for further details.)
Review Questions
- List three reasons that might cause you to perform an upgrade prior to or in place of a restructure.
An upgrade is simpler to perform, requires fewer resources, requires fewer changes to the objects in the namespace, and is appropriate when you are fundamentally satisfied with the design of your Windows NT domain.
- List the Windows NT domain properties that are preserved during an upgrade.
An upgrade preserves application settings, security permissions on files and folders, shares and permissions on the shares, trust relationships, user names, passwords, and access tokens.
- Is it possible to upgrade a Windows NT domain that only uses the NetBEUI protocol for communication between servers to a Windows 2000 Active Directory environment?
No. Although the down-level clients of Windows NT can use the NetBEUI protocol for authentication, the servers in the Windows 2000 domain, including Windows NT servers in a mixed-mode environment, must use TCP/IP to communicate.
- List at least three problems that might occur during the upgrade of a Windows NT server.
The following are among the problems that could occur: the failure of an upgrade because of motherboard or BIOS incompatibility, the failure of network card driver software that makes it impossible for the system to contact other systems and join a domain, insufficient disk space on a volume to allow Active Directory logs and indexes to be installed, lack of an NTFS volume required for the Active Directory components, or an incorrectly configured or missing TCP/IP protocol.
- Explain the difference between installing a new copy of Windows 2000 on a Windows NT server and upgrading the server to Windows 2000. Give an example of a situation in which a clean install might be preferred.
A clean install of Windows 2000 is placed in a different folder from the existing Windows NT installation and is in no way related to the currently installed Windows NT system. After a clean install of Windows 2000, it's possible to shut the system down and restart it in the previous version of Windows NT. This dual-boot capability might be required for help desk workstations when supporting a mixed environment. It can also be used to prove that the server system is capable of supporting Windows 2000 and that all the drivers are available while retaining the ability to return to the Windows NT environment.
- Explain how the Lbridge.cmd script works and the problem that it has been designed to resolve.
Lbridge.cmd is a script file that's used to copy a set of files (usually logon scripts) from one replication topology to another. It might be needed because after a server has been upgraded to Windows 2000, it no longer provides the Windows NT Directory Replicator Service. Lbridge.cmd employs the Xcopy command (or alternately, the Robocopy command) to copy the requisite files. The script can be scheduled to run on a Windows 2000 server or a Windows NT server. Another alternative is to run the script manually to copy the updated files into the export folder of a Windows NT export server or a Windows 2000 FRS topology. A custom version of the Lbridge.cmd script must be created for each upgrade situation. A better practice might be to suspend all file replication until the entire network has been migrated, if the business environment can endure such a moratorium.
Chapter 7 Transitioning an Upgrade to Native Mode
Lesson 1: User Profiles in an Upgrade
Practice: Testing User Profiles
- Wait a few seconds for the profile to update, and then log on to MIGKIT2 with the Migkitfin2 user name. Does the Solar Eclipse background appear on the MIGKIT2 desktop?
No. The Windows NT system has not been configured for Active Desktop nor does it contain the solar eclipse background.
- What do you think causes the anomalies in the profiles when user Migkitfin2 logs on to MIGKIT2 or logs on to migkit1.migkit.microsoft.com?
The Windows NT desktop bitmap is not available on Windows 2000, and the Windows 2000 Solar Eclipse bitmap is not available on Windows NT.
Lesson 3: Policy Transition and Migration Phases
Practice: Investigating Ntconfig.pol and Group Policy Objects
To create a group policy object on MIGKIT1
- Try to use the Run command on the Start menu. What happens? Try to access the Background tab in the Display Properties dialog box. What happens? Why?
The Run command and the Background tab are unavailable. The Ntconfig.pol settings have now been tattooed into the user's Ntuser.dat file, even though no Ntconfig.pol file exists on the Windows 2000 system.
Review Questions
- During your migration, a user complains that she occasionally sees a different wallpaper on her screen than her usual one. She is logging on at a number of available workstations into a mixed Windows 2000 and Windows NT environment. What's happening?
There is either a profile or policies problem. The user probably experiences this problem when being validated by a Windows 2000 client, as it might not have the bitmap that's used when she is logging on via a Windows NT system. If it's a policy problem, maybe replication of the Ntconfig.pol file has not been set up between the Windows NT and Windows 2000 domain controllers. You'll need to ask the user for more information or ask her to cope with the situation until the migration has completed. Ask her to get back to you if she finds further problems.
- A help desk user has complained that his Windows 2000 Professional system isn't always set up correctly. He has two user names. One is kept in a Windows 2000 domain that is in the middle of being upgraded, while the other name is held in a Windows NT domain pending upgrade. Suggest a possible explanation and a potential solution.
When the client system is authenticated by a Windows 2000 domain controller, the GPOs are used because the Windows 2000 workstation will locate a Windows 2000 domain controller in the mixed environment. When the client is authenticated by a Windows NT domain controller, only the Windows NT system policies are used; therefore the user will not see any of his Windows 2000 settings as no GPOs will be applied. One solution is to migrate the user name from the Windows NT domain to the domain that is in the middle of being migrated.
The problem of leaving Windows NT domain controllers in a mixed-mode environment is a bit of a red herring. In general, Windows NT domain controllers don't validate Windows 2000 clients because in theory, Windows 2000 computers will look for Windows 2000 domain controllers in preference to Windows NT domain controllers. However, in practice, this behavior depends on factors such as the location of the domain controllers (for example, are they placed across slow WAN links? How heavily are the Windows 2000 controllers being used? How much traffic is there at the controllers?).
- In a trusted environment, list the possible logon scenarios that exist. Here is one scenario to get you started: a Windows NT client in a resource domain logging on to a Windows 2000 domain controller in a trusted Windows 2000 domain.
Mixed Windows NT and Windows 2000 clients validated by Windows NT domain controllers; mixed clients validated by Windows 2000 domain controllers; mixed clients in a Windows NT domain validated by Windows 2000 trusted domain controllers; and mixed clients in a Windows 2000 domain validated by trusted Windows NT domain controllers.
- Describe the difference between a member server and a domain controller in a Windows 2000 domain. Explain how you would convert from one to another.
A member server doesn't take part in Active Directory management. It simply provides resources to users. A member server can be promoted to a domain controller by the use of the DCPROMO tool. Unlike Windows NT, domain controllers can also be demoted to member servers, without requiring a reinstallation.
- Explain how you would convert a Windows 2000 domain from native mode back into mixed mode.
You can't do this conversion. The conversion from mixed to native mode is one way. The only way to return to mixed mode is to restore the mixed-mode domain from backup media.
Chapter 8 Developing a Domain Restructure Strategy
Lesson 5: Intra–Forest Restructure
Practice: Examining Closed Sets
- You would like to move BenW to another Windows 2000 domain. What else would you have to move to ensure a closed set?
The closed set would consist of the following users: BenW, RobM, RimaC, and WayneS, together with the following groups: Authors, Consultants, Developers, and Press.
The closed set was worked out as follows:
BenW is a member of the Consultants and Press groups, so check these groups for other members.
The Press group also contains RobM, so check for all other groups to which RobM belongs.
RobM is also contained in the Authors group, so check for all other users in the Authors group.
RimaC is also contained in the Authors group, so check for all other groups to which RimaC belongs.
RimaC also belongs to the Developers group, so check for all other users in the Developers group.
WayneS is a member of the Developers group.
- How many closed sets are there?
Three. The closed sets are (1) NathanB and the Finance group, (2) JessicaR and MaryM and the Marketing group, and (3) the closed set listed in the answer to Question 1.
- List the members of the smallest closed set.
NathanB and Finance
- List the members of the largest closed set.
The set in Question 1
- How would your answers to Questions 1 through 4 be affected if the global Finance group also contained the global Marketing group and WayneS?
There would be only one closed set, which would contain every user and group listed in consultancy.trainkit.microsoft.com.
Review Questions
- List three reasons for considering a restructure.
You would restructure when you can't afford to jeopardize your production environment, when your current Windows NT environment is badly designed, and when you want to consolidate domains and groups after an upgrade.
- In general, which domain should you begin with when restructuring to a pristine environment and why?
The smallest accounts domain. In an inter-forest restructure, many user accounts will lose their passwords (unless you use a third-party utility), so you might want to validate the effect of this change on your help desk. In an intra-forest restructure, you can move only closed sets. In many cases, the smallest closed set is the entire domain, which might frustrate users if anything goes wrong because the intra-forest restructure also deletes the source objects.
- In which migration scenario is SIDhistory not required and why?
In an upgrade migration, the user's original SIDs are retained because there is no re-creation of the user and group objects during the upgrade.
- Which of the three migration strategies will allow you to retain a parallel production environment?
An inter-forest restructure
- List the advantages and disadvantages of moving versus cloning local groups from a member server to a pristine environment.
Sorry, you can't do this. The only way to migrate local groups on a member server or on a workstation is to make the member server or work-station a member of the new domain. You can do this manually or with one of the migration utilities, such as Netdom or ADMT. Remember that a local group on a member server or workstation can work only within the confines of that server.
- When migrating local groups, what needs to be duplicated in the destination domain and why?
All trust relationships maintained by the source domain will need to be duplicated in the destination domain or else any user or global group from a trusted domain contained in the local groups will no longer have access to the resources on those servers.
- What is the smallest and largest number of objects that can be contained in a closed set for a global group?
The smallest number of objects possible for a closed set is one—an empty global group or a user that doesn't belong to any groups. The largest number possible would be the entire set of users and global groups in the domain.
Chapter 9 Restructure Tools
Lesson 2: Administering DNS in a Restructure Migration
Practice: Configuring DNS
To verify the DNS service
- Type the following commands, one line at a time, and study the results:
ls trainkit.microsoft.com ls _t SRV trainkit.microsoft.com
Notice the global catalog (gc) alias in the first command's listing.
What is the difference between these two commands?
The first command lists all the hosts in trainkit.microsoft.com whereas the second command lists all the special srv records required for Active Directory support in DNS.
Review Questions
- Explain why configuring DNS correctly is so crucial to a restructure into a pristine environment.
You will need to plan for DNS in your production environment and your pristine environment. If there are any conflicts or missing entries, you will find resource access problems because client systems might not be able to locate the servers and domain controllers.
- Which migration utilities can be used to perform an inter-forest copy?
ClonePrincipal and ADMT.
- Which registry setting needs to be enabled on the source and destination domains before an inter-forest restructure can be carried out?
The DWORD value TcpipClientSupport should be added to Hkey_Local_Machine\System\CurrentControlSet\Control\LSA, and the value should be set to 1.
- What should you do prior to using the Movetree utility?
Back up the objects that are about to be moved because Movetree will delete them permanently from the source domain. If the closed set is the entire domain, you should make an image file backup of the server before using Movetree. You should also back up the destination environment in case you need to roll back the destination environment prior to the move operation; otherwise, the destination will contain all the users from the first Movetree operation and could cause potential problems if another Movetree operation is attempted using the recovered domain.
Chapter 10 Post-Migration Tasks
Lesson 4: Creating Support Tools
Practice: Creating a Custom MMC
- Try disabling the Fin1 account. Were you able to do it?
No, the Mig1 user only has permission to set the passwords of these users.
Review Questions
- Why should SID values from the source domain be removed from resources in the destination domain, and what will happen if they aren't?
SID values from the source domain won't have any meaning in the destination domain, and the owner of resources shown on the DACLs might be construed as an unknown user. Management of the resources then becomes difficult because the administrator won't know whether these resources are required. However, it won't affect access to resources because the SID values will appear in SIDhistory entries on security principals in the destination domain.
- Why should the SIDhistory property be removed from users and groups in the destination? What will happen if it isn't removed?
Once all resources have been migrated over, the SIDhistory property will become redundant. SIDhistory increases the size of the access token produced when a user logs on. In extreme situations, where the number of SID entries on an access token exceeds 1,024, a user might be prevented from logging on to the system.
- What are the potential problems when disk quotas are enabled on a volume?
If a quota is set on a volume, users with no specifically allocated quota will be unable to store more files than the specified quota size. If a user exceeds the disk quota when saving profile information during a logout, he or she will be unable to log on again. This problem might result in damage to the user's profile, which will then need to be replaced or rebuilt.
- The user Benw, who is the manager of Research and Development, wants to be able to create and manage users for his division. He has suggested that you create a new domain to allow him to manage them. What would you do instead?
There's no need for a new domain. Benw can be given the ability to create and manage users by creating an OU and delegating control of the OU to him.
- What is a snap-in and how do you use it?
A snap-in is a component tool that can be loaded into Microsoft Management Console. It manages a particular part of the Windows 2000 system. For example, the Active Directory Sites And Services and Active Directory Users And Computers tools are both snap-ins. The name is derived from the way that you can "snap-in" any of the components to an MMC framework. Once a snap-in has been added, you can create a specific view with the tool and then save the MMC configuration as a custom tool. The snap-ins themselves can be protected by policy settings to prevent unauthorized use.
Chapter 11 Troubleshooting Windows 2000 During and After Migration
Lesson 6: Time Synchronization Issues
Practice: Troubleshooting a Time Synchronization Problem
- Log off and attempt to log on again, using MIG1 and a password of secret. What happens?
Either the system will fail to log you on (telling you there's a time difference between the client and the server), or it will log you on and show you a message that your password is about to expire (because the date has now been advanced one month).
If you were MIG1, what would you need to do to troubleshoot this problem?
In this case, waiting would be enough because in time, the client would synchronize its clock with the server once more. However, you can also log on as Administrator and use the W32tm command or the Net utility to reset the date and time. If those don't help, the simplest solution is to restart the user's Windows 2000 workstation, which will force an immediate time resynchronization.
Review Questions
- As you migrate from Windows NT 4.0 to Windows 2000, you find that your DHCP clients are unable to contact a DHCP server. What's the most likely cause of this problem?
The DHCP servers haven't been authorized in Active Directory.
- How would you ensure that your applications work correctly under Windows 2000 when you migrate? What do you do if they don't work?
First, determine whether the application is on the list of applications certified by Microsoft to work correctly under Windows 2000. Then test the application thoroughly. If the application doesn't work under Windows 2000, you can try running it on a Windows 9.x machine, NT workstation, or NT member server without stopping the switchover to native mode.
- All users in one particular part of a building are taking a long time to log on to Windows 2000. By contrast, other users in the same building are logging on quickly. What's the likely cause of this problem?
The subnet that the users are on isn't associated with the appropriate site. Investigate using Active Directory Sites And Services.
- During your migration to a multi-domain model in Windows 2000, your clients have no trouble logging on to the domain. After all your domain controllers have become Windows 2000 domain controllers, you switch to native mode. Some of your clients are no longer able to log on. What happened?
In switching to native mode, you caused the domain controllers to query global catalog servers for universal group memberships. One or more of the domain controllers is unable to locate a global catalog server, and this prevents users without cached credentials from logging on.
- List three problems that can occur if your domain isn't synchronized.
Clients won't be able to log on.
Replication won't occur.
The administrator will have problems using some of the utilities.
Chapter 12: Business Continuity
Lesson 1: Planning for Failure
Practice 1: Identifying Vulnerabilities
To help you focus on the potential areas of failure, speculate on what you think can go wrong. Using the following table as a starting point, list as many potential points of failure in the system as possible and how you might be able to resolve them.
Your answers should have identified a few of the key components listed in the table below.
| Category | Failure Point | Potential Resolution |
|---|---|---|
| Hardware | Hard disks | Use disk mirroring or disk striping with parity. |
| Hard disk controller | Use disk duplexing (where you have a separate redundant hard disk controller in the computer system). | |
| Video controller, network card, RAM chips, and so on | Have spares on hand. At present, you'll need to take the server down to replace any of these parts. | |
| Complete system failure | Use clustering with Windows 2000 Advanced Server or use a third-party backup server. | |
| Software | Data corruption | Use virus protection and perform regular backups. There will be some downtime while the data is restored. |
| Software corruption | Perform load balancing via Dfs and clustering. If the application software doesn't support clustering, virus protection and regular back-ups will be required. There will be some downtime while the software is restored. | |
| Network | Critical network cable damage | Ensure that alternative routes are available to servers by having several routes to a server. |
| Hubs, routers, and bridges | Ensure that you have enough spares and switches to switch a network over to another router or hub in the event of a failure. | |
| Too much traffic generated | Some processes can generate too much traffic for your existing net-work, such as backing up servers across the network. A solution might be to have a second network card in all servers and connect the secondary card to a management hub so that all server management traffic is isolated from the production environment. | |
| Network services such as DHCP, WINS, and DNS | See Lesson 3 on maintaining network services. | |
| Client | Hardware or software failure | Several spare systems should be available if the help desk can't repair these problems in a timely fashion. |
| Miscellaneous | Power supply problems | Use a backup generator or uninterruptible power supply. |
| Missing key personnel because of holidays, business trips, and accidents | Be sure that two or more people in your company understand how to repair systems. If it's not possible, you might require a 24-hour on-call contract with an employee or IT management company. |
Review Questions
- List at least four phases or milestones at which you need to make a backup prior to moving to the next phase.
Creation of pristine environment
Migration of DNS, DHCP, or WINS services
Upgrade of PDC in a domain
Upgrade of a BDC in a site
Successful migration of users, groups, and machines prior to decommissioning source domains
- What potential problems might you encounter when using tape backups during an inter-forest restructure?
It's difficult to manage a tape library holding duplicate tapes of all fallback positions of source and destination domains.
You might experience physical tape problems. (Avoid using DAT because it tends to stretch and be unreliable.)
Tapes will not recover an entire system failure. You'll need to rebuild the system, which can involve partitioning, formatting, and reinstalling the operating system prior to being able to use tape for recovery.
Additional network traffic is caused by running Windows NT Backup over the network—it's best to use service networks (in other words, a secondary network card on a different network) for this operation.
- List two advantages of imaging.
Imaging allows a complete rebuild, including partitioning and restoration of the operating system, system state data, and all applications, in much less time than restoring via a tape backup.
Imaging will enable a faster restore of business processes in the event of a failure.
Managing CDs is easier than managing backups on tape.
CD-ROM is a more robust medium than tape and isn't subject to wear and tear such as stretching.
- List four network services that require consideration to allow ongoing user and machine authentication during the migration.
DHCP—for IP address assignment
WINS—for name resolution to attach to resources
RRAS—for dial-in access and authentication
Domain controllers—for user and password authentication
- Speculate on how you can keep a DHCP service available while the DHCP server is being migrated.
Two possible answers include the following:
Recreate the DHCP service in the existing Windows 2000 environment prior to migrating the Windows NT DHCP service; however, don't activate the service until the DHCP service on the Windows NT system has been deactivated.
Have a secondary DHCP server running that contains a nonduplicated set of the IP addresses for the workstations on the subnet being upgraded.
- Discuss two alternative methods to plan for extra servers to handle business continuity during the migration of network services.
Perform the migration over a holiday period. Depending on the time needed to migrate servers (you should have determined this in your test labs), consider giving employees time off.
Have a moratorium on all network services and provide for employees to work from their local systems. Employees would need to save their work in a specific folder (for example, a folder called Migration on their local hard disks), and then an automated procedure would be written to copy their data onto a file server once network services are back online.
EAN: 2147483647
Pages: 126